Qualys Announcing TotalCloud Attack Path, Cloud Workflow Automation, and Streamlined 3-Step User Onboarding for CNAPP

The shift of business applications and infrastructure to the cloud has heightened the need for security teams to manage cyber risks comprehensively, ensuring visibility and control across diverse cloud environments. As organizations increasingly adopt multi-cloud environments, they often find themselves grappling with a fragmented landscape of siloed, acronym-driven point solutions. This disjointed approach leaves cloud applications vulnerable to attacks while escalating security costs and complexities.
At Qualys, we are deeply committed to innovation that prioritizes our customers’ needs and experiences. Our dedication to innovation is not just a strategy; it’s a core part of our mission to deliver exceptional value and support to our users every step of the way.
We are excited to share the groundbreaking announcements made at QSC Americas and Mumbai 2024, where we unveiled a series of innovative features that will significantly enhance our customers’ cloud security programs. In response to new challenges facing our customers, we are excited to introduce three powerful new features in Qualys TotalCloud CNAPP that enhance threat analysis and context, simplify a scalable response, and accelerate time to value for our customers:
- TotalCloud Attack Path
- Cloud Workflow Automation
- Enhanced User Onboarding and UI
Identify and Break Exposure Chains With TotalCloud Attack Path Analysis
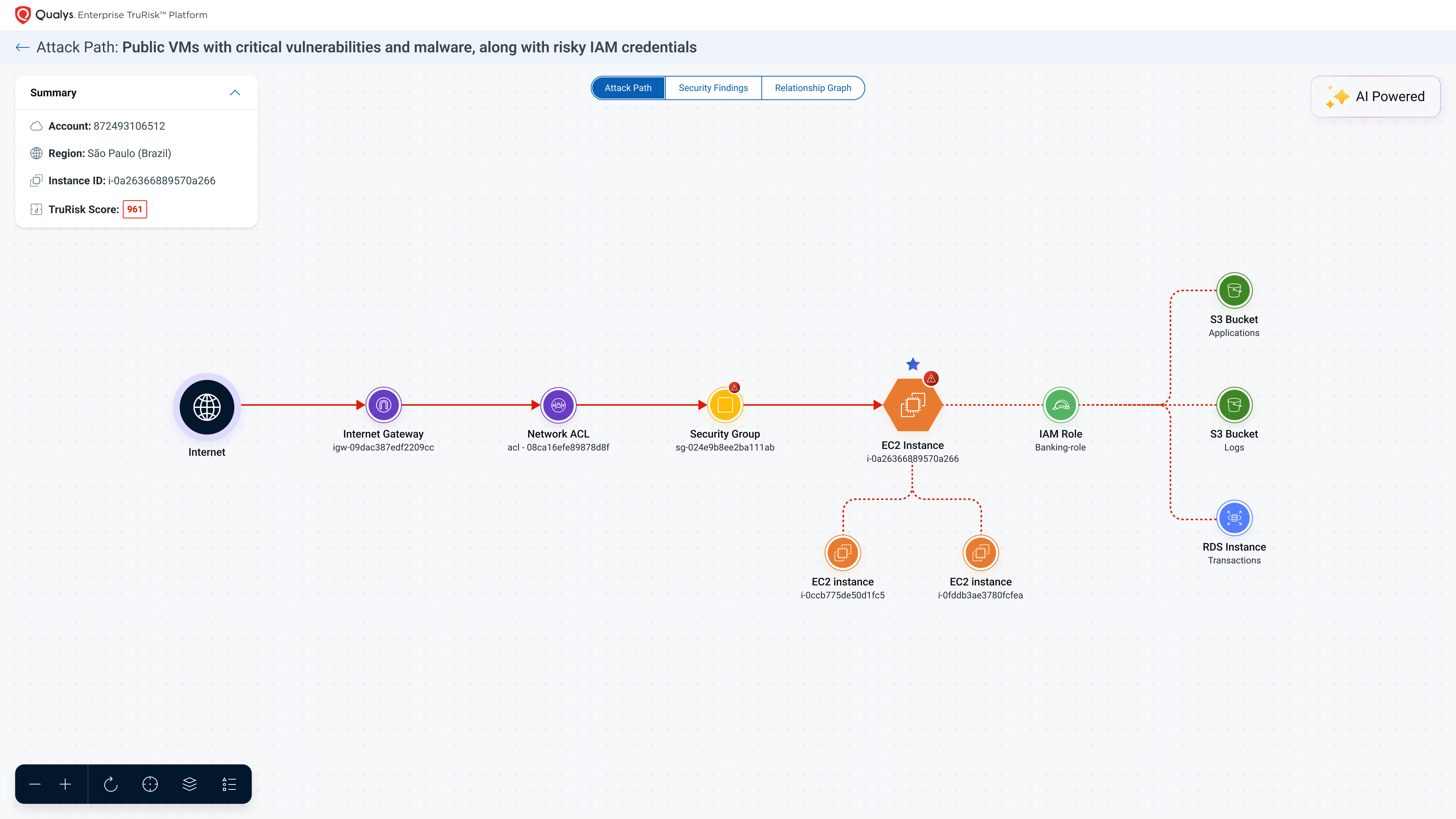
We are excited to announce the launch of TotalCloud Attack Path. This powerful new feature strengthens your cloud security strategy by enabling targeted remediation, breaking exposure chains, and prioritizing high-impact risks to stop threats in their tracks.
