Eliminate Risk with Precision: Introducing Vulnerability Detection Sources in VMDR
In the race against cyber threats, finding vulnerabilities is no longer enough. True security comes from understanding them—where they exist, how they were discovered, and what risks they pose. One of the most overlooked aspects in vulnerability management is knowing the source of detection. Without it, organizations may waste valuable time chasing the wrong threats while leaving real risks unaddressed.
To solve this challenge, Qualys VMDR now offers Vulnerability Detection Sources—a feature designed to eliminate confusion and help organizations take precise, impactful action.
Why Knowing the Source Matters
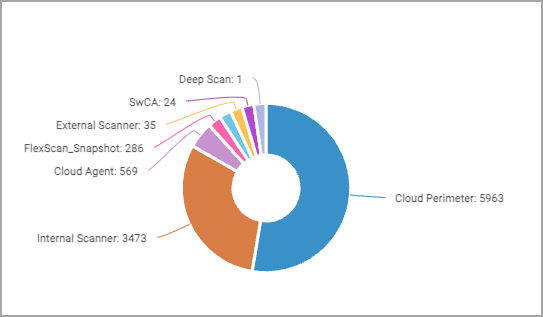
Imagine you’re scanning your cloud virtual machines with agents while also running external perimeter scans. Vulnerabilities begin to appear. But where did they come from? Were they discovered from within your infrastructure or from an external scan?
