Streamline Security: Automate Database Compliance with Qualys Cloud Agent
Compliance audit failures remain a critical challenge for organizations, particularly in database security. According to the 2024 Thales Data Threat Report, nearly 43% of companies failed at least one compliance audit in the past year. This is a significant concern because audit failures correlate strongly with security incidents—organizations that failed audits were ten times more likely to experience data breaches, with 31% of non-compliant organizations reporting breaches, compared to only 3% among those that met compliance standards. This underscores the essential role of compliance in maintaining data security as new threats evolve.
The increase in cyber threats, especially ransomware and malware, is driving up the pressure on compliance efforts. Human error is a prominent factor, contributing to a large portion of breaches and complicating the compliance landscape, necessitating robust data management and security practices.
In response, many organizations are adopting automated compliance solutions, which streamline the audit process and reduce security gaps stemming from human oversight. Automated tools enable organizations to stay audit-ready and more secure, even as regulations change and cyber threats grow more sophisticated.
Sign up for our February 27, 2025 webinar, Streamline Your Security: Automate Compliance Database Assessments with Qualys Cloud Agent.
The Importance of Database Compliance and Challenges
Database compliance has become a priority across industries in today’s data-driven world. With regulations like GDPR, PCI DSS, CIS, and HIPAA imposing stringent requirements, non-compliance poses risks such as data breaches that compromise sensitive information, substantial financial penalties that can affect the organization’s stability, and reputational damage that undermines stakeholder trust. Compliance protects sensitive data, builds customer trust, and maintains an organization’s reputation, and is increasingly vital as regulatory enforcement intensifies. This environment calls for a comprehensive approach to database security management, integrating best practices to keep data secure and compliant.
Traditional authenticated compliance scans face significant challenges despite offering advantages such as centralized management and scalability. Failing to securely share and manage credentials for database access increases the risk of unauthorized access, creating potential security vulnerabilities.
Network-based scans can consume substantial bandwidth, potentially impacting system and network performance, particularly in large environments. Authentication and authorization failures are also common, causing delays and requiring repeated attempts to access resources. These failures can slow down the scanning process and affect overall network efficiency.
Furthermore, remote scanners may struggle to detect issues hidden behind firewalls, VPNs, or complex network configurations. Together, these factors complicate the overall management of compliance scans.
Qualys Policy Compliance’s current offering provides comprehensive database compliance policy coverage and offers flexibility through various data collection sensors, such as scanners and cloud agents.
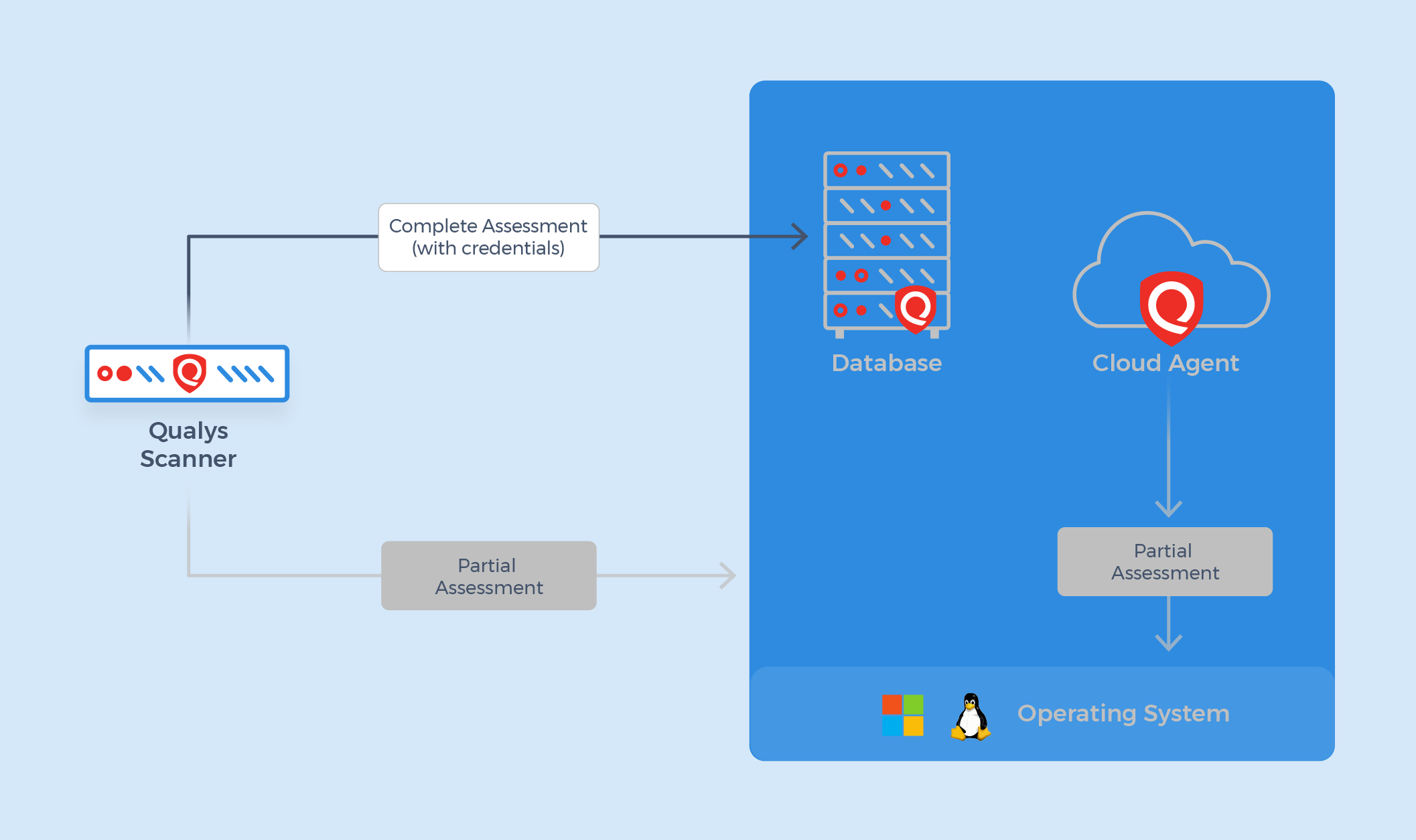
