Compliance Without Coverage is a Risk: How to Close the Gaps with Qualys Policy Audit
Modern compliance and security programs often fail due to technology blind spots rather than weak policies or procedures. Today’s IT environments, spanning hybrid, cloud-native, containerized, and legacy platforms, introduce complexities that traditional compliance tools can’t fully address. When compliance solutions overlook parts of your infrastructure, it leads to incomplete audits, increased manual work, security risks, and regulatory exposure.
Qualys Policy Audit addresses this challenge by providing unified, automated compliance coverage across more than 500 technologies, including operating systems, databases, middleware, cloud infrastructure, containers, and legacy systems, offering one of the broadest technology coverage footprints in the industry. With continuous alignment to global frameworks, built-in risk prioritization, and automated visibility into configuration states, Qualys Policy Audit ensures organizations eliminate audit gaps, reduce risk, and maintain compliance seamlessly as their IT infrastructure evolves.
This level of technology coverage ensures that security posture can be assessed uniformly and reliably, closing compliance gaps, reducing complexity and delivering operational efficiency at scale.
The Challenge: Lack of Comprehensive Compliance Coverage for Complex IT Environments
Securing modern enterprises means continuously managing configurations across increasingly diverse and fragmented IT environments. Traditional compliance solutions often fall short because they don’t adequately support the full spectrum of technologies in use today, from mainstream systems to specialized legacy platforms.
Without comprehensive technology support, critical gaps emerge, particularly in environments running legacy UNIX systems, specialized databases, containerized workloads, and cloud-native infrastructure. These unsupported platforms create significant blind spots, resulting in incomplete audits, increased manual intervention, heightened compliance risk, and greater exposure to security incidents and regulatory penalties.
Organizations need compliance solutions that deliver both extensive coverage (breadth) and detailed assessment capabilities (depth), ensuring that no platform, regardless of its age, specialization, or location, is left unsecured or unmonitored.
Unified Compliance Across 500+ Technologies
Qualys Policy Audit was designed specifically to address these challenges, offering extensive technology support across more than 500 distinct platforms and environments, making it one of the most comprehensive and adaptable compliance solutions available today.
Its comprehensive coverage spans a wide range of asset classes, including operating systems, databases, middleware, web servers, network infrastructure, directory and identity services, and cloud platforms. This breadth includes not only widely adopted platforms like Windows Server, Red Hat Enterprise Linux, and macOS, but also specialized and legacy systems such as AIX, Solaris, HP-UX, and RACF z/OS—platforms often overlooked by competing solutions.
Unlike traditional scanners and agent-based solutions that fall short in fragmented environments, Qualys Policy Audit provides unified visibility and deep configuration-state assessment, closing audit gaps and eliminating blind spots across your entire IT stack.
Qualys Policy Audit extends beyond standard agent-based or scanner-based assessments. It goes further with Out-of-Band Configuration Assessment (OCA), evaluating isolated and high-security environments that aren’t remotely accessible by traditional tools. Even air-gapped and highly sensitive assets stay continuously monitored, leaving no gaps uncovered.
As enterprises continue to adopt emerging technologies to drive innovation, Qualys PA evolves its platform support, enabling your compliance efforts to scale seamlessly without sacrificing security posture or governance controls.