Without this clarity, it’s difficult to:
- Understand the context of a vulnerability
- Prioritize the right remediation efforts
- Apply the appropriate security controls
This lack of insight creates delays, misdirected actions, and ultimately, unnecessary risk.
That’s where Vulnerability Detection Sources come in.
Powered by TruRisk™: Prioritize External Threats with Greater Precision
Detection source visibility is now directly integrated into your TruRisk™ Score to enable smarter risk prioritization. External exposures often present a greater threat surface and require faster remediation. That’s why:
When a vulnerability is detected on an externally exposed asset, TruRisk automatically increases its score by 20%.
This dynamic adjustment ensures that vulnerabilities facing the public internet are escalated with urgency, empowering your team to focus first on the risks that matter most.
What Are Vulnerability Detection Sources?
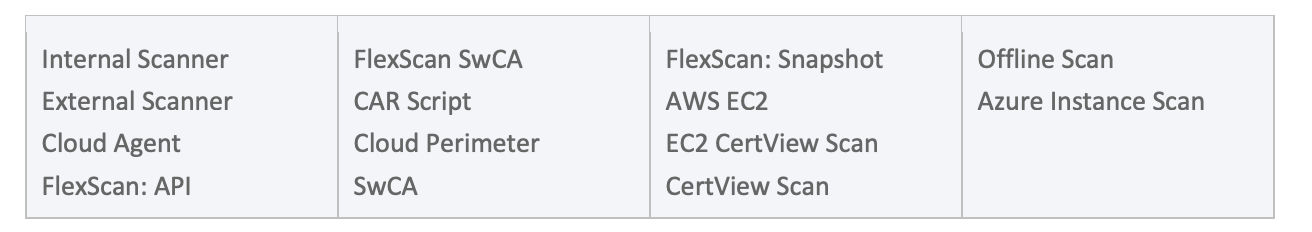