Even though Qualys Scanner encounters challenges like those associated with traditional authenticated remote scanning, it addresses many of these issues by offering long-standing support for database authentication and assessment for policy compliance. With a vast scope of supported databases, Qualys Scanner streamlines the process of scanning and assessing database environments, helping organizations ensure compliance while minimizing performance impact.
In contrast, the Qualys Cloud Agent has so far only supported OS-level database assessments. Although its scope has been more limited than the Qualys Scanner—primarily focusing on OS-AUTH level controls for specific database technologies—it offers a flexible and secure method for performing assessments, even in complex or challenging environments. There is no network impact, and it is also best suited for assets where you are unable to get credentials, see continuous authentication failures, or have servers that are sensitive to port scans.
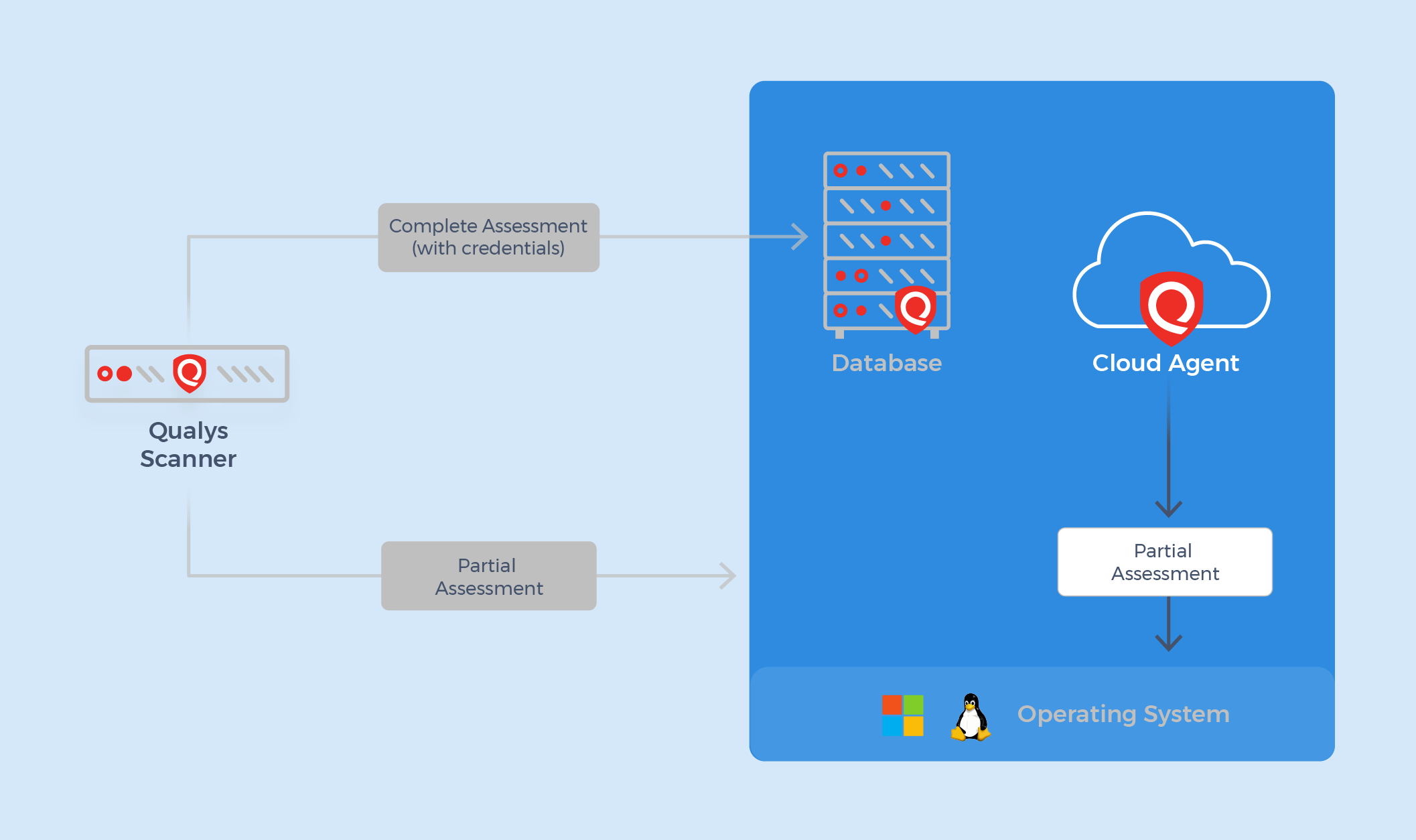
While the cloud agent has been excellent at monitoring, it previously lacked the capability to perform comprehensive database assessments due to its inability to log into databases directly.
Introducing Qualys Cloud Agent’s Database Authentication and Assessment
To address these challenges head-on, Qualys is enhancing its capabilities with the introduction of a database assessment feature using the Qualys Cloud Agent. This robust, cloud-native solution is designed to continuously monitor and assess databases for compliance with security policies, providing organizations with the tools they need to stay ahead of potential risks. With support for Oracle and MS SQL databases, Qualys Cloud Agent ensures adherence to multiple CIS, DISA, NIST, and many more benchmark policies, reinforcing a strong security posture.
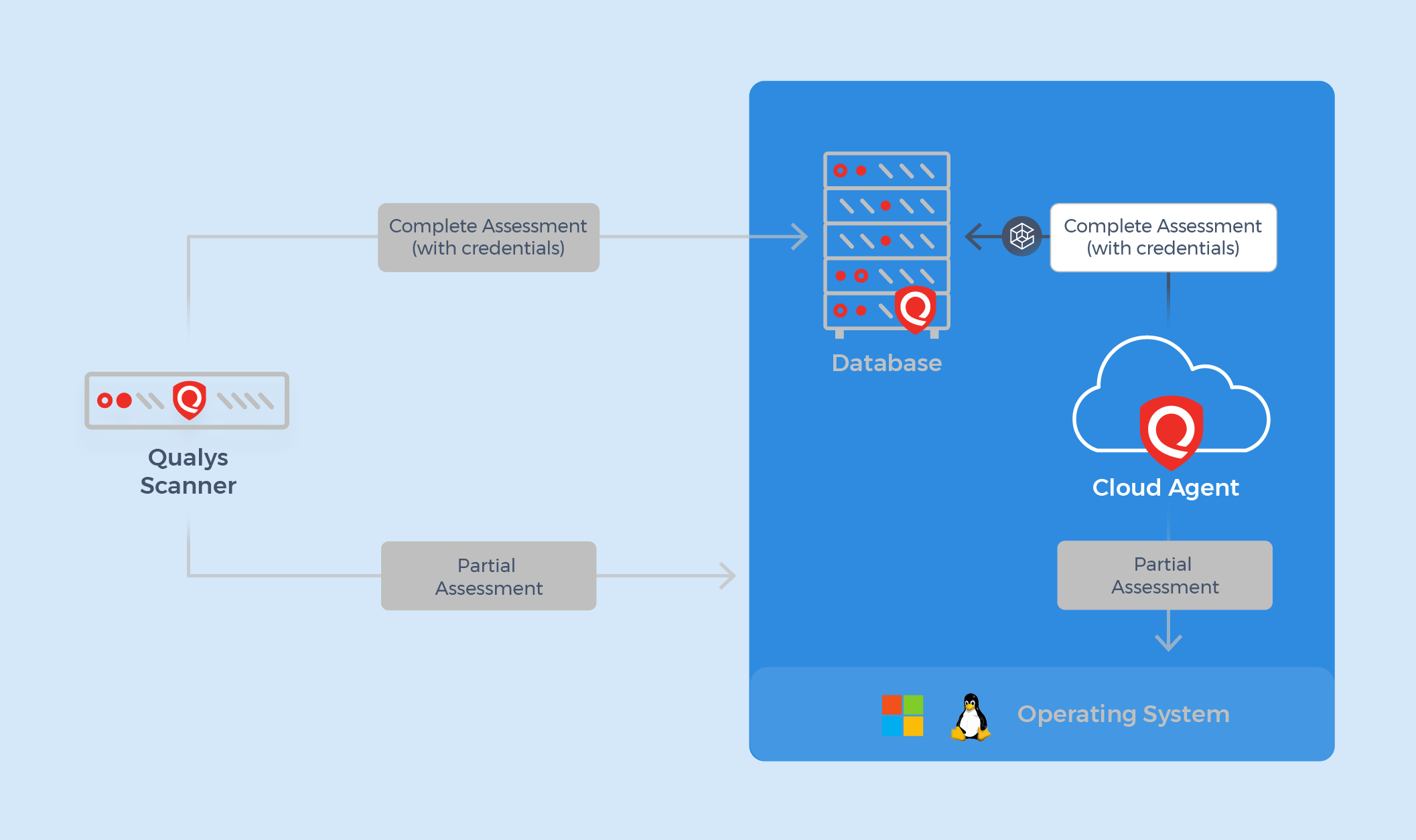
