Navigating SEBI’s Cloud Security Requirements: A Guide for Regulated Entities

Table of Contents
- Introduction
- Why SEBIs Guidelines Matter
- Who Are Regulated Entities (REs)?
- The Core Objectives and Pillars of SEBIs Cybersecurity Guidelines
- From Regulation to Practice: Mapping SEBIs Requirements to Cloud Security
- Principle 6.2 in Action: How Qualys Helps REs Meet SEBIs Cloud Security Controls
- Qualys TotalCloud: Your Comprehensive Compliance Partner
- Detailed Mapping of SEBI Guidelines to Qualys TotalCloud Features
- Use Qualys TotalCloud to Achieve SEBI Continuous Compliance
- Contributors:
Overview:
- Who is impacted: The Securities and Exchange Board of India (SEBI) is the primary regulatory authority for the securities market in India. It was established to protect investor interests and promote market development, but its guidelines also impact cybersecurity professionals at regulated entities (REs) operating in India, especially those with cloud infrastructures.
- Why now: India’s securities market is decisively cloud-powered, which means security controls and audit readiness must keep pace. It’s estimated that 80% of corporate banks in India have migrated their operations to the cloud.
- What SEBI requires: Encryption, identity governance, continuous monitoring, incident readiness, and third-party oversight, all implemented and demonstrable.
- How to ensure compliance: Turn policy into enforceable, day-to-day controls across AWS, Azure, GCP, and on-premises environments.
- Where Qualys helps: Unified asset visibility, misconfiguration and identity risk detection, vulnerability and patch management, policy compliance, and exportable audit evidence delivered through Qualys TotalCloud™ and the broader platform.
Introduction
Cybersecurity in India’s securities market is under the spotlight like never before. As more tools and services shift to cloud-hosted infrastructure, the benefits of scale and agility come with new risks. Even small lapses can lead to significant financial and reputational damage.
At a recent address, SEBI Chief Tuhin Kanta Pandey issued a sharp reminder of how fragile today’s digital infrastructure can be:
“A small glitch in a trading algorithm can trigger market disruption in milliseconds. A misconfigured server can give malicious actors a way in. A compromised account can lead to damaging data leaks.”
To improve stability and trust in the industry, SEBI introduced the Framework for Adoption of Cloud Services by Regulated Entities (REs), published in Circular No.: SEBI/HO/ITD/ITD_VAPT/P/CIR/2023/033. The framework sets clear expectations for how REs must secure cloud workloads, applications, and data, helping close gaps that traditional approaches often miss.
Why SEBI’s Guidelines Matter
Cybersecurity in financial markets has always been high stakes, but the shift to cloud has magnified the risks. In his address, Pandey highlighted the infamous Knight Capital incident of 2012, where a dormant trading algorithm was accidentally reactivated—causing a $440 million loss in just 45 minutes. He also pointed to the 2010 breach of a major US stock exchange where hackers compromised a board portal, shaking investor confidence despite trading operations remaining unaffected.
His message is clear: even small mistakes can have big consequences. As India’s securities market increasingly relies on the cloud, REs must strengthen their defenses, not just against external attacks, but also against internal misconfigurations, faulty application programming interfaces (APIs), and compromised accounts.
SEBI’s framework directly addresses these concerns, setting expectations for data confidentiality, operational resilience, supply chain security, and more.
Who Are Regulated Entities (REs)?
Under SEBI, REs include stock exchanges, depositories, asset management companies, and other pivotal organizations in the securities market. For these entities, compliance with SEBI’s guidelines is critical to maintaining the trust and integrity of the financial ecosystem. Non-compliance can lead to severe financial, legal, and reputational consequences, making it imperative for REs to fortify their cloud security posture in alignment with SEBI.