This feature in VMDR identifies exactly where each vulnerability was detected—whether through Cloud Agent, perimeter scans, internal scanners, or one of many supported methods. By revealing the detection source, security teams can:
- Identify the root cause of the vulnerability
- Take targeted action based on where the vulnerability exists
- Accelerate remediation efforts
- Reduce the attack surface and proactively eliminate risk
Supported Sensor Types Include:
How It Works: Better Visibility, Better Decisions
Once enabled, the detection source information becomes visible from the next scan onward (note: not retroactive). Here’s how it helps:
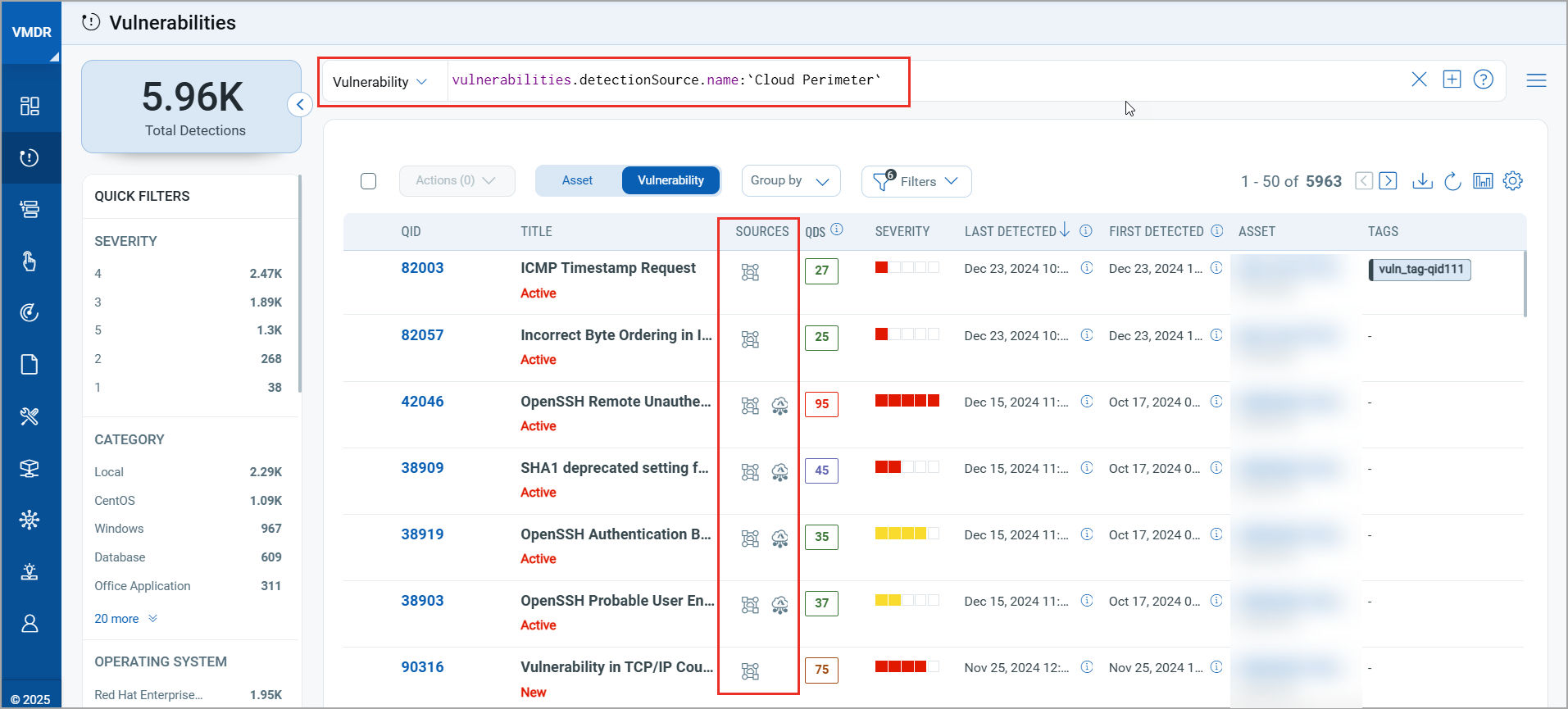
1. Enhanced Vulnerability Listings
A new “Sources” column now appears in the Vulnerabilities page, letting you hover for detection details, including:
- Source name(s)
- First detected date
- Last detected date
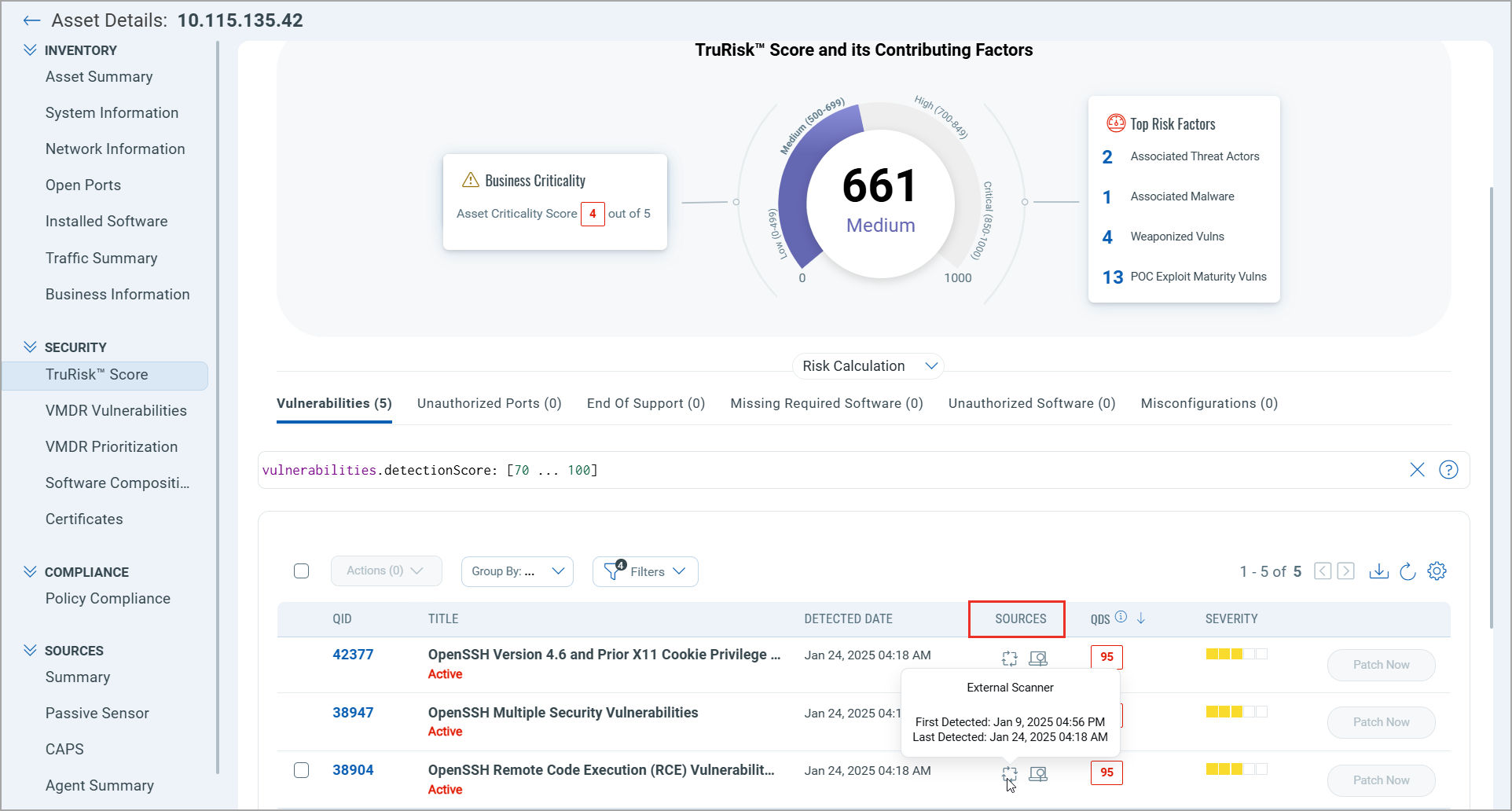
You’ll also find this information integrated into the TruRisk™ Score page for deeper context.
