Ensuring Safe and Reliable Updates with Qualys TruRisk™ Manifest Version Control
Table of Contents
- Why Update Validation Matters as Much as Speed
- Core Capabilities of Manifest Version Control in TruRisk Platform
- Progressive Rollouts and Canary Testing (Operational Patterns)
- Why Manifest Version Control Matters
- Accuracy Engineered into Every Detection
- Agent Version Control for Consistency and Security
- Always-On Resilience with Self-Healing Agents
- Achieving Precision with Custom Assessment and Remediation
- The Bigger Picture of Risk-Aligned Security
- Conclusion: End-to-End Resilience and Control
The Fragility of “One Bad Update”
In cybersecurity, speed is non-negotiable. New vulnerabilities surface daily, and enterprises expect coverage the moment exploits are in the wild. For years, the mantra was simple: push signatures fast, and you reduce risk. Faster updates meant faster protection.
But speed without guardrails introduces fragility. A single flawed update can cascade across thousands of endpoints, halting business operations and creating costly downtime. According to Veeam’s 2019 Cloud Data Management Report, enterprises experience multiple unplanned outages each year, with each hour of downtime carrying an average six-figure cost for many organizations. For large enterprises, that figure quickly climbs into hundreds of thousands, even millions, per hour.
That reality has prompted an industry-wide reckoning: resilience matters just as much as speed.
Why Update Validation Matters as Much as Speed
Today, organizations no longer view immediate updates as an unquestioned good. The conversation has shifted to a trade-off that must be actively managed:
- Immediate Deployment: “We want new signatures as soon as they’re available.”
- Safe Deployment: “We want updates applied only once they’ve been validated in our operational context.”
Security teams operate under the pressure of zero-day exploits, where every hour matters, while operations teams must protect uptime for customer-facing systems and critical business processes. Add to that hybrid architectures, where Windows servers, cloud workloads, containers, and legacy host types coexist, and you have an environment where updates can behave differently in every segment.
Most platforms offer limited controls: an all-or-nothing push, or a manual, high-friction process. Without staging, canaries, or the ability to prevent a manifest from applying to certain assets, customers are left balancing risk and exposure without the necessary tools.
