Qualys Survey of Top 10 Exploited Vulnerabilities in 2023
The Qualys Threat Research Unit (TRU) has thoroughly analyzed vulnerabilities reported in 2023. Our comprehensive study assesses factors including weaponization status, existence in the CISA KEV, instances or usage of malware and ransomware, trending vulnerabilities, various scoring metrics, and recency of threats. Insights for the Top 10 vulnerabilities during 2023 are also based on evidence of exploitation, patch adoption rates, and the longevity of vulnerabilities.
7 Key Insights by the Qualys Threat Research Unit
- Exploits are, on average, emerging before the official disclosure of vulnerabilities, which signals the presence of zero-day exploits.
- MITRE ATT&CK techniques T1210 (Exploitation of Remote Services) and T1190 (Exploit Public-Facing Application) are the predominant techniques leveraged by Top 10 vulnerabilities, reinforcing the need for an accurate inventory of external assets and quick remediation of their vulnerabilities.
- Identified threat actors for the analyzed vulnerabilities include Fancy Bear, Graceful Spider, FIN11, North Korea Attribution, LABYRINTH CHOLLIMA, Russia Attribution, Iran Attribution, Static Kitten, Charming Kitten, UNC4841, and China Attribution.
- Evidence suggests state-sponsored attributions in sophisticated cyber-attacks with geopolitical motives, requiring firms to strengthen defenses against Advanced Persistent Threats (APTs) by nation-states.
- Many of the Top 10 vulnerabilities in 2023 lack attribution to known threat entities, pointing to potential new or covert cyber actors; this stresses the importance of proactive monitoring to detect, track, and counter these developing risks.
- CVE-2023-29059 (3CX Desktop) and CVE-2023-34362 (MOVEit) received the most effective responses and fastest remediation.
- CVE-2023-0669 (Fortra GoAnywhere) and CVE-2023-22952 (SugarCRM RCE) had the least effective responses and the slowest remediation.
A Closer Look at the Top 10 Exploited Vulnerabilities
of 2023
| Rank | CVE ID | Vulnerability Description | Qualys Detection Score (QDS) | Qualys ID (QID) |
| 10 | CVE-2023-22952 | SugarCRM Remote Code Execution (RCE) Vulnerability | 95 | 730704 |
| 9 | CVE-2023-20887 | VMware Aria Operations for Networks Command Injection | 95 | 730825 |
| 8 | CVE-2023-2868 | Barracuda Email Security Gateway Vulnerability | 95 | 150701 |
| 7 | CVE-2023-28252 | Windows Common Log File System Driver Elevation of Privilege | 95 | 92003, 92005 |
| 6 | CVE-2023-29059 | 3CX Desktop Client Supply Chain Vulnerability | 95 | 378327 |
| 5 | CVE-2023-34362 | MOVEit Transfer Injection Vulnerability | 100 | 378543 |
| 4 | CVE-2023-23397 | Microsoft Outlook Elevation of Privilege Vulnerability | 95 | 110428 |
| 3 | CVE-2023-0669 | Fortra GoAnywhere Managed File Transfer (MFT) RCE | 95 | 730720 |
| 2 | CVE-2023-24880 | Windows SmartScreen Security Feature Bypass | 95 | 91990 |
| 1 | CVE-2023-27350 | PaperCut NG/MF Multiple Security Vulnerabilities | 100 | 730790 |
Before diving deeper into the specifics of each vulnerability, it is crucial to note three key considerations. First, data analyzed by TRU is meticulously anonymized, ensuring that any subsequent analysis cannot be traced back to specific organizations or assets. Second, the sequence in which these vulnerabilities are presented aligns with their Top 10 rank, according to Qualys.
Finally, a vulnerability is deemed “trending” when there is corroborated evidence of its exploitation in the wild or mentions of it on the dark web. This assessment is based on data aggregated from one or more of the 25+ threat intelligence sources used by Qualys TruRisk.
In our effort to evaluate these Top 10 vulnerabilities in 2023, multiple metrics were considered, such as evidence of exploitation, patch rate, vulnerability age, and MTTR (Mean Time to Respond/Remediate).
Let us delve into the vulnerabilities that have defined the
cyber challenges of 2023.
10. CVE-2023-22952: SugarCRM Remote Code Execution (RCE) Vulnerability
Vulnerability Snapshot
- Trending in 2023: Noted 15 times
- Threat Landscape: Exploited by one threat actor; trending date in the wild as recently as August 30, 2023
- Qualys Detection Score (QDS): 95
- Qualys ID: Vulnerability Detection (QID): 730704
The SugarCRM vulnerability (CVE-2023-22952) is a critical focal point in the evolving landscape of cyber threats. It carries a Qualys Detection Score (QDS) of 95 and a CVSS score of 8.8. Marking a significant escalation in potential damages, this zero-day authentication bypass and remote code execution flaw allows malicious actors to inject malicious PHP code through a CRM platform module and amplifies the repercussions of an attack if the system is not securely configured.