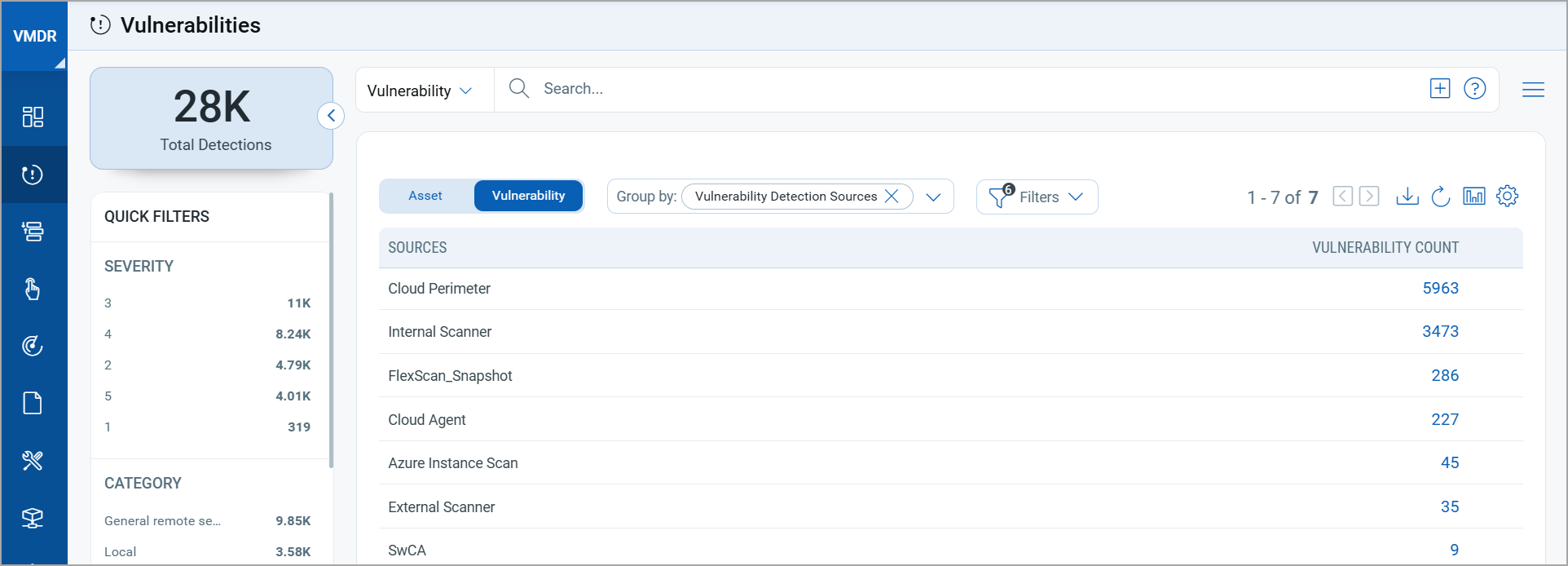
2. Group by Detection Source
Using the new Group by: Vulnerability Detection Sources filter, you can organize vulnerabilities by source. This helps you:
- Pinpoint where risks are coming from
- See how many vulnerabilities are tied to each detection method
- Drill into each group for focused remediation
3. New QQL Search Tokens
For advanced users, new search tokens allow granular queries:
- vulnerabilities.detectionSource.name
- vulnerabilities.detectionSource.firstFoundDate
- vulnerabilities.detectionSource.lastFoundDate
This makes it easier to track vulnerability lifecycles, understand patterns, and build dashboards or reports based on precise data.
4. Smarter Reports and Dashboards
