Ensure PCI 4.0 Readiness with File Integrity Monitoring for Containers
Table of Contents
- PCI 4.0: The Shift Toward Continuous, Risk-Based Compliance
- The Challenge with Containers: Why Traditional FIM Falls Short
- Key Requirements for Container FIM Under PCI 4.0
- Qualys Runtime FIM for Containers: Seamless, Scalable, and Real-Time
- Seeing Qualys FIM in Action
- Use Case: Simplifying PCI DSS For Containers
- Beyond FIM: Why Audit Readiness Requires More
- Conclusion: Take Back Control of Compliance
Compliance isn’t optional. But it’s never been more complex.
The rise of containers has revolutionized modern infrastructure—enabling faster innovation and greater scalability. But with this transformation comes a new wave of compliance challenges.
PCI DSS 4.0 introduces stricter requirements for both vulnerability management and file integrity monitoring (FIM) in dynamic environments like Kubernetes and containerized workloads. For many security and compliance teams, this presents an operational blind spot that legacy tools weren’t built to handle.
In this blog, we’ll break down the new PCI DSS 4.0 requirements, common pitfalls around FIM in containers, and how Qualys bridges the gap to help you stay continuously audit-ready—without the heavy lift.
PCI 4.0: The Shift Toward Continuous, Risk-Based Compliance
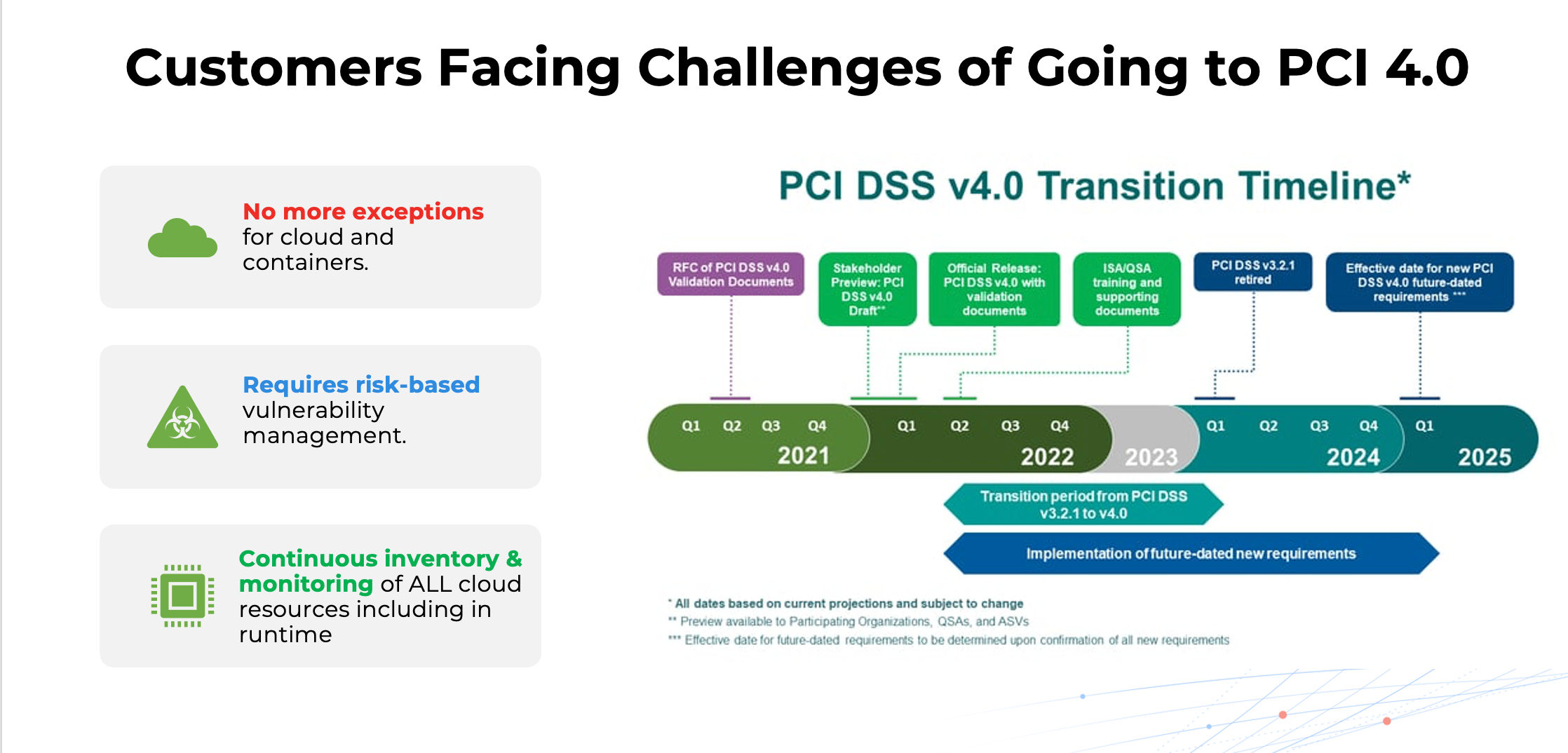
Under PCI 3.2.1, security teams were often granted exceptions when it came to container workloads. Not anymore.
