React2Shell: Decoding CVE-2025-55182 – The Silent Threat in React Server Components
Table of Contents
- Understanding React Server Components (RSC)
- Decoding React2Shell CVE-2025-55182
- Applications & Software Affected
- Exploitation in the Wild How Attackers are Executing the Attack
- Mitigating This Vulnerability
- Threat Landscape and Business Risk
- Qualys QID Coverage
- Eliminating the Risk of these Vulnerabilities with the Qualys Enterprise TruRiskTMPlatform
- Contributors
On December 3, 2025, a critical remote code execution (RCE) vulnerability, dubbed “React2Shell,” was disclosed, impacting React Server Components and frameworks like Next.js. The flaw, CVE-2025-55182, could lead to full server takeover and is rated CVSS 10.0. It is under active exploitation, has been added to the CISA KEV, and organizations should take immediate steps to remediate.
IMPORTANT NOTE FOR CUSTOMERS –
Qualys Products and Platforms are safe from React2Shell (CVE-2025-55182) and are not affected. While certain products do use the vulnerable versions of React and Next.js, preventative in-line mitigations are in place and designed specifically to address the risk posed by this vulnerability. We have prioritized releases to eliminate the use of these vulnerable versions in the limited products that leverage the dependencies. For more information, please contact Qualys Support.
Understanding React Server Components (RSC)
React Server Components (RSC) enable developers to run parts of a React application’s rendering logic on the server — rather than the browser — which reduces client-side complexity and improves performance. Under the hood, RSC uses a serialization/deserialization protocol called “Flight” to shuttle component trees and server-function calls between client and server. Because RSC is broadly implemented across popular frameworks and bundlers, a wide range of modern web apps rely on it—including those built with Next.js, RSC plugins for bundlers like webpack, Turbopack, and Parcel, as well as frameworks such as Vite, Waku, and Redwood.
Decoding React2Shell – CVE-2025-55182
Disclosed on December 3, 2025, CVE‑2025‑55182 (dubbed “React2Shell” as a reference to the 2021 flaw “Log4Shell” and rated CVSS 10.0) affects React 19.0.0–19.2.0 and any framework leveraging React Server Components. The issue lies in how React’s internal Flight protocol serializes and deserializes “component trees” — the data structures that describe how UI components should be rendered on the server. During this process, React’s server‑side decoder fails to validate incoming payloads, allowing attackers to inject arbitrary objects that are then deserialized in privileged server contexts.
What makes CVE‑2025‑55182 especially dangerous is that React’s server runtime was never built to handle untrusted input. Traditionally, client input is sanitized and filtered by APIs before any server logic is executed. By contrast, React Server Components — a core feature introduced for performance — blurred that separation, allowing serialized data representing app state to travel directly between client and server. Because many RSC-based frameworks embed React’s vulnerable deserialization logic, this impacts a broad ecosystem — including Next.js. Consequently, Next.js issued a separate (but upstream-rooted) advisory under CVE-2025-66478 to track its exposure.
Applications & Software Affected
Applications using React Server Components with the App Router are affected when running the following versions:
- Next.js 15.x
- Next.js 16.x
- Next.js 14.3.0-canary.77 and later canary releases
Affected Software Versions
- react-server-dom-parcel versions 19.0, 19.1.0, 19.1.1 and 19.2.0
- react-server-dom-turbopack versions 19.0, 19.1.0, 19.1.1 and 19.2.0
- react-server-dom-webpack versions 19.0, 19.1.0, 19.1.1 and 19.2.0
Please note that an application is not affected by the vulnerability if application’s code does not use a framework, bundler, or bundler plugin that supports React Server Components.
- Next.js 15.x
- Next.js 16.x
- Next.js 14.3.0-canary.77 and later canary releases
- Next.js 13.x, Next.js 14.x stable, Pages Router applications, and the Edge Runtime are not affected.
Exploitation in the Wild – How Attackers are Executing the Attack
Telemetry from multiple vendors shows that CVE‑2025‑55182 went from disclosure to active exploitation in hours, with automated scanners and hands‑on‑keyboard operators both leveraging the bug. Attackers focus primarily on internet‑facing Next.js frontends and other RSC workloads running in cloud environments such as Kubernetes clusters and managed PaaS platforms.
Once React2Shell delivers an interactive shell inside a container or VM, common behaviors include:
- Environment and identity discovery: executing commands like whoami, hostname, environment variable dumps, and browsing /etc/passwd to profile the host and execution context.
- DNS and HTTP beaconing: using oast‑style domains and callback infrastructure to verify outbound connectivity and fingerprint environments, often exfiltrating environment variables and host metadata.
- Reverse shells: pivoting from one‑off command tests to long‑lived reverse shells that give operators persistent, interactive access to the Node.js / Next.js process.
Attackers have been able to execute various monetization and persistence tactics, including:
- Deploying XMRig‑based cryptominers, sometimes packed or disguised as system processes, often combined with scripts that kill competing miners and try local privilege escalation.
- Using installer scripts from third‑party pools and lightweight persistence tricks (for example, running miners under names like crond or systemd-devd in writable directories).
- Installing Sliver implants and other backdoors via shell scripts that fetch ELF payloads and connect to dedicated command‑and‑control infrastructure, indicating more targeted, long‑term access operations.
Mitigating This Vulnerability
Customers must upgrade to the following patched versions to address the vulnerabilities:
- react-server-dom-parcel 19.0.1, 19.1.2, 19.2.1
- react-server-dom-turbopack 19.0.1, 19.1.2, 19.2.1
- react-server-dom-webpack 19.0.1, 19.1.2, 19.2.1
- Next.js releases 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, 16.0.7
Threat Landscape and Business Risk
Our recent blog highlights that weaknesses in the Flight protocol’s handling of serialized payloads allow attackers to bypass validation and deliver crafted requests that lead directly to remote code execution. Additional advisories further confirm that the flaw impacts widely used frameworks beyond just React or Next.js; any bundler or plugin that integrates RSC (e.g., Vite, Waku, Parcel, etc.) may be affected. This vulnerability is being actively exploited in the wild, including:
- Known threat actors — including China-nexus groups — have rapidly weaponized “React2Shell” in automated attacks targeting internet-facing applications.
- Observed attack activity includes credential harvesting, cloud-native backdoor deployment, and opportunistic cryptomining.
- Given how widespread React/Next.js is (over 2.1 million websites/applications, many in cloud environments), any unpatched system remains a high-value target.
From a business continuity perspective, exploitation could lead to full server takeover, theft of sensitive data or secrets, unauthorized persistence, compliance violations, and large-scale disruption of web services. Cyber risk quantification technologies like Qualys Enterprise TruRiskTM Management (ETM) can help identify dollars at risk from vulnerabilities like React2Shell. ETM also leverages Qualys TruRiskTM prioritization to identify the most critical exposures to resolve.
Qualys QID Coverage
Qualys has released the QIDs in the table below for the above-mentioned vulnerabilities.
| Type | QID | Title |
| SwCA (applies to hosts and container images) | 5006447 | NodeJs (Npm) Security Update for react-server-dom-parcel (GHSA-fv66-9v8q-g76r) |
| 5006445 | NodeJs (Npm) Security Update for next (GHSA-9qr9-h5gf-34mp) | |
| Unauthenticated Scan | 733480 | React Server Components (RSC) Remote Code Execution (RCE) Vulnerability (React2Shell) (Unauthenticated Check) |
| Cloud Agent QID | 386154 | React Server Dom Component NPM Package Remote Code Execution (RCE) Vulnerability |
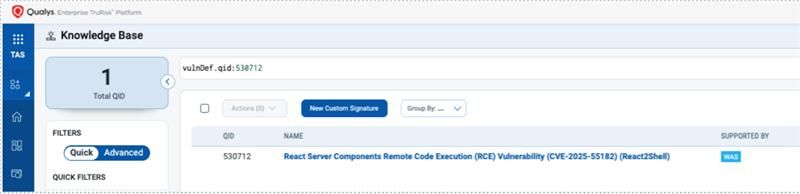
| WebApp/AppSec QID | 530712 | React Server Components Remote Code Execution (RCE) Vulnerability (CVE-2025-55182) (React2Shell) |
Customers can also search for this vulnerability by CVE ID: CVE-2025-55182 (e.g., in VMDR – vulnerabilities.vulnerability.cveIds: CVE-2025-55182).
Eliminating the Risk of these Vulnerabilities with the Qualys Enterprise TruRiskTM Platform
Attack Surface Visibility
With Qualys CSAM and EASM, externally exposed Next.js applications with this critical vulnerability are automatically surfaced. In addition, you can search by software component name to identify for example where react-server-dom, the vulnerable software, is running in your environment.