The Core Objectives and Pillars of SEBI’s Cybersecurity Guidelines
Beyond best practices, SEBI’s guidelines are targeted responses to the real-world risks financial institutions face as they expand across hybrid and multi-cloud environments. The key objectives of these guidelines include:
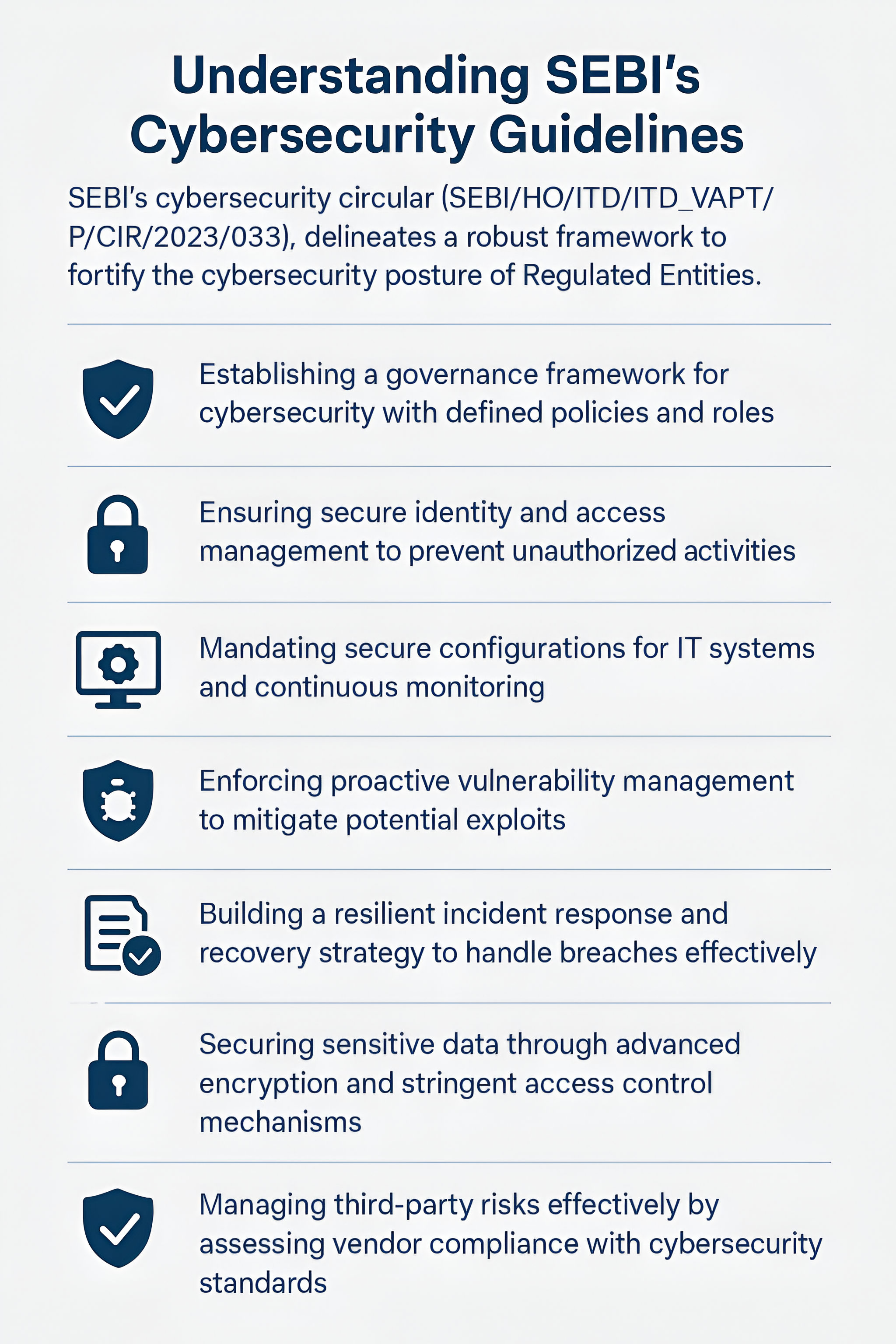
To achieve these objectives, SEBI’s cybersecurity framework is built on a set of core pillars that address the most critical areas of cloud risk. These pillars focus on safeguarding sensitive investor data, maintaining consistent protections across environments, ensuring operational resilience, managing third-party risk, and enabling real-time threat detection.
Data Confidentiality & Investor Trust
Investor data is one of the most sensitive forms of information. In the cloud, this data often moves across distributed, multi-tenant systems, sometimes spanning multiple geographies.
SEBI’s mandates for encryption, identity management, and access control ensure that even in the shared responsibility model of the cloud, sensitive trading and investor data remain protected from both external attackers and insider threats.
