The Unbearable Lightness of Unaudited Supply Chains

An acute need expressed by a majority of CISOs at a roundtable in Italy sparks an idea to use one of our lesser-known compliance apps to manage supply chain security assurance efforts.
In the 1984 novel The Unbearable Lightness of Being, author Milan Kundera ponders the fleeting nature of man’s existence. Such is the nature of today’s supply chains, where processes with suppliers are often inconsistent, technologies divergent, and security workflows hard to standardize.
A while back, Qualys moderated a roundtable of ten CISOs from large enterprises in Italy. The purpose of the day was for us to hear their opinions and learn from their experiences. The discussion kicked off with giving them some food for thought: what did the group think about the clash between the drive for digital transformation and weathering the global pandemic?
While the conversation between the CISOs started with this predicable topic, it rapidly diverted to what the group really wanted to discuss, a topic we hadn’t expected.
The result was a heated exchange about the risks posed by today’s broken supply chains… and the need to audit them. Every single one of the executives expressed how hard it was to sustain, orchestrate, or standardize supply chains these days. They lamented about the need to apply a repeatable, consistent process to assure the level of security awareness reached by their suppliers.
These CISOs were on to something. The strategic importance of tackling broken supply chains is hitting every sector of the global economy as the world struggles to emerge from the Covid-19 pandemic. What is ailing our physical supply chains has now infected our digital ones.
When it comes to fending off hacks and attacks, many digital supply chains are flying blind. Too many suppliers fail to understand or appreciate that how they provide goods and services might be negatively impacting the security posture of the customer’s organization.

The cybersecurity leaders in the group didn’t even discuss technology as the solution to this problem. They were simply expressing a clear need to apply and sustain a process, a workflow more specifically, for supply chain security assurance.
When the roundtable ended, we thanked the CISOs for their time and for a meaningful exchange. But the next day, as thoughts drifted back to the discussion, their need for supply chain auditing stuck. We started thinking about how technology might help this effort to implement continual audit workflows, the possible future without it, and what happens if we don’t act now.
The Lightbulb Moment on the Security Supply Chain Problem
Auditing the supply chain has become more challenging today due to increased attention from attackers. The technology solutions proposed to this point have too often been cumbersome, prone to errors, and based on multiple information formats. This has rendered audit results that are not standardized and difficult to consume quickly.
We wonder:
- Could Qualys provide a solution to this tedious but worrying issue?
- Could there be some synergy between the data we gather and analyze and the workflows the CISOs were demanding?
- How could our cloud platform help fix the problem in some simple but tangible ways?
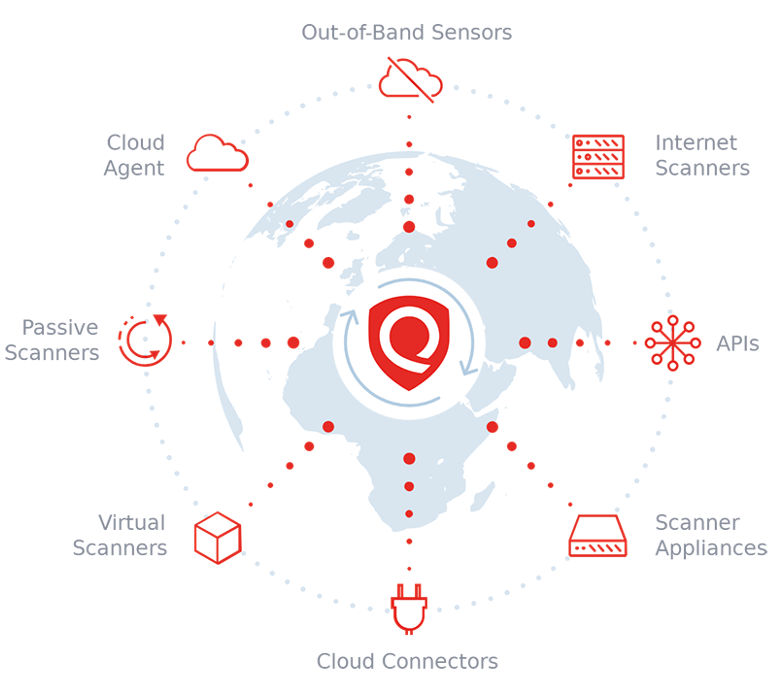
First, a bit of background on the data that Qualys analyzes. One of our core competencies is the collection of accurate metadata from the field with multiple, specialized sensors. This metadata is streamed to the cloud, where it gets normalized, indexed, enriched in context, and then consumed by multiple integrated applications to support myriad security and compliance processes.
