What is Patch Management Automation and Why It Matters
Table of Contents
- Rebuilding Patch Management for Environments That Refuse to Slow Down
- Manual Vs. Automated Patch Management
- How Patch Management Automation Works
- The Tangible Benefits of Automated Patch Management
- Common Challenges in Automating the Patch Management Process
- What to Look for in a Patch Management Automation Platform
- Choosing the Right Automated Patching Approach
- How Qualys Supports Patch Management Automation at Scale
- The Future of Patch Automation
- Frequently Asked Questions (FAQs)
Executive Summary
Environments rarely stay as orderly as they begin. New workloads, faster releases, and growing attack surfaces stretch manual patching beyond its limits. The real risk emerges in the widening gap between spotting a vulnerability and fixing it. Automated patch management closes that gap.
It creates a unified patch lifecycle that monitors assets continuously, applies risk-based patch prioritization, validates updates through production patch testing, and uses patch management software to deploy fixes across hybrid cloud environments. MTTR vulnerability patching improves because the workflow moves from scattered tasks to an intelligence-led sequence.
This blog explores the conditions that make automated patching dependable and the structural shifts needed to move from ad-hoc remediation to automation built for scale.
Rebuilding Patch Management for Environments That Refuse to Slow Down
Digital footprints of most organizations are expanding faster than their resources to secure them. Every new application, workload, or endpoint introduces another surface that must be secured. Manual patching once worked when environments were small and static. Today, it buckles under the velocity of change.
That is why patch management automation has become the invisible engine of modern resilience. It uses intelligent workflows and orchestration software to detect vulnerabilities, test patches, deploy updates, and validate outcomes, all without continuous human oversight. That way, patching is transformed from a periodic task into a continuous safeguard that runs quietly in the background.
Automation does more than accelerate remediation; it restores balance and shortens the distance between detection and defense — the narrow window where most breaches occur. When patching becomes automated, digital trust stops depending on human endurance and starts operating on system intelligence.
Qualys Insights
Discover the blueprint for automated patching at scale. Read ‘Qualys Patch Management Guide’ for 5 core steps that help automation deliver meaningful impact.
Manual Vs. Automated Patch Management
Manual patching was built for a slower world. One where applications changed quarterly, not hourly. In that world, IT teams could plan updates, test them on a few systems, and move through the network, one patch at a time.
That rhythm has collapsed under the weight of scale. Hybrid environments now span thousands of endpoints running different systems and dependencies, and no spreadsheet or ticket queue can keep pace with that speed or complexity.
That is where automation changes the equation. It replaces fragmented, ticket-based steps with policy-driven orchestration and continuous governance. Instead of waiting for human approval, systems detect vulnerabilities, map them to available patches, and deploy fixes under defined policies. The process is faster, but more importantly, it is repeatable, governed by logic rather than fatigue.
| Characteristic | Manual patching | Automated patch management |
| Discovery | Spreadsheet audits | Continuous asset inventory |
| Prioritization | Human triage | Risk-based scoring |
| Testing | Ad hoc | Staged rings and rollback |
| Deployment | Manual scripts | Policy-driven automation |
| Verification | Spot checks | Automated validation and reports |
The difference between Manual Patching and Automated Patch Management is structural. Manual patching depends on coordination. Automated patching depends on connection. Every stage, from detection to validation, speaks the same language, driven by data that updates in real time. The outcome is consistency at scale, where patches are applied uniformly, errors decline, and risk windows shrink.
A mature automated patch management process does not eliminate the need for human judgment. It preserves it for where it matters most, deciding what to prioritize, what to delay, and how to align remediation with business continuity. It turns the patch cycle from a scramble into a system.
How Patch Management Automation Works
Every effective patch management process follows a structured sequence. These steps seem simple, but coordinating them across thousands of assets is difficult without automation.
The Patch Management Lifecycle
- Asset discovery: Build a live inventory of all operating systems, applications, and dependencies.
- Vulnerability assessment: Identify which assets are missing patches or contain exploitable weaknesses.
- Patch mapping: Correlate each vulnerability to the vendor’s fix or mitigation.
- Testing: Deploy updates in controlled groups to prevent production incidents.
- Deployment: Roll out patches automatically within approved maintenance windows.
- Validation: Confirm successful installation and generate audit reports.
In an automated setup, each step feeds into the next through shared intelligence. Discovery builds a live inventory. Detection identifies vulnerabilities. Prioritization ranks them by risk. Testing and deployment occur in controlled phases, and validation confirms success.
By linking these actions through a single data model, automation replaces fragmented processes with continuous orchestration. What used to be a series of disconnected updates becomes a unified, measurable cycle of risk reduction.
