Qualys ETM Identity — The First True Quantification of the Identity Perimeter

Security has always been about controlling who can do what and where.
In 2025, that control is mediated entirely by identity. When an attacker “logs in,” not “breaks in”, they inherit legitimate permissions, blend into normal telemetry, and pivot across AD, Entra/Okta, SaaS, and cloud, driving multi-million-dollar losses. Credentials, tokens, and service accounts have become the real perimeter — and most organizations still can’t measure how exposed that perimeter is.
Identity Has Become the New Attack Surface
Recent data quantifies the shift. IBM’s 2024 breach study found stolen or compromised credentials were the slowest to detect and drives an average loss of $4.88 million. Hybrid attacks that pivot from AD to Entra ID show that identity compromise now spans on-prem and cloud. Machine and AI identities have exploded where machine: human ratio is ~50:1 – yet risks from machine identities remain largely unmanaged. Deepfake and AI-assisted phishing have increased success rates. The perimeter hasn’t disappeared; it’s multiplied.
Built inside Qualys ETM, Qualys ETM Identity converts identity posture into a single risk language, correlating identities with asset context to close the most exploitable identity risks and operationalize risk reduction. It is the essence of modern risk operations and the first true quantification of the identity perimeter.
What Security Leaders Are Struggling With
“Most organizations already deploy IAM, IGA, PAM, ITDR, or AD assessment tools, yet identity-driven breaches persist.”
There are tools that validate access, not risk; govern provisioning workflows without business or asset context; protect credentials, but not the blast radius; detect anomalies, not root causes; visualize trust paths but lack continuous, correlated insight. These tools add more silos. Each tool solves a piece of the puzzle, but none measure how identity exposure changes enterprise risk.
Security teams face a lack of unified visibility into identity risk, with fragmented telemetry that separates identity and asset risks into silos, ambiguous ownership, and valid login abuse that is difficult to detect. Additionally, posture drift lacks an audit trail.
In short, identity security today is where vulnerability management was a decade ago – rich in controls, poor in context. Even the most mature security programs are flying blind on identity risk. The controls exist, but the telemetry doesn’t connect.
As a result, CISOs can’t answer the simplest risk question: Which identities represent measurable loss potential?
