Mitigating Risk with Custom First-Party Software and Application Components: A CISOs’ Guide

What is First-Party Software Anyway?
First-party software, unlike off-the-shelf ‘Third-Party’ software, is custom open-source software (OSS) and applications created by organizations to stitch together existing software to meet custom business needs. Nearly every company today uses some form of first-party software, making it ubiquitous and, therefore, a major blind spot for Chief Information Security Officers (CISOs).
The Catch-22 with First-Party Software
In today’s digital landscape, custom ‘first-party’ OSS and embedded components have become integral to the functioning of organizations across various industries. While these bespoke solutions offer tailored functionality for the companies that use them, they also present a unique set of risks that off-the-shelf third-party applications do not.
Let’s explore the risks associated with custom software and embedded application components and provide mitigation strategies that any CISO can deploy effectively.
First-Party Software Risks
- Vulnerability Exploitation: While the number of vulnerabilities increased 40% over the last 5 years for 3rd-party software, custom first-party OSS and embedded components are growing in popularity, which contain vulnerabilities that hackers can more easily exploit. These vulnerabilities could result from coding errors, outdated libraries, or misconfigurations. Such weaknesses, combined with the fact that conventional VM solutions cannot provide comprehensive coverage over custom applications, first-party software is a prime target.
- Lack of Patch Management: Since the top exploited vulnerabilities are not zero-day threats, it’s key that they are patched – everywhere. However, unlike third-party off-the-shelf software, first-party solutions often lack CVEs that allow users to patch vulnerabilities targeting them. This underlying shortcoming is the crux of what makes first-party applications risky, as this results in the inability to patch vulnerabilities promptly – if at all.

- Third-Party Dependencies: First-party software frequently relies on third-party libraries and components. If these dependencies have their vulnerabilities, they can introduce risks into your system. It’s not just your code you have to worry about; it’s the entire software ecosystem.
- Integration Challenges: When first-party software integrates with other systems or applications, it can create security gaps. Inadequate integration testing can lead to data leaks, privilege escalation, or unintended functionality.
- Insufficient Compensating Controls: First-party software may lack built-in security features present in commercial software. Without proper access controls, encryption, and auditing, sensitive data may be at risk.
- Runtime threats. Many organizations focus their application risk management efforts on the CI/CD pipeline, which enables them to detect and eliminate many vulnerabilities and insecure configurations in a proactive manner, before they make it to production. However, it’s also important for organizations to assess applications at run time. Cyber adversaries employ new attack tactics and techniques almost daily; applications that appeared to be perfectly safe when initially released to production may in fact harbor previously unknown vulnerabilities.
Mitigating the Risk of First-Party Software – A CISO Checklist
Thorough Risk Assessment and Prioritization: Begin by conducting a comprehensive security assessment of first-party software and embedded components with risk context. Identify vulnerabilities, misconfigurations, and potential threats through penetration testing, code reviews, and full perimeter vulnerability scanning.
Integrated Patch Management: Establishing a robust patch management process for custom solutions is half the battle. When it comes to obscure areas of your ecosystem, vulnerability management (VM) needs to work in concert with your patch management solution. This is easier said than done because vulnerability management is typically managed by security teams and patch management is typically managed by IT operations. This division results in efficiencies, potential friction, and missed details between identifying vulnerabilities and remediating them. The better VM and patch management work together, the faster and better first-party risks are addressed.
Integrated Custom Remediation: First-party applications introduce risks that are unique to your organization and often cannot be addressed by pre-built, off-the-shelf commercial solutions. In order to address risk in first-party applications, organizations need the ability to build custom logic to identify and remediate local risks by changing configurations, updating libraries, making registry changes, deleting files, shutting down processes, and more.
CMDB Dependency Management: Related to patch management and the division that exists between security and IT operations, maintaining an up-to-date inventory and CMDB of third-party dependencies is also critical. Make sure you regularly check for security advisories related to these components and assess their impact on your software. Replace or update vulnerable dependencies as necessary and look for ways that your VM program can provide data and automate the process wherever possible.
Secure Coding Practices: Implement secure coding practices during the development of first-party software. Enforce coding standards, conduct code reviews, and train your development team on security best practices to reduce the likelihood of introducing vulnerabilities.