An extensive pool of sensitive data stored in SugarCRM databases allows threat actors to escalate the intrusion to AWS environments by using misconfigurations to broaden their illicit access. Our data reveals an average vulnerability age of roughly 108 days and an MTTR of about 25 days; this indicates a fast response. However, the current patch rate of 36% signifies that many systems are still exposed, underscoring the need for better security measures and patch applications.
9. CVE-2023-20887: VMware Aria Operations for Networks Command Injection Vulnerability
Vulnerability Snapshot
- Trending in 2023: Noted 38 times
- Threat Landscape: Exploited by one threat actor; trending date in the wild as recently as September 21, 2023
- Qualys Detection Score (QDS): 95
- Qualys ID: Vulnerability Detection (QID): 730825
The critical vulnerability marked CVE-2023-20887 in VMware’s Aria Operations for Networks is a significant tool for orchestrating network infrastructure and is a stark reminder of the persistent threat landscape surrounding network security.
Earning a QDS of 95 and a critical severity score of 9.8 on the CVSS scale, the flaw facilitates a command injection opportunity. It allows an unauthorized entity equipped with network access to remotely execute code with administrative privileges and seize substantial control of the affected system.
8. CVE-2023-2868 – Barracuda Email Security Gateway Vulnerability
Vulnerability Snapshot
- Trending in 2023: Noted 48 times
- Threat Landscape: Exploited by two threat actors; trending date in the wild as September 21, 2023
- Qualys Detection Score (QDS): 95
The Barracuda Email Security Gateway (ESG) faces a critical remote command injection flaw tagged as CVE-2023-2868. This vulnerability is found in the parsing logic for processing TAR files; it permits unsanitized user inputs to be executed as a system command, which grants attackers the ability to remotely manipulate system commands with significant privileges.
This flaw has been exploited globally by highly skilled actors, giving them potential capacities to intercept and alter emails, inject malware or phishing links, and compromise the overall security and integrity of organizational communications.
The CVE has elicited a rare and stern response from Barracuda Networks, urging customers not merely to patch their systems but to completely replace the affected devices to prevent persistent backdoor access — highlighting the severe risk posed to email security infrastructures worldwide.
7. CVE-2023-28252 – Windows Common Log File System Driver Elevation of Privilege Vulnerability
Vulnerability Snapshot
- Trending in 2023: Noted 62 times
- Threat Landscape: Exploited by one malware and one threat actor, trending in the wild as of September 22, 2023
- Qualys Detection Score (QDS): 95
- Qualys IDs: Vulnerability Detection (QID): 92003, 92005
The Windows Common Log File System (CLFS) driver vulnerability (CVE-2023-28252) presents a critical risk with a QDS score of 95 and a high CVSS score of 7.8. The affected CLFS driver is a pivotal logging subsystem initiated in Windows 2003 R2.
The CVE allows the transformation of the subsystem into a gateway for attackers to acquire supreme system-level privileges, amplifying the prospects of severe damage. This vulnerability has been weaponized to distribute exploitative ransomware associated with a major malware strain known for multiple breaches.
Rapid and expansive exploitation of this flaw has affected organizations of all sizes around the world. Our analysis found an average vulnerability age of 68 days and an MTTR of 13 days, which emphasizes the need to accelerate the patch rate (currently at 81%) to swiftly mitigate this vulnerability.
6. CVE-2023-29059 – 3CX Desktop Client Supply Chain Vulnerability
Vulnerability Snapshot
- Trending in 2023: Noted 13 times
- Threat Landscape: Exploited by three threat actors and recently trended in the wild on September 24, 2023
- Qualys Detection Score (QDS): 95
- Qualys ID: Vulnerability Detection (QID): 378327
A set of critical supply chain vulnerabilities in the widely used 3CX VOIP desktop client tool used by more than 600,000 customers globally was identified as CVE-2023-29059; it has a QDS score of 95 and a CVSS score of 7.8.
In several attacks, this sophisticated breach was a multi-stage incursion where hackers Trojanized a legitimate version of the 3CX desktop app, embedding malicious code into the MSI installer accessible on the official website or as an update to existing installations.
This tactic enabled the compromise of both Windows and macOS platforms to allow the harvesting of extensive system details and siphoning of stored credentials from various browsers. This vulnerability has an average age of 78 days, which suggests a prolonged exposure period before remediation actions occur. However, the speedy MTTR of about seven days and a high patch rate of 90% reflect proactive measures taken by many entities to secure their systems.
