Simplifying DORA Compliance with the Qualys Enterprise TruRisk™ Platform
Strengthening Resilience for the Financial Sector
The Digital Operational Resilience Act (DORA) is a landmark EU regulation that establishes a unified framework for managing technology risk in the financial sector. It’s designed to ensure that banks, insurers, investment firms, and other financial entities can withstand, respond to, and recover from all types of ICT-related disruptions—from cyberattacks and data breaches to system outages and third-party failures.
Information and Communication Technology (ICT) refers to the systems and services—such as hardware, software, cloud platforms, and networks—that power digital finance. DORA mandates that these technologies remain secure, resilient, and recoverable to preserve operational continuity and protect customer data.
To comply, organizations need full visibility across their digital environment, the ability to respond to threats in real time, and a streamlined way to prove resilience. The Qualys Enterprise TruRisk™ Platform helps financial institutions meet these demands with integrated, automated, and risk-based security operations.
What DORA Requires – and Why It Matters
DORA sets a consistent regulatory baseline for how financial institutions manage ICT risk. Beyond compliance, it plays a critical role in strengthening financial stability, protecting consumers from ICT-related disruptions, and reinforcing customer confidence in a digitally interconnected economy. It applies to a wide range of organizations—including banks, insurers, investment firms, and payment providers—along with their critical third-party service providers.
The regulation is built around five key pillars:
- ICT Risk Management
Establish a comprehensive governance framework to identify, assess, monitor, and reduce technology risk across the organization. - ICT Incident Reporting
Detect and report ICT-related incidents rapidly and consistently, regardless of size or scope. - Digital Operational Resilience Testing
Regularly test systems and response plans to simulate disruptions like cyberattacks, service outages, or human error. - ICT Third-Party Risk Management
Assess, monitor, and control risks associated with external technology vendors and cloud service providers. - Information Sharing
Share cyber threat intelligence and incident data across institutions and regulators to improve collective resilience.
Together, these pillars reflect a shift toward continuous compliance, integrated risk management, and sector-wide accountability—placing greater pressure on organizations to demonstrate both control and agility in their operations.
Key Challenges to DORA Compliance
While DORA raises the bar for operational resilience, achieving compliance isn’t without challenges—especially for organizations with fragmented systems or limited resources.
Here are some of the most common hurdles:
- Expanding Attack Surface
Financial institutions face a growing and dynamic risk surface—spanning on-prem, cloud, and third-party environments—that’s difficult to continuously monitor and secure. - Tool and Team Silos
Disconnected security, IT, and compliance tools make it hard to gain a unified view of risk, slowing down decision-making and remediation. - Lack of Asset Visibility
Many organizations struggle to maintain a real-time inventory of all their ICT assets, including shadow IT and internet-facing systems. - Manual Compliance Burden
Preparing for audits often involves labor-intensive data gathering, evidence collection, and control mapping—diverting resources from higher-value security efforts. - Third-Party Complexity
Evaluating and managing risk across an extended network of vendors and service providers adds another layer of complexity and potential exposure.
These challenges make a strong case for an integrated, automated approach—one that continuously aligns risk, compliance, and operations.
How Qualys Supports End-to-End DORA Complianc
The Qualys Enterprise TruRisk™ Platform integrates asset visibility, risk prioritization, and policy enforcement into a single platform—available via one dashboard, with one agent, and no blind spots.
