Understanding the Impact of Scattered Spider on the Airline & Transportation Industry
In June, the FBI publicly warned that Scattered Spider is actively targeting the aviation and transportation sectors, including well-known airlines and their third-party IT vendors. In this post, we will provide a brief overview of Scattered Spider, insights gathered by our research team into the vulnerabilities they target, and how organizations can protect themselves.
What is Scattered Spider?
Scattered Spider is a financially motivated hacking collective (also known as UNC3944, Octo Tempest, Scatter Swine, and Star Fraud), mostly comprised of young members located in North America and the UK, referred to as “the Com.” It has been active since May 2022 and has evolved from SIM‑swapping to advanced social engineering, MFA‑bombing, and ransomware via affiliates like ALPHV and DragonForce. Scattered Spider has targeted a vast range of industries and companies, including aviation, hospitality, retail, insurance, finance, technology, entertainment, telecommunications, gaming, and cryptocurrency. One of these high-profile breaches resulted in one company losing ~$100 million and another paying a ransom of $15 million. Recent campaigns have involved investigations from the FBI, CISA, and the United Kingdom’s National Crime Agency.
Airline Industry Asset Risks:
In an analysis of 600,000 assets across anonymized Qualys airline-industry customer organizations—rigorously anonymized to ensure our insights cannot be traced back to specific organizations or assets—we mapped exposure to CVEs actively exploited by the threat actor Scattered Spider, including:
- CVE-2015-2291 (QID 92074 – Intel Ethernet Diagnostics Driver DoS)
- CVE-2021-35464 (QID 150623 and QID 730675 – ForgeRock Access Management RCE)
- CVE-2024-37085 (QID 216333 and QID 216331 – VMware ESXi 7.0/8.0 Auth Bypass)
These CVEs are frequently leveraged by Scattered Spider to gain initial access and escalate privileges across infrastructure.
Insights from the Threat Research Unit and Key Findings:
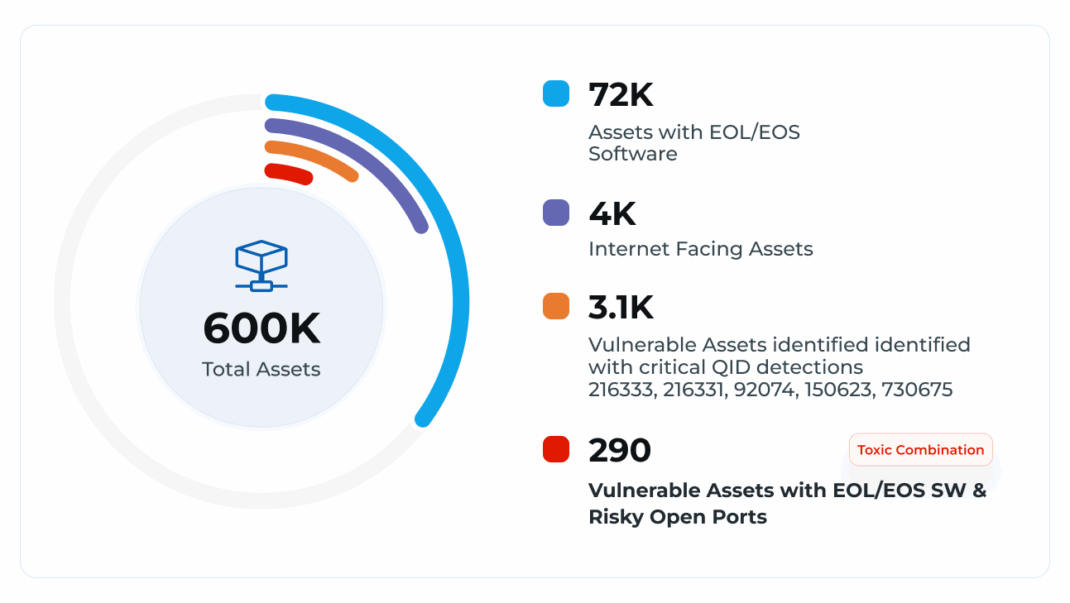
-QID Detections: 3,138 assets were identified with critical QID detections (216333, 216331, 92074, 150623, 730675), representing approximately 0.5% of the total asset base.
