Top 10 Cloud Compliance Tools for Enterprise Security and Audit Readiness in 2026
Table of Contents
- Compliance Breaks When Proof Lags Infrastructure
- Why Cloud Compliance Has Become an Operating Model Problem
- The Criteria That Matter at Enterprise Scale
- Orienting the Decision Before Evaluating the Tools
- The 10 Cloud Compliance Tools Security Leaders Are Evaluating in 2026
- Final Perspective: Resilience Can Be Measured. Compliance Proves It.
- Frequently Asked Questions (FAQs)
- Subject Matter Expert Contributors
Key Takeaways
- Cloud compliance has shifted from periodic audits to a continuous operating requirement as hybrid and multi-cloud environments change faster than traditional controls can keep pace.
- Modern cloud compliance solutions provide continuous, automated compliance monitoring across AWS, Azure, GCP, OCI, Kubernetes, and hybrid environments—replacing manual, point-in-time audits
- Security leaders must manage overlapping frameworks such as NIST CSF 2.0, SOC 2, ISO 27001, PCI DSS, HIPAA, GDPR, and DORA while maintaining a defensible posture between audits.
- Effective cloud compliance platforms improve asset visibility and offer attack path analyses, help manage controls across frameworks, facilitate flexible scanning, and automate evidence collection using live telemetry.
- Risk-based prioritization and integrated remediation are essential to focus effort on exposures that materially impact security and regulatory risk.
- At enterprise scale, compliance is no longer a checkbox exercise. It is a signal of operational resilience and maturity.
Compliance Breaks When Proof Lags Infrastructure
Cloud compliance has changed. It is no longer an audit milestone. It is a continuous expectation. Boards demand visibility into regulatory exposure. Regulators expect evidence, not intent. Enterprise customers want assurance in real time. Meanwhile, frameworks such as NIST and CIS are becoming harder to implement as cloud environments fragment across providers, regions, and operating models.
For security leaders, the tension is structural. Compliance keeps expanding. The cloud refuses to sit still. Audit models were built for neither. This conundrum is forcing a shift from periodic validation to continuous, risk-aware control assurance, where modern cloud compliance tools play a central role.
This guide evaluates the top ten cloud compliance tools to help enterprises make clear, confident decisions on cloud security, compliance, and audit readiness in 2026.
Qualys Insights
Dive into how leading teams are turning cloud compliance best practices into measurable, provable outcomes.
Why Cloud Compliance Has Become an Operating Model Problem
In regulated industries, the question has quietly changed. It is no longer “Are we compliant with SOC 2 or ISO 27001?” It is “Can we continuously demonstrate control effectiveness and drive lower risk register scores across environments that change daily?”
Consider the pressures security leaders face today:
- Regulatory scope and velocity are increasing. Organizations must map controls across SOC 2, ISO 27001, NIST, and CIS, as well as mandates such as PCI DSS 4.0, HIPAA 2023, GDPR, and DORA. The cost of compliance failure now often exceeds breach recovery, driven by penalties, failed audits, delayed deals, and remediation overhead.
- Cloud-specific leniency is disappearing. Standards such as PCI DSS 4.0 no longer provide carve-outs for cloud-native architectures or containers, requiring continuous control assurance regardless of deployment model.
- Hybrid and multi-cloud environments fracture visibility. Workloads spanning AWS, Azure, GCP, SaaS, and on-prem systems introduce divergent control planes and shared responsibility models, complicating consistent policy enforcement.
- Audit defensibility now requires continuous evidence. Regulators expect traceable, immutable documentation that reflects real-time posture rather than point-in-time snapshots.
- Resource constraints amplify risk. Manual control mapping and evidence collection divert limited security capacity away from higher-value risk reduction.
In practice, compliance failures stem less from missing policies than from visibility gaps, control drift, misconfigurations, and delayed detection, prompting teams to adopt a common framework for evaluating compliance.