Security leaders aren’t short on tools. They’re short on measurable alignment between identity posture and business risk. Until that alignment exists, identity remains the least quantified and most exploited attack surface in the enterprise.
Introducing ETM Identity
ETM Identity is the identity risk measurement and operationalization layer that makes those controls effective.
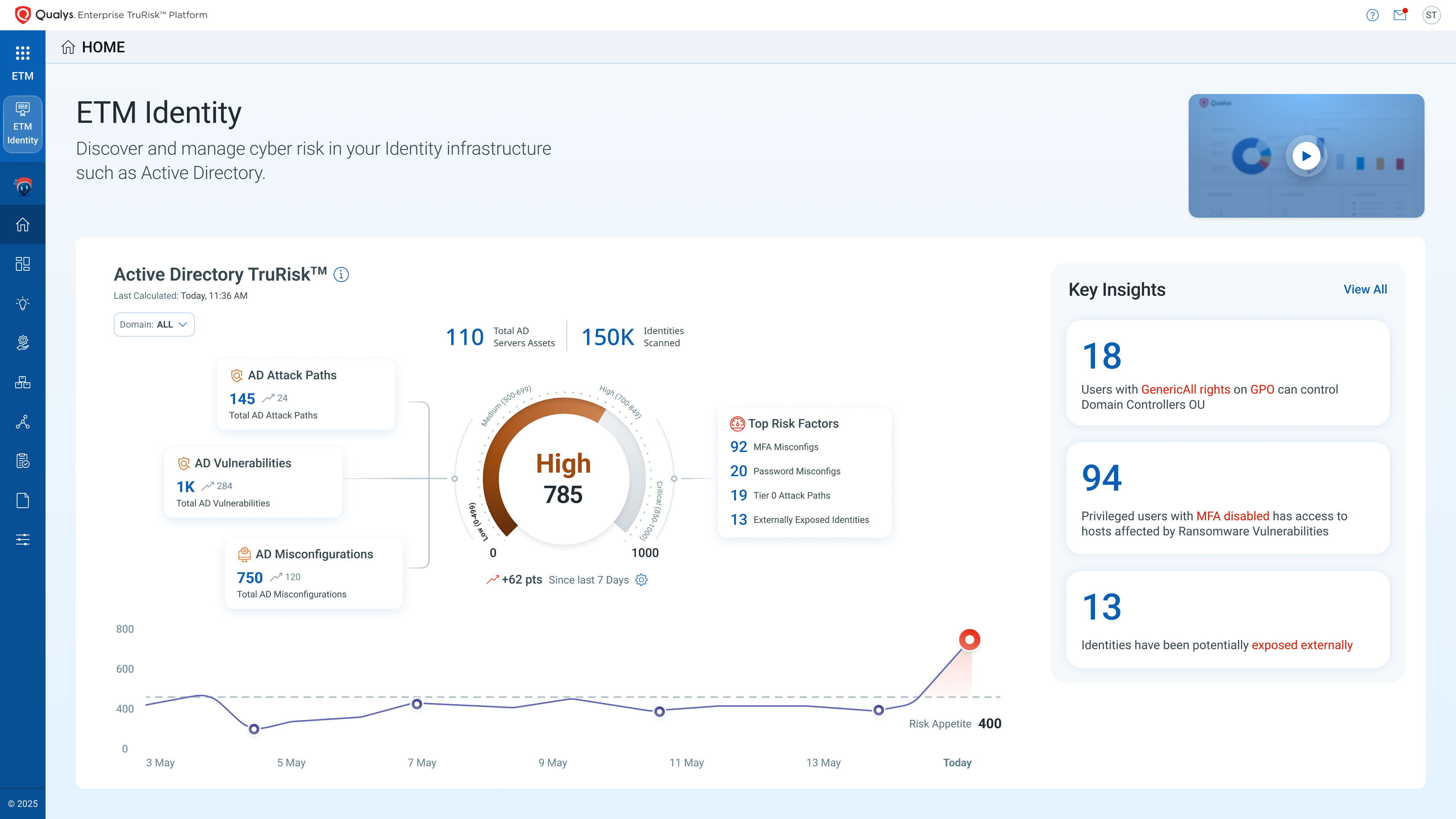
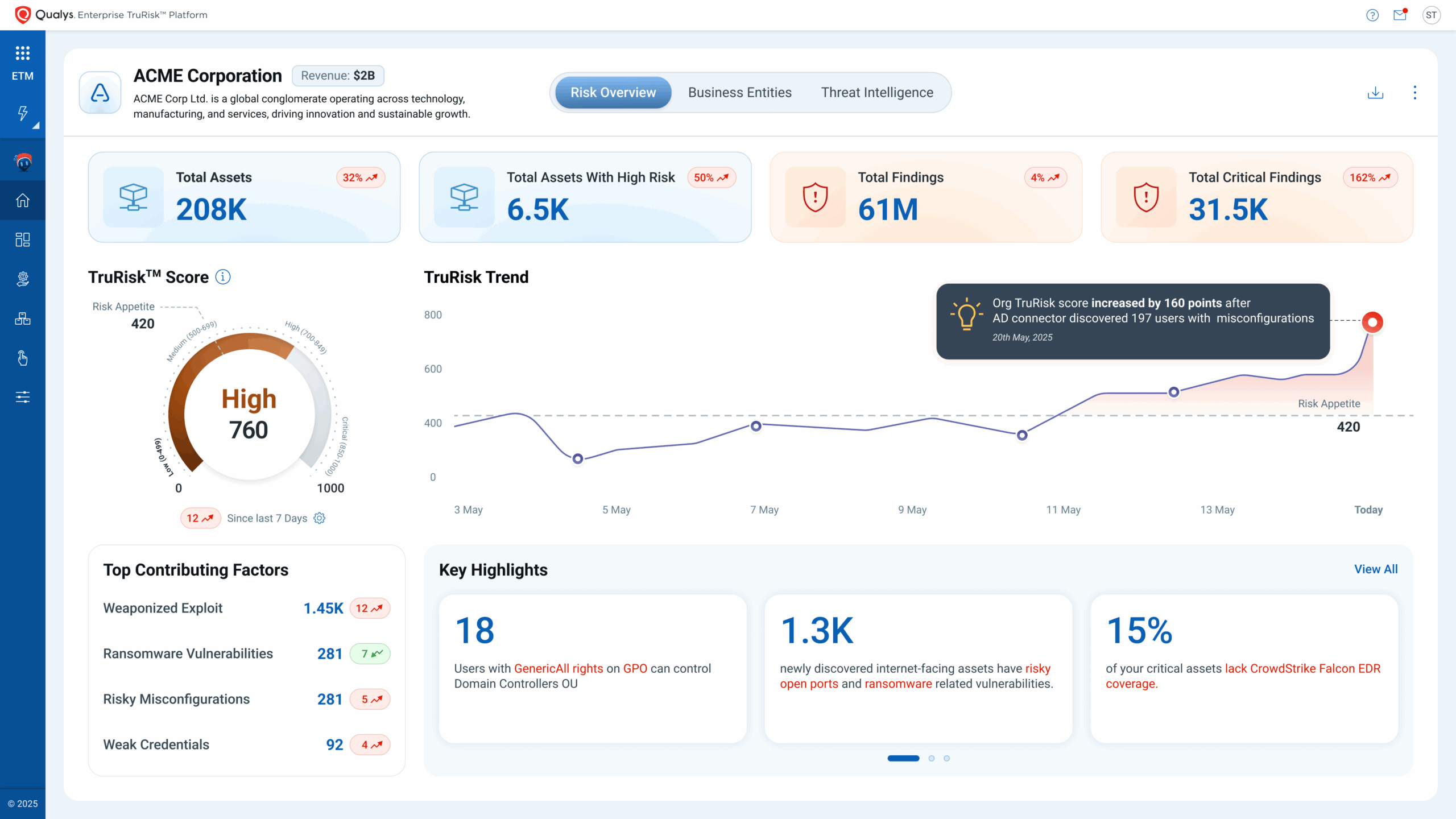
ETM Identity consolidates identity posture into a single risk score that correlates identities (human, service, machine, AI) with asset exposure to prioritize what makes a business impact and operationalize identity risk management for reducing identity-driven attack surface. ETM Identity expresses identity exposure in TruRisk™, correlates posture with threat intel, maps attack paths and domain trust, and then operationalizes risk reduction through closed-loop actions and auto-rescoring.
Measure Identity Risk
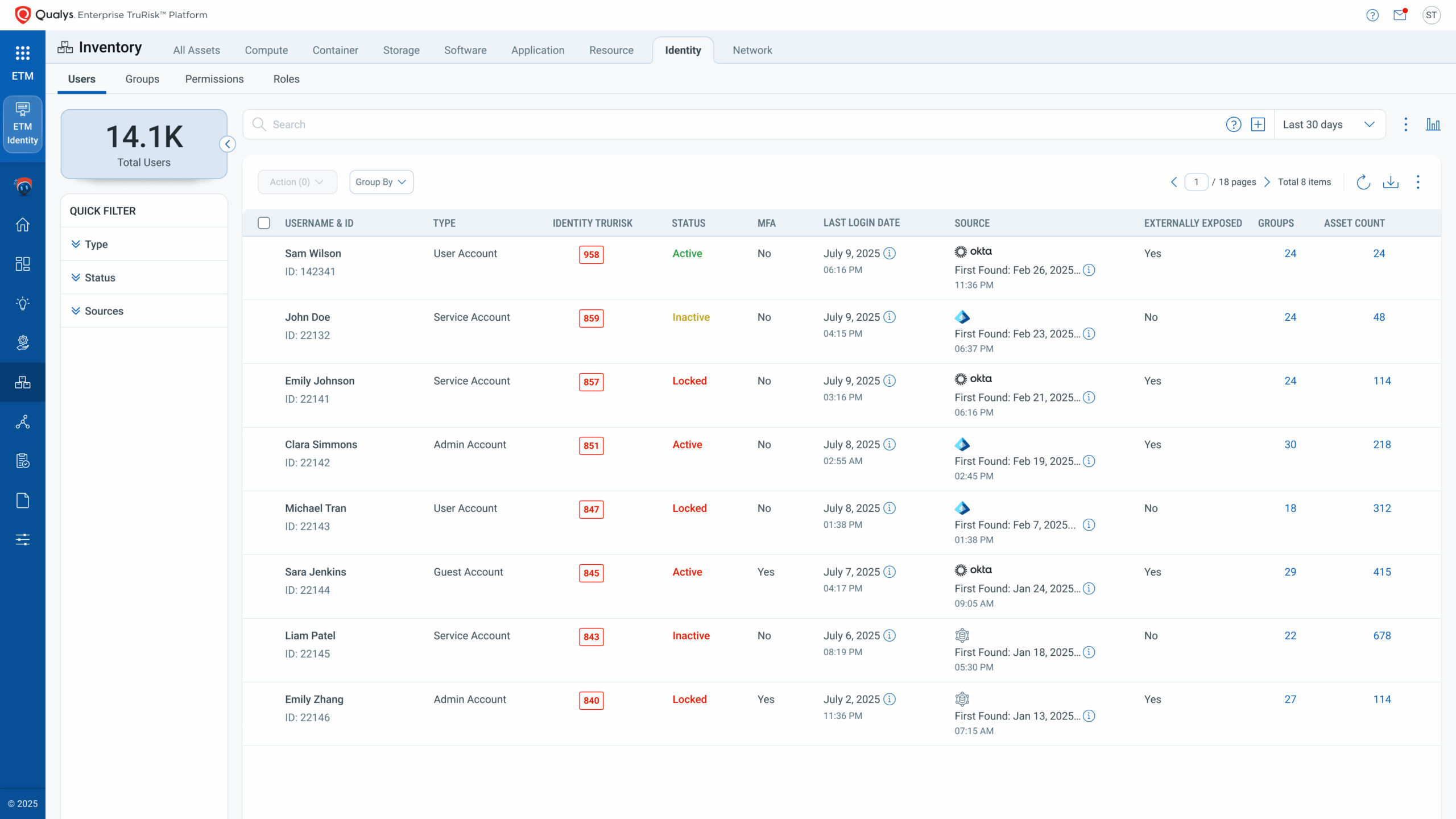
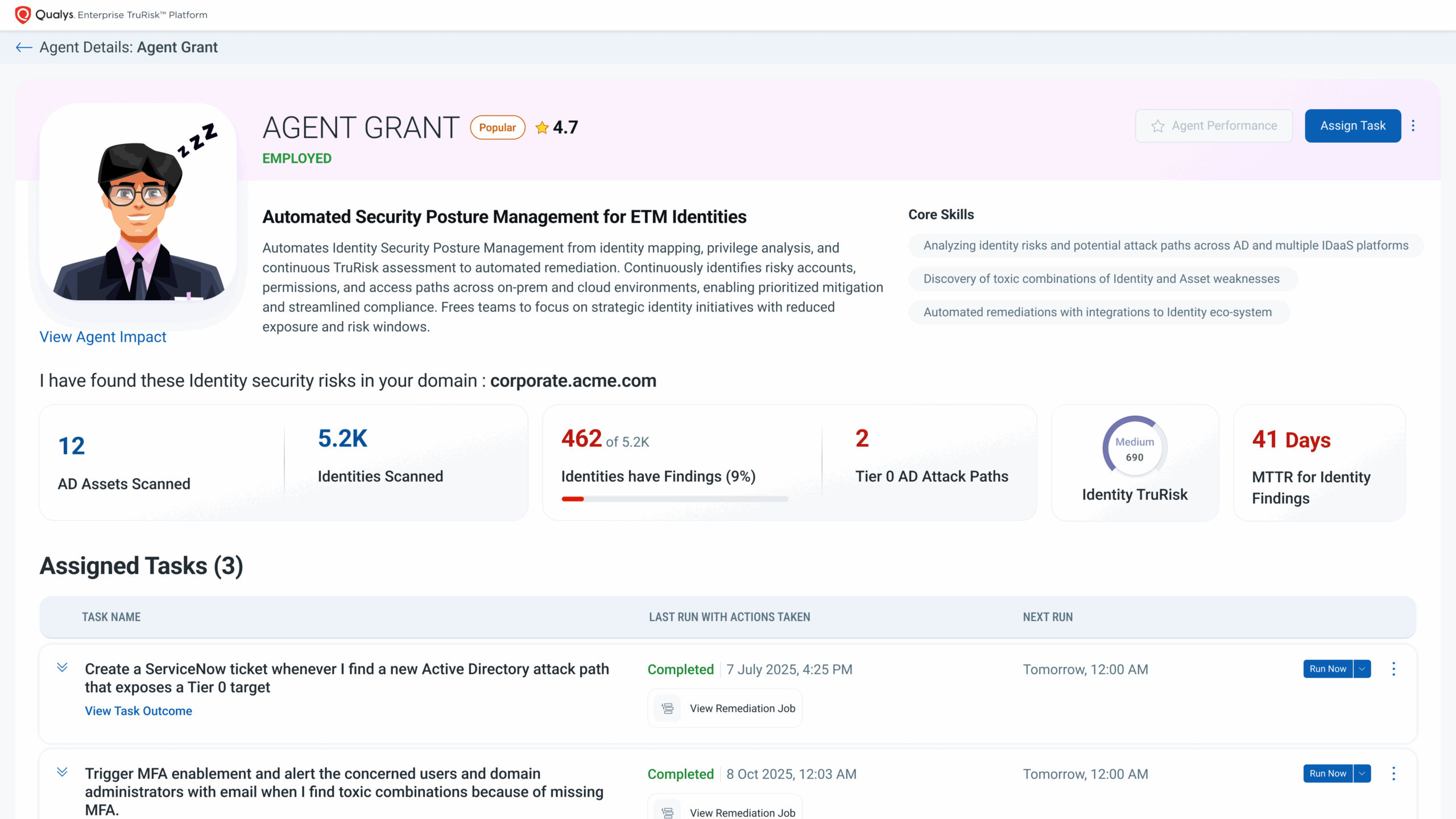
ETM Identity discovers human and machine identities across AD, Entra ID, IdPs, IDaaS; unifies identity risk signals from Qualys Cloud Agent telemetry, native connectors, and third-party identity tools; and