Unified Security Across Hybrid & Multi-Cloud
Market intermediaries rarely operate in a single environment — AWS, Azure, GCP, and on-premise data centers often work together. Without regulatory baselines, these environments could have inconsistent controls.
SEBI’s focus on audits, logging, and configuration baselines ensures that workloads meet a consistent security standard, no matter where they live.
Operational Resilience in a High-Speed Market
Downtime —whether due to ransomware, a misconfigured firewall, or a cloud region failure—can have far-reaching consequences such as trading disruptions and settlement failures that destabilize the financial ecosystem.
SEBI’s requirements for business continuity, disaster recovery, and failover readiness help prevent downtime by mapping to cloud strategies like multi-region deployments, geo-redundant backups, and regular DR drills.
Managing Third-Party & Supply Chain Risks
Modern cloud deployments rely heavily on APIs, managed services, and third-party SaaS tools. This interconnectedness creates new supply chain vulnerabilities.
SEBI’s vendor due diligence clauses ensure that third-party cloud services are held to the same security standards as the financial institution, preventing a small vendor weakness from becoming a systemic risk.
Proactive Threat Detection
In financial markets, the cost of delayed detection is high. Even brief gaps in visibility can allow threats to spread and compromise sensitive information before remediation steps can be taken.
SEBI’s push for real-time monitoring, anomaly detection, and incident reporting translates into cloud-native measures like SIEM/SOAR integrations, GuardDuty alerts, and automated incident response workflows.
From Regulation to Practice: Mapping SEBI’s Requirements to Cloud Security
SEBI’s framework sets clear expectations for what REs must achieve to strengthen their cloud security posture. The table below pairs each requirement with our recommended best practices, plus why they are critical in today’s cloud environments.
| SEBI Cybersecurity Requirement | Cloud Security Best Practice | Why It Matters in the Cloud |
| Data Encryption at Rest & In Transit | Use AWS KMS, Azure Key Vault, GCP Cloud KMS; enable TLS 1.2+; encrypt object storage & databases | Protects investor/trading data in multi-tenant environments |
| Strong Access Control & IAM | Enforce least privilege, enable multi-factor authentication (MFA), apply role-based access controls (RBAC) in Kubernetes and virtual machines (VMs) | Prevents unauthorized access via compromised credentials |
| Regular Security Audits & Compliance Checks | Automate CIS Benchmark scans; use AWS Config, Azure Security Center, GCP SCC | Maintains consistent security posture across environments |
| Incident Detection & Response | Enable CloudTrail, Activity Logs, Audit Logs; integrate security information and event management (SIEM) and security orchestration, automation, and response (SOAR) tools | Reduces breach detection-to-response time |
| Disaster Recovery & Business Continuity | Deploy workloads in multi-availability zone (AZ)/region; automate backups; run disaster recovery (DR) drills | Minimizes downtime during outages or attacks |
| Vendor & Third-Party Risk Management | Review vendor security; demand SOC 2 / ISO 27001; secure APIs | Prevents supply chain vulnerabilities |
| Threat Intelligence & Anomaly Detection | Integrate threat feeds; enable anomaly detection on IAM & network traffic | Identifies threats before major damage occurs |
| Patch & Vulnerability Management | Automate operating system (OS) & container patching; scan images before deployment | Closes known vulnerabilities before they’re exploited |
Principle 6.2 in Action: How Qualys Helps REs Meet SEBI’s Cloud Security Controls
Cloud adoption brings agility, scalability, and cost efficiency, but it also introduces shared security responsibilities. While Cloud Service Providers (CSPs) secure the infrastructure they manage, SEBI’s Principle 6.2 – Security in the Cloud places a clear obligation on REs to safeguard their own workloads, applications, and data in the cloud.
However, translating these requirements into day-to-day operations can be challenging. Many REs struggle with fragmented toolsets that lack interoperability, poor visibility across hybrid and multi-cloud environments, and the highly manual effort required to maintain continuous compliance.
