Latest Trend in Mac Vulnerabilities and How to Efficiently Address Them
Usually, every September/October, Apple releases its updated OSes and, with them, a set of new CVEs. This month was no different.
In fact, if we look at 2023, Qualys released on average 32 new QIDs every month for MacOs and its 3rd-party products (see figure below):
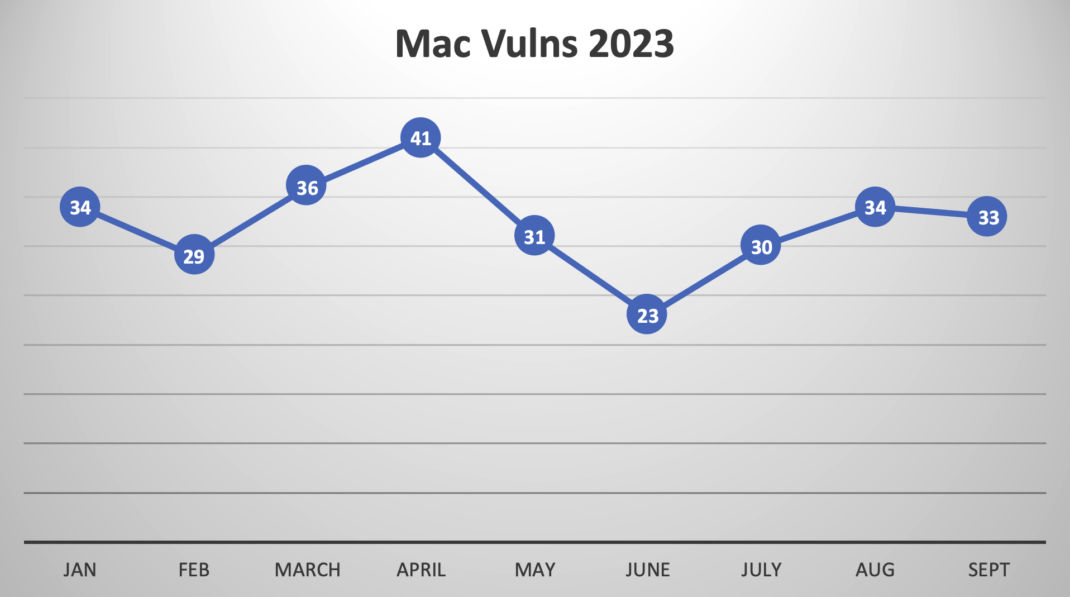
In the past few years, there has been a sharp increase in the number of Mac devices used by end users. As such, ensuring those devices are fully patched has become more critical. To keep up with this volume of vulnerabilities, organizations have to opt-in, buy, and operate a dedicated (and in many cases proprietary) Mac tool to help them enforce the patching of all those vulnerabilities. As a result, customers find themselves with a dedicated set of tools to patch their Windows devices and a new dedicated tool for those with MacOS devices. Mac devices represent a smaller number for some customers than Windows devices. Even so, they are required to buy and operate a proprietary patching tool for Mac.
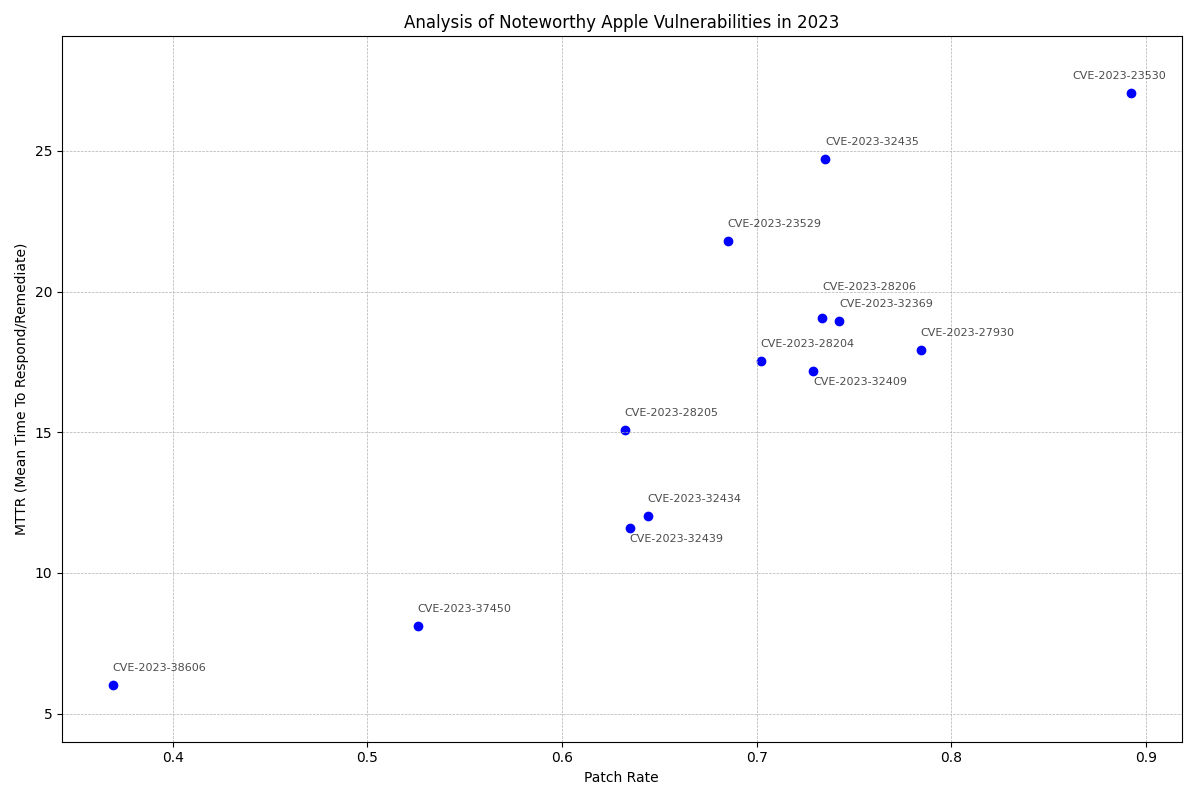
As we emphasize the importance of timely patch adoptions in cybersecurity, two recent Apple vulnerabilities serve as critical examples, highlighting this urgency.
