Transitioning to a Risk-based Approach to Cybersecurity
Last updated on: December 12, 2022
For today’s CISOs, managing cyber risk is Job #1, and it’s a full-time concern. This was communicated loud and clear when Qualys recently hosted several CISOs and cybersecurity executives from our global enterprise customer base at our Strategic Advisory Board meeting in London. Their teams are spending an inordinate amount of time managing cybersecurity threats… and it is only getting harder. Despite differences in size, geography and industry, they all struggle with similar challenges. Most often we hear:
“Teams have limited visibility.” What isn’t seen, can’t be managed. Studies show large organizations are unaware of more than half of all devices on the enterprise network (e.g., unregistered public IP addresses), which widens the potential attack surface while defying even the most effective cybersecurity program.
“We’re swamped by tools and data.” According to Gartner’s 2020 CISO Effectiveness Survey, the average enterprise has more than 16 security tools, with 12% of CISOs reporting 46 or more. What’s often missing is actionable insights, leaving critical gaps in coverage, lack of alignment, and challenges in prioritizing response and remediation across security, compliance, and IT teams.
“Manual processes can’t keep up.” IT infrastructure is increasingly heterogeneous and ephemeral – from on-premises to virtual to serverless, public cloud to private to hybrid, IT to OT to IoT. The task of managing cybersecurity is worsened by the continuing IT skills gap, which makes hiring and retaining seasoned teams that much more difficult. IT complexity is compounded by lack of cybersecurity automation, poor cross-team collaboration, and a need for workflow coordination.
Yet in the face of these obstacles, CIOs and CISOs are increasingly being tasked with tracking and reporting on cyber risk to the board as part of the company’s wider enterprise risk management practices. Why this sudden focus on cyber risk by CEOs and executive teams?
Cyber Risk is a Board-level Concern
Corporate boards can be very news-driven, growing more concerned with each report of cyber warfare in Europe and ransomware attacks at home. Cybersecurity risk is now a regular topic in the boardroom. More than 50% of quarterly board agendas now include the CISO, according to ESG. Reducing cyber risk is important as the cost of a successful cyberattack soars. The average cost of a data breach rose during 2021 from $3.86M to $4.24M – the highest increase per annum in the 17-year history of IBM’s reporting.
It’s not just corporate directors and executives who are watching the news. Wall Street shareholders are also concerned about cyber risk and want to know what the corporations in their portfolios are doing about it. Rising mentions of “cybersecurity” in public earnings transcripts now average 800 per quarter, according to GlobalData. In March 2022, the U.S. Securities and Exchange Commission proposed a new rule requiring a uniform methodology for publicly disclosing cybersecurity risk. Board members now ask pointed questions of CISOs about the company’s cybersecurity spend, success benchmarks, and business continuity plans in the face of a cyber attack.
What this means for every cybersecurity leader is that there’s a new requirement to simplify how they discuss cyber risk with company management, the board, shareholders, customers, partners, and the wider market. According to ESG, it’s time to abolish ‘techno-speak’ and clearly define cyber risk in terms of bottom-line business risk.
For many, this will require a shift. To do so requires adopting a risk-based approach to managing cybersecurity.
Taking a Risk-based Approach to Cybersecurity
Cybersecurity entails mitigating different categories of risk. There are risks posed by standalone software applications, some of which may be out-of-date, end-of-support, or custom-built. There are risks posed by integrated technologies that may be managed by third parties or part of a wider supply chain. Other risks may affect physical or virtual infrastructure such as endpoints, servers, network devices, clouds, and containers. Humans also pose many risks, as a company’s workforce may fall prey to malicious actors exploiting human error.
As CISOs are in the hot seat for reducing cyber risk, they must adopt risk-based methodologies that allow cybersecurity technologies, processes, and people to converge and collaborate. These risk-based methodologies may be prescribed by industry mandates, government regulations, and financial audit standards. They must simultaneously achieve strengthened cyber defenses while maintaining continuous compliance. Finally, they must report their success to executives and the board in clear metrics that prove the success of security controls against internal objectives as well as industry peer benchmarks.
Easier said than done? To adopt a risk-based approach to cybersecurity, Qualys suggests a three-step cycle that continuously monitors the threat landscape, enables quick response, and measures the metrics that company leadership cares about.
- Assess risk by gaining visibility and control over all IT assets in the organization’s environment. Effective attack surface management starts with a foundation of thorough threat assessment. Organizations need a reliable way to quantify their true cybersecurity risk, making it easier to prioritize threats.
- Reduce risk by consolidating siloed security tools into a unified platform with automation capabilities for risk monitoring, detection, and remediation. Actionable steps to reduce risk should be assigned across security, IT or compliance teams in their system(s) of choice.
- Report risk via automated dashboards with clear, risk-defined metrics against industry standards, peer benchmarks, and best practices. Modern techniques break with security reporting of the past by tracking metrics customized to an organization’s unique cyber risk exposure to specific threats.
Free Trial
Qualys VMDR: Get Started wth a 30-day Free trial
Don’t Count Vulnerabilities, Count Risks
With this shift to a risk-based approach to cybersecurity, counting raw vulnerabilities simply doesn’t work anymore.