Even more powerful when integrated with TruRisk Insights
TruRisk Insights is a game-changing capability in Qualys TotalCloud CNAPP, designed to provide organizations with a unified and prioritized view of their cloud security landscape. By correlating risk indicators from various sources, such as misconfiguration, vulnerabilities, and threats, TruRisk Insights enables security teams to identify and focus on the most critical threats first rather than getting lost in a sea of data. For instance, it can highlight virtual machines with known exploitable vulnerabilities that are also exposed to the internet, allowing teams to take immediate action. With TruRisk Insights, organizations can make data-driven proactive decisions, streamline their threat hunting and risk remediation efforts, and significantly reduce their overall risk exposure, ensuring that they are not just patching vulnerabilities but effectively eliminating the most pressing threats to their cloud infrastructure and applications.
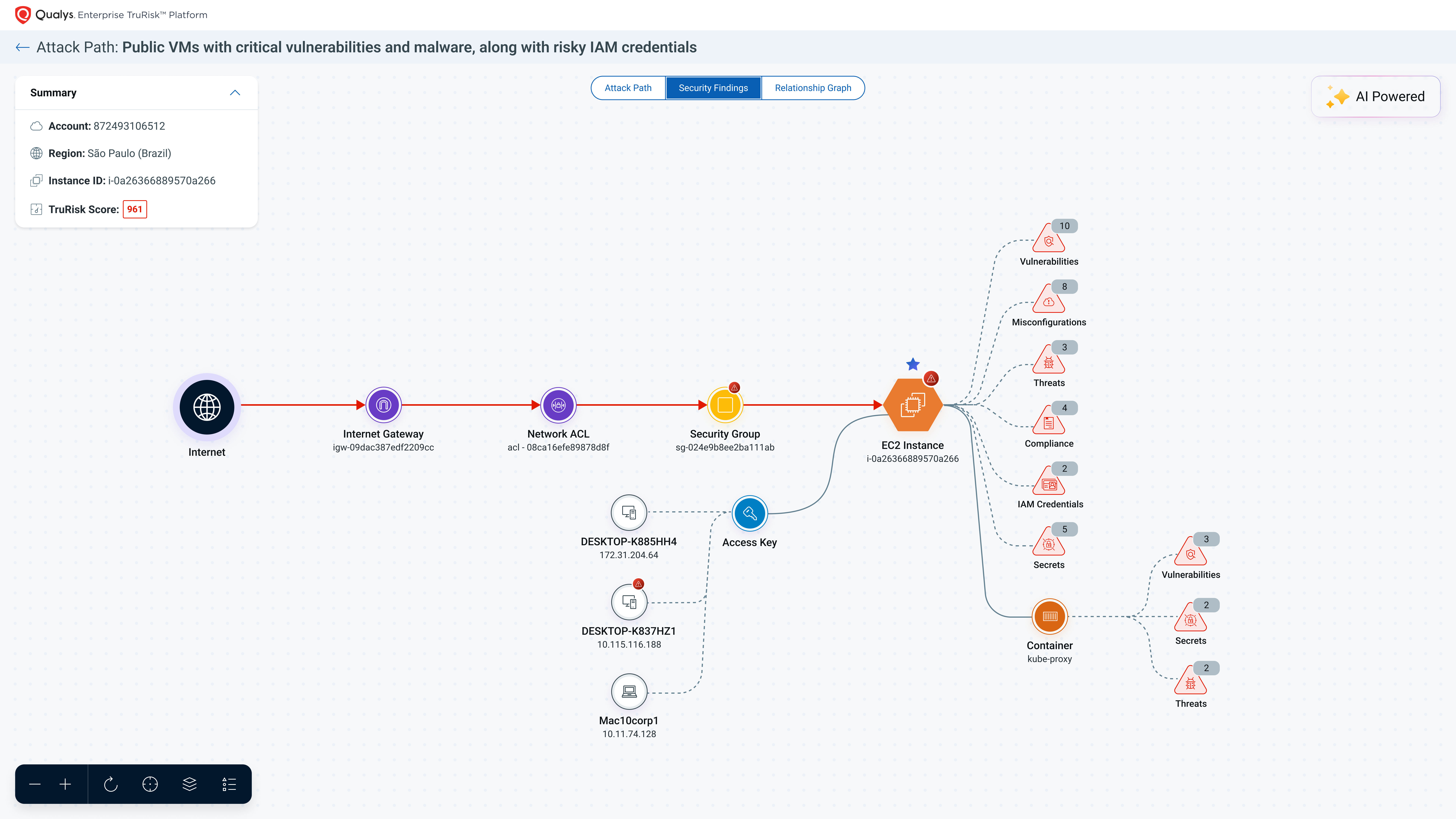
By integrating TruRisk Insights with our new TotalCloud Attack Path capability, we are significantly enhancing the ability of security analysts to respond to threats more swiftly and effectively. TruRisk Insights offers a single prioritized and comprehensive view of risk across your cloud environment, while the Attack Path feature allows teams to visualize critical resource exposure, identifying the blast radius of potential vulnerabilities. This combination enables proactive threat analysis, helping analysts pinpoint where they need to focus their efforts. With the ability to prioritize risk findings through a security graph, analysts can easily navigate to the most critical resources that require immediate attention. With this new capability, Qualys builds on its existing detection and remediation steps by mapping interconnected risks, enabling teams to apply targeted remediation across exposure chains of related vulnerabilities. As a result, organizations can scale their response efforts with rapid, risk-based prioritized threat remediation, ensuring that they address the most pressing vulnerabilities first. This synergy not only accelerates response times but also strengthens the overall cloud security posture.