The Criteria That Matter at Enterprise Scale
The tools examined in this guide are evaluated against six criteria that reflect how compliance must function in modern cloud environments:
- Unified asset visibility across cloud, on-prem, Kubernetes, APIs, and endpoints, because controls cannot be enforced on assets that are unknown and not consistently inventoried.
- Multi-geo, multi-framework support that allows controls to be defined once and reused across regulations, reducing duplication and error.
- Automated evidence collection driven by live telemetry, eliminating reliance on manual, point-in-time artifacts.
- Risk-based prioritization that aligns compliance efforts with real exposure rather than equal weighting of all control gaps and reduces false positives.
- Integration with remediation workflows and ITSM, enabling issues to be resolved and not merely reported.
- Audit-grade reporting that withstands regulatory scrutiny and supports defensible narratives and impacts risk register scores.
- Coverage from code to cloud, ensuring compliance controls can be evaluated earlier in the delivery lifecycle as infrastructure and applications are deployed through code, not only after resources are live.
- Support for policy-driven exceptions and business-aligned prioritization, allowing compliance deviations to be formally approved, tracked, and weighted based on business impact rather than treated as uniform failure
These criteria reflect a broader truth: Compliance must reduce risk, not just satisfy checklists.
Orienting the Decision Before Evaluating the Tools
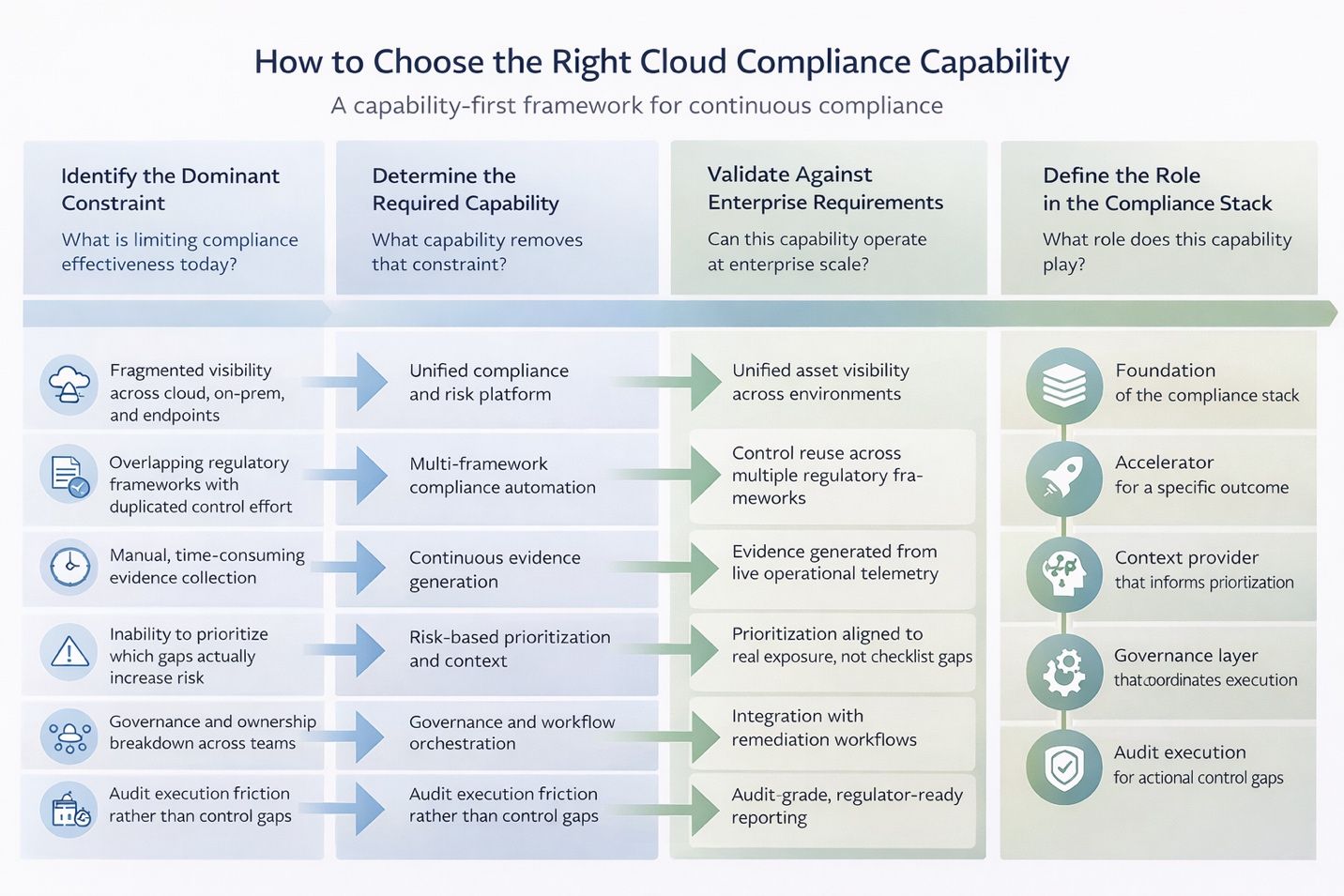
Cloud compliance tooling decisions often fail because they start with features rather than context. Mature organizations begin by identifying the primary constraint limiting continuous compliance.
The framework below structures that decision. It maps organizations’ unique operational and regulatory constraints to the compliance capabilities that matter. The tools comparison comes later.
The table below translates this framework into the most common compliance constraints security leaders encounter, and the capability required to address each one.
| Gaps | What Leaders Are Experiencing | The Capability that Resolves It |
| Fragmented asset visibility | Controls cannot be enforced consistently across cloud, on-prem, and endpoints. | Unified compliance and risk platform |
| Regulatory overlap | Teams duplicate effort across SOC 2, NIST, ISO 27001, PCI DSS, HIPAA, GDPR, DORA. | Multi-framework control reuse |
