Google Chrome to Distrust Chunghwa & Netlock Certificates: How Qualys Certificate View Helps You Respond
In a major change to the global certificate ecosystem, Google Chrome has announced that it will no longer trust any new digital certificates issued by Chunghwa Telecom and Netlock, two long-standing Certificate Authorities (CAs), after July 31, 2025. This move is part of Chrome’s ongoing efforts to improve TLS certificate trust, hold Certificate Authorities (CAs) accountable, and ensure stronger web security standards.
If your organization uses SSL/TLS certificates issued by these authorities, it’s critical to identify, replace, and monitor them before the Chrome update rolls out.
Why Is Chrome Distrusting Chunghwa Telecom and Netlock?
According to Google’s Chromium Security team, the decision stems from repeated compliance failures, unfulfilled improvement commitments, and limited measurable progress from both CAs. These issues include weak incident response and substandard certificate management practices. As a result, Google concluded that continued trust in these CAs is no longer justified and poses a security risk to the Chrome users.
“Chrome’s confidence in the reliability of Chunghwa Telecom and Netlock as CA Owners included in the Chrome Root Store has diminished due to patterns of concerning behavior observed over the past year.”
—Google Chrome Security Team
This distrust will be enforced starting in Chrome version 139 and higher.
What Will Happen After July 31, 2025?
After 11:59:59 PM UTC on July 31, 2025, Chrome will no longer trust any newly issued certificates from Chunghwa Telecom or Netlock.
Here’s what to expect:
- SSL certificates issued after the deadline will be treated as untrusted
- Users visiting affected sites with these certificates will see a full-page security warning (“Your connection is not private”).
- Pre-existing certificates will continue to be valid until they expire, but website operators are strongly encouraged to migrate away as soon as possible to avoid future issues.
Who Is Affected?
- Website operators using TLS/SSL certificates from Chunghwa Telecom or Netlock.
- End users of Chrome on all platforms (Windows, macOS, ChromeOS, Android, Linux).
- Enterprises, especially those relying on legacy trust models or third-party providers
While local trust overrides are possible through custom trust stores or group policies, Google discourages this as a long-term solution.
How Many Qualys Customers Are Impacted ?
Thanks to Qualys VMDR’s Certificate Auto-Discovery capabilities, Qualys has identified:
- ~2,200 certificates issued by Chunghwa or Netlock in active environments
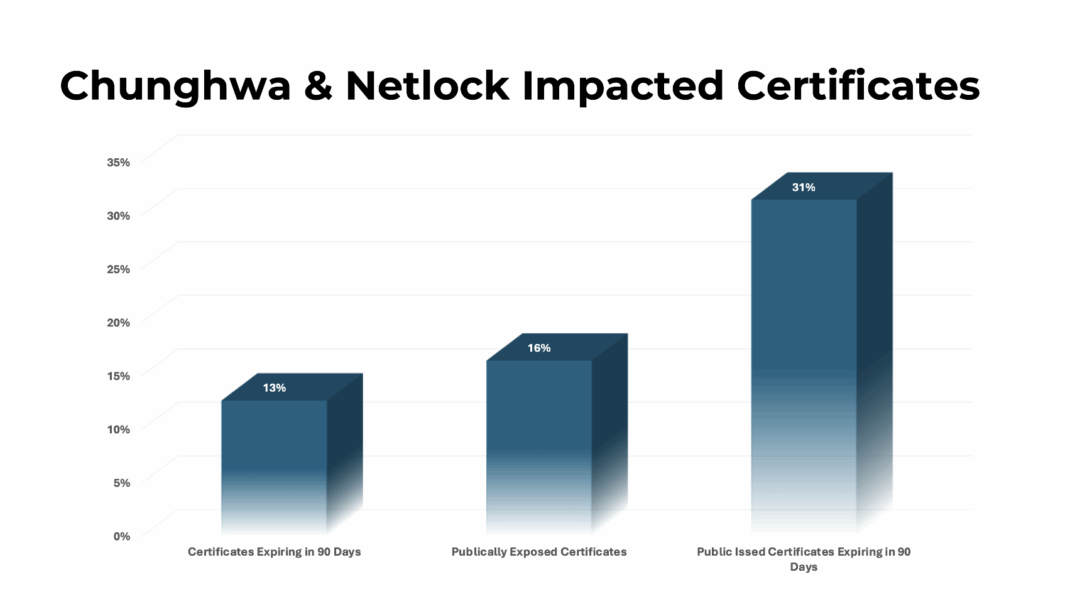
- ~280 are set to expire in the next 90 days
- ~360 are exposed to the public, and around 110 of these are due to expire within the next 90 days.
Nearly 30% of certificates exposed to the public with Chunghwa or Netlock certificates are due to expire in the next 90 days, which is a critical risk window as Chrome revokes trust.