Here’s how Qualys’ capabilities map directly to DORA’s core requirements:
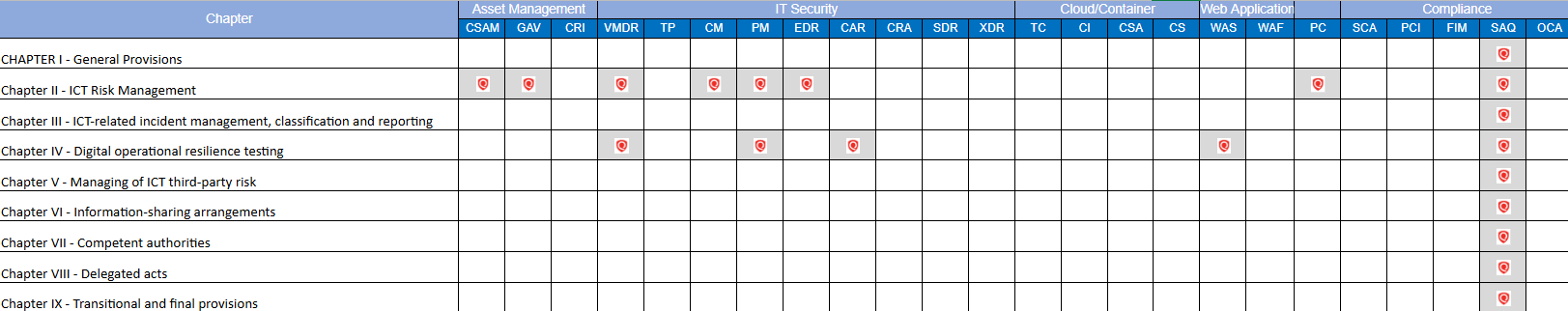
✅ ICT Risk Management & Governance
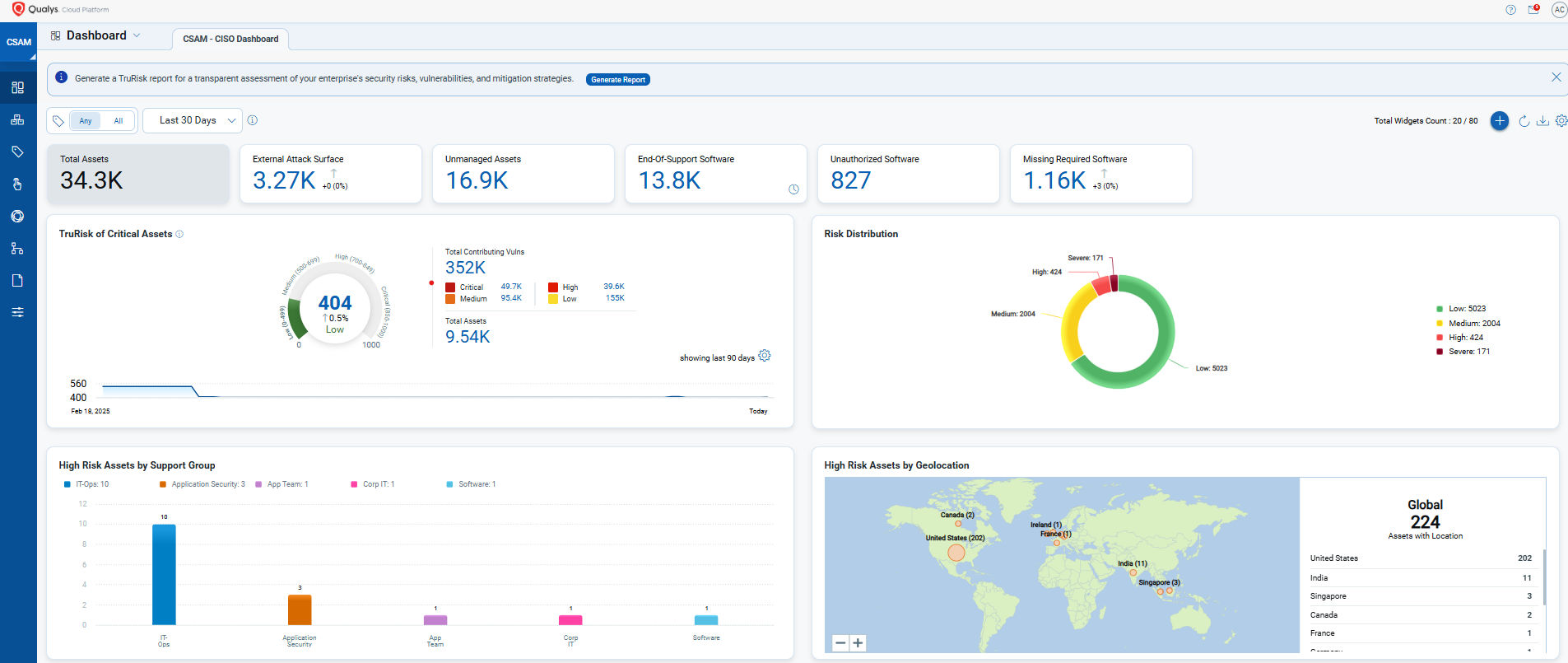
Qualys CyberSecurity Asset Management (CSAM) provides deep, continuous visibility into your entire IT environment—on-premises, in the cloud, and across hybrid infrastructures. CSAM automatically discovers and inventories all ICT assets, including shadow IT and previously unknown internet-facing systems.
