LinkedIn Faux Pas Shines Light on Certificate Management
Table of Contents
Visibility and control of digital certificates remains a challenge for even the largest enterprises, as evidenced by a high profile incident this week affecting Microsoft’s LinkedIn. Users accessing LinkedIn on Tuesday got a warning from their browsers alerting them about an insecure connection. The culprit: An expired TLS certificate.
In a statement to the press, LinkedIn said it experienced a “brief delay” in updating a digital certificate, and stated that member data wasn’t affected. Yet, the incident spotlights a nagging issue that frequently trips even the most technically savvy companies in the world: Digital certificate management.
Qualys SSL Labs’ SSL Pulse, which monitors the quality of SSL/TLS support across 150,000 of the most popular websites in the world, rated about 33% of the sites monitored as having inadequate security in its May report. A few thousand of these sites had expired certificates.
Poor digital certificate management is a serious problem that can lead to security lapses since SSL/TLS certificates are critical for the integrity and protection of a host of e-business functions. Specifically, digital certificates are used to ensure the confidentiality, authenticity, integrity and non-repudiation of public-facing online services, internal services, machine-to-machine communications, public cloud services and API integrations.
Consequently, it’s key for enterprises to know how many digital certificates are in use in their organization. They must know when they expire. They must be able to discover if they’re using digital certificates from unapproved Certificate Authorities.
A recent survey of almost 600 IT and security professionals by Ponemon Institute found that digital certificates have caused unanticipated downtime or outages for 74% of respondents. In addition, 71% of respondents believe their organizations do not know how many keys and certificates they have. The costs associated with poor certificate management are real, according to the study. For example, over a two year period, the cost of unplanned outages due to certificate expiration is estimated to average $11.1 million, while the cost of server certificate and key misuse is estimated to average $13.4 million.
How Qualys can help
With proper certificate management, organizations can cut their risk of breaches and unplanned outages, and continuously and effectively protect their digital assets.
Qualys offers a free app called CertView that lets you discover, inventory and monitor your Internet-facing digital certificates, along with their host SSL/TLS configurations and vulnerabilities. CertView provides a graded assessment of both on-premises and cloud-based assets that takes into account elements such as the host, port, service and certificate.
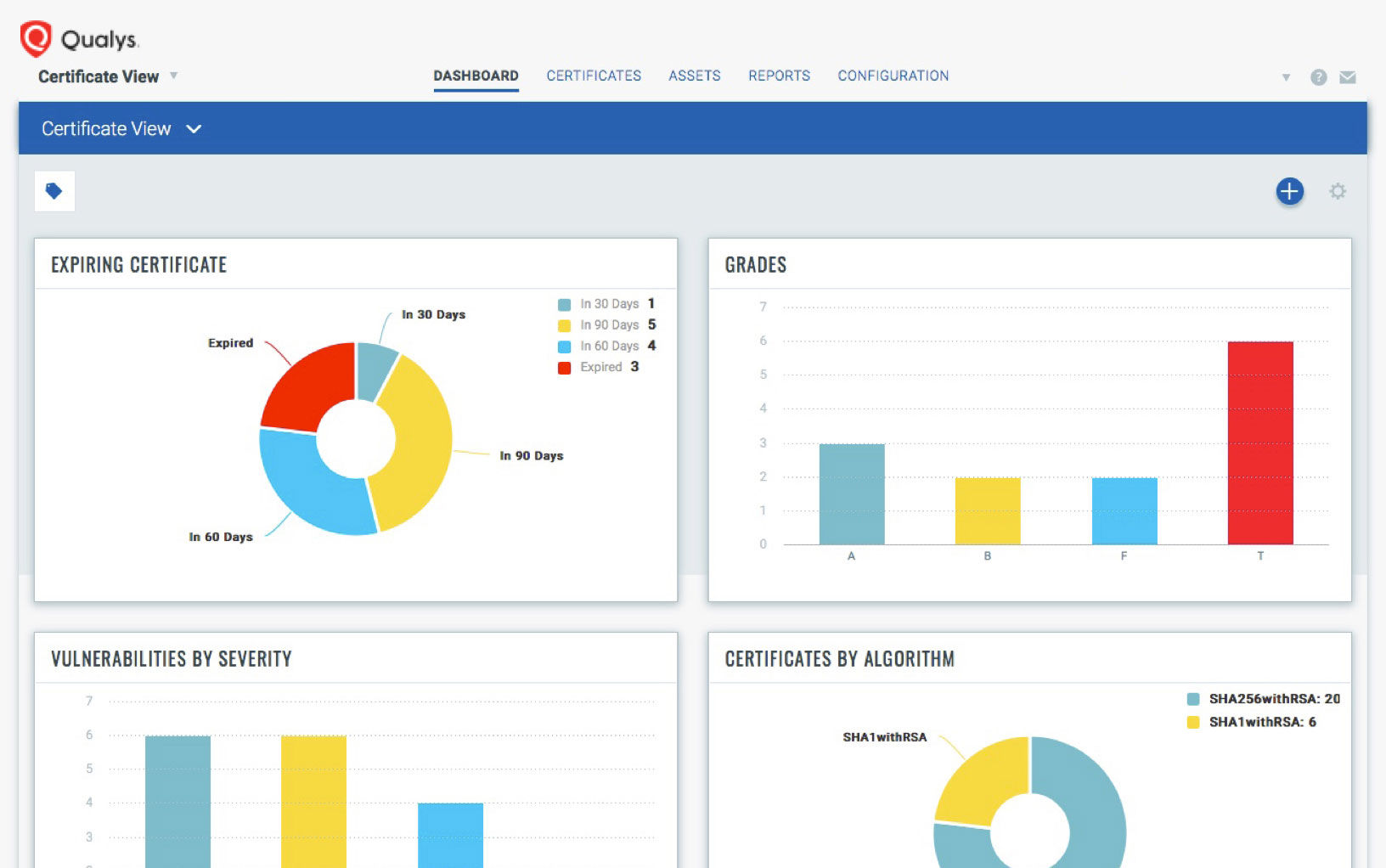
With CertView, organizations can address common use cases such as:
- Preventing downtime and outages caused by expired certificates
- Assessing the strength of SSL/TLS configurations via intuitive certificate grades (A, B, C, D, …) using SSL Labs’ methodology
- Detecting certificate-related anomalies
- Obtaining full certificate visibility via continuous discovery and inventorying, and managing them from a single-pane-of-glass interface with a powerful elastic search engine
- Achieving audit success with automated, downloadable reports
- Carrying out fast, precise remediation (through certificate renewals or TLS configurations)
In short, with CertView, you can quickly identify externally-facing certificates that are weak and non-compliant, along with their associated grades, vulnerabilities and assets, and quickly search through this data, getting results in seconds.
(Asif Karel is Qualys’ Director of Product Management for Certificate Management)
Ivan,
As always, great information.
I’m interested in the OCSP Stapling sharp fall off indicated. Is the root cause understood? I might argue OCSP stapling is a key certificate validation mechanism.
Regards
Nigel