PCI DSS 4.0 requires continuous risk-based vulnerability management and real-time monitoring of sensitive file and directory changes across all environments—including cloud and containers.
That means compliance isn’t just a periodic event—it’s now a continuous operational requirement. And the consequences of falling short are high: audit failure, lost customer trust, regulatory fines, and stalled business growth.
Qualys already leads the market in risk-based vulnerability management—helping organizations prioritize what matters most across cloud, containers, and on-premises environments. Now, we’re bringing that same strength to file integrity monitoring.
The Challenge with Containers: Why Traditional FIM Falls Short
Security teams today face a number of hurdles when trying to apply traditional file monitoring methods to modern environments:
- Lack of real-time coverage for ephemeral containers
- Siloed tooling that splits monitoring across host and container surfaces
- High operational overhead to deploy, manage, and correlate across systems
- Limited audit visibility—especially when containers exist only for minutes
As organizations approach PCI 4.0 enforcement in 2025, these blind spots have become urgent liabilities. And without runtime monitoring, you’re left in the dark between scans—vulnerable to tampering, drift, and audit gaps.
Key Requirements for Container FIM Under PCI 4.0
To meet modern compliance mandates like PCI, you need a FIM solution that’s:
- Built into runtime – not bolted on
- Noise-canceling by design – not just alerting on every event
- Context-rich and correlated to workload, user, and business function
- Unified across host and container surfaces for consistent reporting
- Automated for audit readiness – no more manual evidence scramble
Qualys Runtime FIM for Containers: Seamless, Scalable, and Real-Time
With Qualys Runtime FIM for Containers, we’re closing the gap between traditional compliance tools and modern infrastructure, reimagining the approach to compliance that adapts to how you work today.
Here’s how we do it:
- Continuous Runtime Visibility and Monitoring
- Unlike legacy FIM tools, Qualys leverages eBPF (Extended Berkeley Packet Filter) technology to monitor file changes in real time within containerized environments.
- No performance drags, no side cars – just continuous visibility, even for ephemeral workloads.
- Unified Host and Container Coverage:
- Bring the same level of reporting and FIM policy coverage to both hosts and containers. No need to juggle managing multiple policies for both.
- Actionable Insights for Compliance Needs:
- Don’t just monitor file changes – understand them. Link unauthorized file changes to specific images for remediation. Correlate to specific pods and namespaces to trace back to business and organizational context.
- Automated Reporting for Audit-Readiness:
- Automatically generate reports with proper container context for PCI DSS, HIPAA or NIST. Save time, reduce complexity, and impress your auditors.