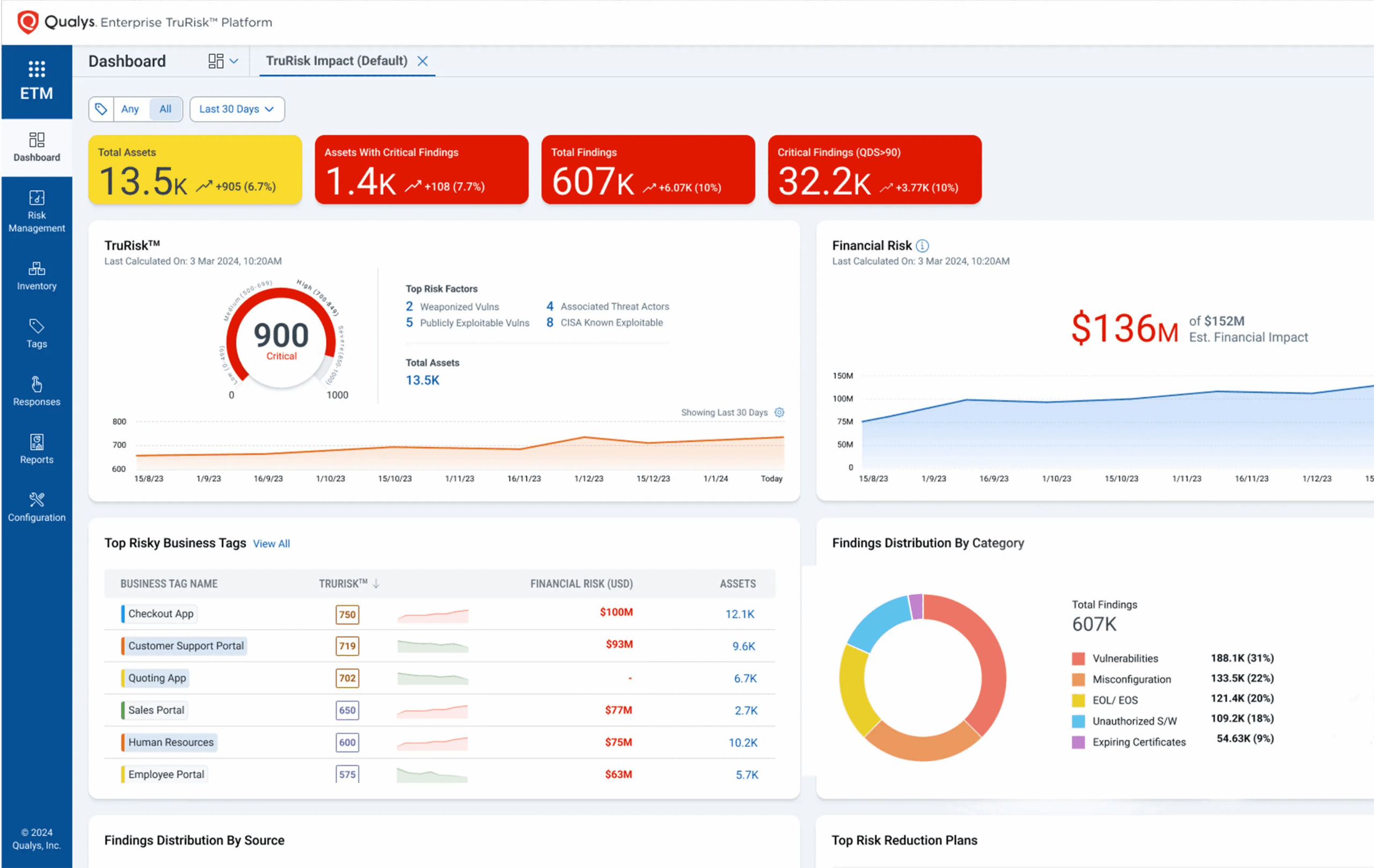
The Qualys Enterprise TruRiskTM Platform helps address these challenges by unifying the security controls outlined in Principle 6.2 into a single, integrated platform that closes visibility gaps, reduces tool sprawl, and automates compliance tasks to lighten the operational load.
The Risk Operations Center (ROC) – powered by Enterprise TruRisk™ Management (ETM), integrates real-time threat intelligence, vulnerability data, and business context into a unified risk view.
As organizations adopt cloud infrastructure and digital transformation accelerates, attack surfaces expand. Meanwhile, most breaches still exploit known, unaddressed vulnerabilities. A Risk Operations Center addresses these challenges by:
- Consolidating attack and risk surface data into a single operational view
- Prioritizing vulnerabilities based on likelihood of exploitation and business impact
- Orchestrating automated, risk-based remediation
- Communicating security posture in executive-friendly, financial terms
How the Qualys platform streamlines compliance for SEBI’s requirements:
1. Vulnerability & Patch Management
SEBI suggests that every RE must maintain a strong patch management process for the systems they manage in the cloud. Regular vulnerability scanning, timely patching of operating systems and applications, and proactive hardening of services reduce the attack surface and help prevent known exploits.
