De-risking Your Organization in Spite of NVD Delays
In the face of recent struggles with the National Vulnerability Database (NVD), causing delays in analyzing Common Vulnerabilities and Exposures (CVEs) since February 12, 2024, a significant number of CVEs lacked essential metadata including severity scores and affected product details. Qualys remains unaffected, however, and can ensure that organizations will not be left vulnerable. This bottleneck in the NVD process, which has caused thousands of vulnerabilities to become stuck in an “AWAITING ANALYSIS” status, poses a severe challenge for organizations that rely on timely and accurate vulnerability information to safeguard their systems.
The significant delays in the NVD analysis of CVEs present profound risks to organizations and could introduce substantial problems in their defense mechanisms. Key issues arising from delays in the NVD’s CVE analysis include:
- Increased Attack Surface: The lack of timely, essential data, such as severity scores and details on affected products, exposes organizations to potential attacks.
- Inefficient Vulnerability Management: The absence of prompt information results in operational delays, inefficient vulnerability prioritization, and remediation efforts.
- Elevated Compliance Risks: Delays impair decision-making processes, complicating adherence to compliance requirements and elevating risk levels.
- Forced Reliance on Less Comprehensive Sources: To fill the information void, organizations turn to alternative sources, which may lack the NVD’s thorough coverage, further jeopardizing their security posture.
- Strategic Advantage to Adversaries: This situation potentially gives adversaries a strategic edge, exploiting the window of vulnerability created by the information gap.
These challenges underscore the critical need for organizations to evolve their approach to vulnerability management.
Qualys has proactively circumvented these challenges by not depending solely on the NVD for its vulnerability detections. Instead, Qualys bases its detections on vendor advisories, leveraging direct information from the source and ensuring the accuracy and timeliness of its vulnerability management solutions. Also, Qualys stands resilient, as VMDR Prioritization and TruRisk ensure continuous protection and strategic threat mitigation for organizations navigating the current cybersecurity landscape. Qualys researchers manually add the Common Vulnerability Scoring System (CVSS) scores when they are not provided by the NVD, maintaining the integrity and usefulness of the data. Furthermore, Qualys’ platform automatically updates the scores from the NVD as soon as they become available, ensuring that its database is always up to date.
This strategic approach to vulnerability detection shields Qualys from the current NVD backlog and highlights the importance of leveraging diverse sources of vulnerability intelligence. While solutions that rely exclusively on the NVD might face significant challenges in detecting and responding to new threats, Qualys’ methodology ensures continuous protection against emerging vulnerabilities. This proactive and multifaceted strategy highlights Qualys’ commitment to robust cybersecurity practices, ensuring that its clients remain secure despite widespread delays and information gaps within the NVD.
Alongside a broad array of protective measures, Qualys further strengthens resilience through two of Qualys’ key features: VMDR Prioritization and Qualys TruRisk.
VMDR Prioritization: This feature empowers organizations to focus their resources efficiently by identifying and remedying the most critical vulnerabilities first. By correlating vulnerability data with threat intelligence, along with the specific context of an organization’s assets, Qualys’ VMDR Prioritization hones in on the vulnerabilities that pose the most significant risk.
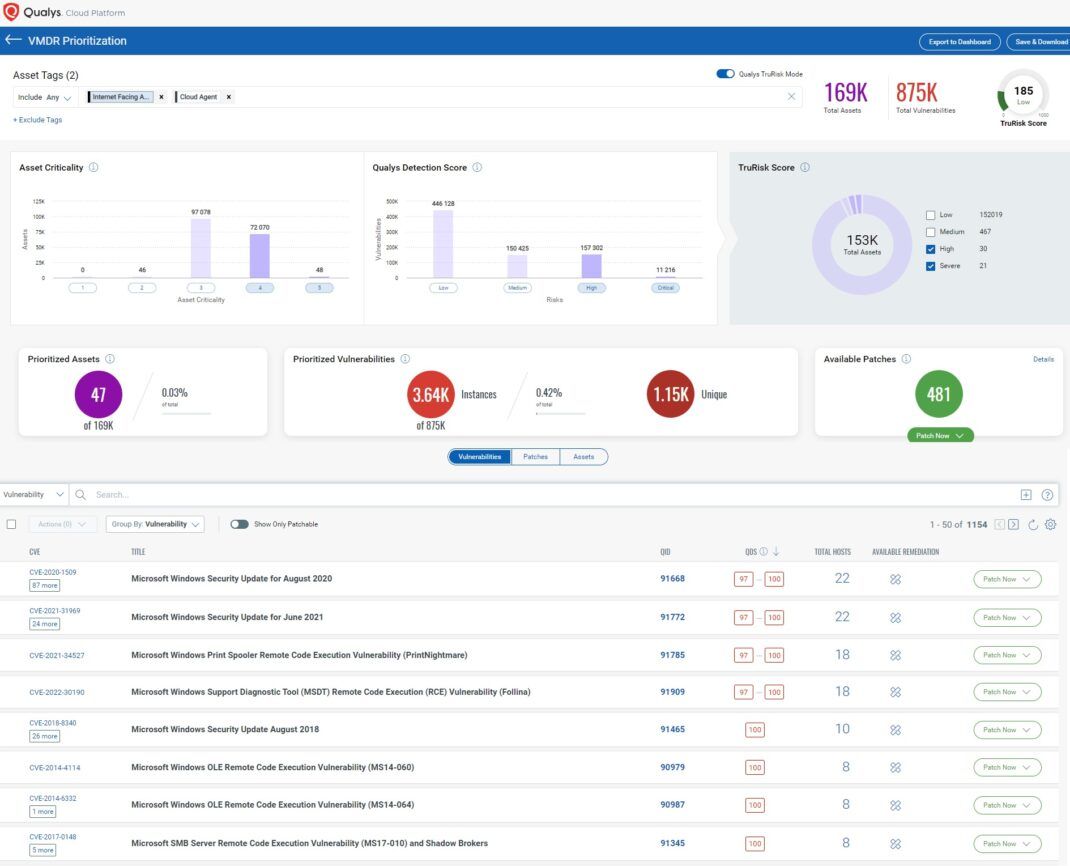
A prioritized view of risk filtered by internet-facing assets, allowing users to identify prioritized vulnerabilities, see which assets are exposed, and deploy patches with a single click.