Seeing Qualys FIM in Action
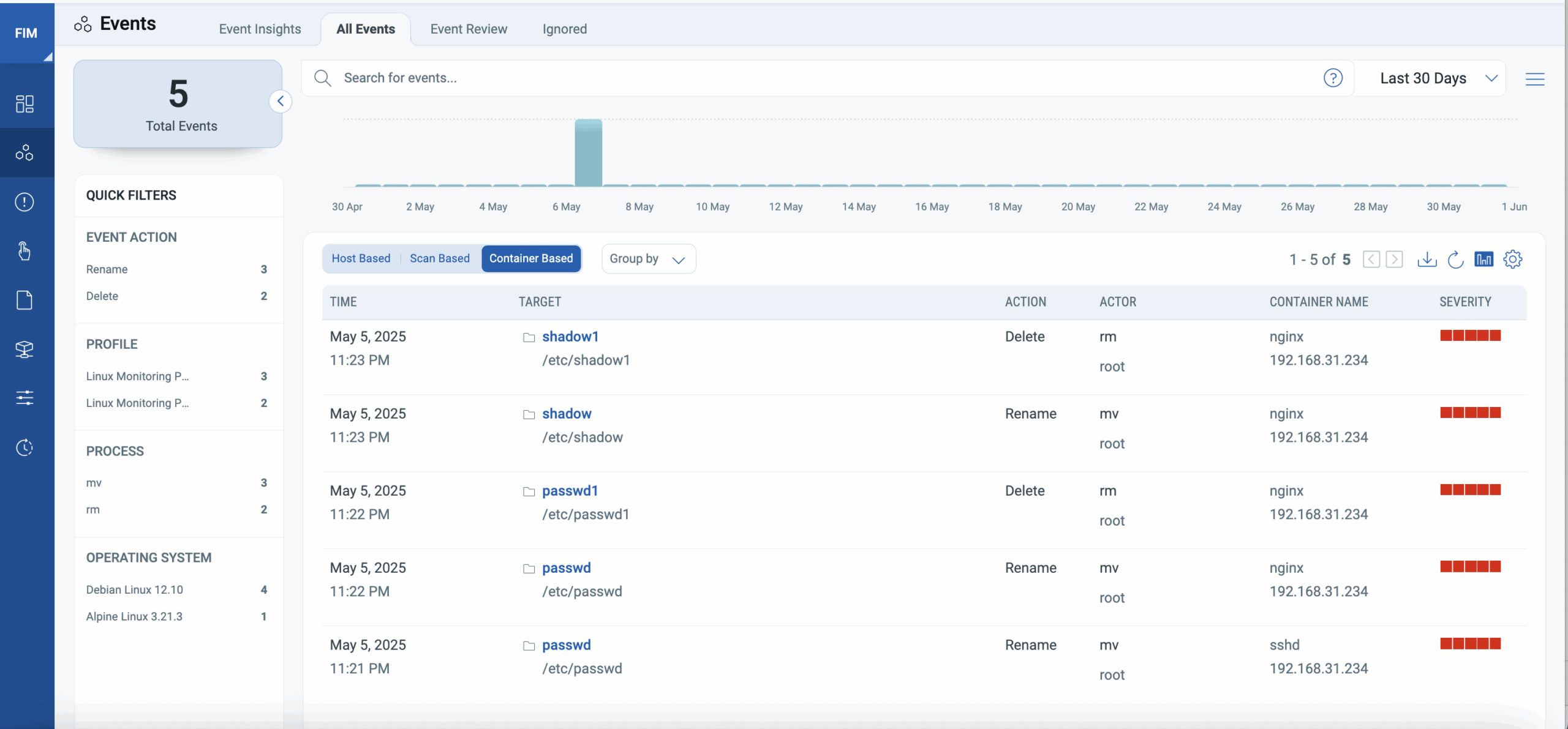
Manage Any FIM Event Seamlessly From One Console:
Qualys FIM is seamlessly embedded into the already trusted and used FIM module in Qualys, enabling a single pane of glass file integrity monitoring and response for both hosts and now a newly added tab for containers.
The Qualys cloud platform stores FIM events for 13 months, even for short-lived containers, ensuring you can meet your audit needs.