Automate Security Response and Remediation With Cloud Workflow Automation
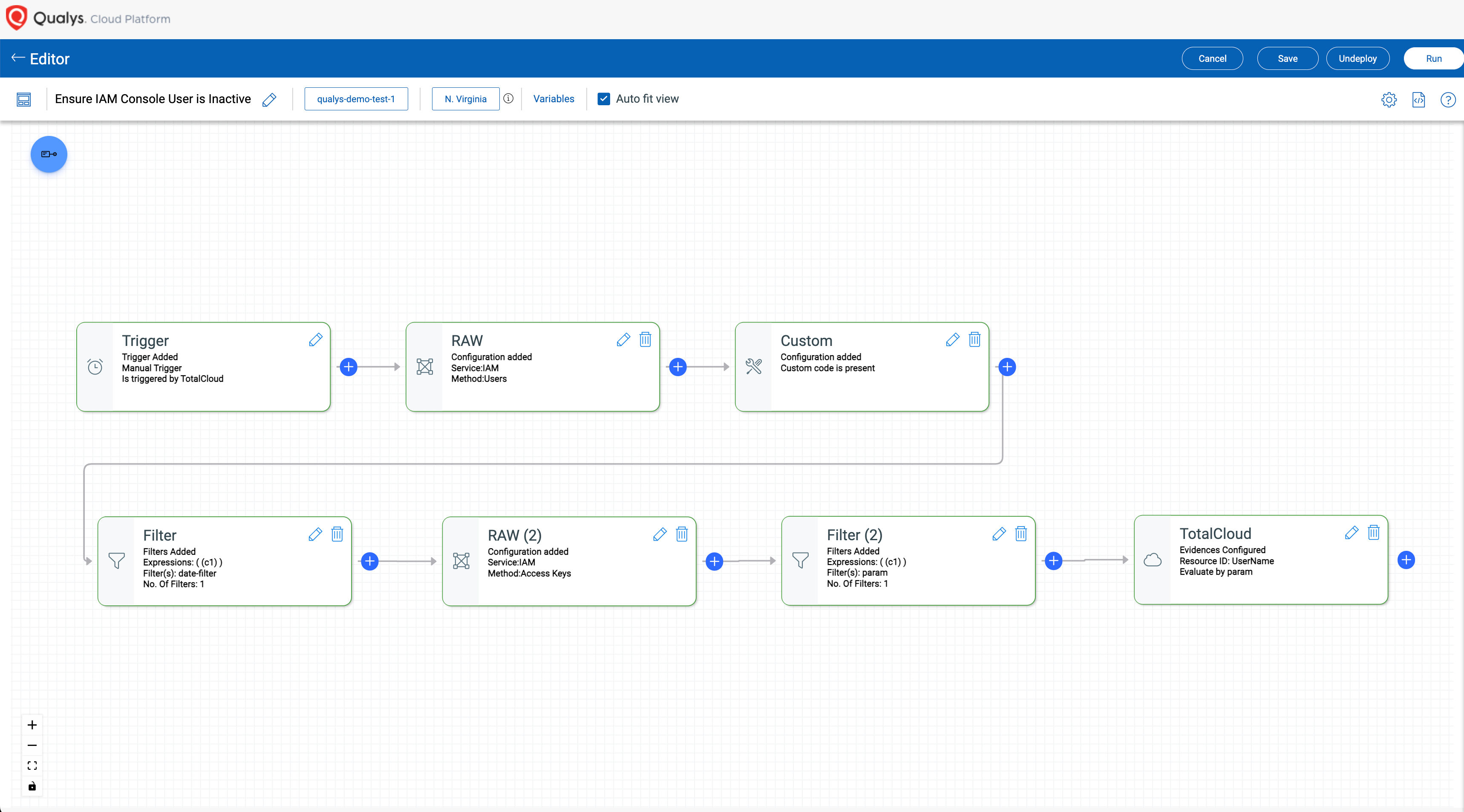
Scale security operations with Cloud Workflow Automation (CWA), enabling last-mile adaptation through custom detections, continuous data enrichment, tailored analysis, and automated responses—all within a scalable, extensible platform. This intuitive workflow builder allows users to easily construct workflows—known as QFlow Playbooks —using a drag-and-drop interface that requires no programming knowledge. With visual nodes representing various functions, security teams can quickly customize workflows to suit their specific needs, whether it’s for inventory discovery or orchestrating complex remediation tasks. With Cloud Workflow Automation (CWA), teams can adopt and customize in-platform workflows and automate routine security processes with a built-in native solution that enhances efficiency compared to the patchwork of DIY approaches. The ability to integrate seamlessly with DevOps and ITSM tools further enriches security operations, allowing for a cohesive approach to managing security programs. Some key capabilities include:
- End-to-End Orchestration: Automate the entire lifecycle of security processes, from detection to remediation, ensuring a streamlined approach to managing vulnerabilities and compliance across your cloud environment.
- Customizable QFlow Playbooks: Tailor workflows to meet specific use cases without coding skills, allowing security teams to quickly adapt to evolving threats and operational requirements.
- Integration with Third-Party Tools: Seamlessly connect with existing DevOps and IT Service Management (ITSM) tools, helping collaboration across teams and enhancing overall efficiency in incident response.
- Real-Time Monitoring and Alerts: Set up triggers for immediate notifications based on specific events, ensuring that security teams can act swiftly when potential threats are detected.