A lightbulb turned on as we thought of Qualys’ “best kept secret”! That’s what many of our existing customers call our Security Assessment Questionnaire, or SAQ. It’s one of two dozen apps that run against Qualys Cloud Platform, and let’s just say it doesn’t get too much press.
The Case for Qualys Security Assessment Questionnaire (SAQ) for Supply Chain Auditing
Created to respond to a specific compliance use case, this app delivers the ability to orchestrate the non-technical part of a compliance workflow. For example, the need to assess third party suppliers within a GDPR Data Privacy framework. It is essentially a campaign manager application, leveraging the cloud to manage Q&A flow between a requester and a responder.
SAQ could also be used to validate the security posture of a supplier within your supply chain. Its Vendor Risk Assessment feature helps with the following:
- Onboards your vendors
- Stores vendor related documents such as contracts, SLA documents, and NDAs
- Supports vendor auto-categorization
- Assigns vendor single point of contact
- Tracks assessments per vendor
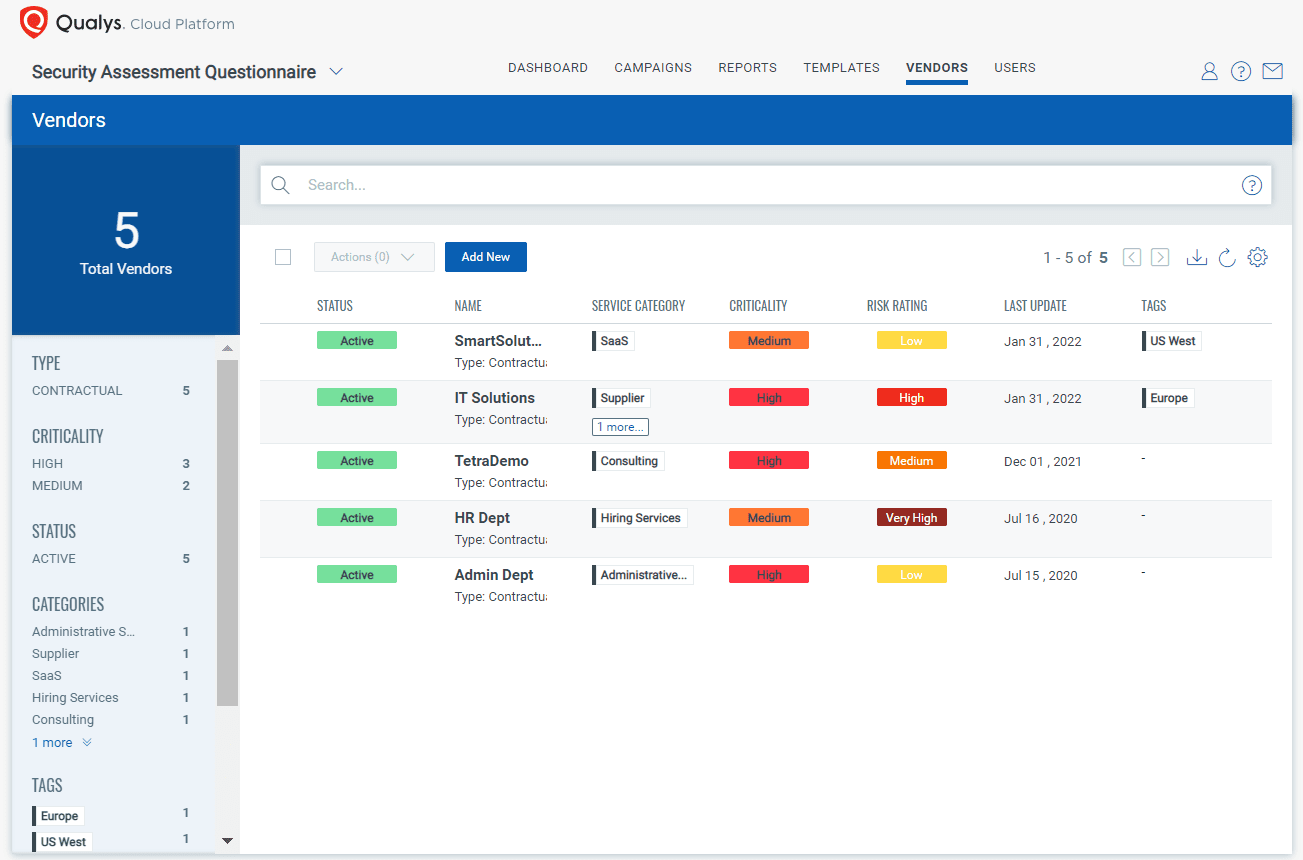
Vendor based assessment tracking helps you get a quick overview of any vendor’s assessment risk rating as well as trends over time. You can see all questionnaires addressed by a specific vendor and how their risk posture is changing over the period. Is the vendor improving over the period or moving to a higher risk rating worthy of concern?