-Internet-Facing Exposure: Nearly 3,000 assets (0.5%) were found to be internet-facing with high-risk open ports (e.g., RDP, SSH, exposed databases), increasing their susceptibility to targeted attacks.
-Legacy Software Risk: Approximately 72,000 assets (12%) are running End-of-Life (EOL) or End-of-Support (EOS) software with known vulnerabilities.
On average, each affected asset is associated with 16 unique CVEs, directly attributable to EOL/EOS software.
Key Impacts and Recommendations:
Given the active nature of this threat, we offer the following guidance to all organizations, particularly those in and associated with the airline and transportation industries.
CVE-2015-2291:
Impact: CVE-2015-2291 is a high-severity vulnerability in Intel Ethernet diagnostics drivers for Windows (IQVW32.sys and IQVW64.sys versions prior to 1.3.1.0). It enables local attackers to execute arbitrary code with kernel privileges or cause a denial of service using crafted IOCTL calls. This vulnerability impacts multiple Windows operating systems, including Windows XP, Windows 7, Windows 8, Windows Server editions, and others, potentially affecting a wide range of systems. Adversaries have exploited this flaw for deploying malicious drivers using the ‘Bring Your Own Vulnerable Driver’ (BYOVD) technique, bypassing Windows security mechanisms and disabling endpoint protection solutions.
Recommended Solutions: Users should upgrade the Intel Ethernet diagnostics drivers (IQVW32.sys and IQVW64.sys) to version 1.3.1.0 or later, available via the Intel Ethernet Adapters Connections CD 20.1 or newer. Administrators should scan all systems for outdated drivers, ensure timely patching of vulnerabilities, and utilize robust endpoint security solutions to monitor and mitigate potential threats while observing unusual system behaviors or signs of compromise.
CVE-2021-35464:
Impact: CVE-2021-35464 is a critical vulnerability in ForgeRock Access Manager (AM), allowing unauthenticated attackers to execute arbitrary code remotely on affected servers. This flaw stems from unsafe Java deserialization in the Jato framework, affecting AM versions 6.0.0.x and all 6.5 versions up to 6.5.3. Exploits can compromise the server, enabling attackers to extract credentials, deploy malware, and move laterally within networks, potentially leading to data breaches or ransomware attacks. The vulnerability is listed in the CISA’s Known Exploited Vulnerabilities (KEV) Catalog due to active exploitation incidents.
Recommended Solutions: Upgrade affected ForgeRock AM versions to 7.0 or later, as the vulnerability is fixed in these versions. If immediate upgrade is not feasible, apply ForgeRock’s workaround by disabling the VersionServlet mapping in the AM web.xml file or blocking access to the ‘/ccversion/*’ endpoint using a reverse proxy. Additionally, limit internet access to vulnerable servers, monitor logs for exploitation indicators (e.g., requests to ‘/ccversion/Version’), and ensure the application runs with minimal privileges. Effective patch management and regular updates are essential to prevent exploitation.
CVE-2024-37085:
Impact: CVE-2024-37085 is an authentication bypass vulnerability impacting VMware ESXi and VMware Cloud Foundation. Attackers with sufficient Active Directory (AD) permissions can exploit this vulnerability to gain unauthorized full administrative access to an ESXi host. This is achieved by recreating the ‘ESX Admins’ AD group—even if previously deleted—because ESXi hosts joined to AD automatically and insecurely grant admin privileges to that group by default. This issue has been widely exploited by ransomware groups, enabling them to achieve mass encryption of virtualized environments. The vulnerability primarily affects ESXi 8.0 (fixed in ESXi80U3-24022510), ESXi 7.0 (no patch planned), VMware Cloud Foundation 5.x (fixed in 5.2), and Cloud Foundation 4.x (no patch planned). Systems exposed to the internet or left unpatched are at risk of complete compromise and data loss through ransomware campaigns.
Recommended Solutions: Upgrade to VMware ESXi 8.0 Update 3 (ESXi80U3-24022510) or VMware Cloud Foundation 5.2 as soon as possible; there is no patch planned for ESXi 7.0 and Cloud Foundation 4.x, so administrators of these products should apply Broadcom’s recommended configuration workarounds involving secure default settings for AD group privileges; remove unnecessary exposure of ESXi servers to the public internet; implement Microsoft’s mitigation guidance and monitor domain group memberships and administrator accounts for anomalies.