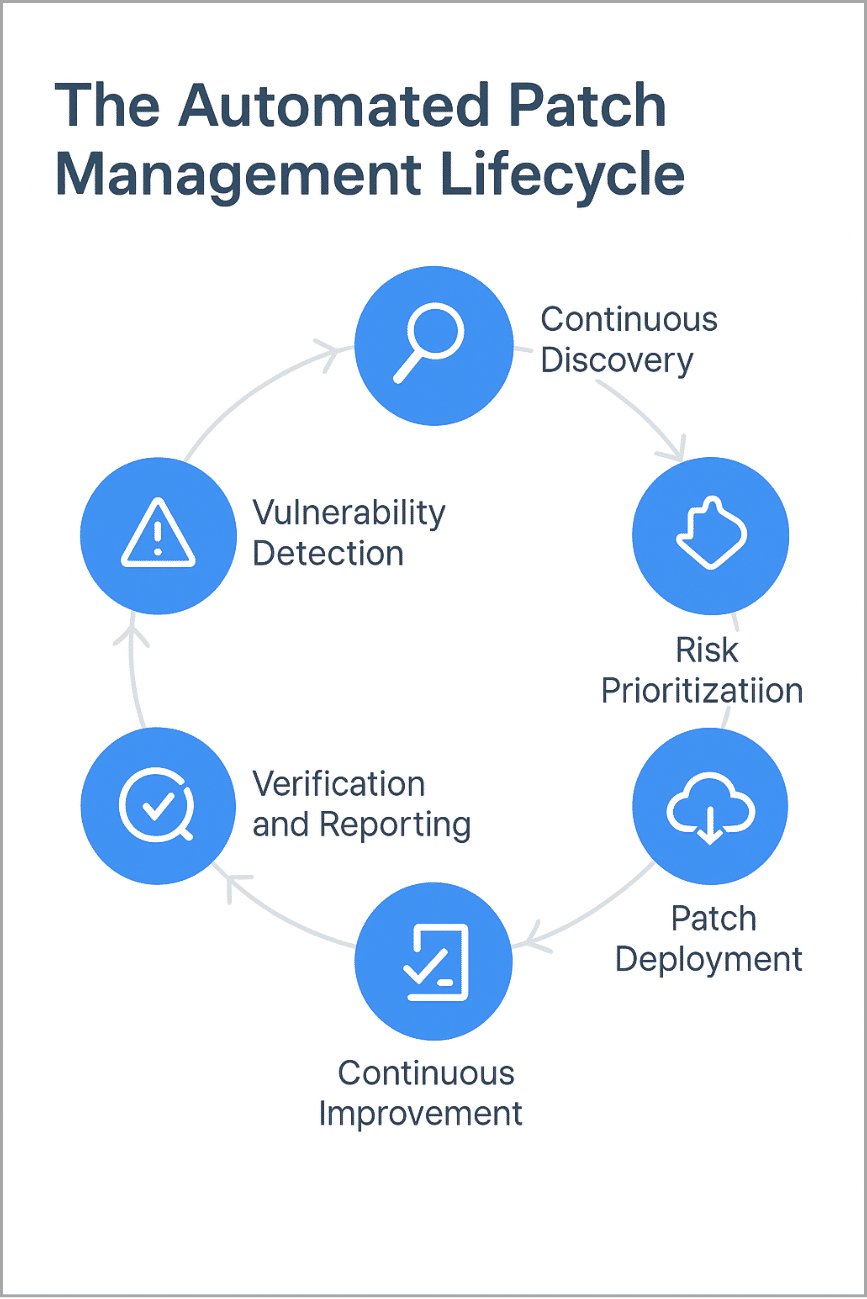
Modern patching software platforms unify these stages in a single console. Only a few extend visibility to remote and cloud environments, applying the same governance regardless of where the workload lives.
The Tangible Benefits of Automated Patch Management
Executives measure cybersecurity by impact, specifically, how quickly detection is turned into remediation and how reliably that progress can be verified. Patch management automation directly influences those metrics.
Of all the benefits of automated patching, speed is the first visible gain. Automated patching can reduce the mean time to patch from an industry average of over 30 days to less than a week, shrinking the exploit window before attackers act.
Consistency is next. Policy-based automation ensures that every asset, whether on-premises or in the cloud, receives updates on time and according to governance standards.
Reliability follows. Automated testing, staged rollouts, and rollback controls make patching safer than manual intervention. And because each step is logged, compliance reporting becomes faster and more precise.
Measured benefits include:
- Faster mean time to patch, often from weeks to days.
- Up to 90% on-time compliance with internal patch SLAs.
- Lower rates of unplanned downtime due to better testing and rollback.
- Reduced audit effort through consistent evidence collection.
- Higher employee productivity as routine tasks move to policy-based automation.
From a cost perspective, automation lowers total effort while improving control quality. From a risk perspective, it prevents known exploits from turning into breaches. Both matter equally to boards and regulators.
Common Challenges in Automating the Patch Management Process
Even automation brings friction. It simplifies execution but introduces new forms of complexity. The most advanced platforms still depend on solid operational discipline.
Frequent challenges include:
- Legacy systems: End-of-life operating systems or custom software with no vendor support.
- Integration complexity: Multiple tools for asset management, vulnerability scanning, and deployment that do not share context.