5. CVE-2023-34362 – MOVEit Transfer Injection Vulnerability
Vulnerability Snapshot
- Trending in 2023: Noted 44 times
- Threat Landscape: Exploited by one malware, three threat actors, and one ransomware; trended in the wild as recently as September 22, 2023
- Qualys Detection Score (QDS): 100
- Qualys ID: Vulnerability Detection (QID): 378543
The CVE-2023-34362 represents a severe vulnerability in MOVEit Transfer, a well-known file transfer solution by Progress Software Corporation, with an alarming QDS score of 100 and a CVSS score of 9.8. This vulnerability paves the way for SQL injection attacks where attackers can inject malicious data into databases to execute arbitrary code and precipitate widespread disruptions.
The associated hackers, linked to a notorious ransomware gang, have extracted substantial amounts of files from compromised MOVEit systems. Our analysis indicates a swift MTTR at seven days and a vulnerability age averaging 56 days. Still, with a patch rate of just over 51%, brisk action is vital to prevent further exploitation.
4. CVE-2023-23397 – Microsoft Outlook Elevation of Privilege Vulnerability
Vulnerability Snapshot
- Trending in 2023: Noted 84 times
- Threat Landscape: Exploited by four threat actors; trended in the wild as recently as September 23, 2023
- Qualys Detection Score (QDS): 95
- Qualys ID: Vulnerability Detection (QID): 110428
The CVE-2023-23397 is a notable elevation of privilege vulnerability in all supported versions of the Microsoft Outlook email client for Windows. This flaw allows attackers to bypass authentication measures, facilitating unauthorized access to confidential data and enabling user impersonation within organizations.
The exploit requires zero user interaction — attackers can initiate it simply by sending an email that activates the vulnerability upon processing by Outlook, which bypasses preventative measures such as the Preview Pane. Our analysis reveals the vulnerability’s age averaging approximately 89 days and an MTTR of about ten days, with a promising patch rate of roughly 87.5%.
3. CVE-2023-0669 – Fortra GoAnywhere Managed File Transfer (MFT) Remote Code Execution (RCE) Vulnerability
Vulnerability Snapshot
- Trending in 2023: Observed 76 times
- Current Threat Landscape: Exploited by one malware, three threat actors, and one ransomware; recently trended in the wild as of September 24, 2023
- Qualys Detection Score (QDS): 95
- Qualys ID: Vulnerability Detection (QID): 730720
CVE-2023-0669 presents a significant threat to organizations using Fortra’s GoAnywhere Managed File Transfer (MFT) tool, a platform centralizing control over internal and external file transfers. This command injection flaw allows attackers with public internet access to the tool’s administrative console to execute remote code on unpatched versions, potentially leading to extensive data breaches and financial extortion. The data show this vulnerability was present for about 89 days before initiation of mitigation steps.
The MTTR is roughly 31 days, demonstrating the average time taken to address the vulnerability after detection. However, with a patch rate of only 33%, a substantial portion of systems remain unprotected. Therefore, organizations must accelerate mitigation plans for this CVE to secure their data and uphold system integrity.
2. CVE-2023-24880 – Windows SmartScreen Security Feature Bypass Vulnerability
Vulnerability Snapshot
- Trending in 2023: Noted 21 times
- Threat Landscape: Exploited by two malware and two ransomware(s); trending in the wild as of September 5, 2023
- Qualys Detection Score (QDS): 95
- Qualys ID: Vulnerability Detection (QID): 91990
The Windows SmartScreen security feature, a vital defense mechanism for protecting users from malicious software and phishing sites, has been severely compromised by CVE-2023-24880. This flaw enables attackers to bypass the Mark of the Web (MOTW) defenses integral to SmartScreen and Microsoft Office’s Protected View, making it easier to spread malware through crafted malicious files that evade essential security checks and distribute malware more freely across systems.
While the vulnerability has a relatively low CVSS severity rating of 4.4, its Qualys Detection Score (QDS) stands notably at 95. Organizations are strongly urged not to overlook this vulnerability. Recent data on the Windows SmartScreen vulnerability indicates an average vulnerability age of approximately 85 days, a swift MTTR of about 13 days, and a patch rate nearing 80%.
1. CVE-2023-27350 – PaperCut NG/MF Multiple Security Vulnerabilities
Vulnerability Snapshot
- Trending in 2023: Noted 81 times
- Threat Landscape: Exploited by four malware(s), four threat actors, and four ransomware(s); trending in the wild as of September 19, 2023
- Qualys Detection Score (QDS): 100
- Qualys ID: Vulnerability Detection (QID): 730790
The No.1 vulnerability for 2023 is CVE-2023-27350 — the most significant threat of the year.