With integrated External Attack Surface Management (EASM), security teams can proactively identify exposures that are visible to attackers, assess asset criticality, and continuously monitor for risk indicators—helping you stay ahead of threats before they escalate.
- Continuously discovers and classifies all hardware and software assets
- Enriches assets with lifecycle intelligence (e.g., end-of-life software, outdated firmware)
- Surfaces unknown or unmanaged assets that introduce hidden compliance risk
- Delivers business context for more effective prioritization and governance decisions
By establishing a real-time, risk-aware foundation of your ICT environment, Qualys CSAM ensures that your DORA-mandated risk management framework is always informed, complete, and actionable.
✅ Identification of Cyber Threats & Vulnerabilities
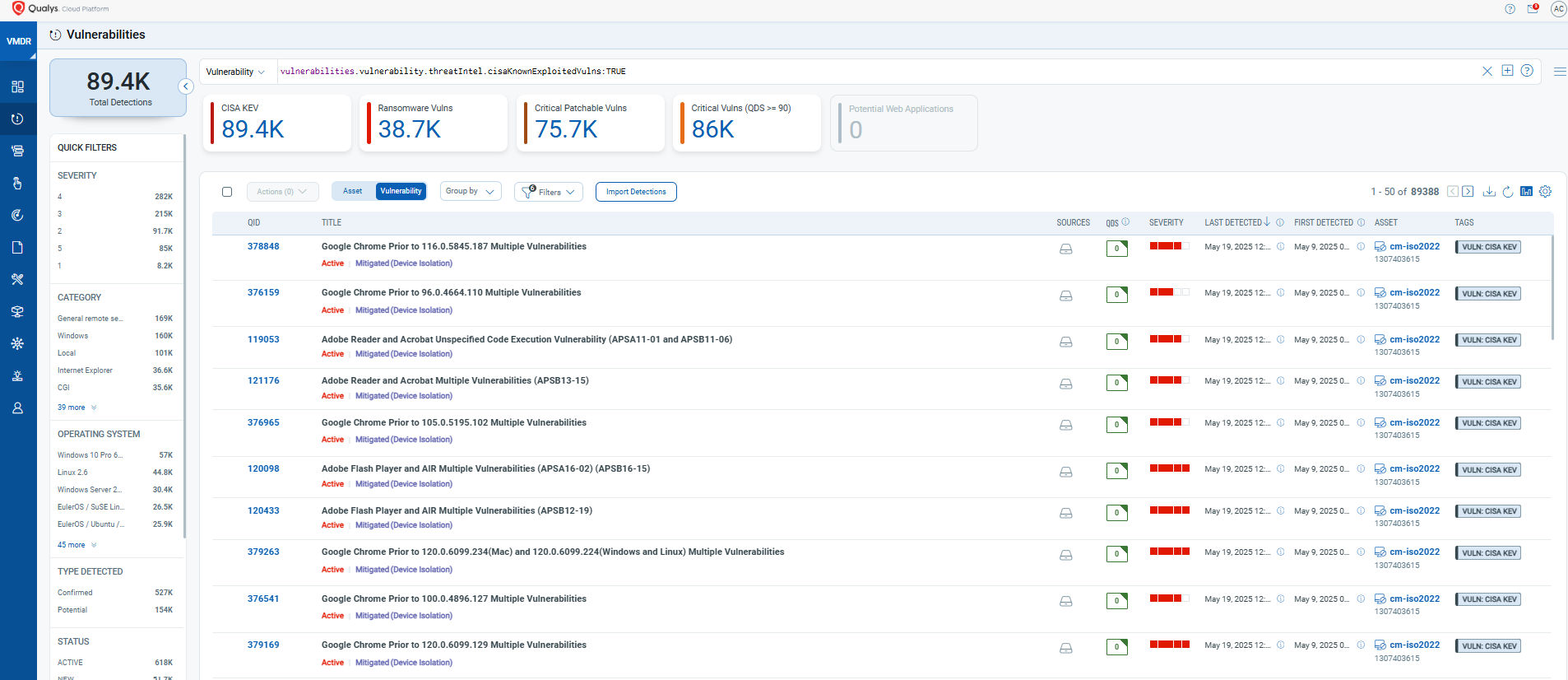
Qualys Vulnerability Management, Detection and Response (VMDR) delivers continuous, automated scanning of all ICT assets for known vulnerabilities and misconfigurations. It integrates threat intelligence, exploit data, and asset criticality to identify not just what’s exposed—but what’s actually dangerous.