The CVE-2023-38606 and CVE-2023-37450 present notable concerns regarding their patch adoption rates.
- CVE-2023-38606, an exploited zero-day kernel vulnerability with a Qualys Detection Score (QDS) of 95, registers a particularly low patch rate at just 36.92%. It implies that over 63% of the devices or systems remain potentially vulnerable even after the patch is available.
- CVE-2023-37450, an exploited WebKit zero-day with a Qualys Detection Score (QDS) of 95. While slightly higher, it still reflects a concerning patch rate at 52.58%, leaving almost half of the customer base exposed to related vulnerability.
The potential security risks associated with these unpatched systems are high, and customers must take proactive measures. A simplified patching process ensures that the process is streamlined and hassle-free.
Note that our data reviewed by Qualys Threat Research Unit (TRU) is thoroughly anonymized, guaranteeing that all ensuing evaluations remain untraceable to specific entities or resources.
Simplify Patching Your MacOS and 3rd-Party Apps
Since we first introduced our Patch solution for Mac devices almost a year ago, common feedback we got from our customers is about the time saving it provides. It’s ability to patch MacOS and 3rd-party applications, as well as its ability to consolidate end-user device patching (Windows and Mac) into one solution, allows customers to be more efficient with their processes and respond faster, in many cases, utilizing automation to address newly discovered vulnerabilities in end-user devices.
Since the majority of MacOS devices are used by end users, an efficient way to respond to the latest increase in their vulns is by leveraging Smart Automation for Mac Patching. Through smart automation, newly discovered vulns (OS and/or 3rd Party apps) on end-user devices are automatically patched as soon as the new vuln is discovered. This method allows organizations to patch more end-user devices faster and, if done right, will introduce minimal operational risk.
However, for the MacOS machines that cannot be automatically patched, you can use smart automation with testing.
Smart Automation with Testing for MacOS Devices
As IT or SecOps professionals, we have concerns that deploying a patch on a Mac device may potentially cause disruptions, leading to the CxO, who owns the Mac, being unable to perform her tasks.
But, it rarely happens.
A guesstimate is that 95%+ of the time, a MacOS patch or a 3rd-party app patch will not cause any issues.
Smart Automation with Testing takes an automated approach to testing by leveraging this 95%+ guesstimate:
In phase 1, macOS and the 3rd party app patches are deployed automatically to a test group of devices a day or two after those patches are released. After a period of 7 days or more, automatically and without “human intervention,” the same tested patches are deployed to a larger group or the entirety of end-user devices.
Assuming 9 out of 10 times, the newly deployed patches do not introduce any operational problems, the entire patch cycle becomes fully automated, and no manual intervention is needed. In rare cases, such as a patch “breaking something,” only then the IT person can manually intervene and stop the deployment of the patches beyond the test group in phase 1.
A Simple and Improved Way to Patch Your MacOS Devices
Qualys Mac patching, which is part of Qualys Patch Management and its tight integration with VMDR, allows Qualys customers to detect, prioritize, and remediate vulnerabilities on all major OSes (including 3rd party). Adding smart automation further simplifies remediation, ensuring an efficient way to respond to the increasing number of vulns on your Mac, Windows, and Linux.
If you are a Qualys customer with agents deployed, starting a Patch Trial is very easy. Your current deployed agents can already patch Mac and Windows devices. Visit the free trial page, and we will enable a trial license for you so your agents can start patching.
If you are interested in learning more about Qualys Patch Management, do not hesitate to reach out to sales.
Contributors
- Saeed Abbasi, Product Manager, Vulnerability Research, Qualys