How Qualys Certificate View Helps You Respond
Qualys Certificate View is a bundled solution with the Qualys VMDR that helps organizations discover, inventory, assess, and manage all their digital certificates internally and externally.
In light of Chrome’s announcement, Qualys Certificate View can be instrumental in helping organizations:
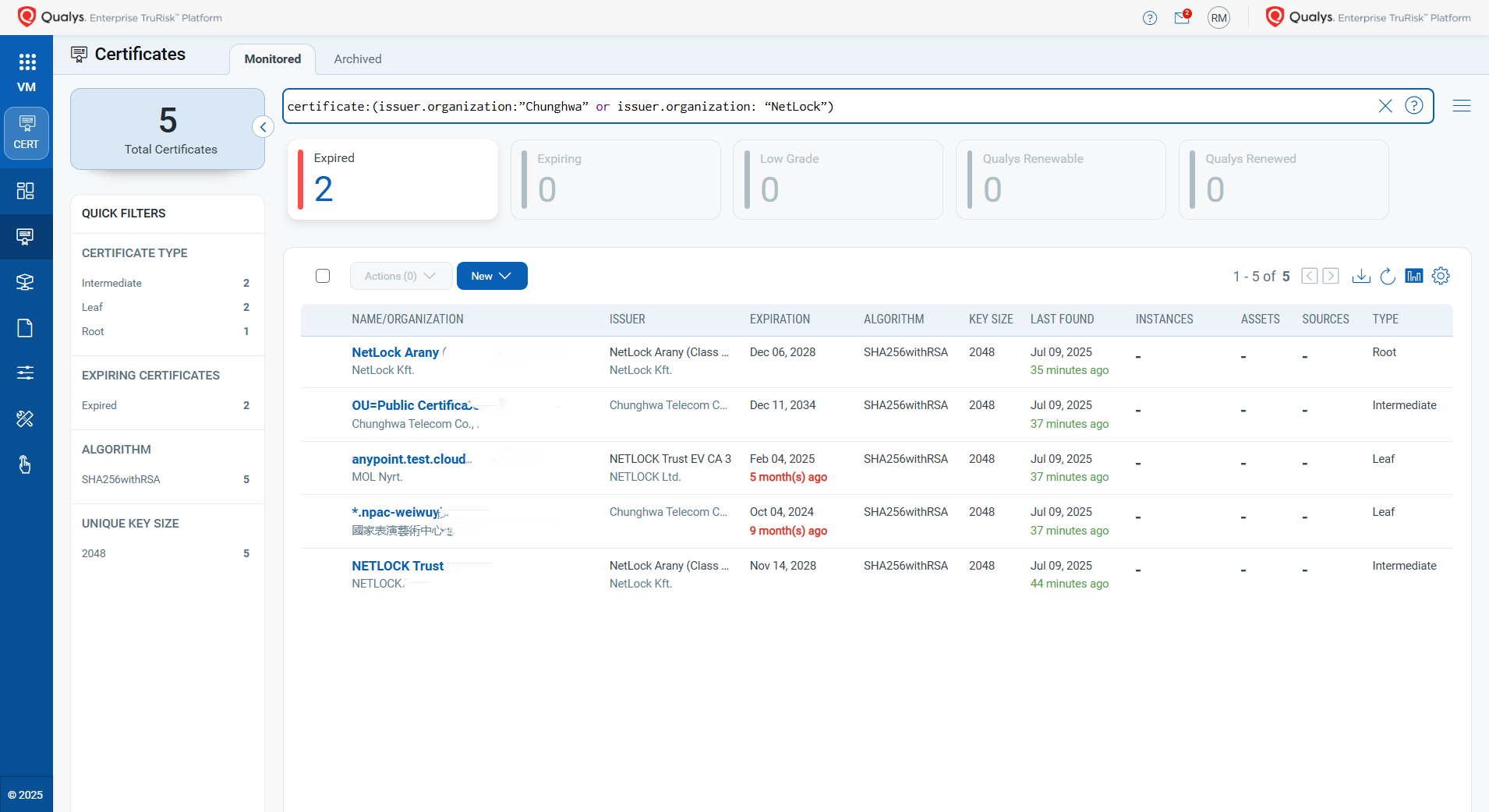