At the core is Qualys TruRisk™, a unified risk-scoring engine that goes beyond CVSS to factor in exploitability, business impact, and asset context. This enables teams to focus on the vulnerabilities that pose the greatest risk to operations, not just those with the highest severity ratings.
- Continuously detects new vulnerabilities and misconfigurations across your estate
- Applies real-time threat intelligence to identify actively exploited vulnerabilities
- Prioritizes risk by exposure and impact using TruRisk scoring
- Integrates with CMDBs and remediation workflows to streamline risk response
VMDR enables financial institutions to meet DORA’s requirements for ongoing risk assessment and proactive threat management—while reducing the noise and inefficiency of legacy, severity-based approaches.
✅ Policy Enforcement & Configuration Hardening
Qualys Policy Audit is purpose-built to simplify audit readiness and streamline compliance with frameworks like DORA. It automates the continuous assessment of system configurations, identifies compliance gaps in real time, and reduces the manual effort traditionally required to prepare for audits.
Rather than relying on static checklists or point-in-time reviews, Policy Audit delivers ongoing control validation across your entire ICT environment. It highlights misconfigurations that violate policy baselines, maps them to DORA’s operational requirements, and provides clear, actionable insight into what needs to be fixed.
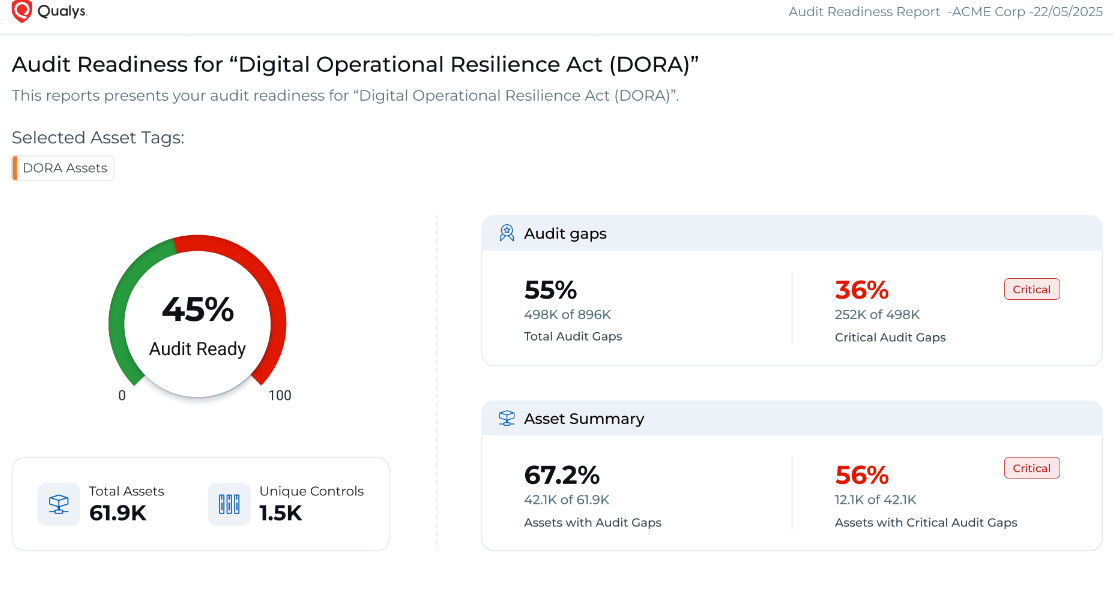
To accelerate time-to-compliance, Executive Audit Readiness Reports offer prescriptive, high-level views of your control coverage, risk areas, and audit posture—tailored for stakeholders across security, compliance, and risk teams.