The Cloud Agent’s Database Authentication and Assessment feature enables secure, automated database assessments by connecting directly to a vault provider to retrieve credentials and authenticate databases. This approach enables organizations to streamline database security management effectively. This innovative approach not only enhances the organization’s overall security posture but also ensures compliance without the manual overhead traditionally associated with database assessments.
Key Features of Database Assessment
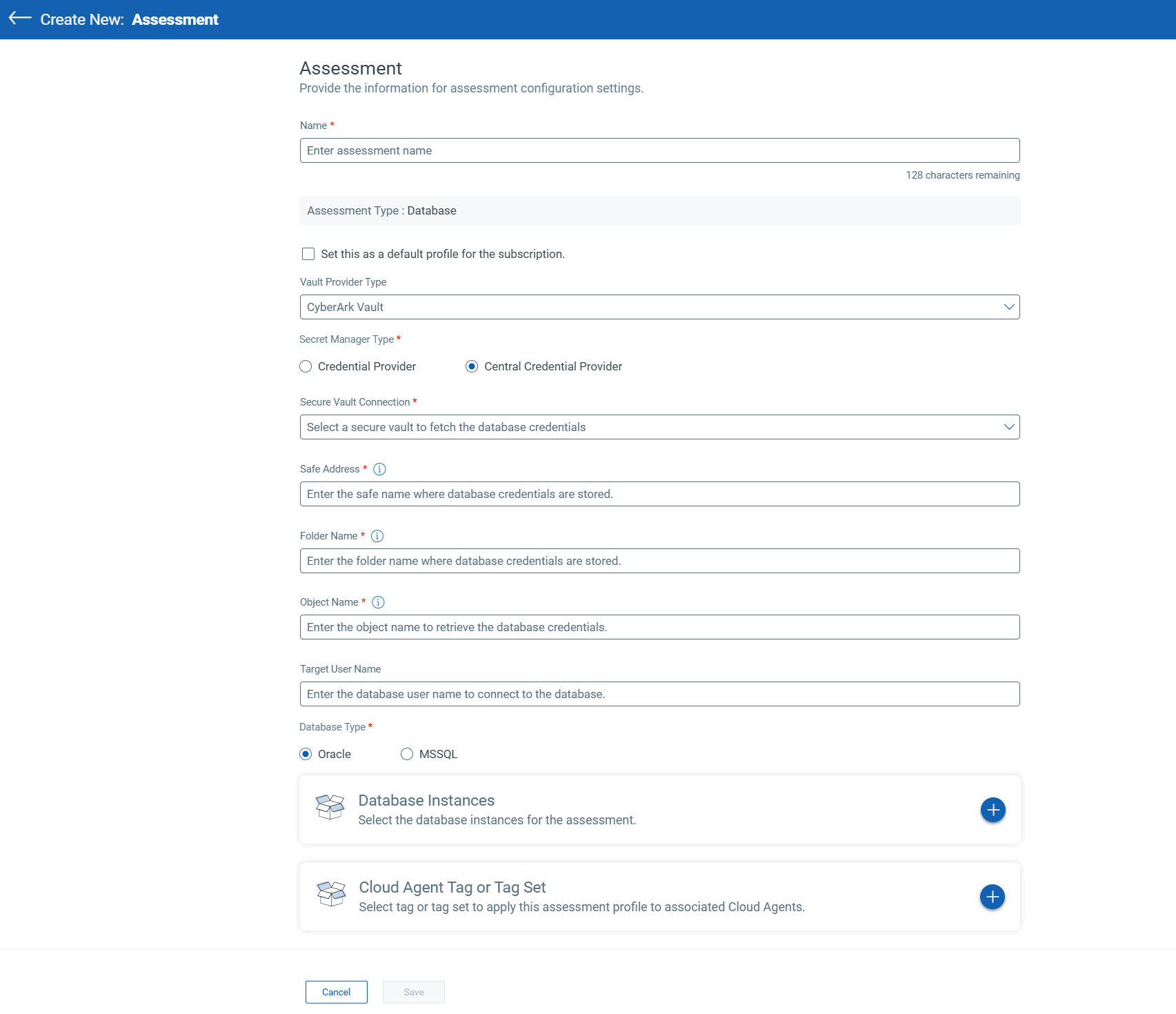
1. Vault and Secret Manager Integration: Supports integration with CyberArk Vault and different secret manager types (Credential Provider, Central Credential Provider) for secure database credential management.
2. Database Assessment Configuration: Cloud Agent connects directly to a vault provider (e.g., CyberArk Vault) to securely fetch credentials for Oracle and SQL Server database assessments.
3. Assessment Management: The Assessment tab allows creating, viewing, editing, and deleting database assessments, with options for tagging and assigning profiles.
Benefits of the Database Assessment Feature
1. Regulatory Compliance: The ability to perform policy compliance checks ensures that organizations can meet the stringent requirements of regulations like GDPR, PCI DSS, CIS, ISO, and HIPAA, thereby mitigating the risk of costly penalties.
2. Enhanced Compliance Posture: Identifying misconfigurations early allows organizations to address misconfigurations before they are exploited, improving overall security and compliance. By remediating these issues proactively, companies can reduce the risk of breaches and ensure adherence to regulatory standards, avoiding audit failures and penalties.