- Identify all certificates issued by Chunghwa Telecom and Netlock across your environment, including cloud and on-premises assets
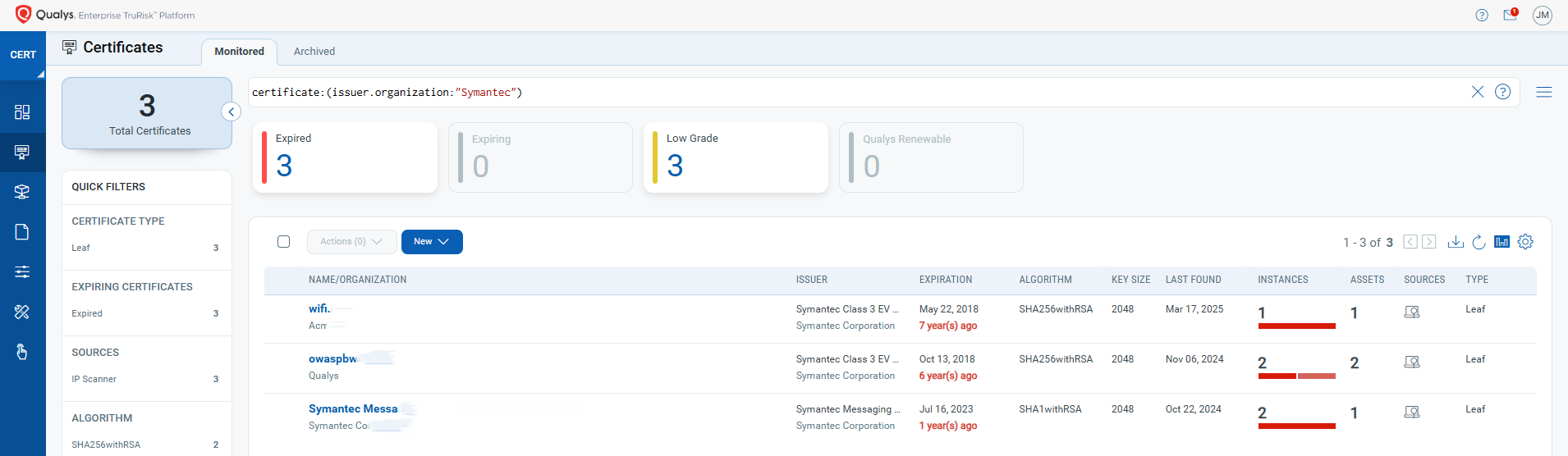
QQL to be referred: certificate:(issuer.organization:”Chunghwa” or issuer.organization: “NetLock”)
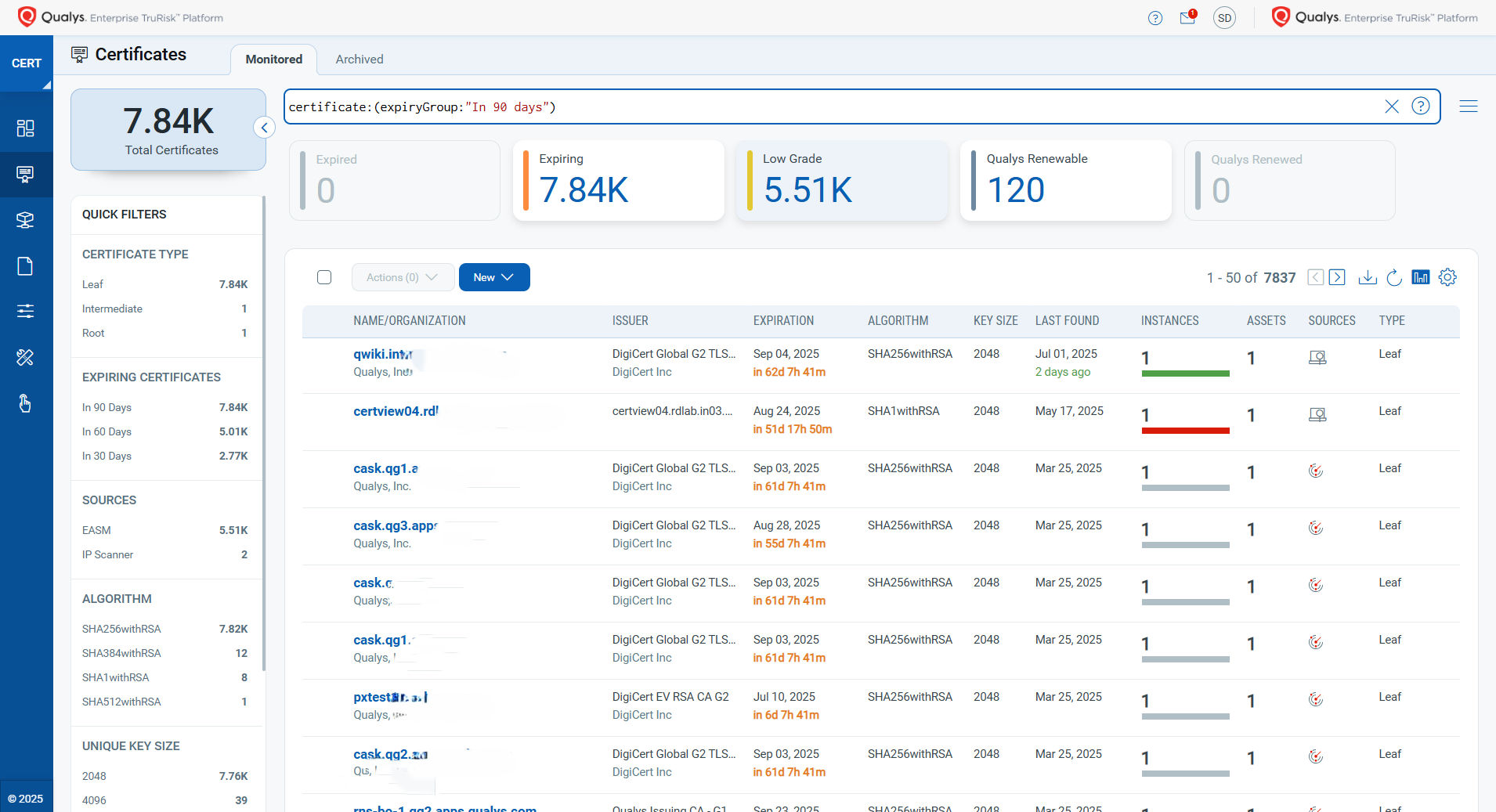
- Monitor certificate expiration dates and compliance status, ensuring you know which certificates are at risk and need replacement.