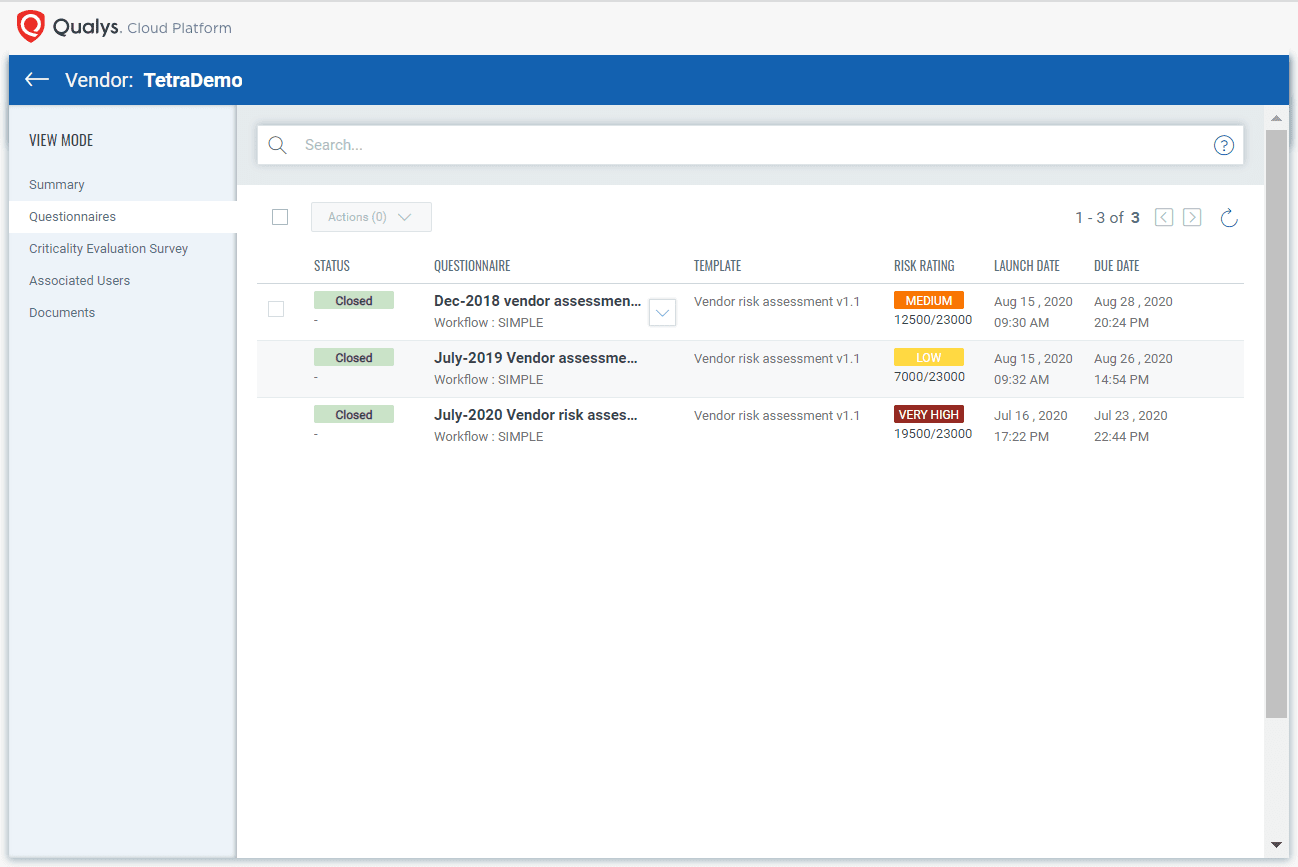
Even better, SAQ can provide an audit trail. The app can handle documentation attachments, assign a score to each answer, freely define fields and information types in a security audit, set deadlines for answers, and more.