- Reusable Workflow Playbooks: Use pre-built playbooks for common security tasks, enabling rapid deployment of workflows that can be customized as needed, reducing setup time and effort.
- Scalability for Growing Environments: Easily expand workflows to accommodate new resources and services as your cloud infrastructure grows, keeping consistent security controls across all assets.
Accelerate Time to Value with an Enhanced UI and Onboarding Flow
The 3-step User Onboarding UI in TotalCloud is designed with usability at its core, providing a modern look and feel that simplifies the onboarding process for integrating their multi-cloud CSP environments. With a streamlined three-step connector onboarding process, users can quickly set up their environment without the steep learning curve often associated with complex security platforms. The guided connector deployment experience walks users through each step, ensuring they understand how to integrate their systems effectively. This value-oriented onboarding flow not only eases a smoother transition but also empowers users to leverage TotalCloud’s capabilities right from the start. Within a few minutes of setting up connectors, users can automatically see the risk and compliance dashboard with their security posture. By focusing on intuitive design and user-friendly navigation, we aim to enhance the overall experience, allowing security teams to hit the ground running and maximize their productivity without unnecessary delays. With these improvements, onboarding becomes less of a hurdle and more of an opportunity to engage users with the powerful features of TotalCloud from day one.
Sign up for a trial of Qualys TotalCloud CNAPP today.
How Qualys TotalCloud Helps You Strengthen Cloud Security
If you want to dive deeper into CNAPP, download the 2024 Gartner CNAPP Market Guide, explore more about the Qualys TotalCloud Platform, get a customized and complimentary TotalCloud TruRisk Insights report, read our FAQ, or speak to a Qualys TotalCloud CNAPP Expert.