ShadyPanda: The Silent Browser Takeover Threat and How Qualys TruRisk Eliminate Helps You Stop It
Executive Summary
ShadyPanda has exploited trusted browser extensions to compromise millions of users, illustrating how legitimate software can unexpectedly become harmful. Qualys TruRisk Eliminate empowers organizations to identify risky behaviors, prioritize real threats, and eliminate malicious components before attackers exploit them.
How Browser Extensions Have Become a New Blind Spot
Browser extensions are part of everyday work. We install them to save time, stay organized, or improve productivity. However, between 2024 and 2025, one threat actor exploited this trusted ecosystem to create a massive covert malware delivery mechanism that organizations no longer ignore.
ShadyPanda exploited a widespread misconception:
If an extension is verified, widely used, and looks safe, it must be trustworthy.
That assumption no longer holds.
Understanding ShadyPanda: A Threat Built on Trust, Not Exploits
Unlike traditional cyberattacks that rely on phishing or zero-day vulnerabilities, ShadyPanda has established an operation built on patience, legitimacy, and a carefully crafted reputation. The group exploits trust within the browser extension ecosystem rather than targeting software flaws.
Researchers have uncovered that ShadyPanda has been executing long-term browser supply chain attacks since 2018 by publishing seemingly harmless extensions. These include wallpapers, utilities, and new-tab tools designed to integrate seamlessly into everyday browser use while amassing high installation counts, positive user ratings, and a trusted status in the marketplace.
Once this trust was firmly established, ShadyPanda cleverly weaponized these extensions through updates, turning them into covert malware delivery mechanisms. These malicious updates enabled remote code execution (RCE) backdoors and large-scale spyware operations without raising traditional security alarms.
Extensions such as Clean Master were operated legitimately for years to build a substantial user base across Chrome and Edge. Researchers estimate that more than 4.3 million users across both browsers were affected, underscoring the scale of the campaign. This was not opportunistic malware; it represented an infrastructure-level compromise of the browser ecosystem itself.
These malicious extensions are actively harvesting a wide range of sensitive browser data, including:
- Browsing Activity
- User Input and Search
- Device Fingerprinting
- Behavioral Biometrics
- Identity & Storage
This level of access empowers attackers to profile users, hijack sessions, and potentially infiltrate enterprise environments. Addressing this kind of risk requires more than trust signals or periodic controls. It requires the ability to identify, prioritize, and eliminate risk arising from legitimate software that has turned malicious. This is where Qualys TruRisk Eliminate comes in.
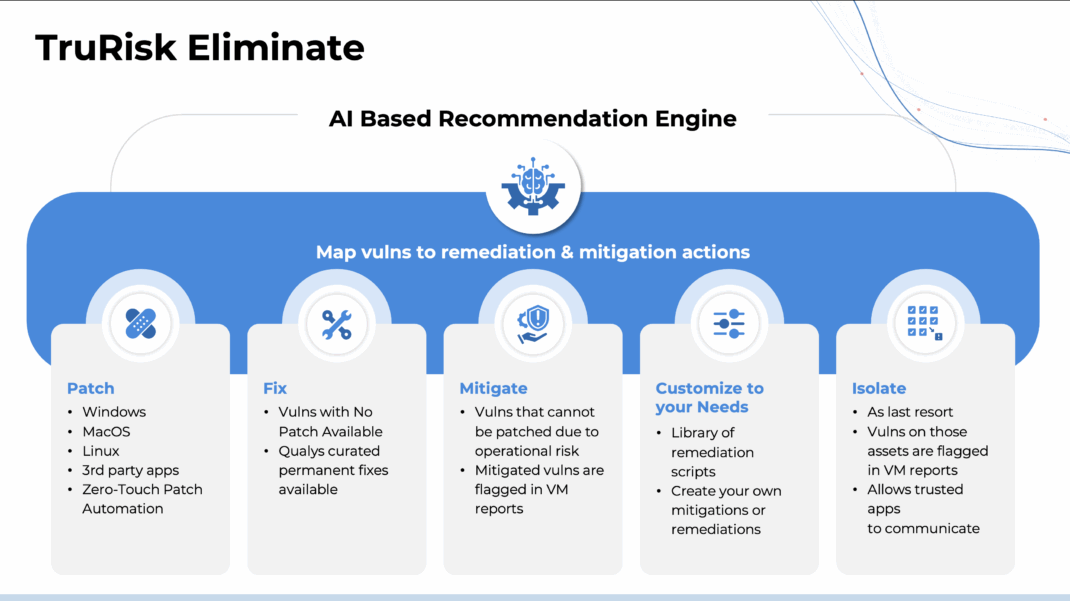
How Qualys TruRisk Eliminate Helps Protect Against ShadyPanda-Like Threats
Qualys TruRisk Eliminate delivers this capability by identifying risky behaviors, prioritizing them based on real threat context, and blocking or removing malicious components before they can be exploited.
To help organizations operationalize this approach, here is a high-level playbook on how to use TruRisk Eliminate to defend against ShadyPanda-like threats.