| Manual evidence collection | Audits consume senior security time with little risk reduction. | Continuous evidence generation |
| Poor prioritization | All gaps look equally urgent, despite very different risk impact. | Risk-based prioritization with context |
| Governance breakdown | Ownership, accountability, and follow-through are inconsistent. | Governance and workflow orchestration |
| Audit execution friction | Controls exist, but audits remain slow and disruptive. | Guided audit and compliance execution |
With the capability requirement clear, tool selection becomes a matter of fit within the compliance operating model, rather than a feature comparison.
The 10 Cloud Compliance Tools Security Leaders Are Evaluating in 2026
1. Qualys TotalCloud with Qualys Policy Audit
When cloud change outpaces compliance assurance
In dynamic cloud and container environments, compliance gaps emerge when configuration drift and policy enforcement fall out of sync with infrastructure change. Qualys addresses this challenge by embedding continuous compliance at both the workload and cloud service layers, combining workload-level policy evaluation with cloud service posture assessment to ensure controls remain enforced as infrastructure, services, and platforms evolve, rather than reconstructing compliance downstream during audits.
- Qualys TotalCloud™ continuously assesses cloud configuration posture across AWS, Azure, OCI, GCP, Kubernetes, and container environments, identifying misconfigurations and vulnerabilities that commonly lead to non-compliance with NIST, CIS Benchmarks, PCI DSS, ISO 27001, GDPR, and 40+ regulatory mandates.
- By evaluating cloud-native resources, identities, and services as they change, TotalCloud reduces the exposure window created by configuration drift between audit cycles.
- TotalCloud includes built-in remediation, including 300+ low-code/no-code automation playbooks. These playbooks can also be further customized and extended to meet last-mile use cases at scale.
- Qualys Policy Audit enables controls to be defined once and evaluated continuously across more than one hundred regulatory and industry frameworks, reducing duplicated effort across overlapping mandates.
- Policy Audit converts technical posture data into control-level evidence, supporting audit defensibility without reliance on manual attestations or static documentation.
- Automated evidence generation and remediation guidance support a shift from point-in-time validation to continuous compliance assurance.