–> Qualys Vulnerability Management, Detection, and Response (VMDR) continuously scans, detects, prioritizes, and facilitates remediation of vulnerabilities. Patch Management enables automated patch deployment and configuration fixes across OS and third-party applications, with integrated workflows for rapid response.
2. Regular Vulnerability Assessments and Penetration Testing (VAPT)
SEBI expects REs to conduct periodic VAPT exercises to uncover misconfigurations, insecure APIs, or weak access policies. These tests should be carried out before new systems go live and at defined intervals, ensuring that vulnerabilities are identified and fixed well within regulatory timelines.
–> VMDR and Web Application Scanning (WAS) conduct automated, scalable scans for vulnerabilities. Integration with partners allows orchestration of advanced penetration tests for deeper exploitation validation.
3. Incident Management and SOC Integration
SEBI says that incidents in the cloud must be treated with urgency. REs should have a well-defined incident response plan, tightly integrated with their Security Operations Center (SOC). Cloud workloads should be monitored in real time, with alerts and events feeding directly into SOC workflows for rapid detection, investigation, and response.
–> Qualys provides real-time detection, alerts, and workflow automation by integrating Qualys’ datasets with popular SIEM and SOC solutions.
4. Continuous Compliance Monitoring
Cloud environments change frequently, making static security checks insufficient. SEBI emphasizes ongoing monitoring of cloud resources, ensuring that configurations, access controls, and CSP compliance remain aligned with SEBI’s cybersecurity guidelines at all times.
–> Qualys TotalCloud CSPM continuously discovers and monitors cloud assets for misconfigurations, while KSPM uses Cluster Sensors with CIS Benchmarks to secure Kubernetes environments, enforce policies, and ensure continuous compliance across hybrid and managed setups.
5. Secure User Management
Access to CSP-managed resources must follow strict controls based on the principle of least privilege. SEBI says administrators and privileged users should have time-bound, justifiable access, with mandatory MFA and comprehensive audit logging.
–> Qualys TotalCloud includes Cloud Infrastructure Entitlement Management (CIEM) capabilities that provide deep visibility into identities, roles, and permissions across multi-cloud environments. It automatically detects excessive, unused, or misconfigured privileges, helping organizations enforce the principle of least privilege.
6. Security of Interfaces
Interfaces are entry points that attackers can exploit. SEBI outlines three specific focus areas:
Management Interfaces: Must be protected with MFA, firewalls, and restricted network access.
Internet-Facing Interfaces: Should be secured with web application firewalls (WAF), anti-distributed denial-of-service attack (DDoS) protections, API gateways, and encrypted connections.
Inter-Organization Interfaces: Links between REs, CSPs, or third parties must be secured using internet security protocol (IPSEC), virtual private networks (VPNs), or equivalent safeguards to prevent interception or unauthorized access.
–> Qualys provides controls via strong authentication, access controls, and audit logs, and automates discovery and protection of public-facing assets using CyberSecurity Asset Management (CSAM) with External Attack Surface Management (EASM), VMDR, and tagging.
7. Secure Software Development
When CSPs provide platform-level services, they must adopt secure development practices, embedding security from design to deployment. SEBI expects CSPs to implement zero-trust principles, secure APIs, and fine-grained access control mechanisms to reduce risks.
–> Qualys Security Configuration Assessment (SCA) helps check security configurations against best practices and scan code/applications for vulnerabilities throughout the SDLC.
8. Managed Service Provider (MSP) and System Integrator (SI)
Engaging MSPs or SIs adds complexity. SEBI says CSPs must have clear, enforceable agreements with their partners or subcontractors to ensure that security controls are consistently applied across the supply chain.
9. Encryption and Cryptographic Key Management
CSPs handling platform-level encryption must manage the full lifecycle of cryptographic keys securely. REs should ensure that encryption practices meet SEBI’s data confidentiality, privacy, and integrity standards.
–> Qualys supports CSP-native Key Management Services (KMS) integrations and enforces encryption policies across cloud resources via security controls in TotalCloud.