Identify and Respond to Vulnerable Hosts With Qualys VMDR
Qualys VMDR offers comprehensive coverage and visibility into vulnerabilities, empowering organizations to rapidly respond to, prioritize, and mitigate the associated risks. Additionally, Qualys customers can leverage Qualys Patch Management to remediate these vulnerabilities effectively.
Leverage the power of Qualys VMDR alongside TruRisk™ scoring and the Qualys Query Language (QQL) to efficiently identify and prioritize vulnerable assets, effectively addressing the vulnerabilities highlighted above.
Use this QQL statement: vulnerabilities.vulnerability.cveIds: CVE-2025-55182

With detailed Software Composition Analysis across hosts, containers, and images, Qualys provides detailed install path information on the location of the vulnerability across any asset, enabling security and development teams to take swift action quickly.

Identify Exposed Containers/Images and Block Vulnerable Deployments With Qualys Kubernetes & Containers Security (KCS)
Using Qualys Kubernetes & Containers Security (KCS), customers can identify containers and images with this vulnerability.

KCS can also give visibility into the specific image layer where the vulnerability was found, as well as the specific install path in the image.


Using Qualys Admission Controllers and Image Admission Policies, you can add this vulnerability to ensure that it is not deployed to any new container and/or blocked from being used in any container image built by your development teams.

Identify Vulnerable Web Apps With TotalAppSec
The on-demand or scheduled vulnerability scan using Qualys TotalAppSec or Qualys Web Application Scanning (WAS) will detect the vulnerability in the scanned web application. Application owners can be identified to enable faster remediation.



Remediate at Scale With TruRiskTM Eliminate
TruRisk Eliminate offers a comprehensive risk reduction solution designed to help security and IT teams proactively address nearly 100% of CISA KEVs and ransomware vulnerabilities.
To address Reach Server Component vulnerabilities, leverage Qualys TruRisk Eliminate to:
- Patch these vulnerabilities, or
- Apply out-of-the-box mitigations until a patch can be deployed
Because these vulnerabilities are Qualys patchable, you should immediately deploy the patches and fix them. Relevant patches were added to the Qualys patch catalog and are ready to be deployed using the Qualys agent.
For an in-depth technical blog post, visit our Threat Protect post on this vulnerability.
Contributors
- Abhinav Mishra, Director, Product Management, TotalCloud Kubernetes and Container Security, Qualys