Whether you’re exporting a vulnerabilities report or visualizing trends, the detection source now appears as a column in downloads and dashboard widgets. This gives stakeholders and security teams a clearer picture of where action is needed most.
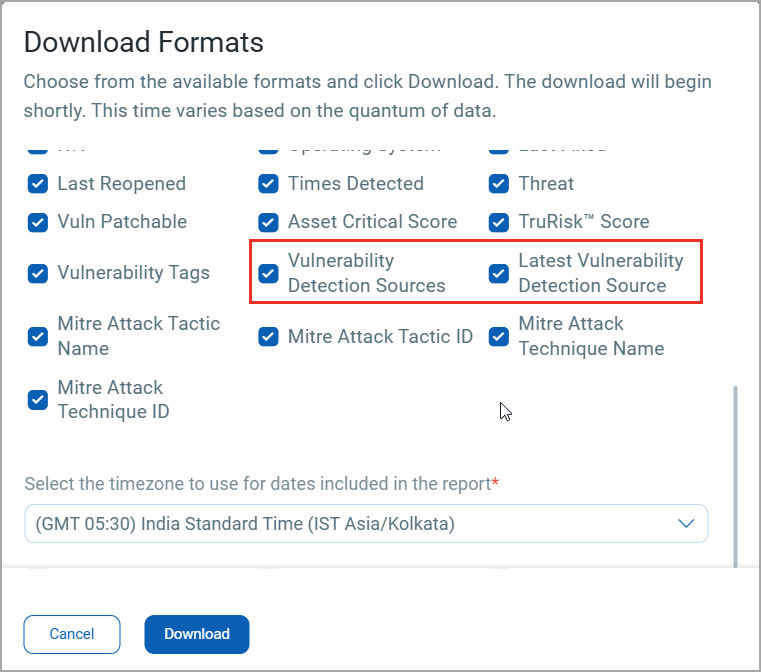
5. Vulnerability Detection Sources in Reports
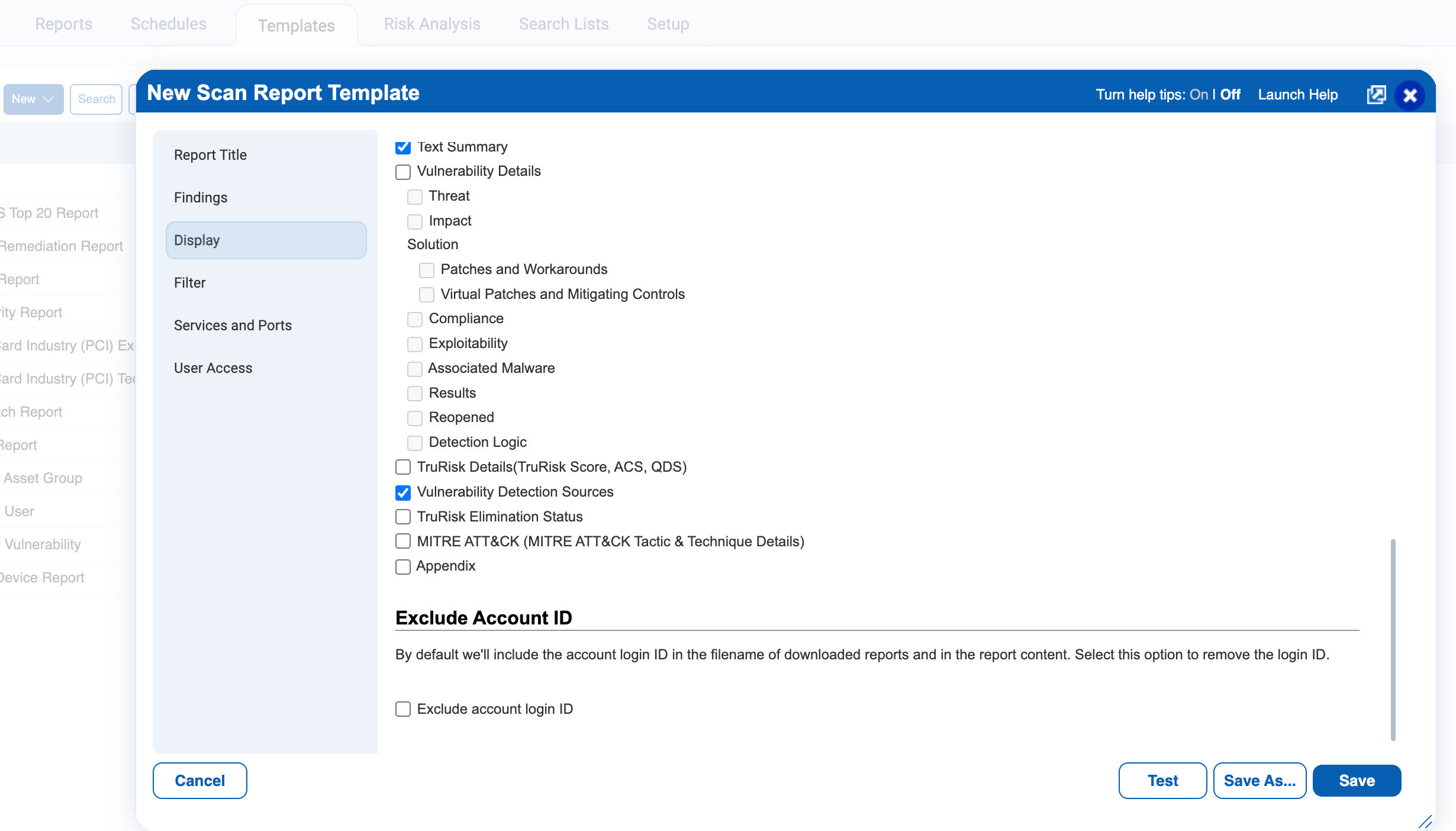
Vulnerability detection source details are now available in CSV reports. To enable:
- Open your Report Template
- In the Display section, check Vulnerability Detection Sources
Once enabled, exported reports include two new columns:
- Vulnerability Detection Sources
- Latest Vulnerability Detection Source
This added visibility helps you analyze trends, segment remediation based on origin (e.g., Cloud Agent vs. Scanner), and generate more actionable executive reporting.