Integration Testing: Prioritize thorough integration testing to identify security weaknesses at the interface between custom and third-party systems. Test for data leaks, privilege escalation, and unexpected behavior.
Access Control and Encryption: Implement strong access controls to restrict user privileges appropriately. Encrypt sensitive data both in transit and at rest. Ensure proper authentication and authorization mechanisms are in place.
Monitoring and Incident Response: Implement continuous monitoring to detect unusual activities or security breaches. Develop an incident response plan to address security incidents promptly and effectively.
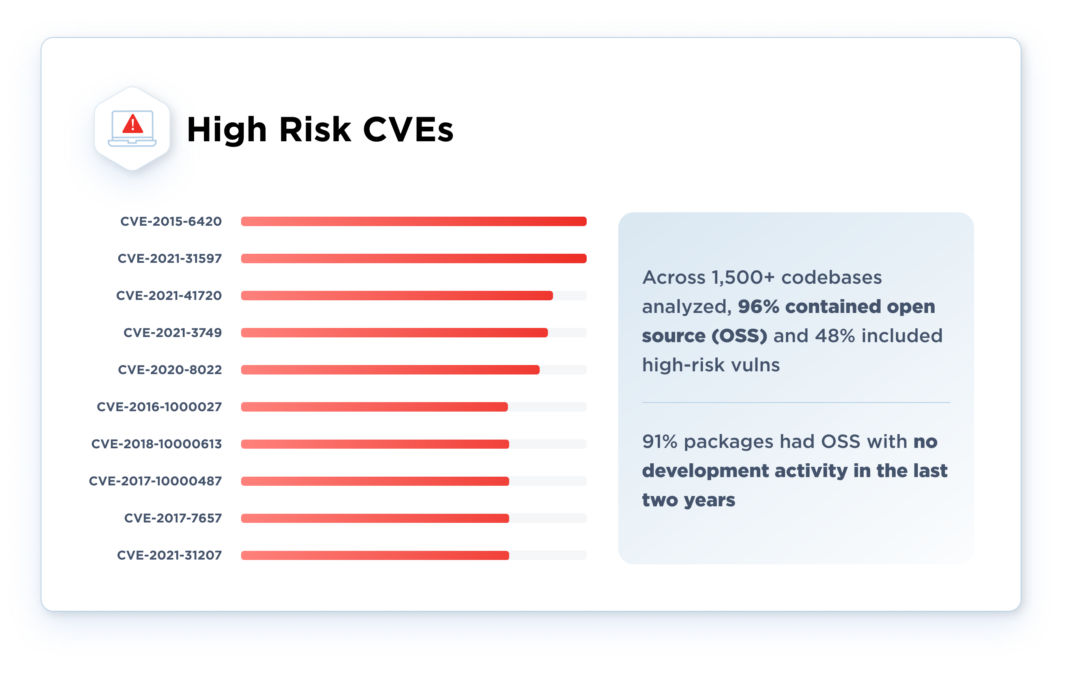
Software Supply Chain Risk Management: When you consider that 96% of codebases include OSS, of which 48% of OSS include high-risk vulnerabilities, first-party is most likely a security weak point for most CISOs. In addition, 91% of OSS show no development in over two-years, suggesting that they’re neglected. This is why it is critical for organizations to have an additional mechanism to make sure OSS has oversight to ensure that first-party software does not serve as an open door to their software supply chain.
CI/CD and Runtime protection: Shifting security left in the CI/CD pipeline helps organizations to reduce risk significantly but does not eliminate the possibility of applications making their way into products with significant, unknown vulnerabilities. CI/CD analysis should be paired with continuous run-time monitoring, allowing security teams to quickly identify and react to emerging threats.
As a CISO, it’s crucial to proactively identify and mitigate these risks through thorough assessment, robust security practices, and vigilant monitoring. By following the strategies outlined in this blog, you can significantly enhance the security posture of your first-party software and embedded components, ultimately safeguarding your organization’s digital assets and reputation in an ever-evolving threat landscape.
