Building Confidence in Cyber Essentials Compliance with Qualys Policy Audit
Table of Contents
- Overview of Cyber Essentials: Requirements for IT Infrastructure
- Understanding Key Domains of the Cyber Essentials Framework
- Establishing a Baseline of Security Hygiene: What are the Key Objectives of the Cyber Essentials Framework?
- Strengthen Your Cyber Essentials Compliance with Qualys Policy Audit and SAQ
- Audit Readiness Report: Unified Visibility for Confident Cyber Essentials Compliance
- Conclusion: Start Scalable Compliance with Qualys and Cyber Essentials
In an era where cyberattacks are becoming more frequent, sophisticated, and damaging, organizations in the UK and around the world are under increasing pressure to adopt effective cybersecurity measures. Threats such as phishing, ransomware, data breaches, and supply chain compromises now target businesses of every size, often resulting in significant financial losses, legal implications, and reputational damage. In response, governments and regulatory bodies are strengthening baseline security requirements to safeguard critical digital infrastructure.
One of the UK’s leading cybersecurity initiatives in this effort is Cyber Essentials, a government-backed framework developed by the National Cyber Security Centre (NCSC) and administered by the IASME organization. Originally launched in 2014, the framework has evolved to reflect the needs of modern IT environments. Its latest version, Cyber Essentials: Requirements for IT Infrastructure, was released in April 2023 to address emerging threats and provide clearer guidance around areas like cloud security, multi-factor authentication, and secure remote work.
Overview of Cyber Essentials: Requirements for IT Infrastructure
A UK government-backed initiative intended to help organizations of all sizes strengthen their cybersecurity posture and protect against common online threats, the ‘Cyber Essentials: Requirements for IT Infrastructure’ framework outlines the key technical controls and processes organizations need to implement to meet the expected standards. The standard defines a set of five technical controls that serve as the minimum level of cybersecurity for any organization. These controls are based on real-world threat intelligence, and they target the most common attack vectors affecting UK businesses.
By aligning with Cyber Essentials, organizations can reduce their exposure to common cyber threats, demonstrate a strong baseline of cybersecurity maturity to clients and partners, meet eligibility requirements for UK government contracts, and enhance overall trust within their digital supply chain.
Understanding Key Domains of the Cyber Essentials Framework
The Cyber Essentials framework defines five critical technical control areas that every organization must address to reduce cyber risk and build a solid security foundation. These domains target the most common attack vectors and help organizations prevent unauthorized access, data loss, and malware infections.
1. Firewalls and Internet Gateways
This domain focuses on controlling the flow of data into and out of your network by using firewalls or boundary devices. Organizations must ensure that all devices connected to the internet are protected by correctly configured firewalls that block unauthorized traffic. These controls help create a secure perimeter and reduce exposure to external threats.
2. Secure Configuration
Secure configuration involves setting up hardware and software in a way that minimizes risk. This includes disabling unnecessary features, removing unused accounts or applications, and applying strong security settings. By reducing the number of potential vulnerabilities in your systems, you lower the chances of successful exploitation by attackers.
3. User Access Control
This domain ensures that users have the minimum level of access necessary to perform their roles. It requires unique user accounts, role-based permissions, and the enforcement of multi-factor authentication (MFA) for admin and cloud accounts. Strong access control helps prevent unauthorized access to sensitive data and systems.
4. Malware Protection
Malware protection aims to detect and block malicious software from infecting devices. Organizations must use up-to-date antivirus or anti-malware tools, or implement secure application configurations that limit software installations to trusted sources. These controls protect against ransomware, viruses, and other harmful code.
5. Security Update Management
Keeping systems up to date is essential for closing known security gaps. This domain requires all devices and software to be updated with critical patches within 14 days of release. Prompt patching ensures vulnerabilities are addressed before attackers can exploit them.
In a threat landscape that moves fast and hits hard, security can’t afford to be vague. The five Cyber Essentials domains bring focus and clarity to what matters most: securing configurations, controlling access, blocking malware, staying up to date, and managing the network edge. These are the frontline defenses that stop everyday threats before they escalate. For organizations aiming to reduce risk with purpose, this is the starting point for lasting security.
Establishing a Baseline of Security Hygiene: What are the Key Objectives of the Cyber Essentials Framework?