QQL to be referred certificate:(expiryGroup: `In 90 Days`)
- Automate the process of certificate discovery and renewal, reducing the risk of outages or security warnings.
With the DigiCert Integration, you can use the Enrollment options to initiate the renewal process for certificates that are about to expire. This workflow assists in sending a renewal request to DigiCert. You can enroll, renew, and even auto-renew certificates issued by DigiCert, as well as those from DigiCert acquisitions such as Thawte, Mocana, and GeoTrust.
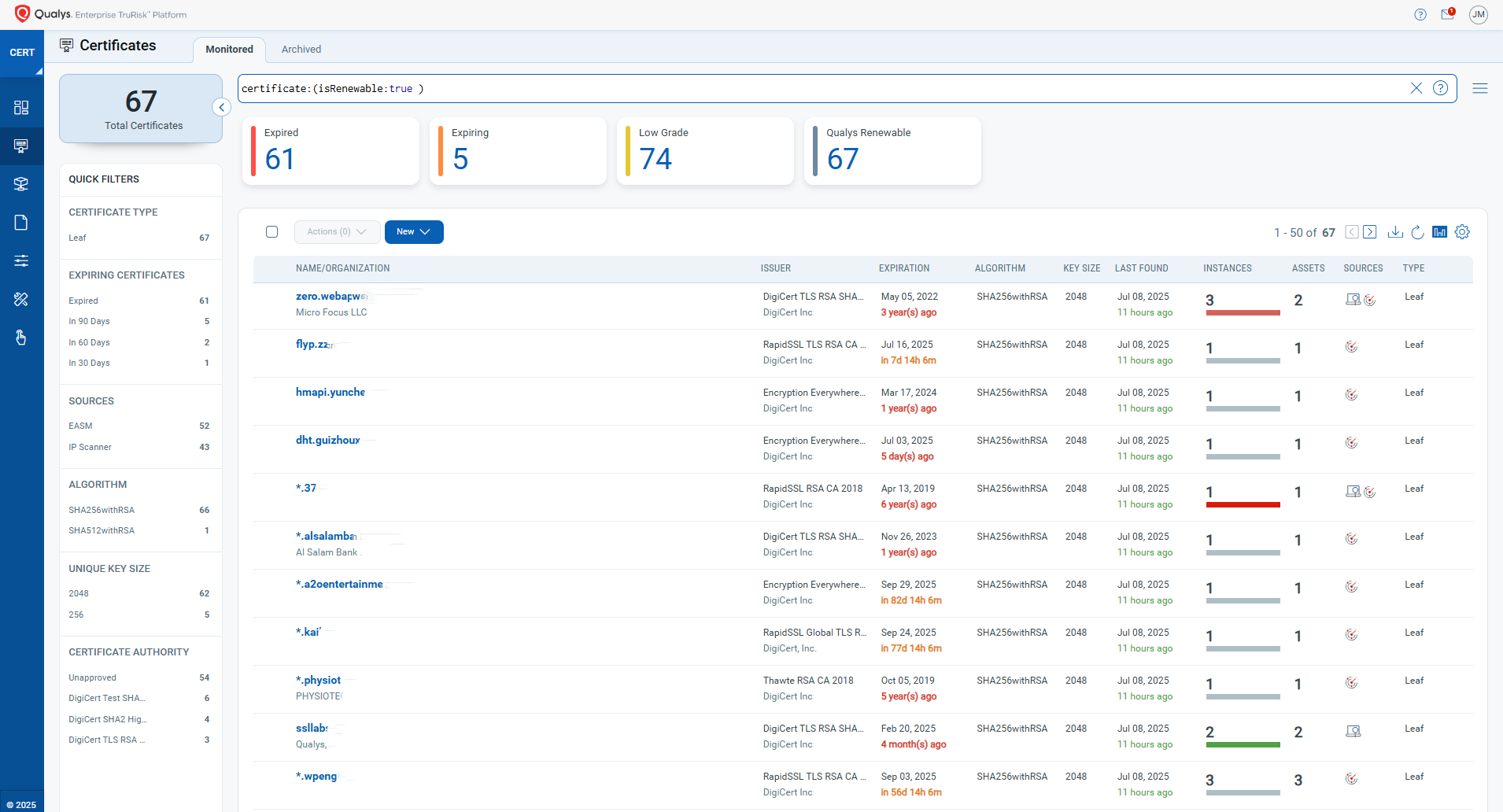
QQL to be referred certificate:(isRenewable:true)
- Plan Remediation: You can prioritize the replacement of these certificates with new ones from a trusted CA included in the Chrome Root Store.
