How to Make Log4Shell Remediation Quick & Effective
Confronting the Log4Shell vulnerability in your environment has seemed anything but “easy” due to its prevalence in Java applications. Rapid remediation is critical. In this blog, Qualys offers some advice – and a new utility – to speed up the process.
Remediation is a critical step to ensure that attackers do not exploit the Log4Shell vulnerable assets in your environment. As most organizations have multiple Java-based applications in their environment. and most Java-based applications use Log4J, the scope of this problem is significant. In addition, the ease of exploitation of this vulnerability makes it a race against time to remediate the issue as quickly and effectively as possible.
While Log4Shell is one of the most serious vulnerabilities ever discovered, remediating it is rapidly becoming a faster process than you might think.
Remediation Options
The answer is upgrades and patches… with a little help from Qualys. Let’s review your options:
Wait for the Vendor to Release a Patch
Many of the applications installed in your environment are developed by vendors. As with any application, these third-party applications may be vulnerable to Log4Shell. Most vendors will test their application(s) to ensure that they are not vulnerable for Log4Shell and, if they are, will release a patch to fix the vulnerability.
Qualys recommends customers analyze the risk involved in waiting for the application vendor’s patch to be released. If the risk can be mitigated, then Qualys Patch Management can be used to deploy the vendor’s patch as soon as it is available.
Upgrade Log4J or Remove the JndiLookup Class
On the Apache Log4j webpage (Apache Log4j Security Vulnerabilities), the following actions are recommended to mitigate Log4Shell (CVE-2021-44228):
- Upgrade to Log4j 2.3.1 (for Java 6), 2.12.3 (for Java 7), or 2.17.0 (for Java 8 and later)
- Otherwise, in any release other than 2.16.0, you may remove the JndiLookup class from the classpath
Based on application patching best practices, some may assume that patching a vulnerable application by upgrading the Log4j library may break the application and will require extensive testing to ensure it doesn’t happen.
Therefore, a less risky remediation option might be to remediate the vulnerability by removing the JndiLookup class. Indeed, this action is becoming a popular method by many organizations as the immediate remediation option.
Organizations can use Qualys Patch Management to perform both remediation actions more quickly than before. How?
Qualys Open-Source Remediation Utility
Qualys has released an open source tool that helps our customers perform the removal. It simplifies the complexity of remediating Log4Shell utilizing the removal of the JndiLookup class.
The remediation utility removes all instances of the JndiLookup class from all the vulnerable Log4j libraries found on any and all of your assets.
The initial challenge with Log4Shell remediation is finding all vulnerable Log4j instances in the asset. The Jndilookup class can be found inside a Jar, inside a nested jar (essentially an archive inside an archive), or inside any other types of archives (war, ear, zip etc.) located anywhere on the disk.
To ensure that all instances on a specific asset are remediated, the Qualys remediation utility relies on the findings as reported by the Qualys Log4jScanner utility. (To learn more about Qualys open source scan utility, please refer to our blog: Out-of-Band Detection for Log4Shell.)
The scan utility must run on each asset before running the remediation tool.
What are the benefits of using this remediation tool with Qualys Patch Management?
Benefits of Log4Shell Remediation Using Qualys
- The new remediation tool works in conjunction with the Qualys Log4Shell scan tool. Customers can find all vulnerable instances of Log4j on their assets and prioritize their remediation using Qualys VMDR.
- Utilizing Qualys Patch Management, customers can run the remediation tool on Windows devices vulnerable to Log4Shell. Since the tool is delivered in the cloud, targeted devices can be in any physical location, which provides efficient remediation even for remote and WFH devices. The remediation tool removes the Jndilookup class from the asset and reports the results to Qualys Patch Management.
- Leveraging Qualys Patch Management’s reporting capabilities, customers can track the remediation status reported by the remediation tool.
- Further VM scans can be used to validate the removal of all vulnerabilities.
How to Remediate Log4Shell Using the Qualys Open Source Remediation Utility
Existing Qualys Patch Management customers can follow these four steps to remediate Log4Shell in their assets.
Step 1:
Download the remediation tool from GitHub.
Store the Log4jRemediate.exe file on a Web server (internally or externally), so all your agents can access it over HTTP.
Step 2:
Create a new Job in Patch Management and select a tag (or individual assets) that represent the assets you would like to remediate.