Cyber Essentials addresses a recurring issue in security: the failure to execute on fundamentals. Organizations often struggle with basic security hygiene, while misconfigured systems, unpatched software, and unmanaged access remain common causes of breaches. In the face of these challenges, the framework signals a maturity shift, one that prioritizes accountability, measurability, and adaptability in modern hybrid environments. From securing cloud assets to managing remote endpoints, Cyber Essentials’ evolution reflects the operational realities of contemporary IT.
This section unpacks the framework’s core objectives and practical impacts, providing a baseline for organizations aiming to reduce risk exposure while aligning with recognized standards of due diligence.
- Protect Against Common Cyber Threats
The framework focuses on mitigating the most prevalent threats, including phishing, malware, ransomware, and unauthorized access. By implementing the five mandated technical controls, organizations can significantly reduce their attack surface and overall risk exposure. - Extend Security to Cloud and Hybrid Environments
As organizations increasingly rely on cloud platforms and remote workforces, the framework includes explicit requirements for securing Software-as-a-Service (SaaS) applications, cloud storage, and Infrastructure-as-a-Service (IaaS). It ensures consistent security practices regardless of where data or systems are hosted. - Enforce Strong Access and Identity Management
The updated mandate requires stricter enforcement of least privilege access, role-based permissions, and mandatory multi-factor authentication (MFA) for administrator and cloud-based accounts. This helps prevent unauthorized access due to stolen or weak credentials. - Promote Secure Configuration of Systems and Devices
Systems must be configured using the industry’s best practices to minimize vulnerabilities. This includes disabling unnecessary features, removing unused accounts, and applying system hardening principles to all endpoints, including those used for remote work. - Require Ongoing Patch and Update Management
The framework enforces the timely application of critical software updates within 14 days of release. This reduces the window of opportunity for attackers to exploit known vulnerabilities in operating systems, firmware, and applications. - Cover Home and Mobile Work Environments
Recognizing the shift toward flexible work, the framework requires that personal and mobile devices used for work purposes meet the same baseline security requirements as corporate-owned equipment. - Enable Demonstrable Compliance for Regulatory and Contractual Needs
For many organizations, especially those working with the UK government, Cyber Essentials certification is a contractual obligation. Meeting the requirements provides assurance to regulators, partners, and customers that the organization takes cybersecurity seriously and is actively managing cyber risk.
For all its simplicity, the Cyber Essentials framework anchors a larger conversation around operational resilience and stakeholder trust. Its true value lies not in regulatory alignment alone but in its ability to catalyze broader cultural and technical shifts, from reactive defense to proactive governance. By embedding clear security expectations into daily operations, it creates shared accountability across technical and business domains. Whether pursuing formal certification or simply adopting its controls as baseline best practice, Cyber Essentials offers a credible pathway to strengthening cyber hygiene, one that is both accessible and impactful across sectors and scales.
Strengthen Your Cyber Essentials Compliance with Qualys Policy Audit and SAQ
Staying compliant with the “Cyber Essentials: Requirements for IT Infrastructure” doesn’t have to be overwhelming or complex, especially when you can leverage a solution designed to unify control monitoring, simplify evidence collection, and provide continuous assurance across diverse environments.