10. Endpoint Security
Endpoints and networks connecting to cloud services must not be weak links. SEBI recommends implementing antivirus tools, Data Loss Prevention (DLP), micro-segmentation of networks, and monitoring tools like cloud access security broker (CASB) or secure access service edge (SASE) solutions for visibility and policy enforcement.
–> Qualys Cloud Agent and Patch Management provide a lightweight agent that delivers asset inventory, vulnerability scanning, and patching across Windows, Linux, and Mac endpoints, regardless of location.
11. Network Security
SEBI says that REs must have a robust, isolated, and encrypted backup and recovery plan. Backups should be tested regularly to ensure that ransomware, accidental deletions, or cloud outages do not disrupt critical business operations.
–> Qualys validates backup integrity, enforces encryption policies, and provides monitoring to ensure recovery systems remain secure and operational.
Qualys TotalCloud: Your Comprehensive Compliance Partner
Qualys TotalCloud is meticulously designed to simplify and streamline the cybersecurity and compliance journey for REs. Here’s how it addresses SEBI’s key requirements:
- Governance Framework:
- Provides centralized dashboards for unified visibility across all assets.
- Enables role-based access controls to define and enforce security governance policies.
- Ensures comprehensive audit trails for accountability and transparency.
- IAM:
- Detects toxic combinations such as privileged users without MFA.
- Alerts for public exposure of sensitive data to mitigate identity-related risks.
- Continuously monitors user activities to prevent unauthorized actions.
- Secure Configurations and Continuous Monitoring:
- Automates secure baseline configurations with pre-defined templates.
- Continuously monitors cloud resources to detect and remediate misconfigurations in real-time, ensuring a secure operational state.
- Vulnerability Management:
- Conducts comprehensive scans to identify and prioritize vulnerabilities based on risk.
- Integrates patch management workflows to expedite remediation efforts, reducing the attack surface effectively.
- Incident Response and Recovery:
- Provides advanced detection and response capabilities with actionable insights.
- Offers built-in workflows to streamline recovery processes and minimize downtime, ensuring business continuity.
- Data Protection:
- Enforces encryption policies for data at rest and in transit to prevent unauthorized access.
- Tracks compliance with data protection regulations through intuitive reporting and real-time analytics.
- Third-Party Risk Management:
- Conducts continuous security assessments of third-party integrations and vendors.
- Ensures vendor compliance with SEBI’s cybersecurity standards through automated evaluations.
Detailed Mapping of SEBI Guidelines to Qualys TotalCloud Features
| SEBI Requirement | Qualys TotalCloud Capability |
|---|---|
| Governance Framework | Centralized dashboards, role-based access controls |
| IAM | MFA enforcement, toxic combination detection |
| Secure Configurations | Automated secure baseline templates, real-time misconfiguration alerts |
| Vulnerability Management | Comprehensive scans, integrated patch management |
| Incident Response and Recovery | Advanced detection, actionable response workflows |
| Data Protection | Encryption enforcement, compliance tracking |
| Third-Party Risk Management | Continuous vendor assessments, compliance monitoring |
Use Qualys TotalCloud to Achieve SEBI Continuous Compliance
As REs modernize their infrastructure, cloud security compliance has become a 24/7 commitment. Qualys TotalCloud makes the journey toward continuous compliance easier by unifying SEBI-aligned security controls into a single, integrated platform that offers benefits such as:
- Ease of Use: Intuitive interfaces and automation reduce the complexity of security management.
- Cost Efficiency: Consolidate multiple security tools into a single solution, saving costs and improving operational efficiency.
- Proactive Insights: Stay ahead of potential threats with real-time intelligence and proactive alerts tailored to SEBI requirements.
- Future-Ready Security: Regular updates and enhancements ensure your organization remains compliant with evolving guidelines and threats.
Qualys TotalCloud is the ultimate ally for REs striving to achieve and maintain SEBI compliance. Empower your organization with the tools, visibility, and confidence needed to thrive in today’s dynamic threat landscape.
Try TotalCloud free for 30 days.
Contributors:
- Shilpa Gite – Senior Manager, Cloud Security Compliance
- Atul Parmar – Senior Security Analyst, Cloud
- Yash Jhunjhunwala – Lead SME, Cloud Security Solutions