- Visualize and report on certificate issuers, making it easy to spot and prioritize remediation for certificates from untrusted or soon-to-be-untrusted CAs.
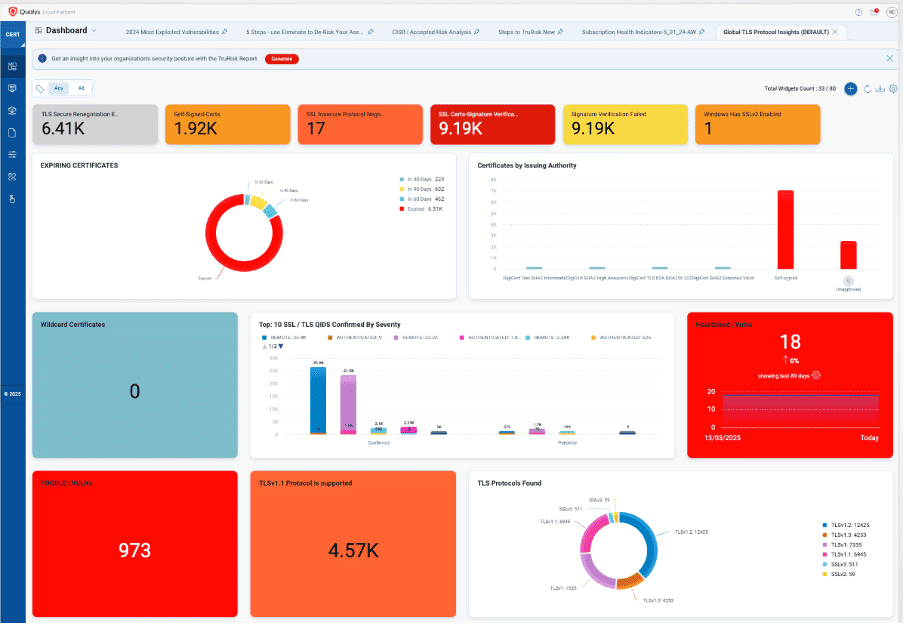
To explore the latest certificate trends, download the Global TLS Protocol Insights dashboard.
Qualys Certificate View Recommendations
- Auto-Discovery of Certificates: Ensure all VMDR Assets are activated for Certificate View. Standard VMDR Scans will automatically discover all certificates in your environment.
You can also launch a lightweight Certificate View scan directly from VMDR or launch from Certificate View module. - Granular Certificate Details: Certificate View module provides detailed information about each certificate, including the latest TLS Protocols in use. This helps you monitor protocol versions and ensure compliance with security best practices.
- Classify Certificates: Certificates discovered by Qualys are automatically classified as Leaf, Intermediate & Root for easier management.