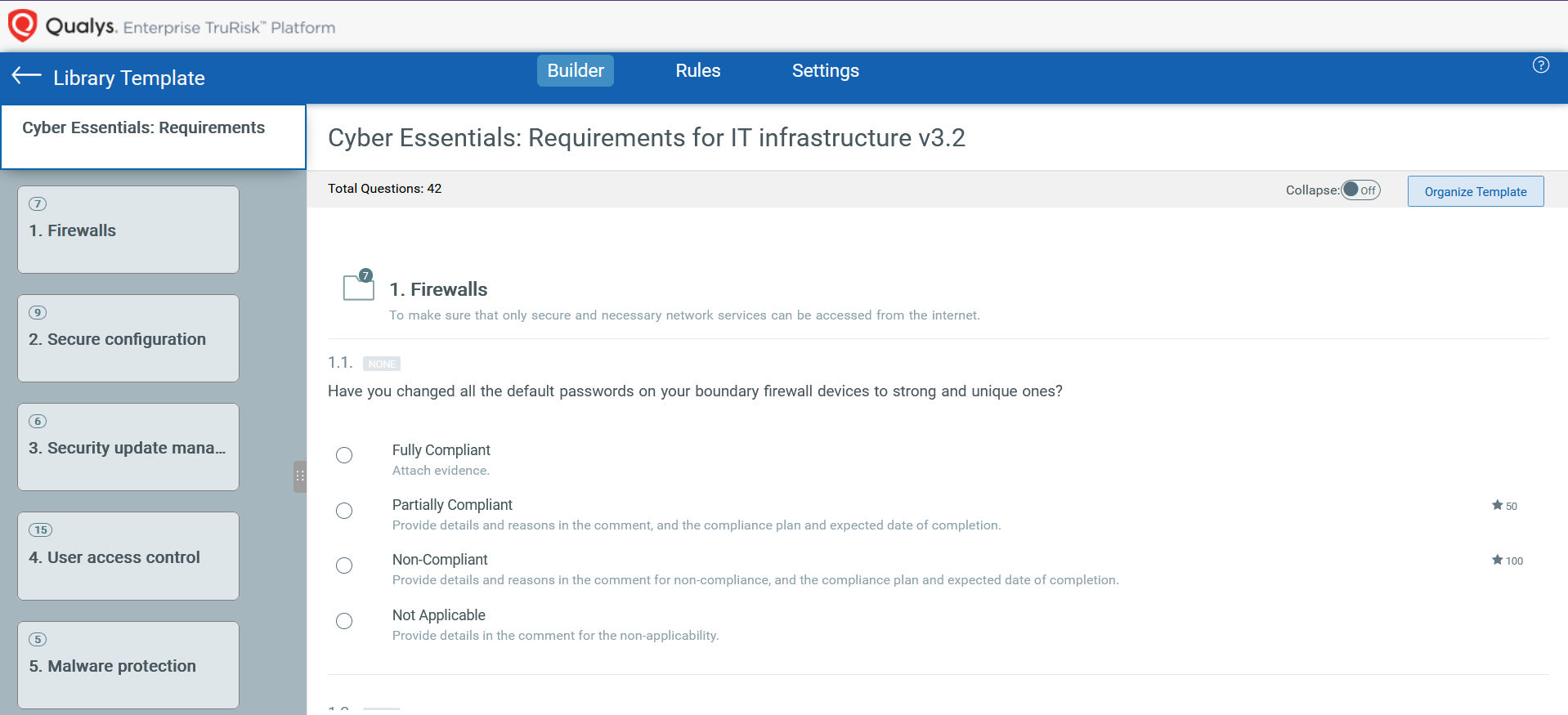
Qualys Policy Audit helps organizations operationalize the Cyber Essentials framework and enables them to achieve and sustain compliance by automating the assessment of required controls and validating system configurations against its defined benchmarks. It streamlines evidence collection, highlights control gaps in real time, and enables teams to operationalize security hygiene, strengthening both compliance and overall cyber resilience.
With Qualys Policy Audit, organizations can keep a real-time pulse on their compliance posture. The platform not only tracks how well systems align with the Cyber Essentials requirements but also provides in-depth, audit-ready reports and practical insights into both technical setups and procedural controls. This level of visibility makes it much easier to spot gaps, take corrective action quickly, and stay aligned with government-backed cybersecurity best practices—all from one centralized platform.
Qualys delivers a robust library of over 1200 pre-built policies, 100 regulatory standards, and more than 25,000 technical controls, spanning across 490+ technologies, including operating systems, databases, cloud platforms, firewalls, network infrastructure, and web applications. While the Cyber Essentials framework emphasizes key technical areas, such as secure configuration, patch management, access control, and malware protection, it also underscores the importance of clearly defined procedures and effective governance. Addressing both aspects is essential for a well-rounded and resilient cybersecurity strategy.
To address the non-technical aspects of the Cyber Essentials framework, organizations can leverage the Qualys Security Assessment Questionnaire (SAQ) application. SAQ allows teams to design and distribute customizable questionnaires that evaluate key areas such as user awareness, third-party risk, and data handling practices. These structured assessments provide the necessary documentation and insight to demonstrate alignment with Cyber Essentials requirements, supporting a more complete and defensible compliance posture.