- Automates configuration assessments aligned to DORA mandates
- Pinpoints and prioritizes audit gaps for faster resolution
- Reduces manual evidence collection with mandate-based reporting
Qualys Policy Audit enables financial institutions to confidently maintain continuous compliance while dramatically reducing the operational burden of meeting DORA requirements.
✅ Third-Party & Internal Risk Assessments
Qualys Security Assessment Questionnaire (SAQ) helps organizations meet DORA’s requirements for evaluating and managing ICT risk across both internal teams and third-party service providers. It automates the process of designing, distributing, and tracking risk assessments—eliminating spreadsheets, emails, and manual reviews.
With SAQ, you can issue structured questionnaires that assess vendor security controls, internal process compliance, and adherence to DORA-specific resilience requirements. Built-in workflows streamline review cycles, evidence collection, and escalation—making it easier to demonstrate diligence and accountability.
- Automates internal and third-party risk assessments at scale
- Supports custom questionnaires and out-of-the-box templates
- Enables role-based workflows with due dates, criticality scores, and evidence attachments
- Improves documentation and transparency for regulatory audits
By operationalizing the risk assessment process, Qualys SAQ helps financial institutions create a defensible, repeatable approach to evaluating ICT risk exposure—both inside and outside the organization.
✅ Detection & Incident Response
Qualys Endpoint Detection and Response (EDR), integrated with VMDR, equips financial institutions with advanced capabilities to detect and investigate cyber threats in real time. It captures rich telemetry from endpoints, correlates it with known vulnerabilities and misconfigurations, and surfaces malicious activity before it escalates.
With built-in attack context and automated threat intelligence, security teams can quickly triage events, trace root causes, and assess the scope of impact—helping fulfill DORA’s requirement for rapid incident detection and response.
- Identifies live threats across endpoints using behavioral analytics and telemetry
- Correlates attack data with asset vulnerabilities for root cause analysis
- Supports incident investigation workflows and real-time containment
- Enhances response speed and precision with integrated threat intelligence
This ensures your organization is not only aware of ICT-related incidents as they emerge, but also equipped to respond swiftly and decisively.
✅ Remediation & Recovery
Detection is only half the battle. Under DORA, financial institutions must also demonstrate that they can rapidly mitigate risk and recover from ICT-related incidents with minimal disruption.
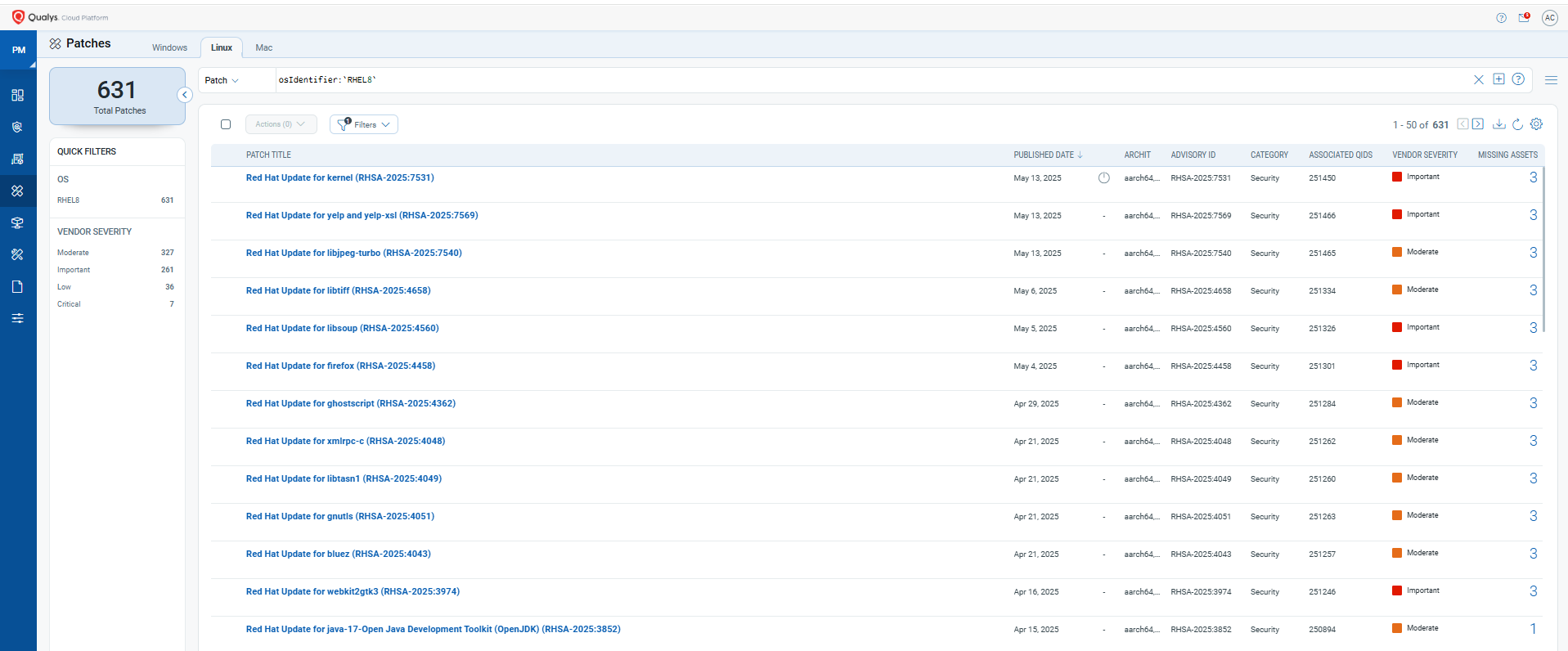