6. Retrieve Detection Source via API
You can programmatically access Vulnerability Detection Sources via the Qualys API, enabling integration with external tools and dashboards.
Endpoint:
/api/4.0/fo/asset/host/vm/detection/
Parameter:
To include source information, use the following:
vuln_detection_source=1
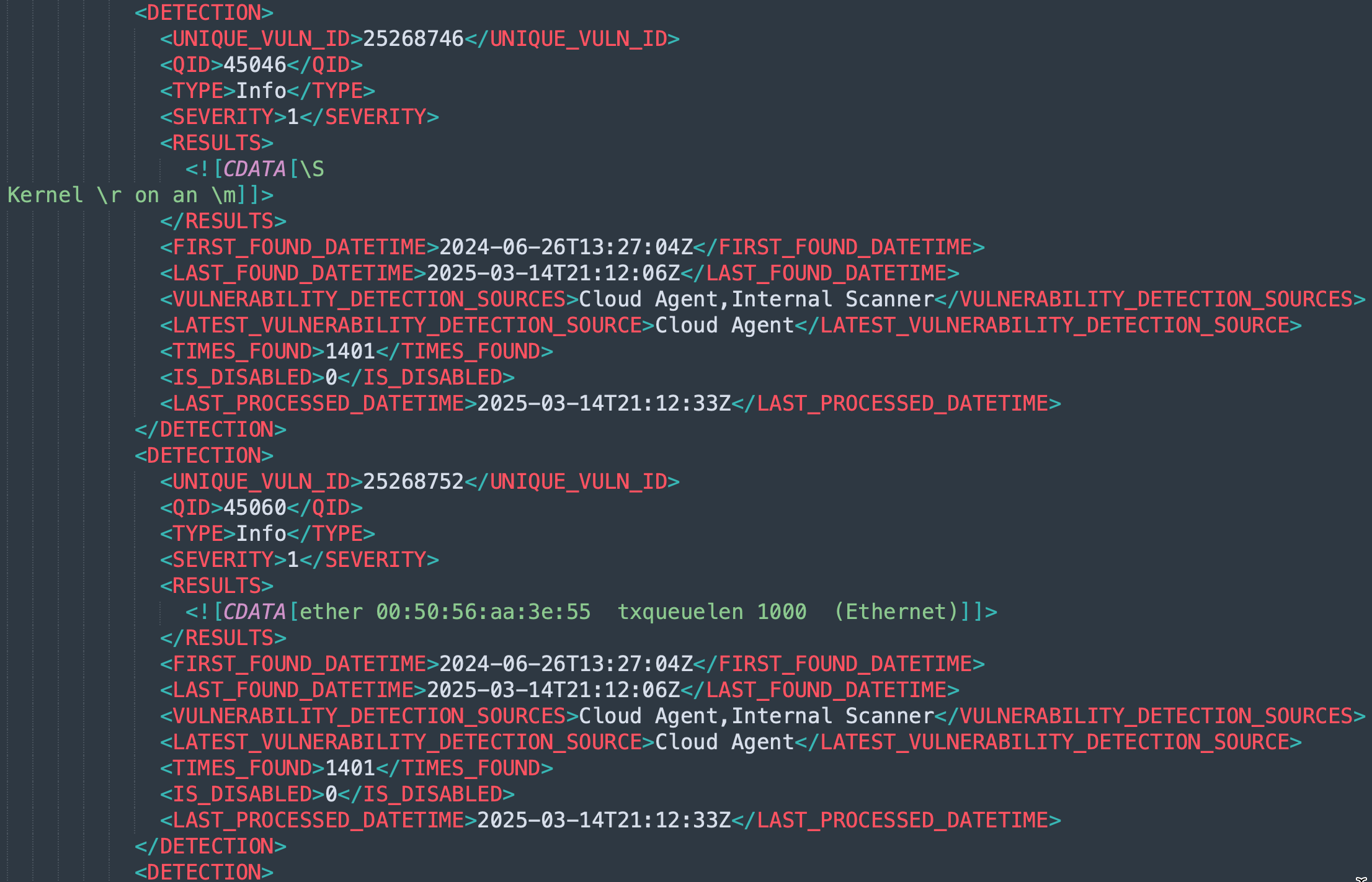
Example XML Output:
| <DETECTION> <UNIQUE_VULN_ID>25268746</UNIQUE_VULN_ID> <QID>45046</QID> <TYPE>Info</TYPE> <SEVERITY>1</SEVERITY> <RESULTS><![CDATA[\S Kernel \r on an \m]]></RESULTS> <FIRST_FOUND_DATETIME>2024-06-26T13:27:04Z</FIRST_FOUND_DATETIME> <LAST_FOUND_DATETIME>2025-03-14T21:12:06Z</LAST_FOUND_DATETIME> <VULNERABILITY_DETECTION_SOURCES>Cloud Agent,Internal Scanner</VULNERABILITY_DETECTION_SOURCES> <LATEST_VULNERABILITY_DETECTION_SOURCE>Cloud Agent</LATEST_VULNERABILITY_DETECTION_SOURCE> <TIMES_FOUND>1401</TIMES_FOUND> </DETECTION> |
This provides complete detection history, including the full list of sources and the most recent one.
The Impact: From Uncertainty to Action
Imagine a vulnerability is detected within your environment. If identified by a Cloud Agent, it might indicate a misconfigured application or outdated package on a cloud VM. Conversely, if an external scanner uncovers it, the threat could be exposed to the public internet—necessitating immediate firewall or perimeter control updates.
By leveraging Vulnerability Detection Sources, you gain clarity on where vulnerabilities originate, enabling precise and timely responses.
Building upon this, TruRisk™ Eliminate empowers organizations to go beyond traditional patching. It offers a comprehensive remediation approach that includes:
- Automated Patching: Streamlining the deployment of patches to reduce threat exposure.
- Configuration-Based Mitigations: Implementing registry changes or configuration modifications when patches are unavailable or risky.
- Device Isolation: Quarantining high-risk assets to prevent the spread of threats within the network.