correlates with asset exploitability. ETM Identity turns identity exposure into one actionable per-identity score – Identity TruRisk™, the same risk language that can be used alongside assets, vulnerabilities, misconfigurations across hosts, applications, cloud – now directories, identity providers and so on.
Communicate Identity Risk
ETM Identity transforms raw identity findings, identity insights (hygiene gaps, toxic privilege chains, misconfigurations) and attack path analysis (lateral routes, domain/forest trust maps) into a shared risk score, aligned with enterprise risk operations. Identity TruRisk correlates with Asset TruRisk and rolls up to Org TruRisk, communicating board-ready metrics on what changed, why it mattered, and how much risk was reduced. ETM Identity creates an identity posture that’s measurable, reportable, and explainable, bridging the gap between security engineers, auditors, and executives with a single risk language.
Eliminate Identity Risk
Measurement without elimination is just observation. ETM Identity operationalizes reduction through risk response orchestration, translating findings into verified, automated action. It integrates with ServiceNow and Jira to open, track, and close remediation tickets; executes over 200 AD policy controls, patches, and ready-to-run automation scripts; and performs one-click identity-aware actions. Additionally, it automatically validates closure and creates measurable before/after deltas for TruRisk, ensuring accurate scoring. When patching isn’t feasible, it applies compensating controls — such as policy hardening, conditional-access updates, or containment — to reduce exploitability immediately.
With ETM Identity, the enterprise can measure what matters, communicate it credibly, and eliminate what’s exploitable, all within one platform and one risk language.
Want to see ETM Identity in action?
Explore our webinar, “Extending Your Risk Operations Center with Qualys ETM Identity”, to learn how identity context transforms risk operations.
Key Capabilities — Built to Measure, Communicate, and Eliminate Identity Risk
- Comprehensive Identity Inventory – Discovers human, service, and machine/non-human identities across AD, Entra ID, Okta and other IdP, IDaaS systems; maps owners, life-cycle state, entitlements, and change history.
- Unified Identity Risk View – Consolidates identity risk signals from Qualys Cloud Agent, native identity connectors, and 3rd-party tools (IGA, PAM, ITDR, AD assessors like BloodHound, SailPoint, etc.), unifying identity posture with endpoint, workload, and network telemetry.