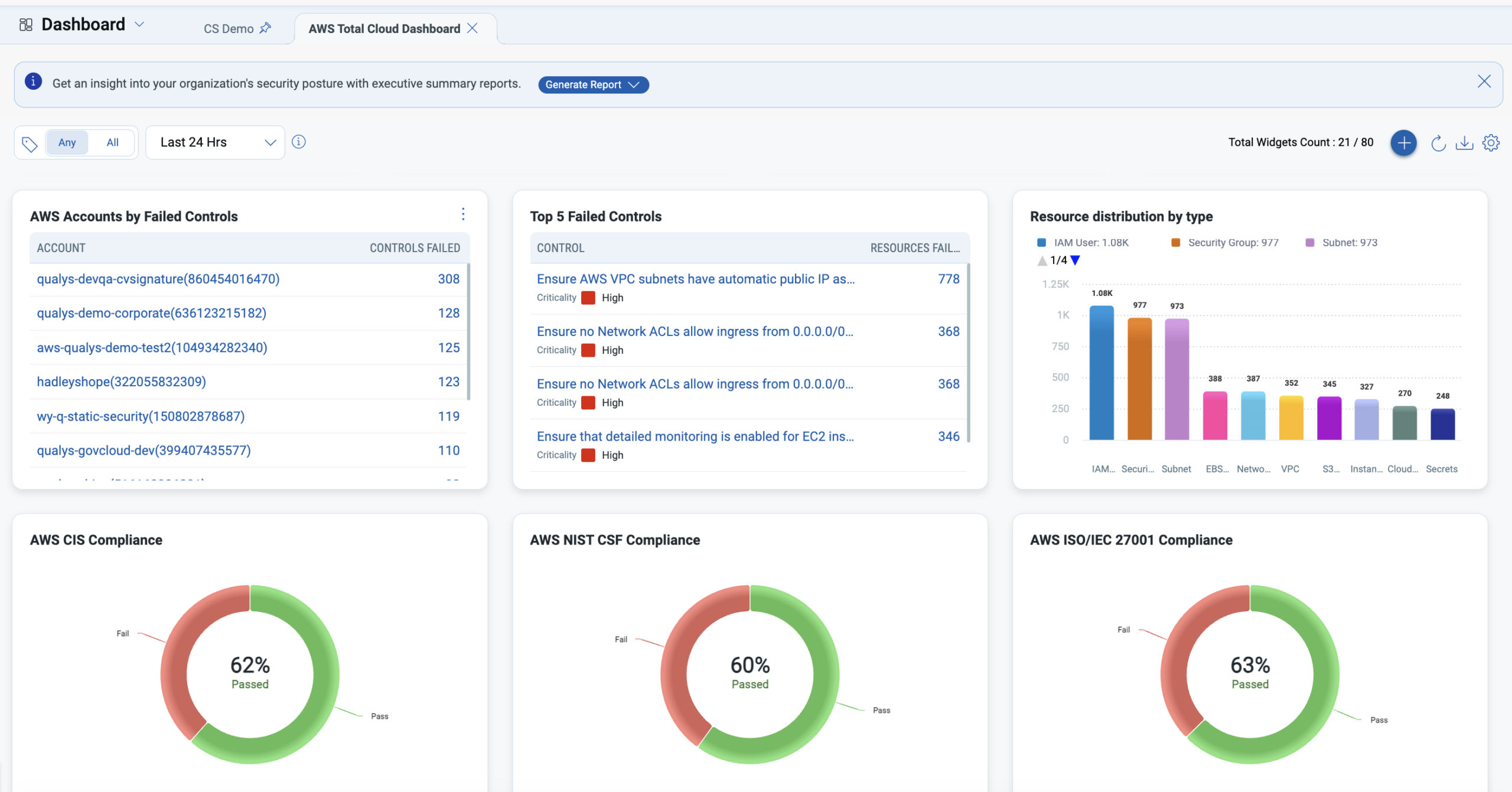
TotalCloud™ compliance dashboards provide a consolidated view of failed controls, resource exposure, and alignment across CIS, NIST CSF, and ISO frameworks, enabling continuous assessment rather than periodic audits.