Other industries have already learned this lesson. In aviation, for example, new systems are staged in simulators and test flights before widespread adoption. In financial services, trading systems are stress-tested under load before live deployment. Both sectors know that speed is meaningless without safeguards, and security operations are no different. What’s emerging now in cybersecurity is the same principle: resilience must be engineered into the process, not bolted on after failure.
Manifest Version Control in the Qualys TruRisk™ Platform
The Qualys TruRisk Platform resolves this tension by building resilience into the update lifecycle itself. Manifest Version Control (MVC) is the mechanism that turns manifest updates from an uncontrollable vendor push into a governed, observable, and reversible operational process.
Core Capabilities of Manifest Version Control in TruRisk™ Platform
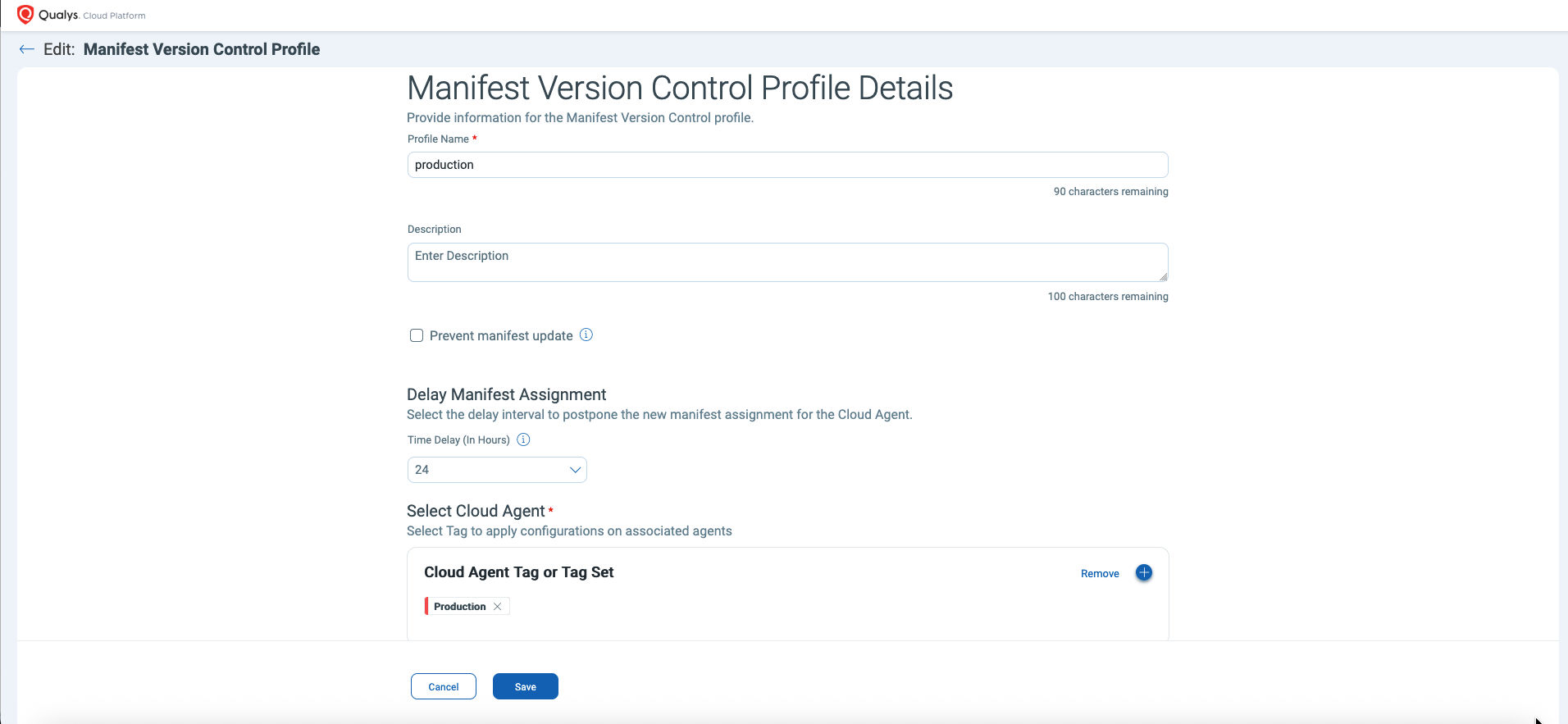
- Delay Manifest Assignment
- Introduce a configurable 0–48 hour buffer between release and deployment.
- Align updates with maintenance windows, change management approvals, and operational readiness checks.
- Stage adoption across environments so new signatures land first in test or canary groups before reaching production.
- Use the buffer to run smoke tests and monitor telemetry, catching instability before broad rollout.
- Prevent Manifest Update
- Temporarily block specific manifests from applying to chosen assets or groups.
- Target controls by profile, OS, region, or any grouping that reflects operational risk.
- Validate updates safely in dev/test while keeping production locked until issues are resolved.
- Re-enable a manifest when stable or roll forward a corrected version without exposing live systems to disruption.
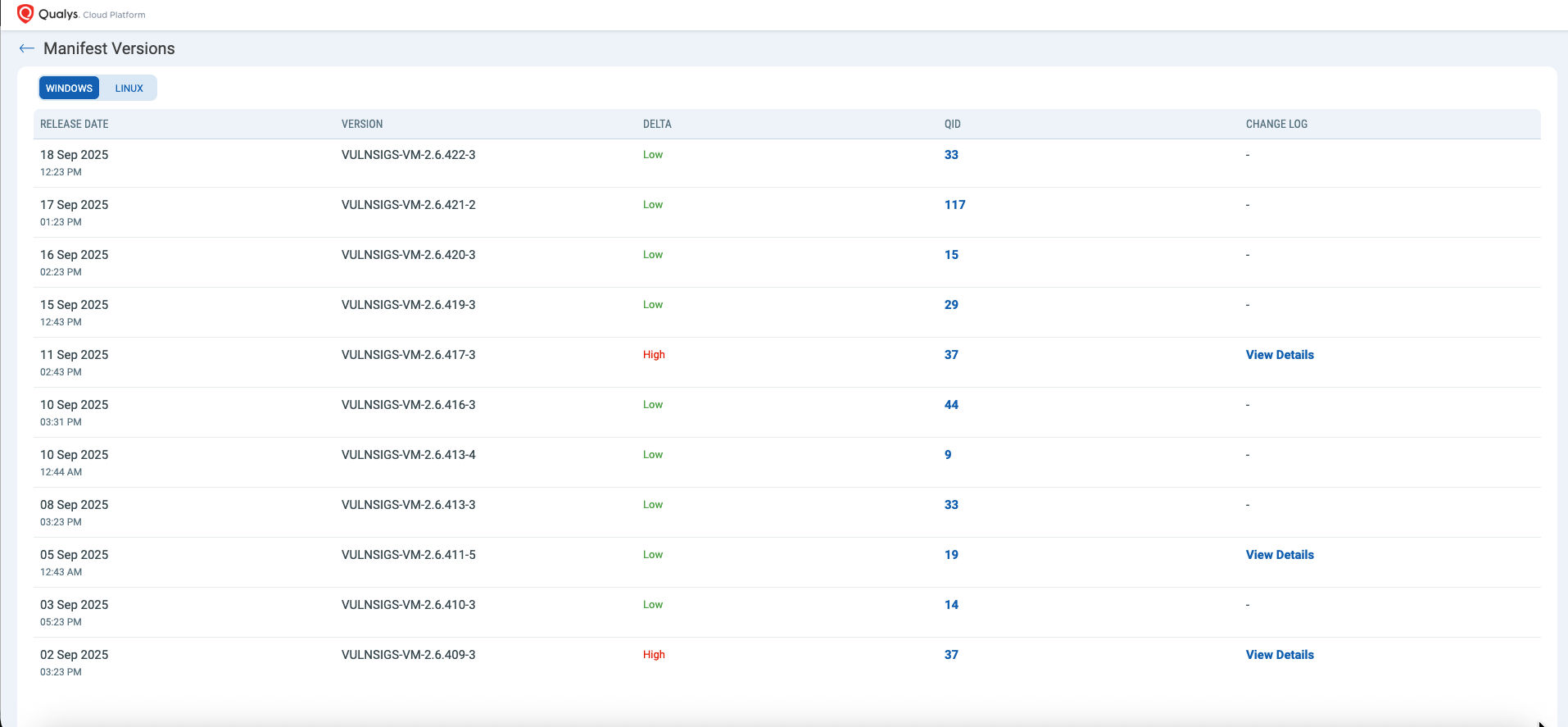
- Manifest Insights
- Provide clear metadata, including release dates, version deltas, QID lists, and change logs.
- Offer a human-readable summary of what each signature does and why it matters.
- Surface delta analysis and QID correlation so teams can distinguish between new and modified detections.
- Tie insights to telemetry and health signals, enabling rollout decisions based on evidence rather than guesswork.
Watch Webinar
Join our webinar to see how Manifest Version Control in the Qualys TruRisk™ Platform keeps your updates safe, staged, and resilient
Progressive Rollouts and Canary Testing (Operational Patterns)
Beyond delay and prevention, MVC enables progressive rollout patterns that mirror best practices in modern software delivery:
- Canary groups: deploy a manifest to a small representative subset, monitor errors and performance, then expand.
- Waves: roll out in defined waves (for example: 1% → 10% → 50% → 100%) to reduce blast radius.
- Telemetry gates: automatically pause or stop rollout if predefined health signals cross thresholds.
Real-World Example