How Qualys Helps with First-Party Software Risk Management
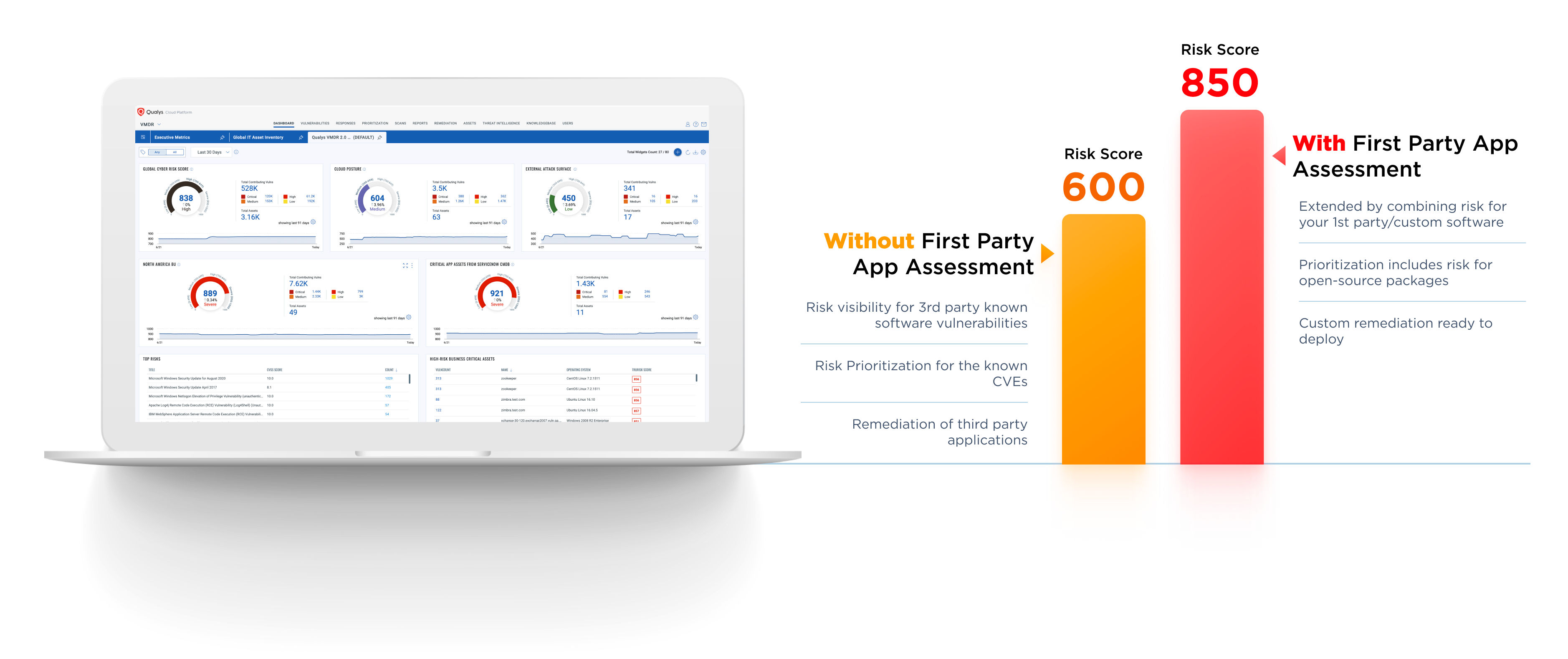
Qualys is attacking the risk embedded in first-party OSS and embedded components with two new capabilities. First Qualys has opened our threat library, unifying VMDR (Vulnerability Management, Detection and Response) with Custom Assessment and Remediation (CAR). This creates a comprehensive First-Party Software Risk Management solution based on the single powerful Qualys Cloud Agent. Qualys CAR allows users to write their own discovery and remediation logic for custom first-party software and execute actions using the VMDR interface, allowing them to extend the power of the Qualys platform across every application and for any use case.
Second is Qualys Runtime Software Composition Analysis (SCA), which offers comprehensive real-time detection and assessment of vulnerabilities in embedded open-source and commercial software packages used in production environments while prioritizing and remediating the risk with the context of threats and asset criticality.
Combined, these solutions provide deep visibility into vulnerabilities in first-party software both during the development process and runtime, empowering organizations to fortify applications against emerging threats with confidence & ease.
Get Started
To learn more about how Qualys can help with mitigating risk with custom first-party software and application components in your organization, watch this space for additional in-depth blogs covering software risk management.
To learn how to get started with First-Party Software Risk Management,
- Contact your Qualys Technical Account Manager
- Start a Qualys Trial at no extra cost