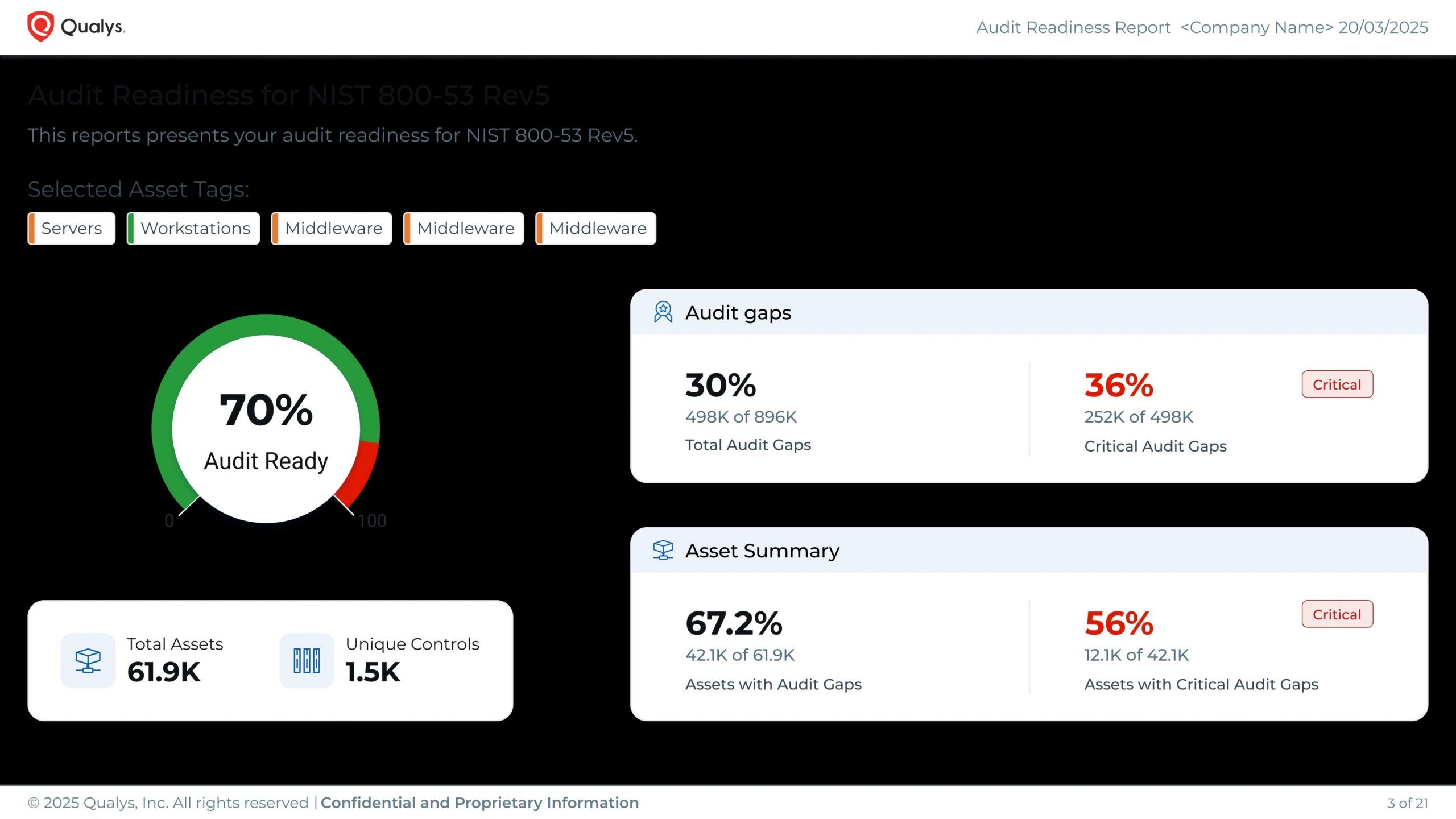
Policy Audit includes Audit Readiness Reports tailored to each compliance framework to identify critical audit gaps at the board and CISO levels, as well as Audit Fix, which enables swift remediation from build to runtime.