Consider an enterprise with distinct non-production and production profiles. In non-production, updates are applied immediately to validate detection accuracy and compatibility. In production, updates are delayed by 24 hours while canary groups and telemetry checks run.
If an issue is observed in non-production or in a canary cohort, for example, a detection that triggers excessive scanning load or a false positive affecting a business application, operators can activate Prevent Manifest Update for production profiles. Qualys engineering can then investigate, patch the manifest, and release a corrected version. Because the rollout was staged, the business avoided widespread disruption while still benefiting from fast detection once the issue was resolved.
Why Manifest Version Control Matters
Manifest Version Control addresses a set of concrete challenges enterprises face:
- Resilience Without Sacrificing Speed: MVC lets security teams receive signatures rapidly while operations control when and where they apply.
- Minimized Business Risk: By avoiding sudden, unverified pushes to production, organizations reduce the chance of outages that carry six-figure impacts.
- Granular Rollouts: Wave and canary strategies limit blast radius and surface compatibility issues early.
- Audit-Ready Transparency: Detailed change logs and QID lists support compliance and post-incident analysis.
- Operational Confidence: Teams move from reactive firefighting to evidence-driven, strategic update management.
Accuracy Engineered into Every Detection
Resilience starts with the code. Every Qualys detection (QID) is created and verified through a disciplined, multi-step process:
- Authoring: Engineering authors the detection and documents expected behavior and impact.
- Peer Review: Human reviewers validate logic, edge cases, and potential performance implications.
- QA and Regression: Automated and manual tests verify detection accuracy, performance overhead, and compatibility across OS and agent versions.
- Staging: New signatures are exercised in lab and hybrid environments, including targeted functional and load tests.
- Release: Only after passing these gates does a signature enter a production manifest, and even then, MVC governs its rollout.
For example, a detection that requires a new parsing command is first committed to a test branch. Engineers run regression scans across representative OS images and agent versions to validate both detection fidelity and resource overhead. Any performance degradation triggers a remediation loop before the signature is promoted.
Agent Version Control for Consistency and Security
Engineering validation in isolation is necessary but not sufficient. TruRisk™ Labs maintains a portfolio of environments that mirrors customer diversity: virtualization stacks (VMware, KVM), cloud providers, containers (KubeVirt), legacy hosts (Solaris, PowerVM), and bare metal.