In the context of a security assurance or attestation effort, auditors can build results reports measuring if responses were received in time, or if the risk level of the supplier is above or below an acceptable threshold.
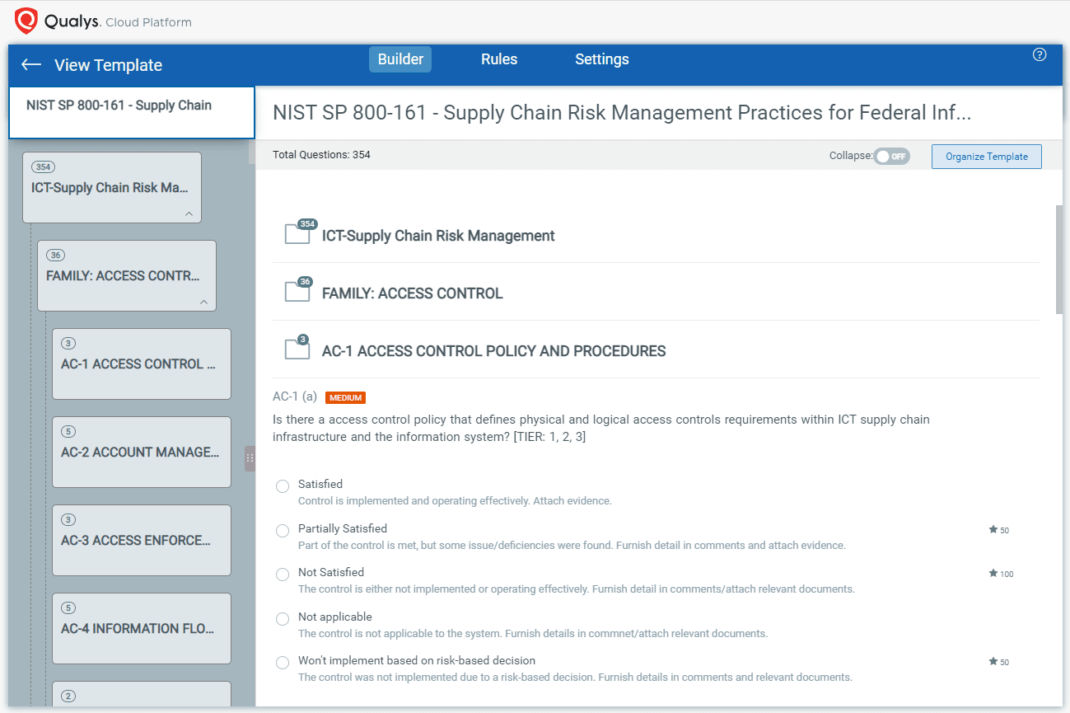
These combined functions could make Qualys SAQ a foundational technology to support a multi-lingual, effective, standardized, sustainable, and repeatable way to audit and assess your supply chain.
The good news is that Qualys SAQ already comes loaded with questions and templates that address well-known audit tasks such as GDPR Third Party Vendor Assessment, Payment Card Industry Data Security Standard (PCI-DSS), NIST Cyber Security Framework, and more. However, it’s easy enough to build your own with your own questions, your own scoring, and your own language.
A meaningful dashboard in SAQ will enable instant situational awareness about your running and completed supply chain security audit efforts. This would be kept consistently within Qualys Cloud Platform right next to your other security and compliance data. This will keep audit results efficiently organized, ready to access when needed, and ready to democratize across the various supply chain stakeholders who need them.
Conclusion
Fixing today’s broken supply chains can’t wait. As government and industry work to unravel the knotted supply chains at the world’s trade ports, we in cybersecurity should take the opportunity to improve the security of digital supply chains as well. Here is a solution to orchestrate a repeatable, consistent process for supplier security assurance.
By offering Qualys SAQ to the CISOs at our roundtable, Qualys could tangibly contribute to smoother operational efficiency by bringing effectiveness, consistency, and velocity to supply chain auditing. SAQ represents a solution that can be rapidly implemented, efficiently orchestrated, and securely stored. It truly is one of the most important workflows to keep your entire organization’s security posture intact. For a secure, audited, and efficient supply chain – consider using Security Assessment Questionnaire from Qualys.
Visit product page for more information: https://www.qualys.com/apps/security-assessment-questionnaire/
Start your free trial now https://www.qualys.com/free-trial/#/saq