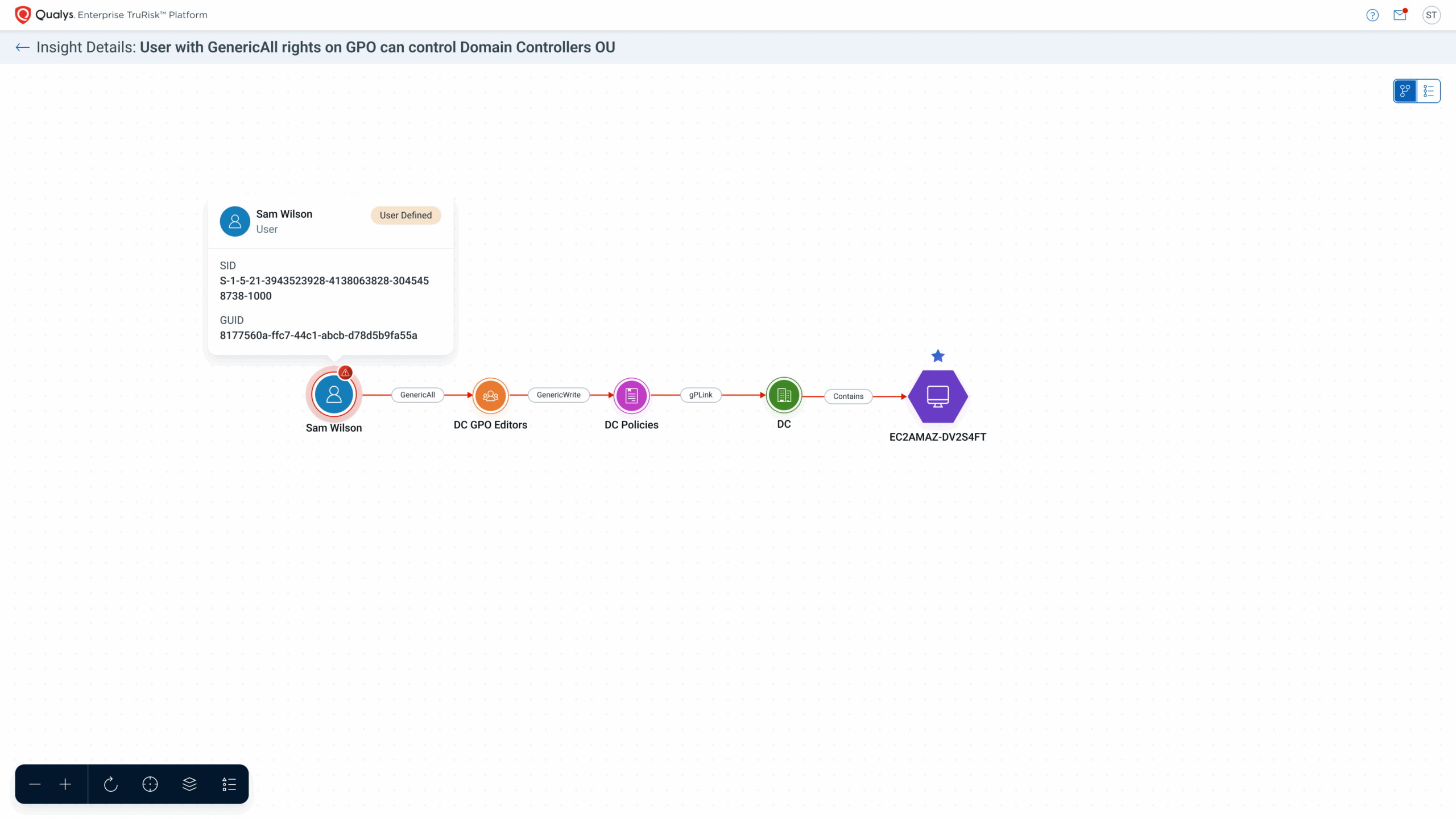
- Attack Path Analysis & Domain Trust Map – Visualize hidden relationships inside AD, see blast radius with toxic privilege combinations, choke points, and rank exploitable paths by TruRisk™. The Domain Trust Map surfaces lateral movement routes across domains/forests/tenants to identify easy pivots.