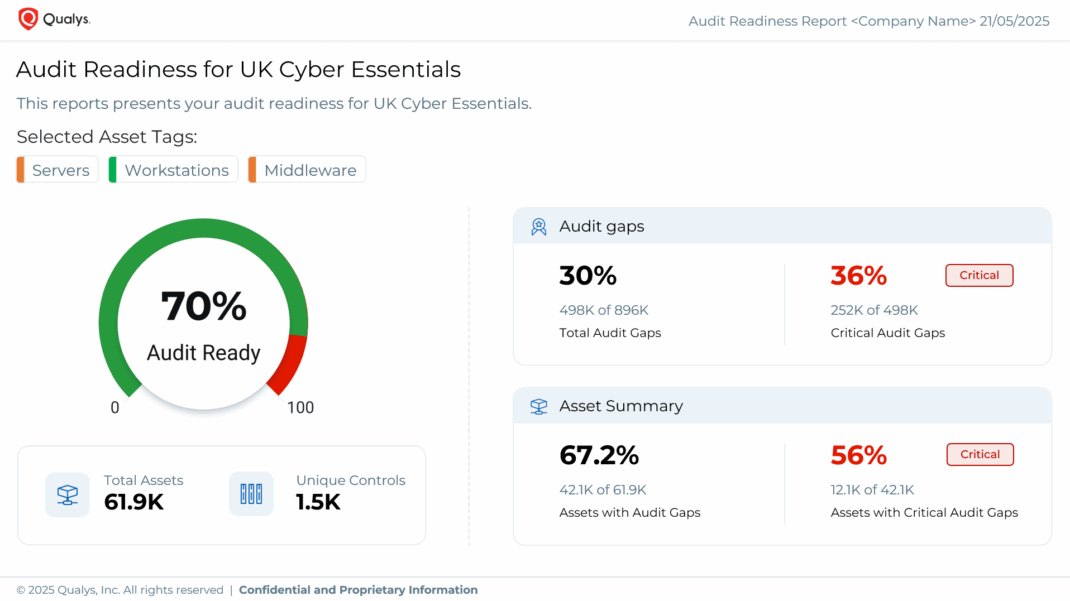
Audit Readiness Report: Unified Visibility for Confident Cyber Essentials Compliance
Effective compliance is not just about passing an audit but also about maintaining a defensible, transparent security posture that withstands scrutiny. To achieve this, organizations need real-time clarity into how well their systems, controls, and policies align with established frameworks like Cyber Essentials.
The Audit Readiness Report plays a central role in this effort. The purpose of the Audit Readiness Report is to present a clear, structured overview of the organization’s current security and audit posture in relation to the selected compliance framework. It highlights the organization’s alignment with compliance requirements, security controls, and policies, while also identifying areas for improvement. Each section distills complex data into actionable insights summarizing key findings, audit insights, metrics, and targeted recommendations to help teams prioritize remediation and prepare confidently for formal certification or internal assessments.
When combined with the Qualys Policy Audit and the Security Assessment Questionnaire (SAQ), through the Qualys Enterprise TruRisk™ Platform, this reporting capability delivers a comprehensive, integrated approach to Cyber Essentials compliance. Together, Qualys Policy Audit and SAQ deliver continuous validation of both technical and procedural controls, while consolidating compliance evidence and risk insights in a single, scalable platform.
This unified approach helps reduce the overhead of manual audit preparation, shorten response times to emerging compliance gaps, and ensure alignment with Cyber Essentials even as requirements evolve. Essentially, it automates control validation, simplifies documentation, and consolidates risk intelligence within a single platform, making compliance more manageable and actionable.
Conclusion: Start Scalable Compliance with Qualys and Cyber Essentials
Cyber Essentials offers a structured benchmark for foundational security, but sustaining that benchmark requires more than periodic reviews or siloed reporting. It calls for integrated oversight, audit discipline, and the ability to align both technical and procedural controls at scale.
Qualys brings over 25 years of experience in helping organizations translate regulatory requirements into operational security. Through the Enterprise TruRisk™ Platform and Policy Audit, Qualys combines automated policy evaluation, tailored control mapping, and centralized evidence management to support a consistent and efficient approach to Cyber Essentials.
This integrated model streamlines internal review processes and equips teams with the clarity and context needed to address control gaps, validate improvements, and meet external requirements with confidence without disrupting day-to-day operations.
Excited to assess the audit readiness of your organization? Kick off your free Policy Audit trial now.