Where they fit in a modern compliance stack
Qualys TotalCloud and Qualys Policy Audit together form the cloud compliance foundation for organizations that need to continuously enforce, measure, and prove control effectiveness in fast-changing cloud environments.
Qualys Insights
What does audit readiness look like when controls, policies, and evidence are assessed together?
2. Wiz
When a deep cloud risk context must be established quickly
In complex cloud environments, security leaders often struggle to understand how misconfigurations, identities, and vulnerabilities combine to create real exposure. Wiz is designed to surface this context rapidly, enabling teams to see risk paths rather than isolated findings.
- Wiz delivers broad, agentless visibility across cloud workloads, configurations, identities, and data.
- Compliance framework coverage is available, but depth and evidence structure vary by regulatory use case.
- Evidence collection is derived from snapshot-based posture analysis rather than continuous control evaluation.
- Risk prioritization is a core strength, driven by contextual risk graphs that highlight attack paths.
- Remediation execution depends on external tools and operational workflows.
- Audit reporting often requires additional translation to meet regulator and auditor expectations.
Where it fits in a modern compliance stack
Wiz functions as a high-value risk context and exposure analysis layer, informing compliance prioritization rather than serving as a primary compliance engine.
3. Microsoft Defender for Cloud
When compliance is anchored to a Microsoft-centric cloud strategy
Organizations deeply invested in Microsoft Azure often seek native security and compliance capabilities tightly integrated into their cloud environment. Defender for Cloud addresses this need through embedded posture management and policy enforcement.
- Defender for Cloud provides strong visibility across Azure resources, with expanding support for other clouds.
- Compliance frameworks are supported natively, particularly for Microsoft-aligned standards and benchmarks.
- Evidence collection is continuous within supported environments but may be uneven across hybrid estates.
- Risk prioritization is policy- and configuration-driven rather than exploitability-led.
- Remediation workflows integrate well with Microsoft-native tooling.
- Audit reporting is effective for Azure-centric audits but may require augmentation for multi-cloud or regulatory depth.
Where it fits in a modern compliance stack
Defender for Cloud works best as a native compliance and posture layer within Microsoft-first environments, complemented by broader platforms for multi-cloud assurance.
4. Orca Security
When the speed of visibility matters more than procedural depth
Cloud-native teams often need immediate insight into risk without introducing deployment friction or operational overhead. Orca addresses this need through agentless scanning that surfaces exposure quickly across dynamic cloud environments.
- Orca delivers broad, agentless visibility across cloud workloads, configurations, identities, and data stores.
- Compliance framework coverage is available, but depth and evidence structure vary depending on regulatory requirements and use case.
- Evidence collection is snapshot-based, reflecting posture at a point in time rather than continuous control evaluation across the lifecycle.
- Risk prioritization benefits from strong asset relationship modeling that highlights potential attack paths and exposure chains.
- Remediation depends on external tooling and operational workflows rather than native orchestration.
- Audit reporting often requires additional interpretation or supplementation to meet regulator and auditor expectations.
Where it fits in a modern compliance stack
Orca supports rapid visibility and contextual risk understanding in cloud-first environments, complementing compliance platforms that provide continuous control enforcement and audit-grade assurance.
5. Palo Alto Networks Cortex Cloud
When compliance decisions are driven by threat and runtime security
In security-led organizations, compliance prioritization is often informed by runtime behavior and adversary activity. Cortex Cloud reflects this approach by tying posture and compliance signals to threat detection.
- Cortex Cloud provides strong visibility across cloud assets, workloads, and runtime activity.
- Compliance framework support exists but is secondary to security detection and response capabilities.