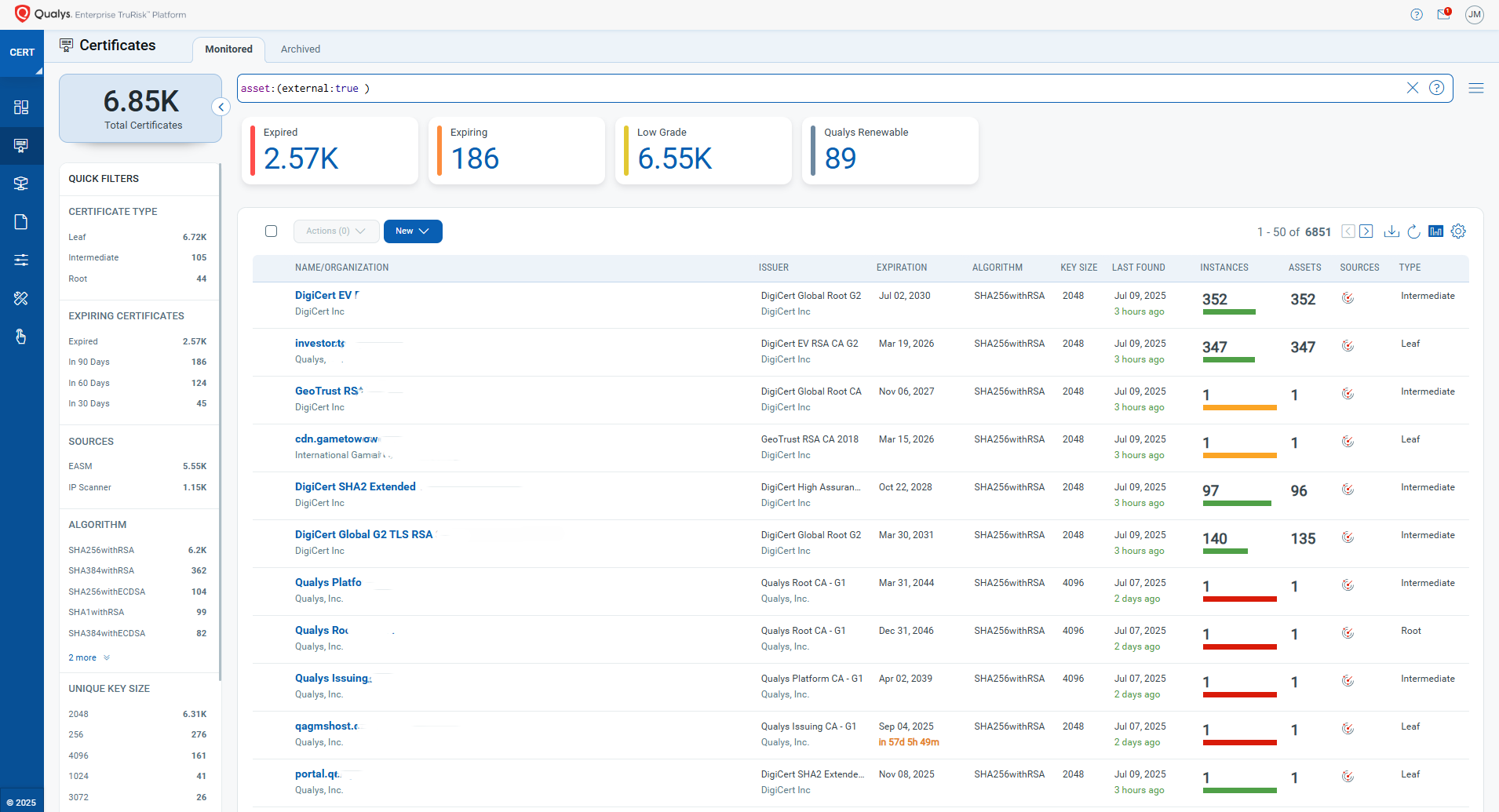
- Internal vs. External Segregation: Qualys Certificate View distinguishes between Internally & Externally discovered Certificates, enabling you to effectively monitor the upcoming certificate renewals/expirations.
QQL to be referred asset:(external:true)
- Filter by Issuer: Use dashboard widgets or search queries to list all certificates issued by Chunghwa Telecom and Netlock or by CA Issuer.
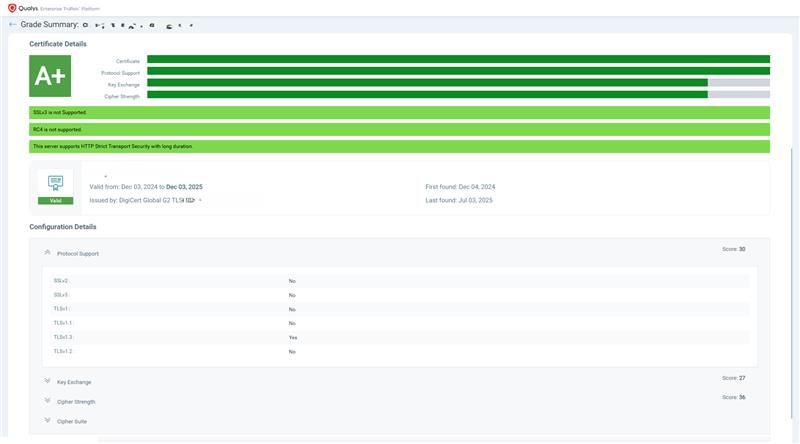
- Assess Risk, Weak & Expiring Certificates: Identify certificates that are using weak/insecure protocols or algorithms. The Grade Summary for each certificate shows the actual risk associated with weaker cipher suites, outdated protocols, and insufficient key exchange parameters.