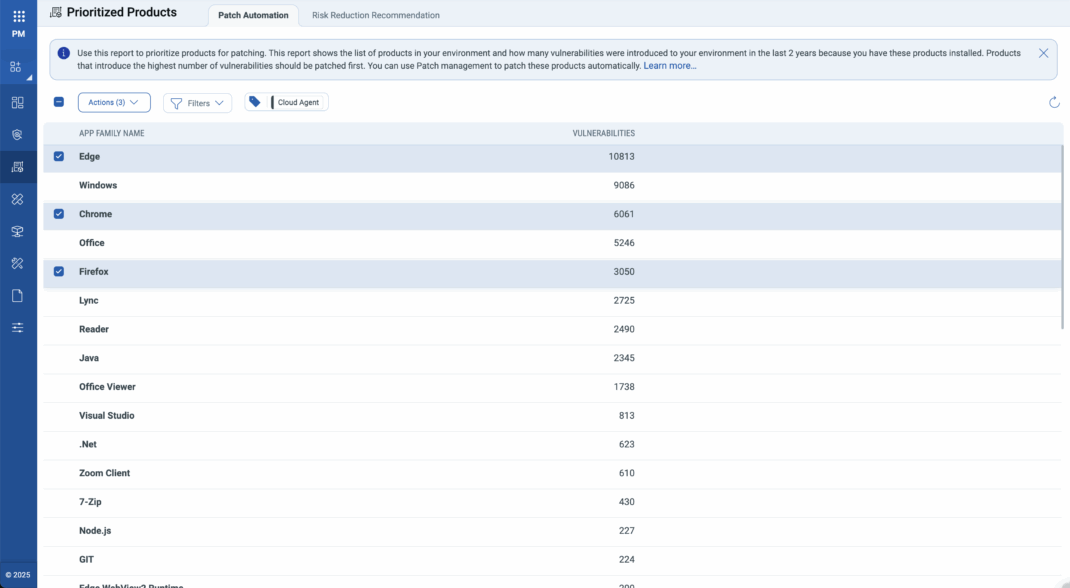
Step 1 – Patch Automation for Chrome & Edge
Leverage Zero-Touch Patch Automation with Qualys Patch Management to guarantee that all endpoints receive the latest secure browser versions with zero user delay. This proactive measure fortifies browser integrity and significantly minimizes exposure to threats originating from malicious extensions.
With Zero-Touch Patch Automation, you will:
- Automatically deploy the latest Chrome Stable and Edge Stable updates.
- Effectively close exploited CVEs leveraged by malicious extensions.
- Slash Mean Time to Resolution (MTTR) from days or weeks to just hours.
Step 2- Use CAR Scripts for Eliminating Non-Default / Rogue Browser Extensions
Leverage Qualys Custom Assessment & Remediation (CAR) to deploy decisive scripts that will detect and remove any non-default or unauthorized Chrome/Edge extensions.
With CAR Scripts, you can:
- Identify all installed extensions (Chrome/Edge) immediately.
- Compare them rigorously against your approved extension list.
- Eliminate any untrusted or malicious extensions without hesitation.
- Execute a comprehensive organization-wide clean-up within minutes.
CAR Scripts also enables you to remove all passwords stored in Chrome, Edge, or Firefox directly using PowerShell. Import the script from the Library and proceed confidently with your actions.

Conclusion
ShadyPanda exposes a critical shift in attacker strategy: weaponizing trusted software to infiltrate environments silently. Defending modern enterprises requires more than patching vulnerabilities. It demands behavioral intelligence and proactive risk elimination.
Qualys TruRisk Eliminate delivers these capabilities at scale, empowering teams to uncover malicious behaviors, block emerging threats, and remove compromised components before attackers gain a foothold.
Go Beyond Patching with Qualys TruRisk Eliminate and de-risk cyber threats before they impact your business.
Qualys Insights
See how Qualys TruRisk Eliminate helps you stop threats like ShadyPanda.
Frequently Asked Questions (FAQs)
What is ShadyPanda?
ShadyPanda is a significant threat campaign that exploits trusted browser extensions to deliver spyware and malicious functionality on a large scale. The attackers cleverly launched seemingly legitimate extensions, earning user trust, and then weaponized them through updates that affected millions of Chrome and Edge users.
Why are browser extensions a growing security risk?
Browser extensions possess extensive permissions and deep access to user activity. When a trusted extension turns malicious, it operates silently, collecting sensitive data, redirecting traffic, or executing scripts without relying on traditional vulnerabilities.
Did ShadyPanda exploit browser vulnerabilities or zero-days?
No. ShadyPanda exploited trust and reputation rather than zero-day vulnerabilities. This campaign relied on legitimate distribution channels and behavior-based abuse, steering clear of specific CVEs.
Why isn’t traditional CVE-based security enough for threats like ShadyPanda?
Because ShadyPanda does not depend on exploitable vulnerabilities, it leverages normal extension functionality and updates. This reality underscores the urgent need for continuous visibility into software behavior, far exceeding simple vulnerability scanning.
How does Qualys TruRisk Eliminate address ShadyPanda-like threats?
Qualys TruRisk Eliminate helps organizations to identify when legitimate software starts behaving maliciously, prioritize those risks using real threat context, and take decisive action to block or remove compromised components before they can be exploited.
Does Qualys TruRisk Eliminate scan browser stores or extension marketplaces?
No. TruRisk Eliminate does not monitor browser marketplaces. It focuses on risk identification and elimination within your environment, relying on observed behavior, exposure, and threat context.
Can Qualys TruRisk Eliminate help reduce the impact of malicious browser updates?
Absolutely. By delivering continuous visibility into software behavior and prioritizing risks based on tangible real-world context, Qualys TruRisk Eliminate equips organizations to respond swiftly when trusted components turn malicious, effectively reducing exposure and limiting impact.
Is patching still important for defending against extension-based threats?
Certainly, keeping browsers up to date is crucial for closing known vulnerabilities and fortifying the security foundation. Patch automation enhances risk-based detection by minimizing the overall attack surface.
What is the key lesson organizations should take away from ShadyPanda?
The key lesson is that trust is no longer a static concept. Legitimate software can become a risk at any time, making continuous risk assessment and elimination essential to modern security strategies.