- Evidence collection is derived from security telemetry rather than dedicated control mapping.
- Risk prioritization benefits from threat intelligence and behavioral context.
- Remediation aligns closely with security operations workflows.
- Audit reporting typically requires additional structuring for formal compliance use.
Where it fits in a modern compliance stack
Cortex Cloud supports threat-informed compliance decisions and is best positioned as a security context layer rather than a standalone compliance platform.
6. Trend Micro Cloud One
When compliance must extend into workload and application security
Organizations running diverse workloads often need compliance visibility that reaches beyond configuration into runtime protection. Cloud One addresses this need through integrated workload and container security.
- Cloud One provides visibility across cloud workloads and containerized environments.
- Compliance framework support is available for infrastructure and workload controls.
- Evidence collection is continuous for supported services but limited for governance-level requirements.
- Risk prioritization incorporates workload and vulnerability context.
- Remediation integrates effectively with workload security tooling.
- Audit reporting may require supplementation for enterprise regulatory audits.
Where it fits in a modern compliance stack
Cloud One functions as a workload-focused compliance and security layer that complements governance-centric platforms.
7. SentinelOne Singularity Cloud Platform
When an endpoint-driven security strategy extends into the cloud
Organizations extending endpoint-centric security models into cloud environments often seek consistent detection and response across workloads. Singularity Cloud reflects this security-first expansion.
- The platform provides growing visibility across cloud workloads and identities.
- Compliance framework coverage is limited compared to compliance-first platforms.
- Evidence collection is indirect, based on security signals rather than control evaluation.
- Risk prioritization benefits from behavioral detection and anomaly analysis.
- Remediation workflows align strongly with security response actions.
- Audit reporting typically requires external tooling to formalize compliance.
Where it fits in a modern compliance stack
Singularity Cloud prioritizes compliance through security insights while relying on dedicated platforms for audit defensibility.
8. Fortinet Lacework Cloud Security
When behavioral risk signals matter more than static compliance checks
In highly dynamic cloud environments, compliance gaps often emerge from unexpected behavior rather than explicit control failures. As developer self-service, automation, and ephemeral workloads increase, static configuration checks alone struggle to surface early indicators of drift. Fortinet Lacework Cloud Security addresses this by focusing on behavioral context across cloud workloads.
- Lacework provides broad multi-cloud visibility by continuously observing runtime behavior across workloads rather than relying solely on static posture assessments.
- Compliance framework coverage is available, but control mapping and evidence are derived indirectly from security telemetry rather than a purpose-built compliance evaluation.
- Evidence collection reflects observed behavioral signals and anomalies rather than continuous control validation across the full lifecycle.
- Risk prioritization is a core strength, informed by behavioral baselines that surface deviations with potential security and compliance impact.
- Remediation depends on integration with Fortinet and external security operations workflows rather than native compliance enforcement.
- Audit reporting typically requires translation and supplementation to meet formal regulatory and auditor requirements.
Where it fits in a modern compliance stack
Fortinet Lacework Cloud Security functions as a behavioral risk and drift detection layer that informs compliance prioritization, complementing platforms responsible for continuous control enforcement and audit-grade assurance.
9. Amazon Web Services Security Hub
When native cloud aggregation is the starting point
AWS-native teams often begin compliance efforts with built-in services that centralize findings across accounts. Security Hub serves as an aggregation layer for this purpose.
- Security Hub aggregates security and compliance findings across AWS services and accounts.
- Compliance standards are supported for AWS-aligned frameworks and benchmarks.
- Evidence collection is continuous within AWS but does not extend beyond the ecosystem.
- Risk prioritization is standards-based rather than exposure-led.
- Remediation depends on downstream AWS services and operational workflows.
- Audit reporting is suitable for AWS-specific audits but insufficient for multi-cloud regulatory needs.
Where it fits in a modern compliance stack
Security Hub acts as a foundational aggregation layer for AWS environments, typically complemented by cross-cloud compliance platforms.