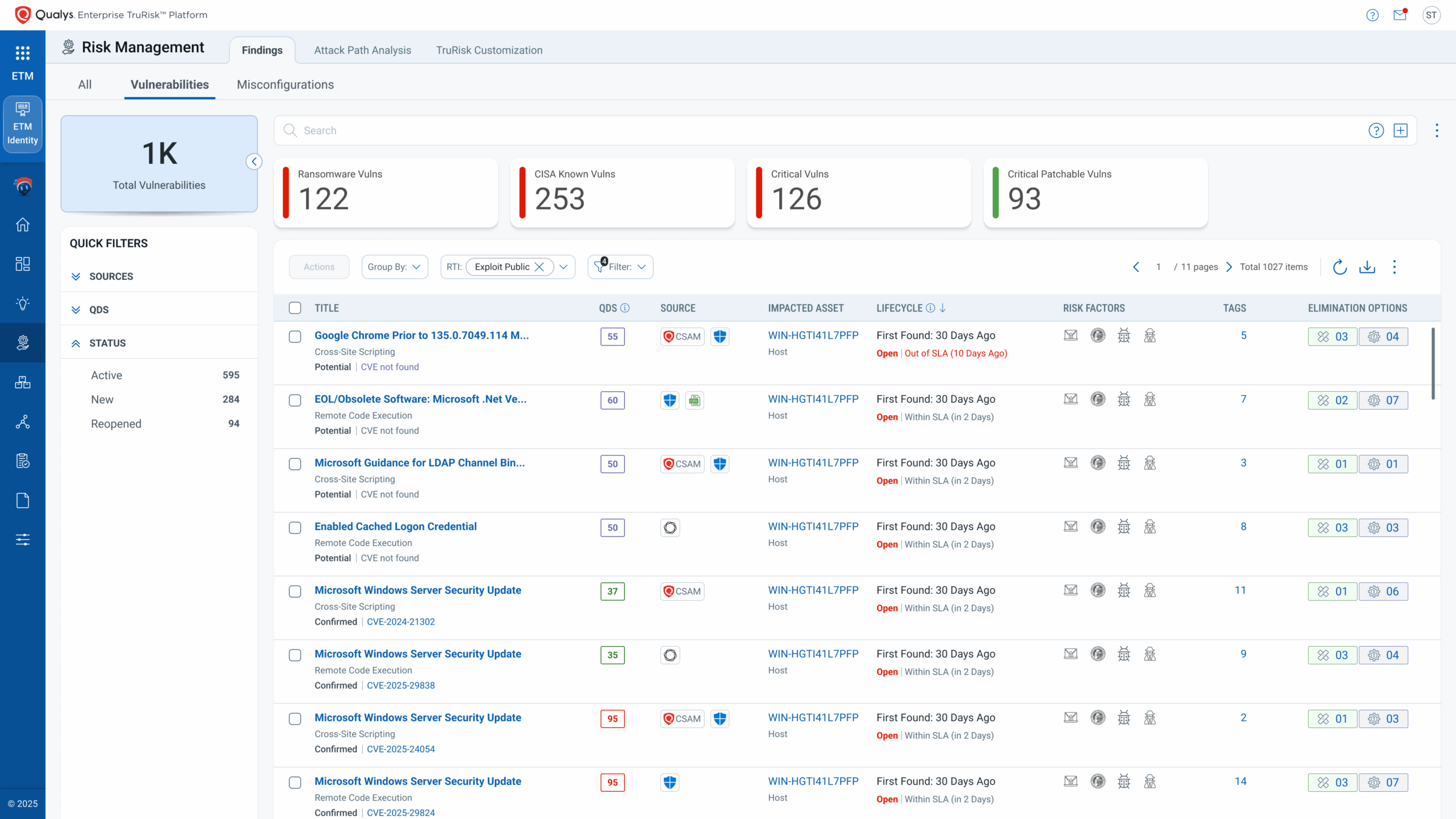
- Identity Insights – Flags weak password policies, plaintext credentials, stale/admin rights, excessive permissions, risky OAuth consents, and ADCS misconfigurations. Targets the “need of the hour”: AD hardening, service-account risk (e.g., Kerberoasting), and certificate abuse vectors for high ROI fixes that rapidly shrink the blast radius.