Qualys Patch Management, tightly integrated with VMDR, enables automated, scalable remediation of vulnerabilities across your environment. Once a threat is identified, the platform correlates it with the exact patches needed, creates deployment jobs, and allows for automated or policy-driven rollout—all from the same dashboard.
For compliance-related gaps, Audit Fix works in tandem with Policy Audit to resolve configuration issues that impact audit posture. It automatically generates the specific changes required to bring systems back into alignment with DORA-aligned policy baselines.
- Maps vulnerabilities to available patches for fast, targeted remediation
- Automates patch deployment across OS and third-party software
- Closes configuration compliance gaps using Audit Fix
- Reduces recovery timelines and supports continuous compliance
Together, these capabilities help organizations restore secure operations quickly—minimizing exposure, accelerating recovery, and fulfilling DORA’s expectations for timely and effective incident response.
✅ DORA-Focused Dashboards & Executive Reporting
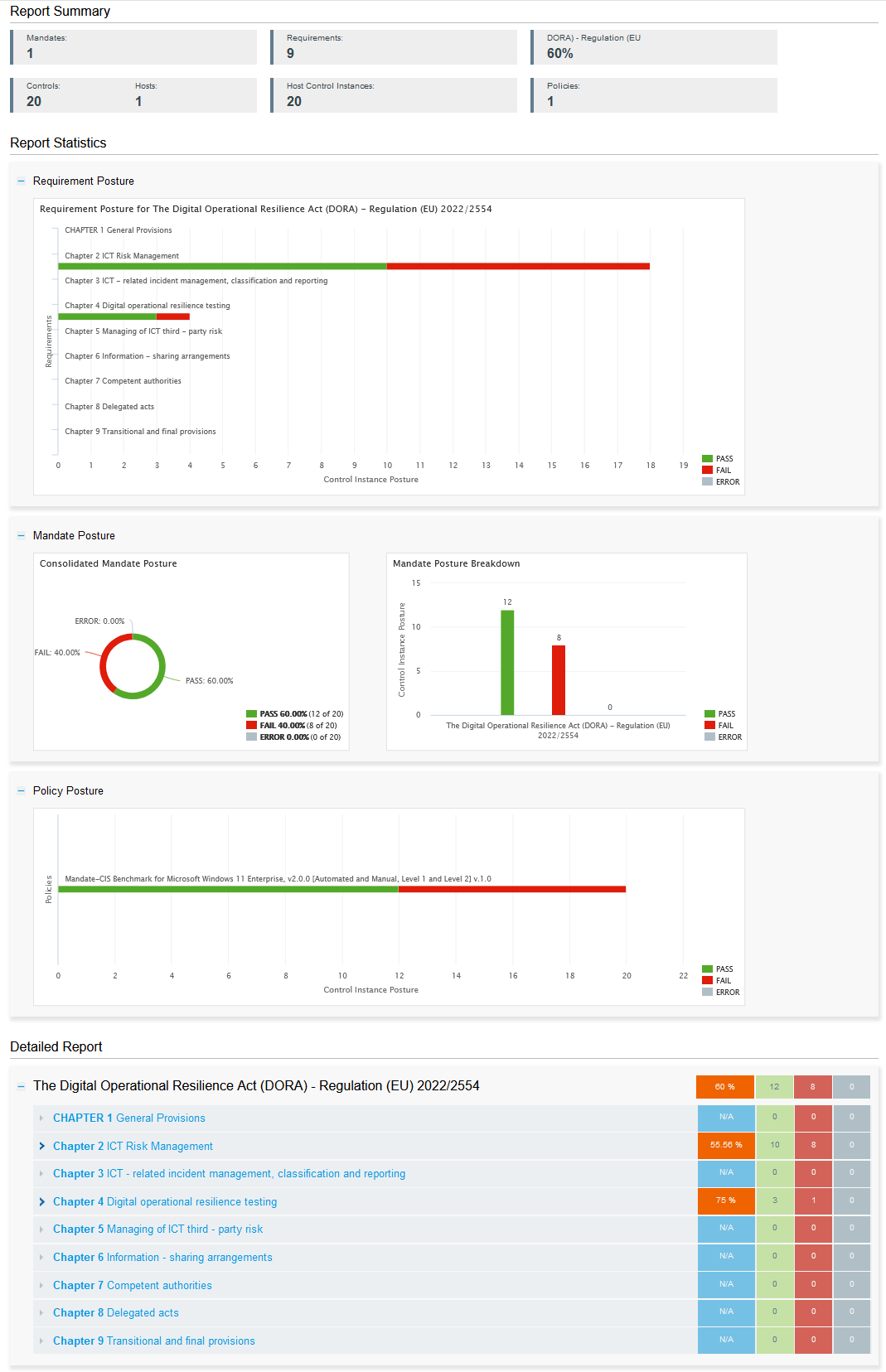
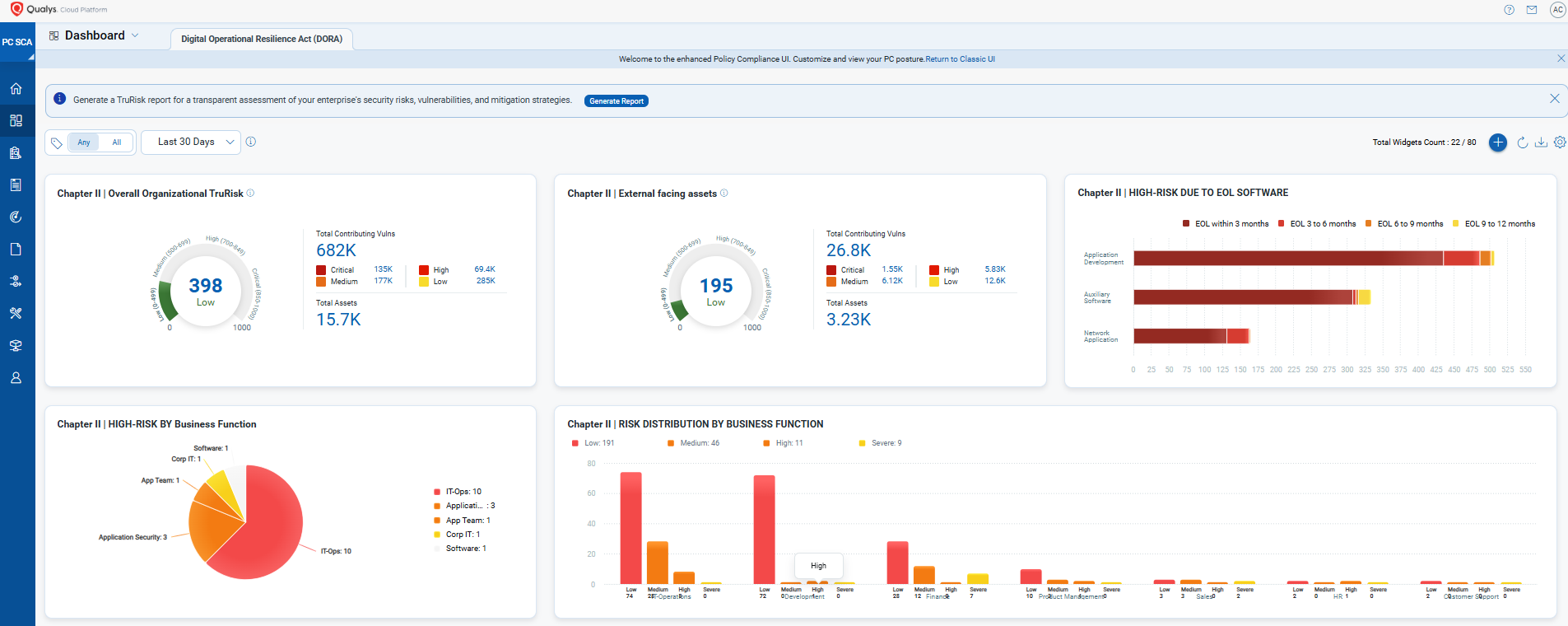
DORA demands continuous oversight, audit readiness, and clear reporting across ICT risk, compliance, and third-party exposure. Within the Qualys Enterprise TruRisk Platform, organizations can create custom DORA-focused dashboards that consolidate and visualize all relevant data in real time—spanning assets, vulnerabilities, control coverage, and remediation status.
