Key Insights from the NCSC’s Vulnerability Management Guidance
Table of Contents
- Update Management and Automating for Enhanced Cybersecurity
- Asset Discovery and Vulnerability Management
- Assess, Triage, and Prioritize Vulnerabilities
- Mastering Risk, Not Avoidance: Navigating Risk Ownership
- The Art of Dynamic Vulnerability Management
- How Qualys Can Help: Unified Solutions for Enhanced Vulnerability Management and Risk Reduction
- Contributors
In a world increasingly surrounded by cyber threats, the UK’s National Cyber Security Centre (NCSC) offers vital guidance on Vulnerability Management, providing clear and actionable advice for tackling cyber threats. Their recommendations are essential for organizations to understand and mitigate vulnerabilities, from configuration flaws to software defects. This involves a systematic approach to identifying vulnerabilities, assessing exposure, and enhancing the effectiveness of software updates and security measures. The NCSC’s guidance simplifies the complex task of cyber defense, emphasizing regular updates and the importance of a proactive security posture to create a safer digital environment.
Qualys’ Threat Research Unit’s (TRU) analysis of anonymized vulnerability data underscores the importance of organizational defense strategies. In 2023, the UK’s analysis of vulnerabilities revealed that internal vulnerabilities were approximately 43.6 times more prevalent than external vulnerabilities. The data indicates that exposures linked to internal assets greatly outnumbered those associated with external assets, highlighting the critical importance of internal security measures to mitigate risks effectively.
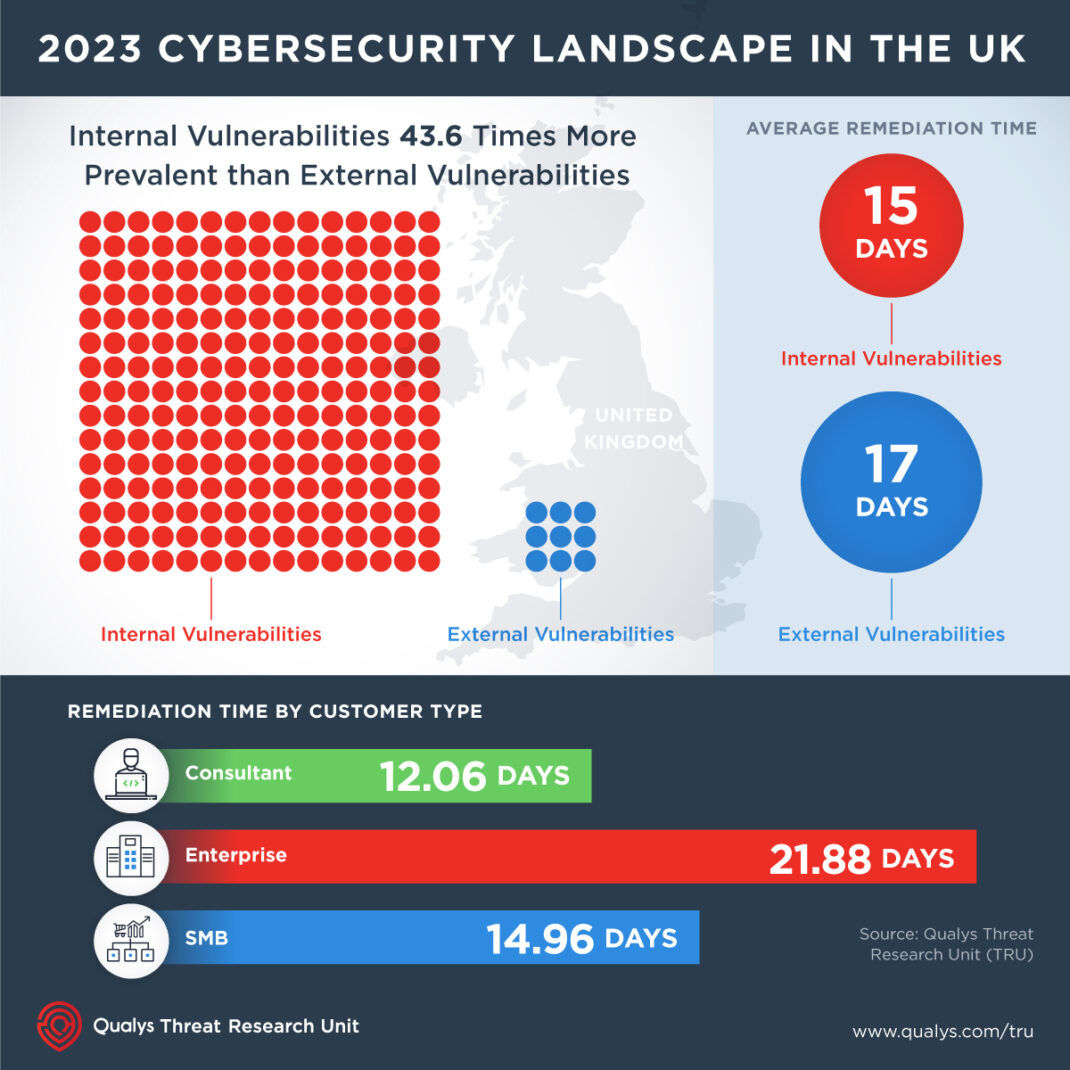
The average time to address these vulnerabilities stood at 17 days, with internal issues resolved slightly quicker at 15 days compared to 17 days for external vulnerabilities. Remediation times also varied by customer type: consultants were the quickest, patching vulnerabilities in 12.06 days, while enterprises took the longest at 21.88 days, and SMBs averaged 14.96 days.
These findings emphasize the essential nature of continuous vigilance and the integration of sophisticated technologies to effectively counter digital vulnerabilities, highlighting the necessity for prompt and effective cybersecurity measures.
This blog aims to delve into the nuances of the NCSC’s recommendations, highlighting its significance in fostering a more secure and resilient environment.
Update Management and Automating for Enhanced Cybersecurity