- Identity TruRisk™ – Quantifies per-identity risk from aggregated misconfigurations, excessive privileges, vulnerabilities, and IOR, correlates with asset exposure (internet-facing, vuln/KEV proximity), and rolls up to Asset TruRisk and Org TruRisk. It provides one risk language for ROC, SecOps, and the executive board.

- Risk Response Orchestration – Executes 200+ policy controls for AD, out-of-the-box automation scripts, patch, mitigate or isolate, automates one-click identity actions (enforce MFA, de-privilege, disable/quarantine, remove toxic rights). It integrates ITSM workflows for ServiceNow/Jira ticketing with evidence, approvals, and auto-rescore on closure.
- Agent Grant, an agentic AI coworker for identity security – Built on the Qualys Agentic AI fabric, Agent Grant is a pre-built Cyber Risk Agent specialized for ETM Identity. It continuously maps identities, flags toxic privilege chains and AD to cloud attack paths, and then executes next-best actions, including opening/advancing ServiceNow or Jira tickets, prompting MFA enforcement, de-privileging, or quarantining risky accounts while capturing evidence and re-scoring Identity TruRisk™. Agent Grant benefits from 25+ threat intel feeds, Cloud Agent telemetry, and CMDB business context inside the Qualys Enterprise TruRisk Management (ETM), which can be tailored (or even cloned) for your workflows via the agent marketplace/no-code builder.
- Compliance Mapping & Audit Lineage – Maps identity controls/findings toDISA STIG (AD), CIS M365, HIPAA/PCI/GDPR, etc. and maintains versioned change history (who/what/when/where). Replaces screenshots with continuous, non-repudiable evidence; speeds audits and proves control effectiveness.
- Identity Integrity Monitoring – Tracks configuration drift across AD, Entra/Okta, and SaaS tenants; alerts on high-risk changes to policies, trusts, or entitlements.
The Next Evolution of Qualys ETM (and Your Stack)
Every security team says the same thing today: “We have identity tools, but we still don’t know which identities actually matter.” That’s the heart of the problem ETM Identity was built to solve. ETM Identity is how Qualys extends its risk operations DNA to the identity perimeter, giving you a unified and auditable view of cyber risk across people, machines, and systems.
Inside the Qualys Enterprise TruRisk™ Management (ETM) platform, ETM Identity becomes another high-fidelity, first-class telemetry source. Qualys ETM unifies asset, vulnerability, configuration, and now identity exposure under TruRisk so ROC teams can make trade-offs with evidence. It correlates identity findings and asset exploitability and then rolls up those findings into the single TruRisk™ score that fuels your Risk Operations Center. It’s also deeply integrated. Qualys Cloud Agent data, threat intelligence from 25+ feeds, business context from CMDB and Business Entities – all converge to create one view of exposure. Whether the risk stems from a vulnerable workload, a stale admin, or a misconfigured trust path, it’s visible, correlated, and prioritized.
Plus, it fits neatly into what you already have. Qualys ETM Identity doesn’t replace your existing IAM, IGA, or PAM stack – it connects them. ETM Identity ingests from AD, Entra ID, Okta, and third-party tools like PingCastle, BloodHound, and SailPoint, ensuring your existing investments keep working, now with a measurable ROI.
Why it matters
- Identity exposure is quantified in the same units as vulnerabilities and misconfigurations, so you can choose the highest risk-reduction.
- Instead of chasing alerts, teams follow a repeatable loop, proving reductions in MTTR.
- Non-repudiable change history and consistent roll-ups replace screenshots and spreadsheets.
When you can measure risk across identities, assets, cloud, and applications in one model, prioritization stops being a guessing game. Because risk isn’t about how many controls you have – it’s about how well you can measure, communicate, and eliminate what truly drives business impact.
Ready to see your identity perimeter in measurable terms? Explore how ETM Identity turns identity exposure into quantifiable insight.
Discover how quickly identity risks can be eliminated from your environment when you have the right insight.