3. Comprehensive Assessments: The Qualys Cloud Agent performs in-depth assessments of databases, identifying compliance gaps that could pose risks to the organization.
4. Continuous Monitoring: With real-time monitoring capabilities, organizations can stay informed about their database security status and quickly address any compliance issues as they arise.
5. Automation: The Qualys Cloud Agent performs daily automated scans, eliminating the need for manual scheduling. This lets organizations reduce the time and resources required for manual checks, allowing security teams to focus on strategic initiatives rather than routine compliance tasks.
How to Get Started
By April 2025, the feature will be enabled by default for all Qualys Policy Compliance-enabled accounts. Until then, customers must contact Qualys support or the respective Technical Account Manager (TAM) to enable the feature.
Conclusion
The launch of the database assessment feature via the Qualys Cloud Agent represents a significant advancement in database security. By providing organizations with the tools to automate compliance checks and continuously monitor their databases, Qualys empowers businesses to protect their sensitive data more effectively than ever before. In an age where data breaches and regulatory penalties can have devastating consequences, the ability to ensure compliance and enhance security posture is not just beneficial—it is essential for sustained business success.
With Qualys, organizations can navigate the complexities of database security with confidence, knowing they have a powerful ally in their quest for compliance and security excellence.
Contact your TAM and Enable Today!
Current Qualys customers can contact their technical account manager (TAM) to arrange a demo and discuss how this feature can be tailored to their specific needs.