Updating software is fundamental to securing IT systems. Organizations should adopt a policy of updating by default and aiming for automatic and timely updates. This approach is crucial because updates can significantly mitigate security risks. Here is the highlighted guidance by the National Cyber Security Centre (NCSC):
- It is advised to install all updates promptly to avoid vulnerabilities.
- Ensuring updates from trusted sources, like vendor support websites, is essential. Verifying the hash or checksum before installation can provide additional security.
- Testing is critical; organizations should test system updates without delaying the rollout. This can be achieved through phased or canary deployment models.
- The NCSC provides timelines for different types of systems, emphasizing rapid updates to outpace attackers. These timelines vary from 5 days for internet-facing services to 14 days for internal/air-gapped systems.
- In scenarios where vulnerabilities are being actively exploited, expediting the update process is critical to protect against attacks.
The essence of effective update management lies in automating updates, ensuring they are sourced reliably, and adhering to best-practice timelines. These practices enhance security and position organizations to respond swiftly to emerging threats. By incorporating structured testing and rollout strategies, businesses can navigate the complexities of update management, ensuring their systems remain robust against vulnerabilities.
Asset Discovery and Vulnerability Management
Identifying Assets is crucial for effective vulnerability management. It involves understanding what systems and software your organization has, who is responsible for them, and identifying vulnerabilities. The NCSC emphasizes the importance of asset discovery to monitor systems, services, cloud infrastructure, mobile devices, hardware, and software and advocates for a comprehensive approach to avoid missing or conflating categories with distinct requirements.
Asset Discovery should be an ongoing process, with automation playing a pivotal role in focusing on results and supporting other cybersecurity functions, such as incident response.
In addition, managing obsolete and extended-support products is critical; migrating to a supported product is advised for outdated products, whereas extended-support products may require manual updates and do not receive fixes for all vulnerabilities. Furthermore, configuration management is essential for maintaining security and operation efficiency.
This process, combined with asset discovery and update management, provides situational awareness of all assets’ software and firmware versions.