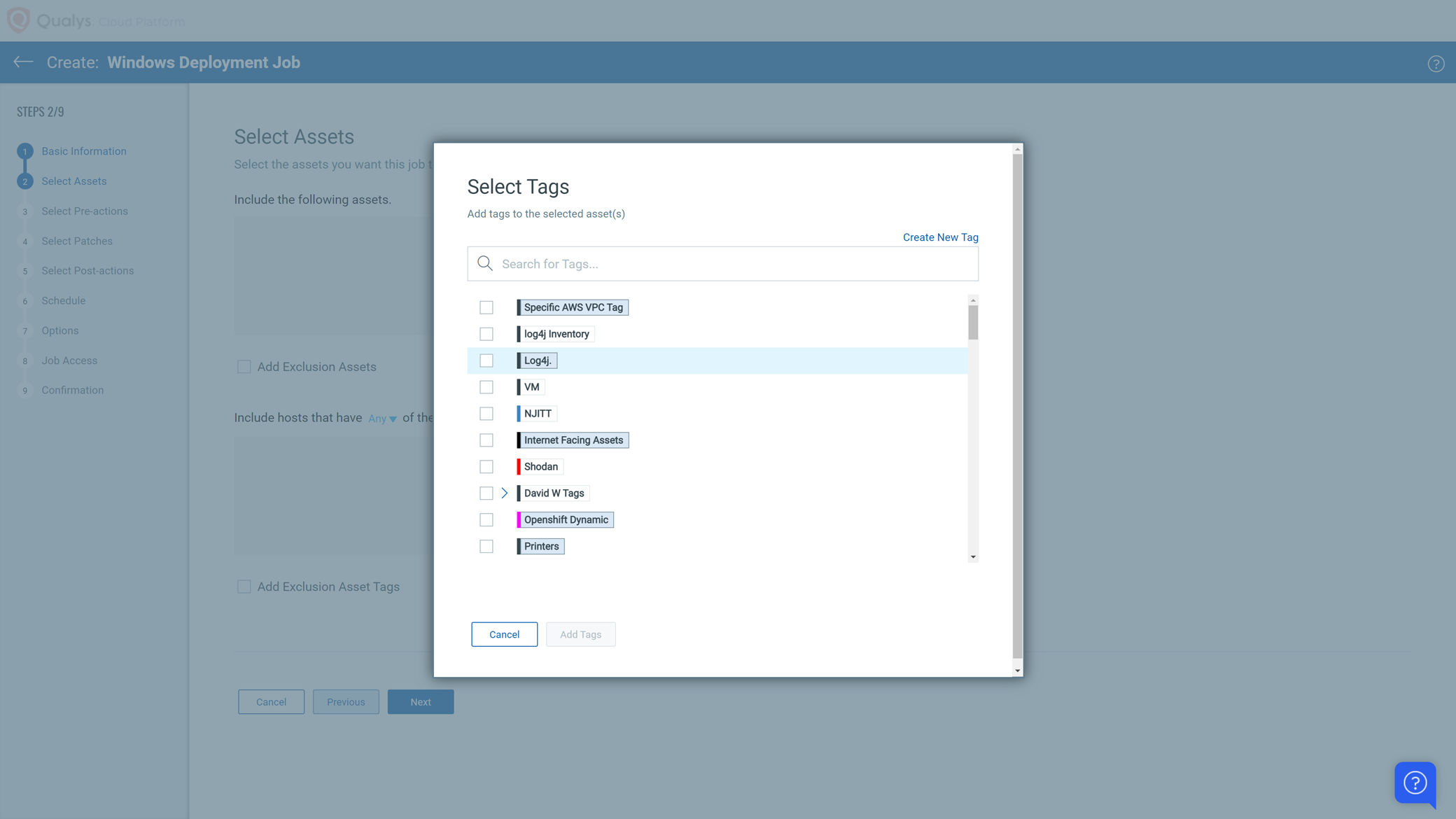
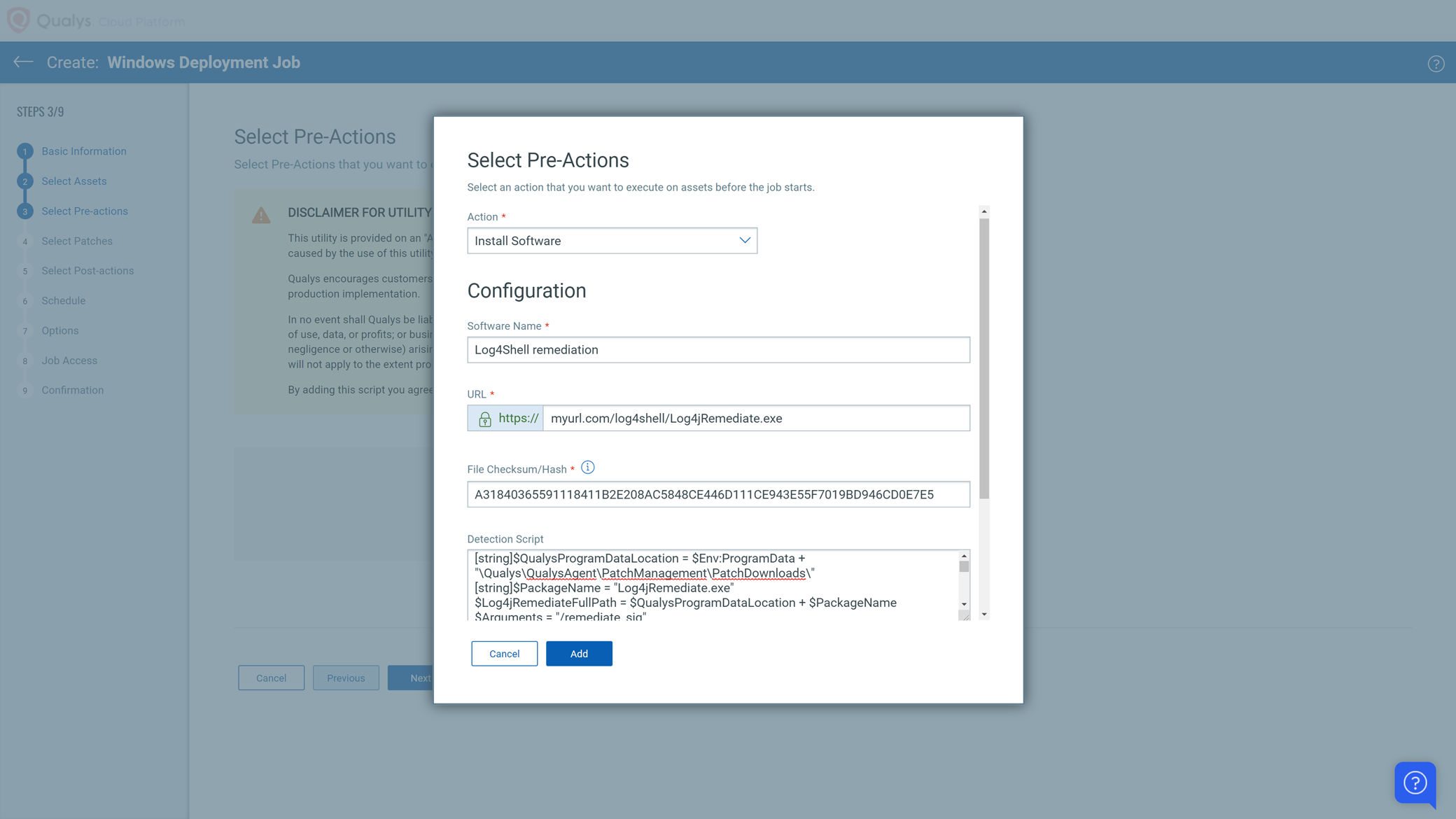
Step 3:
In the pre-action step, add a new Install Software action and configure it as follows:
Action: Install SoftwareSoftware Name: [Log4j_Remediation]URL: [http from where the log4j remediate exe is accessible to the agent]File Checksum/Hash: SHA256 of the file. E.g. A31840365591118411B2E208AC5848CE446D111CE943E55F7019BD946CD0E7E5
NOTE: The remediation tool in GitHub will get updated. Make sure to update the hash with every new version you use.Detection Script: [optional – you may leave empty]Install Script: [see example below]
Install script:
This PowerShell script is executed by the agent, then is used to run the remediation utility and report its results to the Qualys platform. This script can be customized based on the customer’s needs. Note: In case the Java application is running, it is best to use the script to stop the Java application before the remediation tool runs. The remediation tool may fail if the Java process prevents it from removing the JndiLookup class.
Here is an example of a script that can be used to run the remediation tool:
[string]$QualysProgramDataLocation = $Env:ProgramData + "\Qualys\QualysAgent\PatchManagement\PatchDownloads\" [string]$PackageName = "Log4jRemediate.exe" $Log4jRemediateFullPath = $QualysProgramDataLocation + $PackageName $Arguments = "/remediate_sig" function Start-Program { param ( [ValidateNotNullOrEmpty()] [string] $ProgramFullPath, [Parameter(Mandatory = $false)] [string] $Arguments ) try { $pinfo = New-Object System.Diagnostics.ProcessStartInfo $pinfo.FileName = $ProgramFullPath $pinfo.RedirectStandardError = $true $pinfo.RedirectStandardOutput = $true $pinfo.UseShellExecute = $false if ($null -ne $Arguments) { $pinfo.Arguments = $Arguments } $pinfo.WorkingDirectory = Get-Location $p = New-Object System.Diagnostics.Process $p.StartInfo = $pinfo $p.Start() | Out-Null $p.WaitForExit() if(Test-Path -Path "$Env:ProgramData\Qualys\remediation_status.out") { $content = (Get-Content -Path "$Env:ProgramData\Qualys\remediation_status.out" -Encoding utf8) -join "`n" Write-Host "Process Stdout:" Write-Host $content } else { Write-Host "Remediation status file not found" } Write-Host "Exit Code: "$p.ExitCode return $p.ExitCode } catch { Write-Host -ForegroundColor DarkRed "Failed to execute program" $_.Exception.Message return 1 } } if (Test-Path $Log4jRemediateFullPath) { Write-Host "Found $PackageName at "$Log4jRemediateFullPath } else { Write-Host "$PackageName does not exist at "$Log4jRemediateFullPath exit 1; } Write-Host "Launching $PackageName..." $ReturnCode = Start-Program $Log4jRemediateFullPath $Arguments if ($ReturnCode -eq 0) { Write-Host "$PackageName returned success." exit 0; } else { Write-Host "$PackageName returned failure. See output for more details." exit 1 }
Step 4:
Finish all the other steps required to create a new job and enable the job.
Use the Job tab and specifically the Job progress page to check on the progress and results of this job.
Note: There is no need to add patches to the job. Qualys Patch jobs can run actions without deploying patches from the same job.
For more information on Qualys Patch Management, please visit:
Patch Management Getting Started Guide | Patch Management Online Help