This enhances an organization’s security posture by addressing the vulnerabilities most likely to be exploited and providing clear guidance on which patches to apply, streamlining the remediation process. Such an approach is invaluable, especially when the NVD has delays, as it ensures that organizations can continue to mitigate the most pressing threats based on the latest intelligence without having to rely solely on the NVD’s analysis.
Qualys TruRisk: Integrating risk-based vulnerability management, Qualys TruRisk offers organizations a sophisticated method to prioritize threats, which considers the
severity of vulnerabilities as influenced by a variety of factors, including the assets’ business and operational criticality, its exposure level to potential attacks, and its importance to business-critical applications.
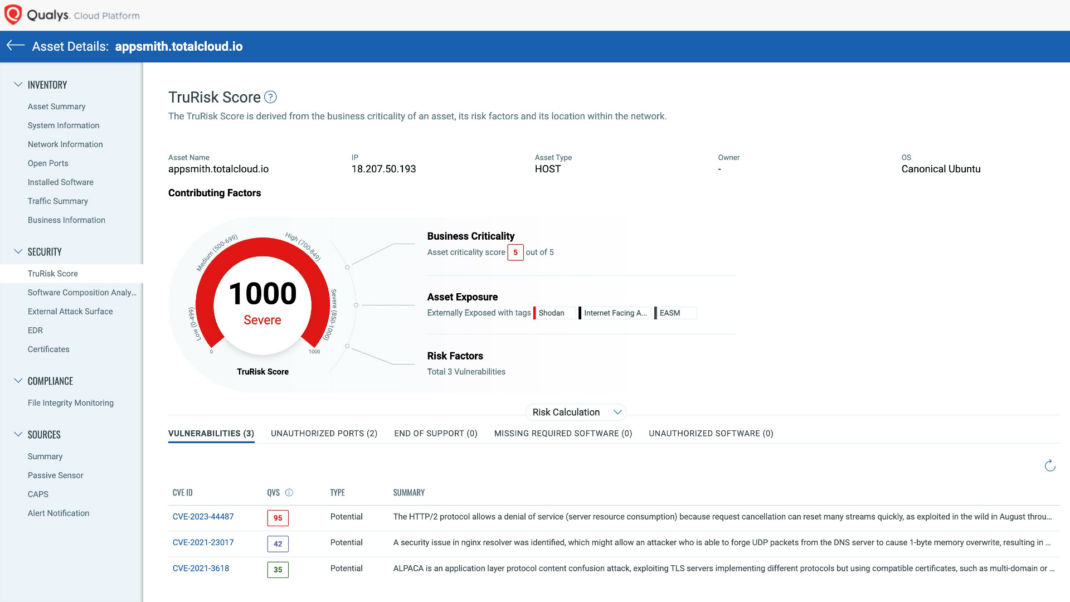
TruRisk Score of an asset, accounting for business criticality and risk factors such as vulnerabilities, exposed ports, EoS software, and missing security controls.
By providing a comprehensive view of a vulnerability’s impact on the organization, including a TruRisk Score, Qualys enables a more nuanced prioritization beyond traditional technical severity rankings. This is particularly critical in times when NVD updates are lagging, as it allows organizations to continue their vulnerability management processes based on dynamic and context-rich risk assessments. Despite 42% of CVEs lacking critical metadata such as CVSS during the NVD delays, TruRisk Scoring can still pinpoint organizational risk using business context, threat intel, and numerous other risk factors.
Conclusion
Embedding these capabilities into an organization’s cybersecurity strategy offers a proactive and informed approach to vulnerability management. The reliance on direct vendor advisories and the integration of sophisticated prioritization methodologies mean that Qualys-equipped organizations can maintain a robust defense posture, even when external databases like the NVD experience significant delays. This ensures continuous protection against emerging threats and a resilient security framework that adapts to the challenges posed by the ever-evolving landscape of cyber threats.
Contributors
- Chris McManus, Senior Product Marketing Manager
- Bill Reed, Marketing