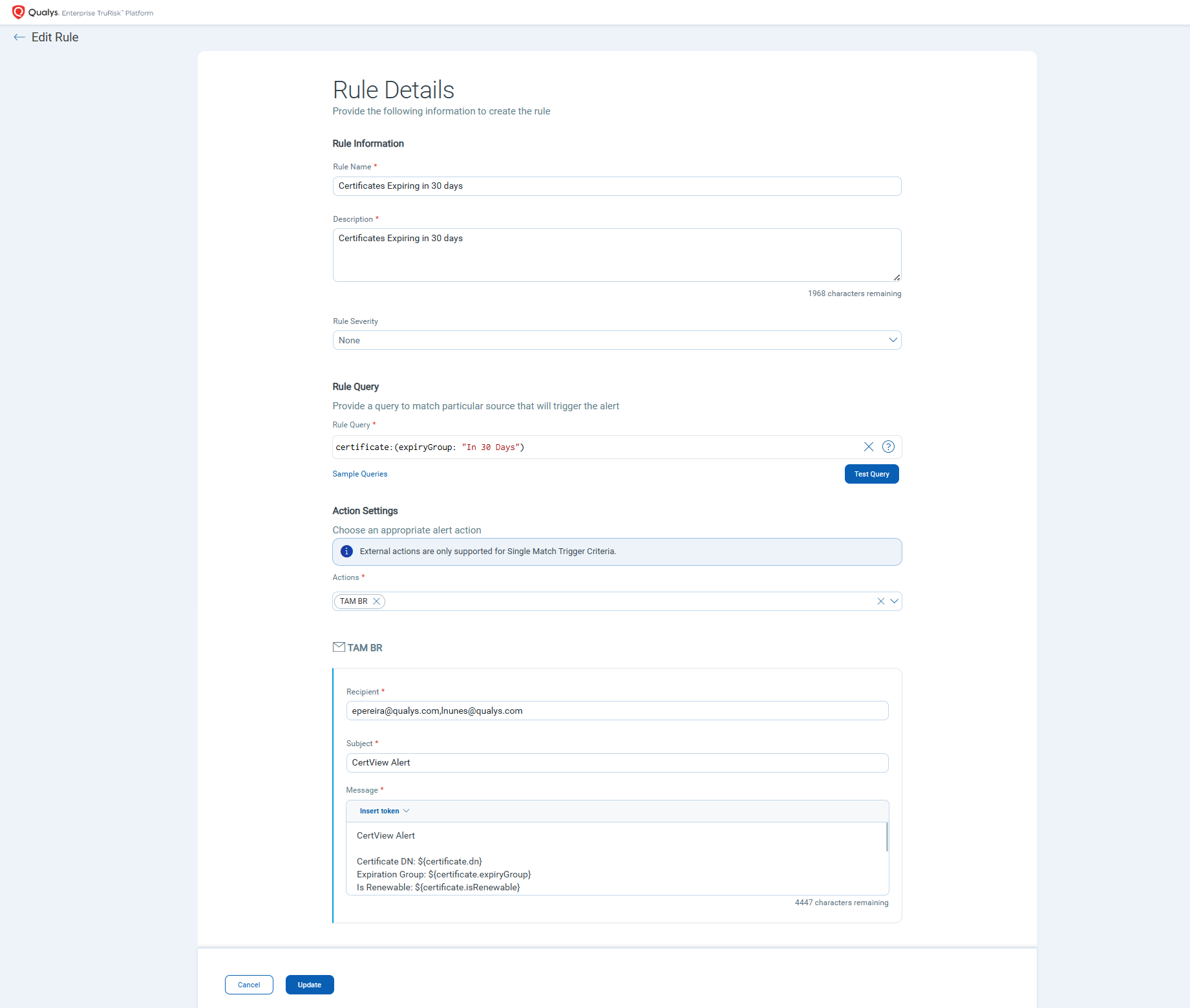
- Set up alerts and monitor Upcoming Expirations: To monitor any upcoming expirations of the certificates, encourage the use of Responses (alerting) to trigger alerts to respective stakeholders and get notified via Microsoft Teams, Email, Slack, and PagerDuty. This ensures that no certificates are overlooked.