Built-in Alignment with Leading Security and Compliance Standards
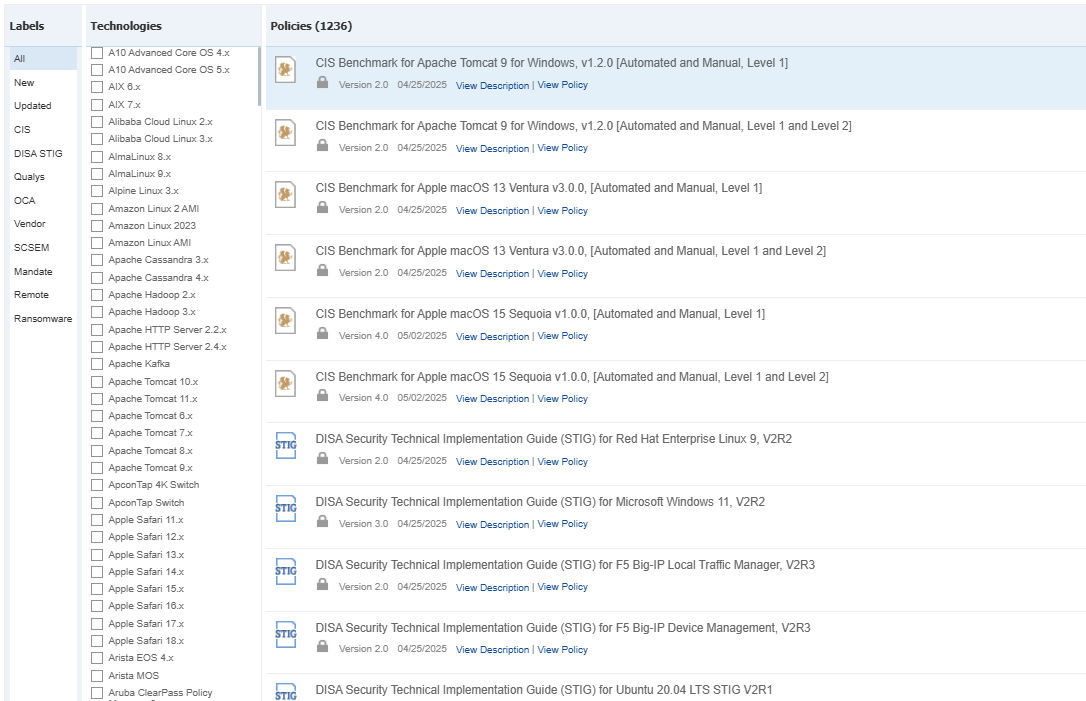
A compliance tool is only effective if it aligns closely with real-world requirements and auditor expectations. Qualys Policy Audit comes pre-loaded with over 1,200 ready-to-use policies mapped directly to globally recognized frameworks, including:
- CIS Benchmarks
- NIST SP 800-53
- ISO/IEC 27001
- PCI DSS
- GDPR
- DISA STIGs
These policies aren’t just checklists. They’re practical, actionable assessments you can deploy immediately, without lengthy interpretation or manual mapping.
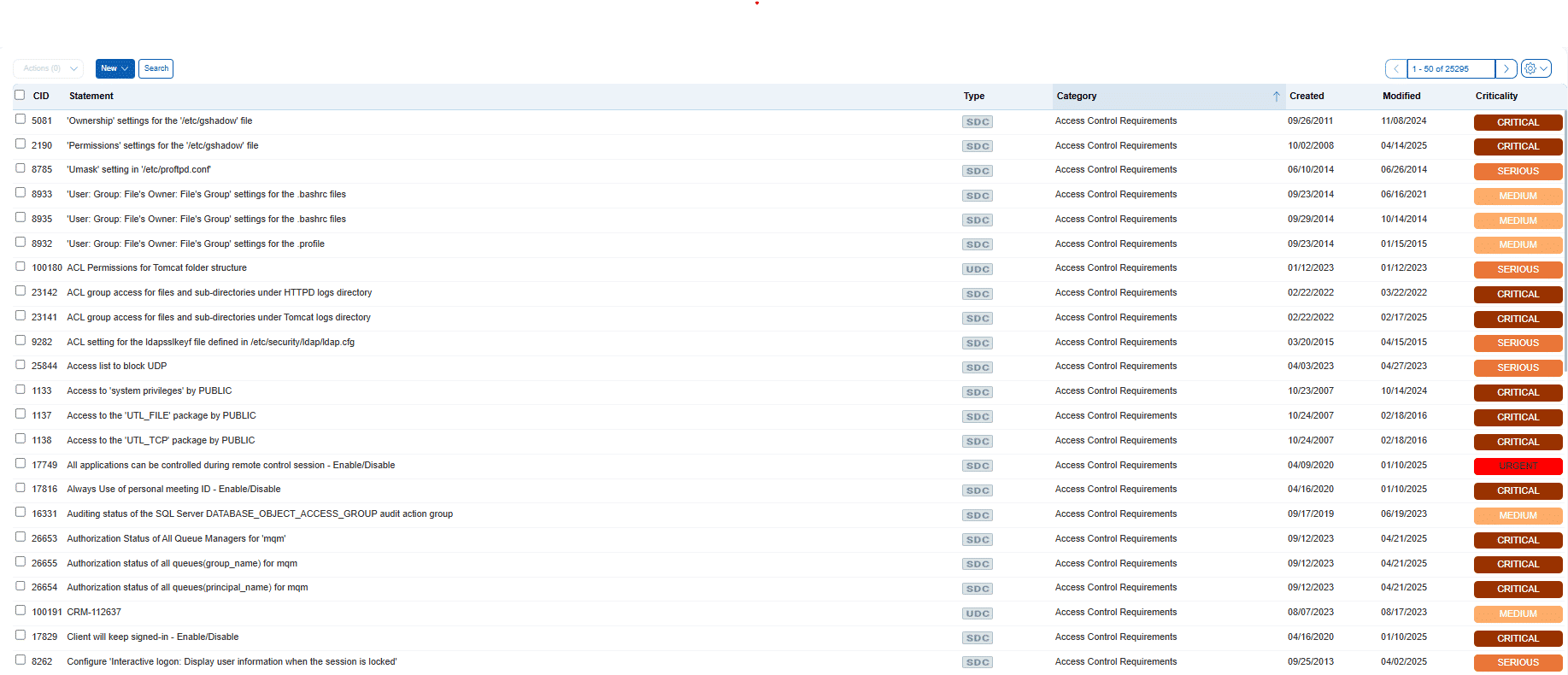
Behind these policies is an extensive library of over 25,000 technical controls enabling accurate, detailed checks of security configurations across all your platforms, from Active Directory and middleware to cloud VMs and mainframes.
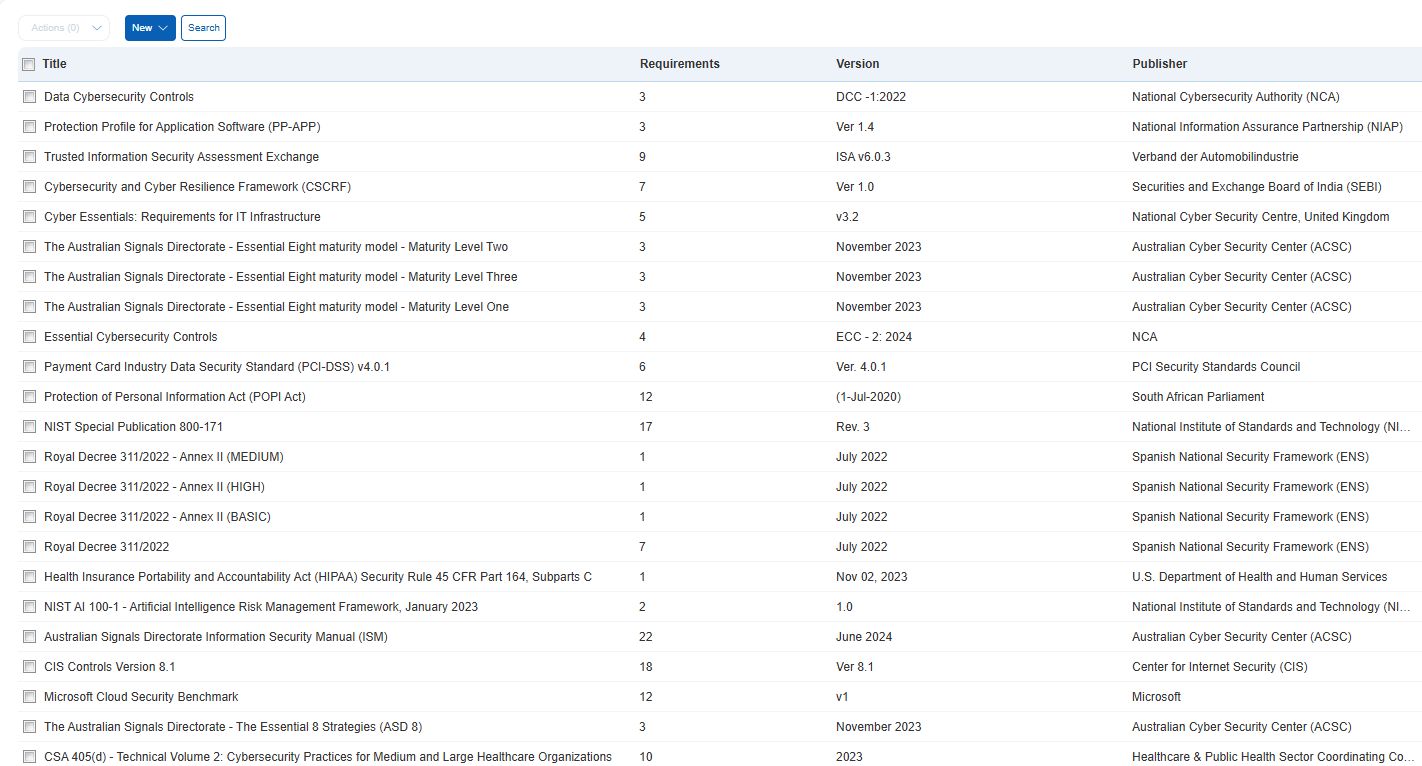
Many organizations require controls that reflect internal standards. Qualys supports this with nearly 100 customizable framework templates mapped to both industry and enterprise policies, enabling rapid compliance implementation at any scale.