10. ServiceNow Risk & Compliance (IRM / GRC)
When governance, workflow orchestration, and audit execution are the primary challenges
In large enterprises, compliance friction often arises from ownership, approvals, and audit execution rather than from missing controls. ServiceNow Risk and Compliance addresses this by centralizing governance and audit workflows.
- Centralizes control definitions, ownership, exceptions, and attestations across SOC 2, ISO 27001, NIST, PCI DSS, and other mandates such as DORA.
- Evidence collection is workflow-driven, based on approvals and documentation rather than live cloud telemetry.
- Risk prioritization reflects governance inputs and process state rather than real-time exposure.
- Remediation tracking focuses on accountability and task coordination across teams.
- Continuous cloud posture assessment and workload-level compliance enforcement depend on upstream platforms.
- Audit reporting is strong for traceability, but reflects the depth and timeliness of integrated data sources.
Where it fits in a modern compliance stack
ServiceNow supports governance and audit execution; however, it relies on cloud security and compliance platforms for continuous control validation and technical posture insight.
Final Perspective: Resilience Can Be Measured. Compliance Proves It.
In cloud-first enterprises, resilience is proven through continuous control enforcement, drift detection, risk prioritization, and defensible evidence under real operating conditions. When compliance operates as a continuous model rather than an audit exercise, it becomes a reliable signal of resilience.
Organizations that embed compliance into cloud posture, policy enforcement, and remediation workflows gain durable confidence that their environments can scale securely and withstand scrutiny as conditions change. In this context, compliance is not overhead. It is engineered, measurable resilience by design.
If cloud compliance must be continuous, provable, and scalable, see how Qualys TotalCloud™ supports that model in practice.
Frequently Asked Questions (FAQs)
What are cloud compliance tools?
Cloud compliance tools continuously assess cloud environments against regulatory, industry, and internal standards by evaluating live configurations, identities, and policies across cloud and hybrid environments.
How is cloud compliance different from traditional IT compliance?
Traditional compliance relies on static infrastructure and periodic audits. Cloud compliance must address ephemeral assets, continuous change, shared responsibility models, and multi-cloud sprawl through automation and real-time evidence.
Why is continuous compliance becoming mandatory?
Regulators, customers, and auditors increasingly expect controls to be enforced at all times. Continuous compliance reduces detection gaps, strengthens audit defensibility, and surfaces operational risk earlier.
Which compliance frameworks do cloud compliance tools typically support?
Enterprise platforms commonly support NIST, SOC 2, ISO 27001, PCI DSS, HIPAA, GDPR, and CIS Benchmarks, with control reuse across overlapping mandates such as DORA.
How do cloud compliance tools handle multi-cloud and hybrid environments?
Effective tools maintain unified asset visibility across cloud providers, on-prem infrastructure, and endpoints to ensure consistent control enforcement and defensible evidence.
What is the role of risk-based prioritization in compliance
Risk-based prioritization aligns compliance findings to exploitability and business impact, enabling teams to focus remediation on issues that materially increase exposure.
Do cloud compliance tools replace audits?
No. They make audits less disruptive by maintaining audit-ready evidence continuously, turning audits into verification exercises rather than manual investigations.
How does Qualys support cloud compliance?
Qualys supports cloud compliance through Qualys TotalCloud and Qualys Policy Audit, enabling continuous cloud posture assessment, control evaluation across frameworks, and audit-grade evidence generation.
How should organizations choose the right cloud compliance tool?
Selection should start by identifying the dominant compliance constraint, then evaluating tools based on their capability fit within a modern compliance stack rather than on feature comparison.
Is cloud compliance a security or governance function?
Both. Cloud compliance sits at the intersection of security operations, risk management, and governance, aligning control enforcement with operational resilience.
Subject Matter Expert Contributors
- Shrikant Dhanawade, Director, Product Management, Cloud Security
- Abhinav Mishra, Director, Product Management, Qualys TotalCloud Kubernetes and Container Security
- Bill Reed, Principal Product Manager, Product Marketing