- Testing constraints: The need to validate critical patches without breaking production workloads.
- Change windows: Limited downtime for globally distributed systems.
- Cultural resistance: Teams accustomed to manual control can be slow to trust automation.
Legacy environments and fragmented toolchains can slow adoption, as some patches need testing to prevent disruptions, and integrations with CMDBs, ITSM workflows, and scanners demand both technical and governance alignment. Confidence in automation grows only through transparency, via clear dashboards that show what was patched, when, and why.
Automation succeeds when it augments human decision-making, rather than replacing it. The technology handles repetition; people handle judgment. Together, they close the distance between detection and defense.
True progress happens when organizations treat automation as a journey, starting with standardized discovery and gradually extending it to prioritization and deployment once trust in data accuracy is established.
What to Look for in a Patch Management Automation Platform
With dozens of patching software solutions on the market, it is critical to evaluate beyond the feature checklist. The right platform should align with your operational maturity, security architecture, and compliance needs, delivering both automation and intelligence. It must not only deploy updates but also help teams understand why those patches matter.
The most capable platforms share six traits:
- Broad coverage across operating systems and third-party apps.
- Integration with vulnerability detection tools or risk scoring platforms for unified visibility.
- Policy-based scheduling and risk-based prioritization.
- Staged rollouts and rollback safeguards in case of failed updates.
- Real-time reporting and SLA tracking.
- Scalability across hybrid and multi-cloud environments.
The most valuable feature is visibility, knowing exactly which systems are patched, which remain exposed, and why. That transparency enables better governance and more informed security reporting, making patching part of a continuous risk management cycle.
Choosing the Right Automated Patching Approach
Selecting the right automation strategy starts with clarity about your environment, risk appetite, and operational model. Begin by mapping assets, dependencies, and patch workflows to identify where delays occur — in prioritization, testing, or scheduling.
Key considerations include:
- Size and scale: Large enterprises benefit from centralized control and policy templates, while smaller organizations may prefer managed patching as a service.
- Compliance expectations: Regulated industries require detailed audit trails and reporting automation.
- Network architecture: Hybrid networks need optimized content delivery to reduce bandwidth impact.
- Change management style: Some teams value full automation; others prefer guided recommendations and human approval points.
- Ownership model: Decide whether IT or security leads the process, or whether both unify under shared governance.
Automation succeeds when it adapts to your structure, and not the other way around.
How Qualys Supports Patch Management Automation at Scale
Qualys VMDR with Patch Management exemplifies how modern security automation bridges continuous vulnerability assessment with automated patch deployment. VMDR continuously identifies and prioritizes vulnerabilities across on-premises and cloud environments, while Patch Management operationalizes that insight, correlating each risk with the right fix and deploying updates through governed workflows. It continuously discovers assets across on-premises and cloud environments, maps vulnerabilities to verified patches, and orchestrates deployment through a single, governed workflow.
By anchoring both vulnerability intelligence and patch execution to the same data foundation, organizations gain real-time visibility, faster decision cycles, and stronger governance. This convergence redefines remediation, shifting it from reactive maintenance to a proactive strategy for measurable risk reduction and enterprise resilience.
The Future of Patch Automation
As enterprises adopt AI-driven observability and autonomous infrastructure, patching will evolve from reaction to prediction. Future systems will use AI and predictive analytics to anticipate vulnerabilities before public disclosure and pre-stage patches accordingly. Self-healing environments will apply updates dynamically, analyzing dependencies in real time to minimize downtime.
The cultural shift will be as significant as the technical one. Security and IT operations will converge into shared accountability models: a unified discipline often described as risk operations. Automation will no longer be a feature; it will be the baseline for resilience.
As enterprise environments grow more distributed, the objective will shift from patching faster to preventing exposure altogether. Automation will become the connective tissue linking vulnerability management, configuration control, and incident response, creating a continuous defense loop. Organizations that start this journey now will not just patch faster; they will build the adaptive resilience that defines modern cybersecurity.
Make automated patching count. Use Qualys TruRisk™ to eliminate high-impact exposures with clarity and precision.
Frequently Asked Questions (FAQs)
What is automated patch management?
Automated patch management uses software to identify missing updates, prioritize them based on risk, test and deploy them on schedule, and verify success — or apply configuration-based fixes when no patch exists — all without manual intervention.
Why is patch management important for cybersecurity?
Most breaches exploit known vulnerabilities. A strong patch management process limits the time between disclosure and fix, reducing exposure to common attack vectors.
What are the main benefits of automated patching tools?
They deliver speed, consistency, compliance visibility, and fewer configuration errors compared to manual patching.
Is automated patching safe for production systems?
Yes, when applied through staged rollouts, maintenance windows, and rollback options tested under controlled policies.
Can automation handle third-party applications?
Modern tools manage updates for browsers, productivity suites, runtimes, and developer tools alongside operating systems.
What challenges do large enterprises face?
Scale, legacy systems, distributed networks, and fragmented ownership across IT and security remain common hurdles.