Measure, Communicate, and Eliminate Your Risk from Scattered Spider with Qualys
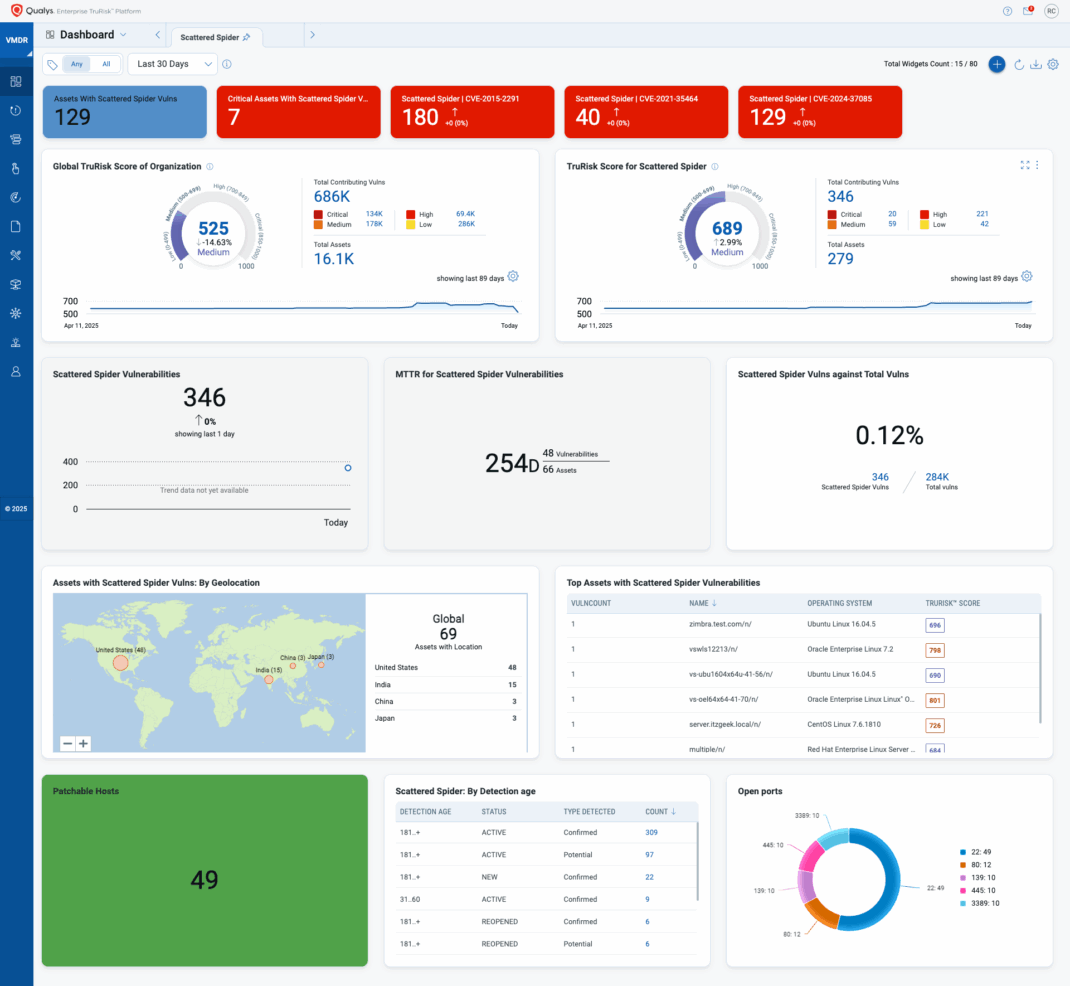
To take action against Scattered Spider attacks in your network, Qualys offers several options:
- Using Qualys VMDR (Vulnerability Management, Detection and Response), you can rapidly identify and prioritize your vulnerabilities through scanning your environment for the specific QIDs tied to Scattered Spider’s known exploits.
- Utilize TruRisk scoring to prioritize your remediation using filters such as real-world exploitability and business criticality.
- Monitor your internet-facing exposure using Qualys’ CyberSecurity Asset Management (CSAM) to discover and classify all internet-facing assets and detect misconfigurations and high-risk services.
New to Qualys? Visit our website to find out more about our products.