With roughly a thousand on-premises instances and automated provisioning workflows, Labs can construct large hybrid environments quickly, enabling broad validation far faster than ad-hoc customer testing permits. Continuous integration pipelines exercise signatures under realistic load and interaction patterns, surfacing corner cases early.
For zero-day vulnerabilities, Labs prioritizes creating the required configuration and test harnesses the same day to accelerate QID release, while ensuring changes pass the multi-step validation above.
Always-On Resilience with Self-Healing Agents
Platform resilience is incomplete without resilient agents. The TruRisk™ Platform extends resilience to the agent level. Qualys Cloud Agents are designed to self-heal, eliminating the need for manual reinstalls or downtime.
Key aspects include:
- Immediate Recovery: Agents fetch latest configs and manifests on restart.
- Smart Retry: Failed requests retry automatically.
- Adaptive Communication: Proxy handling and backoff prevent bottlenecks.
- Safe Data Handling: Pending scans and updates are preserved during errors.
- Robust Error Handling: Unexpected conditions are auto-managed to maintain protection.
These capabilities reduce the need for manual intervention and help maintain continuous visibility and coverage even when parts of the infrastructure are degraded.
Agent Version Control: Consistency and Security
Agent Version Control (AVC), an innovative feature of the Qualys Cloud Agent, adds another layer of resilience to the TruRisk Platform by giving organizations enhanced control and flexibility over their agent deployment. AVC ensures that agent versions are consistent, security protocols are standardized, and updates are aligned with organizational priorities:all while maintaining the automated protections and self-healing capabilities that make Qualys agents reliable.

Key Features
- Uniform agent versions for consistent protection
- Controlled update staging to minimize disruption
- AVC profiles tailored by OS or workload
- Access to previously supported binaries for stable deployment
- Streamlined update workflows with automated protections
Benefits
- Uniform Security Measures: Endpoints remain consistently protected.
- Enhanced Reliability: Controlled agent rollouts reduce compatibility issues.
- Reduced IT Workload: Automation frees teams to focus on strategic priorities.
- Stable, Risk-Aware Operations: Security aligned with organizational readiness.
Together, MVC and AVC deliver end-to-end resilience: the agent itself and the updates it applies are governed, controlled, and reliable.
Achieving Precision with Custom Assessment and Remediation
Automation handles most scenarios, but sometimes direct intervention is required. Custom Assessment and Remediation (CAR) enables safe execution of PowerShell, Bash, Python, or other scripts directly on endpoints.
With CAR, teams can:
- Run PowerShell, Bash, Python, or other scripts securely on endpoints.
- Remediate misconfigurations, apply mitigations, or collect forensic data without uninstalling agents.
- Orchestrate targeted remediation workflows that align with change management policies.
CAR is designed to complement automation rather than replacing it, enabling precise, auditable interventions when an automated path is insufficient.
This gives IT teams precision control when needed, complementing the self-healing capabilities of Cloud Agents with targeted, policy-aligned actions.
The Bigger Picture of Risk-Aligned Security
More than a feature set, this is a strategic shift: aligning security delivery with operational risk tolerance. Manifest Version Control, Agent Version Control, self-healing agents, CAR, and resilient lab validation together allow organizations to:
- Keep detection velocity high without exposing production to unnecessary risk.
- Map rollout strategies to business criticality and regulatory requirements.
- Demonstrate control in audits and incident reviews with rich telemetry and change history.
This shift is also reshaping board-level conversations. CISOs are no longer evaluated solely on how fast they patch but on how well they balance speed with continuity, compliance, and trust. By embedding resilience, they can show that the security program not only reacts to threats but also protects uptime and customer confidence. That alignment between security and business resilience is becoming a new benchmark of leadership.
Conclusion: End-to-End Resilience and Control
The Qualys TruRisk™ Platform delivers both speed and stability by embedding resilience at every layer:
- Validated Detections: Signatures vetted through rigorous QA.
- Resilient Infrastructure: Self-healing Cloud Agents with AVC safeguards.
- Intelligent Update Management: MVC and CAR ensure safe, controlled rollouts.
From the lab to production, resilience is engineered, validated, and proven in customer-like environments. By making updates a strategic, risk-aware process, the TruRisk Platform empowers organizations to reduce operational risk, maintain business continuity, and strengthen security posture.
Ultimately, resilience is less about resisting disruption and more about absorbing it without compromising security or momentum. It should be understood as a living capability, as the combination of adaptability, protection, and continuity that enables enterprises to thrive in environments where change is the only constant. Those who embed this outlook into their strategy build not just defenses, but enduring confidence.
Contact Qualys Customer Support to enable Manifest Version Control in your environment and operationalize risk-aware update management across endpoints.