This CVE has a high QDS of 100 and a severity score of 9.8. It affects the popular print management software PaperCut and poses an urgent and significant threat to network security across many organizations.
Originating from inadequate access control measures within the SetupCompleted Java class, the CVE allows malicious actors to bypass authentication procedures and execute arbitrary codes with heightened privileges on targeted systems. Incidents using this vulnerability have deployed ransomware. Given its capacity to compromise the integrity of entire networks, the need for immediate action is paramount.
The data on CVE-2023-27350 indicates an average vulnerability age of 97 days and an MTTR of about 23 days. The patch rate is approximately 59%, highlighting the urgent need for faster patching to mitigate potential exploits.
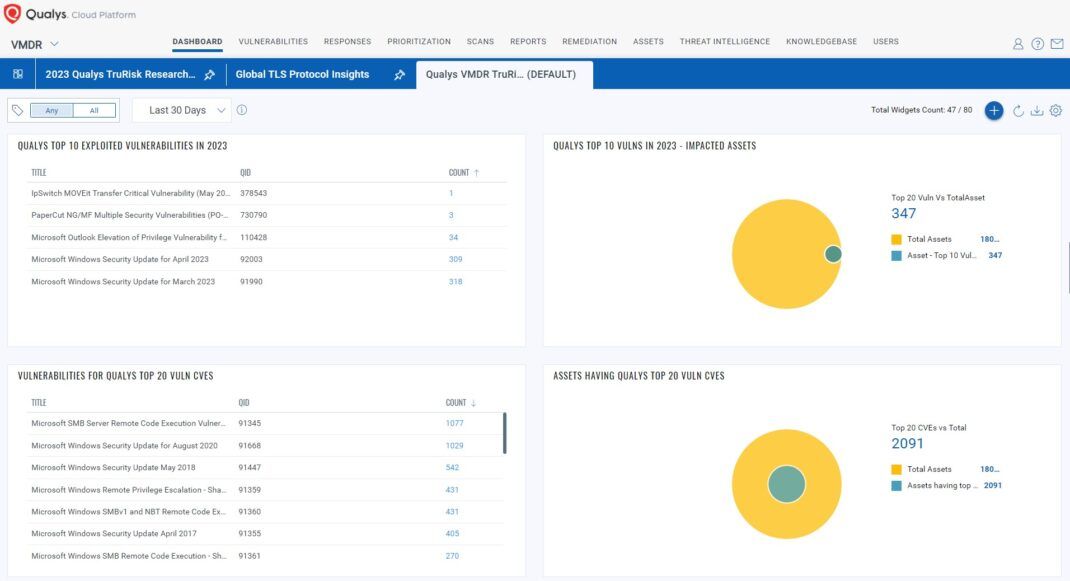
Optimizing Risk Management with Qualys VMDR TruRisk Dashboard
The Qualys VMDR helps organizations get instant visibility into high-risk and top-ten vulnerabilities.
The Qualys VMDR TruRisk Dashboard provides organizations with comprehensive visibility into open vulnerabilities, emphasizing the organization’s global risk score and high-risk vulnerabilities. After pinpointing vulnerable assets associated with the top ten CVEs, you can employ Qualys Patch Management to mitigate the risk swiftly.
The TruRisk VMDR Dashboard is available – Download the Dashboard Here
Next Steps: Reduce Your Risk to the Top 10 Vulnerabilities with Qualys VMDR
As cyber-attacks continue to escalate, it is crucial for organizations to prioritize vulnerabilities based on their associated risks. Qualys VMDR systematically elevates the priority of vulnerabilities that either show evidence of exploitation or have a high likelihood of being exploited.
Qualys advises security teams to follow this shortlist of recommendations for remediating Top 10 vulnerabilities:
- Prioritize the remediation process. Focus first on vulnerabilities with a score of 95 or higher, followed by those scoring above 90, and finally, those with a score of 70 or above.
- Use automated remediation to reduce risk. Automatically deploy patches for applications, e.g., client-side applications that have low or minimal impact.
- Maintain accurate inventory of externally facing assets. Keep a vigilant eye on vulnerabilities affecting these assets and remediate critical issues as swiftly as possible.
If you are not a Qualys VMDR user, we invite you to try it in your own environment. Click the link to see how Qualys can help you quickly detect and eliminate the Top 10 vulnerabilities:
Get the Free Trial
Sign Up for a Free Trial and See your TruRisk
Additional Contributors:
- Ramesh Ramachandran, Principal Product Manager, VMDR, Qualys
- Shreya Salvi, Data Scientist, Qualys