From Static Assessments to Real-Time, Risk-Informed Decisions
Compliance should do more than meet regulatory requirements. It should proactively shape your risk strategy.
As part of the Qualys Enterprise TruRisk™ Platform, Qualys Policy Audit integrates seamlessly with vulnerability management, asset inventory, threat intelligence, and broader risk analytics. Every misconfiguration, policy violation, or control failure becomes part of a holistic risk view, empowering teams to prioritize issues based on actual business impact rather than generic severity ratings.
This shifts your compliance program from static checks to dynamic, real-time, risk-informed decision-making, enabling security and compliance teams to demonstrate clearly to executives, auditors, and regulators that your controls are comprehensive, adaptive, and truly effective.
The Business Impact of Comprehensive Compliance Coverage
Broad technology support in a compliance solution is critical for overall enterprise risk reduction. By eliminating visibility gaps across legacy, modern and hybrid IT environments, Qualys Policy Audit:
- Consolidates compliance monitoring onto a single unified platform
- Automates time-consuming manual tasks, dramatically reducing tool sprawl
- Delivers real-time visibility and prioritization for faster, more informed remediation
- Provides actionable intelligence to strengthen your overall security posture
- Supports agile cloud transformation without compromising governance
This broad coverage directly supports business goals by aligning security baselines with both internal governance and external regulatory requirements. It ensures that compliance programs are enforceable, scalable, and auditable no matter how fast technology evolves.
Ultimately, comprehensive technology support offered by Qualys Policy Audit translates into operational, continuous compliance readiness and reduced business risk. With Qualys, compliance is an integral part of protecting your business, and strengthening your overall security posture without compromise.
Want to explore the full capabilities of Qualys Policy Audit?