Assess, Triage, and Prioritize Vulnerabilities
The NCSC provides comprehensive guidance on handling vulnerabilities, focusing on triage and prioritization as essential steps in the process, key takeaways include:
- There is an essential need for a comprehensive understanding of both external and internal vulnerabilities.
- Organizations should implement consistent vulnerability and configuration scanning to identify risks, including those not fixable through software updates, necessitating manual remediation.
- When updates cannot immediately address vulnerabilities, a structured process to triage and prioritize is critical.
- This involves Fixing high-priority vulnerabilities, especially those affecting internet-facing services or critical infrastructure.
- Acknowledging vulnerabilities that will not be resolved immediately, with reasons and review dates documented.
- Investigating unresolved vulnerabilities to determine the most effective solution.
- Encourages setting up channels for security researchers to report vulnerabilities, aiding in proactive security management.
Mastering Risk, Not Avoidance: Navigating Risk Ownership
The NCSC emphasizes the importance of owning the risks of not updating systems. This strategic stance on vulnerability management is not just an IT issue but a critical component of organizational risk management.
- Decisions on updates are senior-level risk decisions integral to the broader organizational risk management framework.
- Not all vulnerabilities can be addressed immediately; prioritization is based on risk assessment, not just severity scores. Consider factors like potential impact, cost, and available resources.
- Focusing on vulnerabilities that pose the most significant risk to your organization.
- Documenting decisions on vulnerability management and ensuring they are visible to senior leadership is crucial for accountability and strategic planning.
Leveraging tools that are aligned with NCSC’s recommendations, such as Qualys VMDR with TruRisk, can enhance vulnerability management by offering risk-based prioritization for more effective cybersecurity practices.
Register for our upcoming webinar, ‘Mastering NCSC Guidelines,’ on April 9th to gain comprehensive expertise in navigating and implementing the NCSC guidelines effectively.

The Art of Dynamic Vulnerability Management
The NCSC stresses the critical need for organizations to not only establish but also continuously verify and review their approaches to managing vulnerabilities. Here are the vital takeaways:
- A static vulnerability management process is a recipe for disaster. Instead, implement a dynamic process that incorporates continuous verification and improvements.
- Once addressed through reconfiguration or mitigation, ensure each identified vulnerability is verified as resolved.
- An objective assessment from third-party penetration tests can provide invaluable insights into the effectiveness of your vulnerability management process. These tests, recommended by the NCSC, help identify gaps or weaknesses that need addressing.
- The digital landscape and organizational structures are ever-changing. Regularly review your vulnerability management process to adapt to these changes, such as architectural shifts or the exposure of more services to the internet. Keeping up-to-date on new threats and vulnerabilities through security alerts from vendors and suppliers ensures your process remains current and effective.
How Qualys Can Help: Unified Solutions for Enhanced Vulnerability Management and Risk Reduction
Qualys’ product suite is perfectly tailored to meet the critical recommendations highlighted. The CyberSecurity Asset Management (CSAM) tool provides complete visibility of assets, in line with the comprehensive asset discovery advocated for. For timely software updates, Qualys Patch Management delivers an advanced automated solution. Meanwhile, Qualys VMDR streamlines discovering, assessing, and prioritizing vulnerabilities. With the addition of Qualys VMDR with TruRisk, the platform takes vulnerability management to the next level by incorporating risk-based prioritization, leading to more effective cybersecurity measures. By integrating Qualys’ unified platform, organizations can seamlessly align with best practices, significantly boosting their defense mechanisms against cyber threats.
In summary, the NCSC’s guidance on Vulnerability Management is an indispensable checklist for organizations seeking to enhance their cybersecurity measures. For a deeper understanding and to implement these critical recommendations effectively, we encourage you to review the complete guidance provided by the NCSC. Embracing these practices will strengthen your organization’s defense mechanisms and contribute to a more secure digital ecosystem.
Measure, Communicate, and Remediate According to NCSC Guidelines
Contributors
- Sandeep Potdar, Senior Director, Product Management, VMDR, Qualys
- Palmer Wallace, Senior Product Marketing Manager, Qualys