With TruRisk Eliminate, you can proactively address nearly 100% of CISA Known Exploited Vulnerabilities (KEVs), ensuring robust protection even when traditional patching isn’t feasible.
This integrated approach transforms your vulnerability management from reactive to proactive, enabling you to eliminate risks intelligently and by design.
For more details on TruRisk Eliminate and how it can enhance your cybersecurity strategy, click here: TruRisk Eliminate
Coming Soon: Support for Policy Audit
The benefits of detection source visibility don’t stop with vulnerability management. This capability is also coming to Qualys Policy Audit in Q3, 2025.
In the near future, you’ll be able to identify the exact sensor source that detected each compliance control failure—whether it was a Cloud Agent, an authenticated scan, or another supported method.
This added visibility will help audit & compliance teams:
• Understand the true origin of misconfigurations or compliance failures
• Take faster, more precise corrective actions
• Improve audit readiness and reporting accuracy
Stay tuned for more updates as we bring this same level of precision and transparency to Policy Compliance assessments.
In Summary: Why This Matters
The Vulnerability Detection Sources feature is more than just an enhancement.
It’s a strategic capability for any organization aiming to:
- Improve decision-making
- Focus resources on the right problems
- Accelerate time to remediation
- Reduce the attack surface
- Prioritize external threats with increased TruRisk weighting
- Eliminate risk with clarity and confidence
Ready to take the guesswork out of vulnerability management?
Contact Qualys Support or your technical account manager to enable vulnerability detection sources in Qualys VMDR today, and secure your environment with greater insight and precision.
Ready to see how these features come together in action? Take a closer look at the vulnerability detection sources that power smarter security!

I want to note that vuln_detection_source parameter only works with V4 of the API. And the responses with vuln_detection_source=1 is about 8x slower than without in my env.