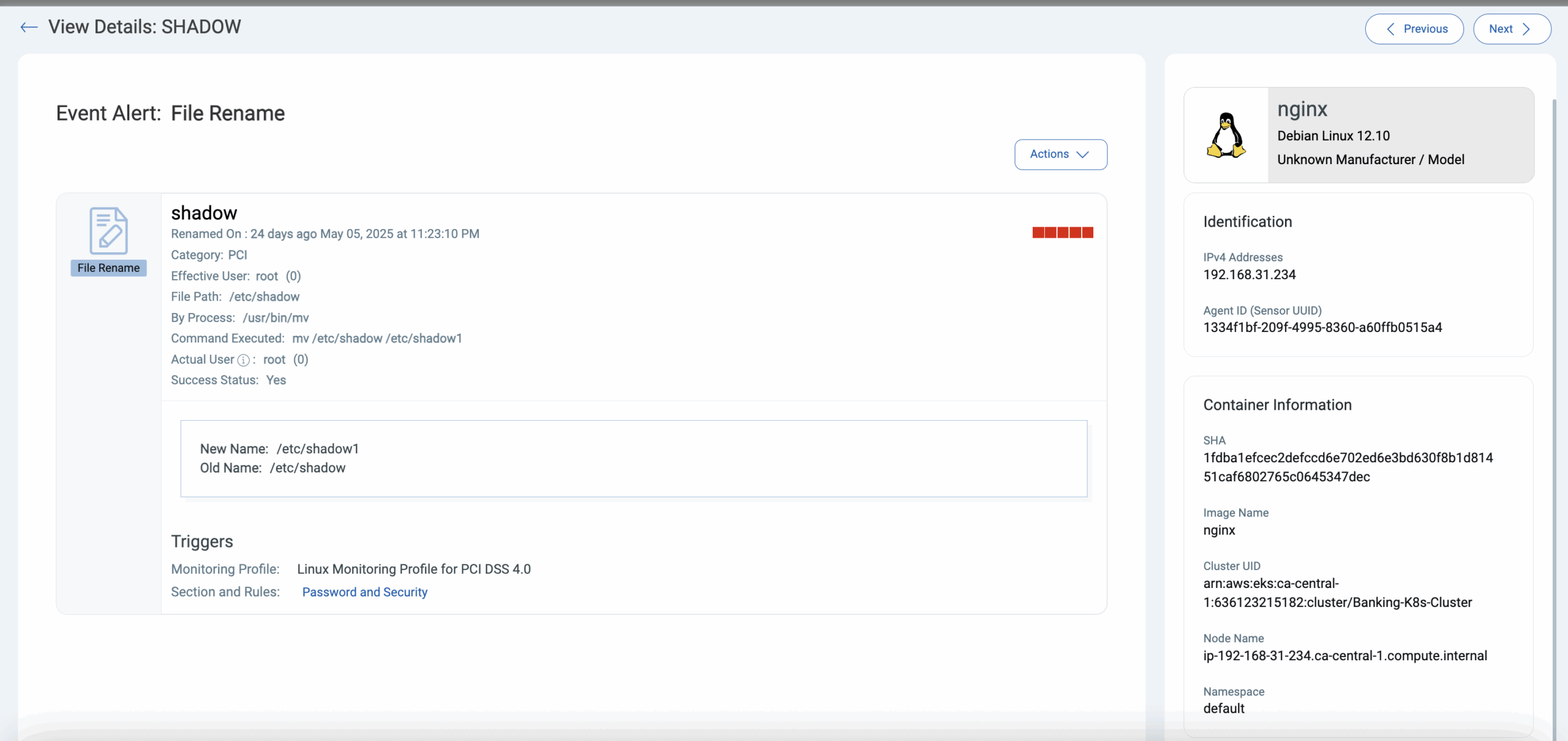
Analyze and Take Action with Context:
Qualys tracks rich metadata for each FIM event, including correlation to container and Kubernetes context. Unlike traditional FIM tooling, Qualys enables security teams to respond and take action with context, including user attribution, actions taken, and, of course, the specific file or directory that was modified. Leverage the same Qualys FIM event review capabilities to instantly cut through any noise and focus on what is most important to your business.
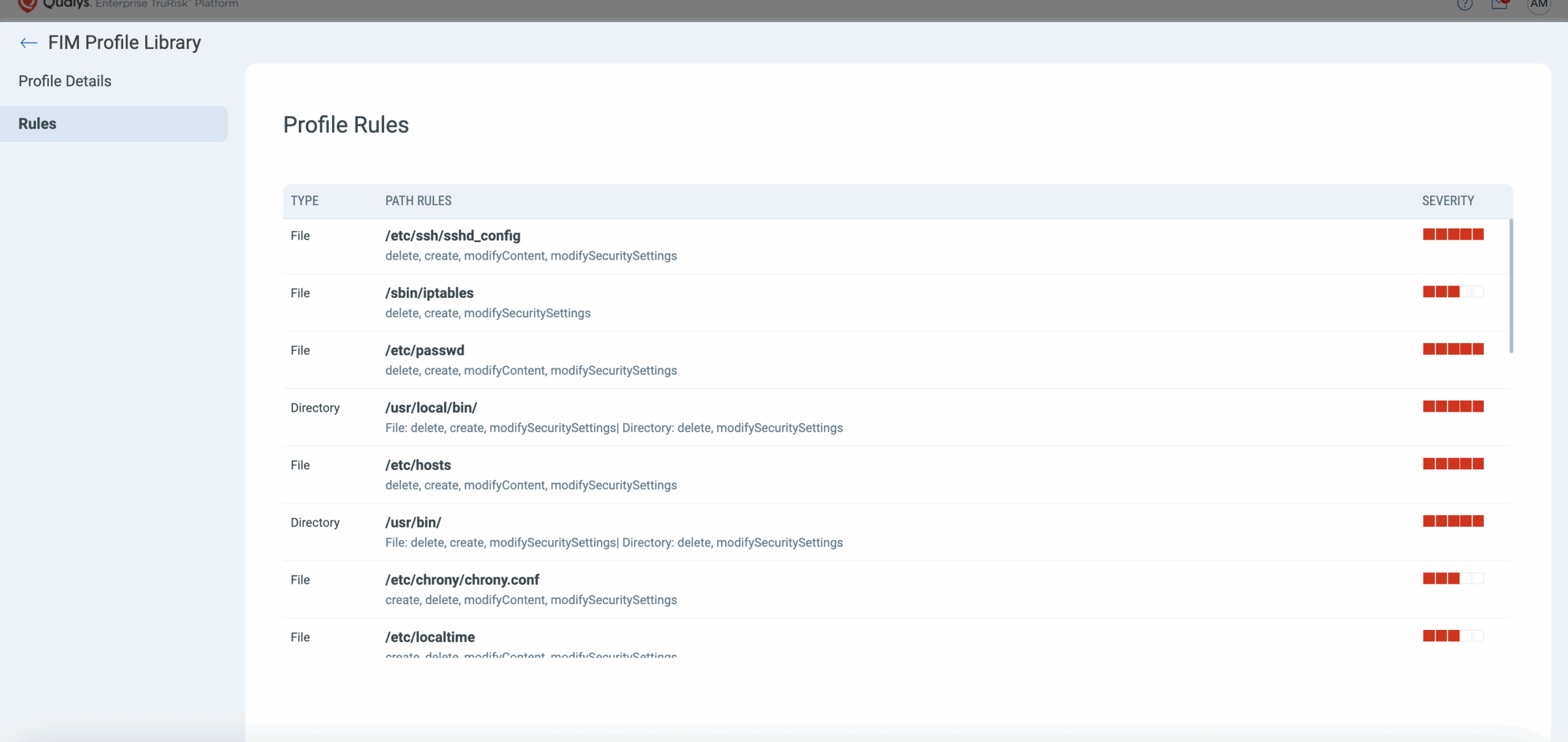
Decrease Time to Compliance Readiness with Out-of-the box Policies:
With Qualys FIM, you can reduce PCI DSS audit overhead with out-of-the-box policies and scoring to monitor the most sensitive files, ensuing easy detection of deletion of log files, introduction of ransomware, and modification of user permissions.
Use Case: Simplifying PCI DSS For Containers
A global financial services company leveraged Qualys runtime FIM to secure its payment processing applications. The results?
- Real-time tracking across hybrid cloud applications
- Increased speed and agility in moving to modernized applications with confidence in same level of security visibility and monitoring for both hosts and containers
- Reduced Compliance Gaps: Satisfied compliance needs in less time through scalable visibility across all their new application stacks running containers including Kubernetes clusters.