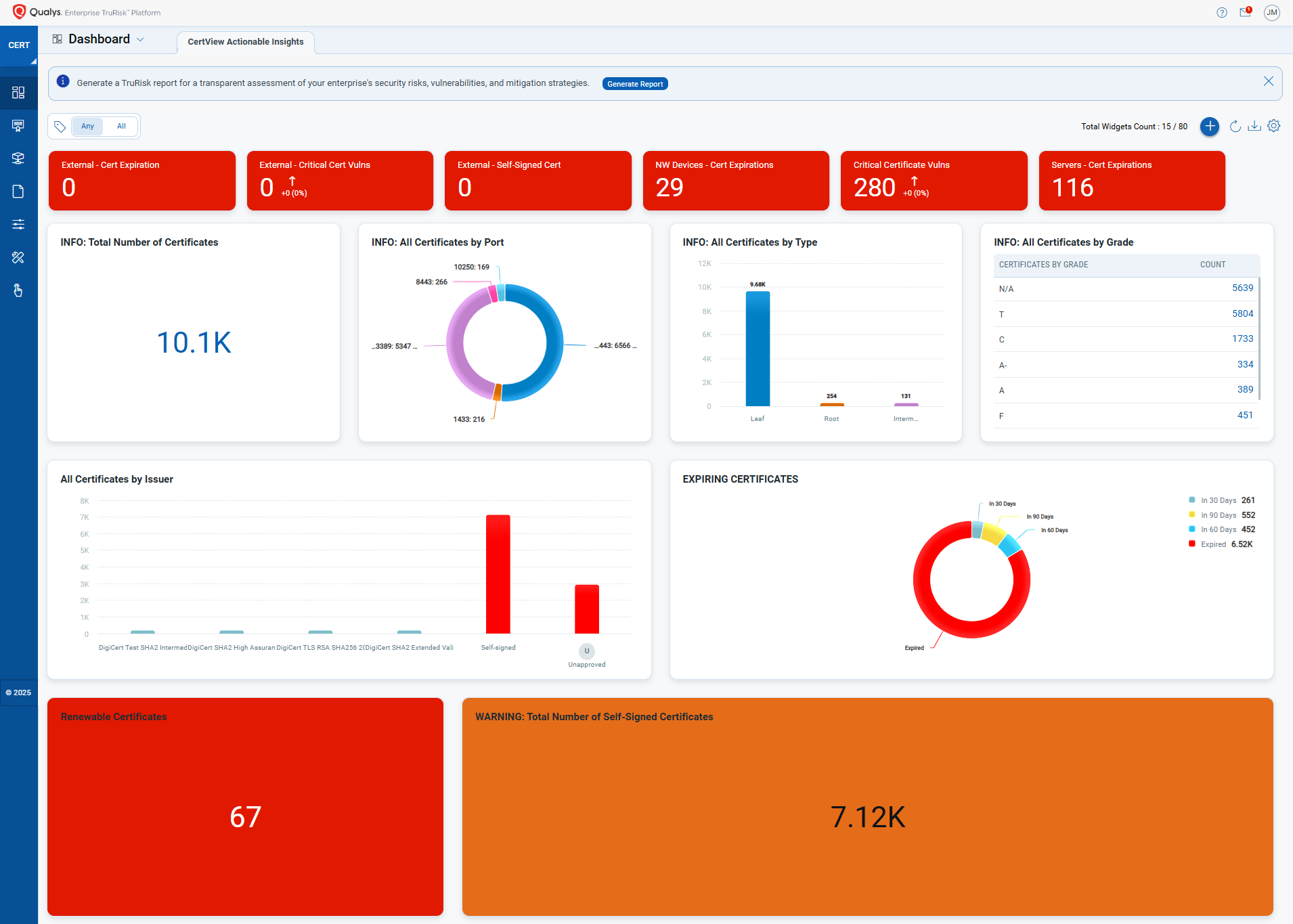
- Actionable Dashboard for all discovered certificates: Use Qualys dashboards for actionable insights about all your certificates across your estate and take recommended actions to stay ahead and remain compliant for all your web services that are actively used by your end-users.
To explore the new features, download the Certificate View Actionable Insights dashboard.
What Should Website Operators Do Now?
Chrome’s upcoming changes demand immediate action. Here’s your action plan:
- Immediately inventory all SSL/TLS certificates using tools like Qualys Certificate View or Chrome’s built-in Certificate Viewer.
- Replace all Chunghwa Telecom and Netlock certificates expiring after July 31, 2025, with certificates from a trusted CA.
- Test your website to ensure no security warnings appear in Chrome.
- Monitor for future CA trust changes using Qualys Certificate View to automate this process and stay ahead of browser policy shifts.
Why Qualys Certificate View Matters
As browsers like Chrome raise the bar on CA trustworthiness, organizations need continuous visibility and automated control over their digital certificates. Whether you’re managing 50 certificates or 5,000, Qualys helps you:
- Eliminate blind spots in your certificate infrastructure
- Ensure compliance with browser and CA policies
- Avoid service disruptions caused by expired or distrusted certificates
Conclusion
Google Chrome’s upcoming distrust of Chunghwa Telecom and Netlock certificates, effective July 31, 2025, marks a major shift in the SSL/TLS certificate trust landscape. This change reinforces the importance of proactive digital certificate management to protect your business from unexpected outages, security warnings, and the loss of user confidence.
With Qualys Certificate View, security teams gain end-to-end visibility, automated certificate discovery, and streamlined reporting needed to identify, assess, and replace affected certificates efficiently. By staying ahead of browser trust policy changes, you can ensure a seamless, secure, and compliant transition, safeguarding your users and maintaining digital trust.
Stay proactive, stay secure, and let Qualys Certificate View be your partner in digital certificate management.
Reference Links
Sustaining Digital Certificate Security – Upcoming Changes to the Chrome Root Store
Qualys Certificate View API Guide
Ready to start your free trial of Qualys VMDR with TruRisk™ and accelerate your digital certificate management efforts?