On the surface, counting vulnerabilities still seems important. The total number of reported vulnerabilities has exploded in recent years. The 1990s clocked 2,594 vulnerabilities in total, which rose 796% to 37,231 in the 2000s, and since 2010 another 135,284 have been discovered (source: Qualys). A cumulative growth rate in vulnerabilities of 5,116% over the years seems startling. But by assessing cyber risk in terms of business risk, these astronomical numbers can be put into perspective.
To illustrate, out of the universe of 185,446 known vulnerabilities, only 29% have exploits available. Just 2% have weaponized exploit code. And considering the range of malware currently in the wild, a mere 0.4% – 718 vulnerabilities – have been exploited by malware. Threat actors are actively leveraging only 0.16% of the universe of known vulnerabilities. Finally, even fewer vulnerabilities end up branded with their own name. Those show up on the front page of major newspapers, e.g., Log4Shell, Heartbleed.
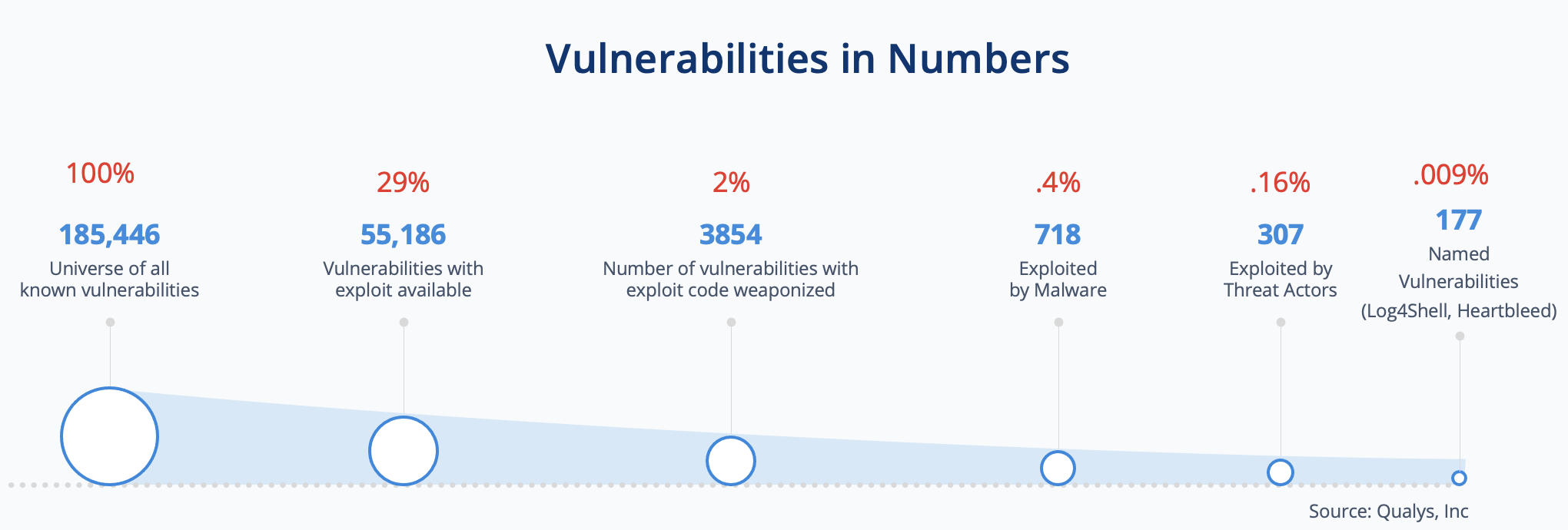
Most security teams don’t have visibility into this simple fact, so vulnerability management objectives are prioritized based on CVSS scores alone. This results in wasted effort often patching vulnerabilities that may or may not actually reduce risk.
To be a true risk to your enterprise, a specific vulnerability must have material applicability in your specific environment. For example, a high severity vulnerability may not be as much of a concern should your enterprise have compensating controls to mitigate the risk posed. Clearly, controlling cybersecurity risk is much more achievable by focusing security and IT teams like a laser beam on the vulnerabilities that matter most to your company’s exposure. It’s the essence of a risk-based approach to security.
The Future of Qualys VMDR
Twenty years ago, Qualys practically invented cloud-native Vulnerability Management software. As a market leader for more than two decades, we have continued to evolve our approach.
Two years ago, we introduced VMDR 1.0 to provide asset inventory, vulnerability management, prioritization, available patch information, and threat detection in a single solution. In the process, we changed how vulnerability management programs were scaled across the enterprise. Now we’re gearing up to do it again.
We’ve announced the next generation of Qualys VMDR, which we are calling VMDR 2.0 with Qualys TruRiskTM.
We listened when CISOs told us their needs and have evolved our flagship cloud service to support this risk-based approach to cybersecurity. It provides a framework to drive cyber risk reduction with automation, evaluate cybersecurity program effectiveness, and then communicate clearly to the Board.
Yeah!!
Thank you for sharing such a great blog of cyber security.
How to check current VMDR version?
You are giving a very depth in article it’s very usefully this article is very helpful for those people who has threats of cyber attack & frauds. this article is providing great ideas to avoid cyber attacks.