- Audit-ready reports generated in seconds not days
- Unified compliance policies that reduced manual effort by 30% through avoided redundancy in generating reports for hosts and containers
Beyond FIM: Why Audit Readiness Requires More
Audit readiness is no longer just about producing documentation—it’s a business-critical capability.
- A failed audit can halt product launches or market entry
- Missed evidence can cost 10,000+ hours in manual remediation effort
- 48% of compliance failures stem from human error in misconfigured fixes
Qualys helps you move from point-in-time checklists to continuous audit confidence by:
- Mapping FIM and vulnerability data to PCI and other compliance frameworks
- Automating evidence collection and retention
- Aligning technical control data with TruRisk™ prioritization
- Streamlining workflows across ITSM, GRC, and SecOps
Conclusion: Take Back Control of Compliance
The compliance landscape has changed. Point tools, agentless scanners, and spreadsheet audits no longer suffice.
Qualys Runtime FIM for Containers gives you:
- Visibility between scans
- Unified risk and compliance posture across cloud, containers, and on-premises
- Automated, audit-ready insights that reduce both time and cost
With Qualys, compliance becomes more than a requirement—it becomes a catalyst for smart, scalable, and cost-effective security.
Ready to get started with Qualys Runtime FIM for Containers and take a leap towards continuous audit confidence right away?