These dashboards are fully configurable, allowing security, compliance, and risk teams to track DORA control objectives, identify gaps, and monitor trends across hybrid environments. For executive stakeholders, Executive Audit Readiness Reports translate that data into high-level, prescriptive insights that simplify decision-making and audit preparation.
- Build custom dashboards aligned to DORA’s five core pillars
- Track asset posture, vulnerabilities, misconfigurations, and third-party risk in one view
- Visualize real-time progress toward control coverage and remediation
- Generate mandate-aligned audit reports for internal and external stakeholders
By unifying risk and compliance intelligence into a DORA-specific lens, Qualys helps organizations operationalize compliance—and prove it on demand.
Why Qualys for DORA
Meeting DORA’s operational resilience standards requires more than scattered tools and manual processes—it demands a unified, intelligent platform that connects asset visibility, risk prioritization, and continuous compliance.
The Qualys Enterprise TruRisk Platform stands out by delivering all of this in one solution, designed to scale with your organization and simplify every stage of the compliance lifecycle.
With Qualys, financial institutions can:
- Reduce audit overhead through continuous control validation and automated evidence collection
- Accelerate remediation by identifying and fixing high-risk vulnerabilities and misconfigurations faster
- Consolidate tools and agents to lower complexity, costs, and operational friction
- Strengthen oversight of third parties with structured, scalable risk assessments
- Prove compliance on demand with dashboards, reporting, and mandate-aligned documentation
Whether you’re preparing for DORA enforcement or building long-term operational resilience, Qualys provides the visibility, automation, and precision you need to succeed.
Trusted for Regulated Environments
DORA is just one of many frameworks raising the bar for cyber resilience. The Qualys Enterprise TruRisk Platform is already trusted by some of the most sensitive customers around the globe—including financial institutions, government agencies, and critical infrastructure providers.
The platform is:
- FedRAMP Authorized at the Moderate impact level, meeting strict U.S. federal cybersecurity standards
- Trusted by over 70 U.S. federal agencies to secure critical systems and support continuous monitoring
- Aligned with leading global frameworks, including NIST SP 800-53, ISO/IEC 27001, CIS, and PCI DSS
- Built for Zero Trust architectures, enabling real-time, risk-based access and control across hybrid environments
With a proven foundation in high-stakes environments, Qualys delivers the visibility, automation, and trust you need to comply with DORA and beyond.
Ready for DORA. Ready for Anything.
Complying with the Digital Operational Resilience Act isn’t just about passing audits—it’s about building a stronger, more resilient organization.
The Qualys Enterprise TruRisk™ Platform equips financial institutions with the visibility, automation, and intelligence needed to meet DORA’s requirements today—and adapt to whatever comes next.
From continuous risk assessment and policy enforcement to real-time remediation and audit-ready reporting, Qualys helps you stay ahead of threats, simplify compliance, and safeguard operational continuity.
Ready to operationalize DORA compliance? Qualys is ready when you are.
Start your Policy Audit trial today to get your Executive DORA Audit Readiness report.