An Easy and Effective Strategy To Shield Your Business From Ransomware
Last updated on: December 15, 2023
Ransomware continues to make headlines and remains a top concern
2022 was a breakout year for ransomware as it wreaked havoc on individuals and organizations around the world. The numbers are staggering:
- Ransomware attacks surged dramatically in 2022 and were involved in 25% of all breaches, according to the 2022 Verizon Data Breach Investigations Report and
- Losses reported by the FBI from ransomware increased by 449% between 2019 and 2021, from $8.9 million to $49.2 million, according to the FBI’s Internet Crime Complaint Center (IC3).
Ransomware attacks continued in 2023, with new players such as Royal, BianLian, and Play ransomware gangs joining the field and major players like Lockbit, ALPHV, Malas, and Clop executing mass ransomware attacks.
Ransomware attacks have just become more difficult to conceal by public companies subjected to a material breach. In a new amendment that became effective on September 5, 2023, the US Securities and Exchange Commission (SEC) announced that publicly traded companies would be required to disclose, through a Form 8-K filing, any material cybersecurity breach within four business days unless otherwise instructed by the US attorney general due to substantial risk to national security or public safety.
In an ironic twist to the SEC’s new disclosure requirement, the ransomware group known as ALPHV and BlackCat claims to have breached the systems of MeridianLink. This California-based company provides digital lending solutions for financial institutions and data verification solutions for consumers. To increase its chances of getting paid, the malicious hackers claim to have filed a complaint with the SEC against MeridianLink, accusing the company of failing to disclose the breach within four business days, as required by rules announced by the agency in July. This appears to be the first time a ransomware group has filed an SEC complaint against one of its victims.
Prevention is key to protection from ransomware
Many ransomware attacks start with the attackers exploiting a known vulnerability to get a foothold in the environment. Unfortunately, many organizations are not able to address such initial breaches in a timely manner. Ransomware-related vulnerabilities also allow ransomware groups to exploit the same vulnerabilities using the same techniques against different organizations. When organizations do not patch those vulnerabilities – even after being exploited – ransomware groups will exploit the same vulnerability against the same organization running a new ransomware campaign!
The Cybersecurity and Infrastructure Security Agency’s (CISA) recent #StopRansomware Guide (October 19, 2023) emphasizes the importance of prevention by advising organizations to “regularly patch and update software and operating systems to the latest available versions. Prioritize timely patching, … especially for known exploited vulnerabilities.” Unfortunately, in many cases, organizations find it challenging to prioritize and take remediation actions against those “known exploited vulnerabilities.”
In the same SEC amendment mentioned above, the SEC instructs all registered companies to “describe their processes, if any, for the assessment, identification, and management of material risks from cybersecurity threats…” As a successful ransomware attack is highly likely to be a “material risk,” Qualys recommends the pursuit of prevention should also be a key part of every organization’s risk management strategy.
Ransomware vulnerabilities – the data points
Fortunately, preventing ransomware by first focusing on the vulnerabilities that are used in ransomware attacks is achievable. Based on a study by the Qualys Threat Research Unit, out of 76,667 all-time weaponized vulnerabilities, only 270 are actively used in ransomware campaigns. This is less than 1%. The good news is that this is an achievable goal! However, even though the number of ransomware vulnerabilities is low, they are highly targeted and actively being repeatedly re-used by ransomware groups. Rachel Wilson, Managing Director at Morgan Stanley, discussed the repeated use of ransomware vulnerabilities at our recent Qualys Security Conference in Orlando. Moreover, the Qualys Threat Research Unit estimates that 25% of assets, which is one out of every four assets, still have at least one open ransomware-related vulnerability. Our research shows that the average time to remediate a ransomware vulnerability is a whopping 141 days!

To summarize, the above data points illustrate two key findings:
- The number of vulnerabilities to focus on to prevent ransomware is not astronomically high.
- However, on average, organizations are not sufficiently targeting and remediating these ransomware-related vulnerabilities.
3 actions for an efficient ransomware prevention program
To more effectively remediate vulnerabilities and prevent ransomware attacks, Qualys experts recommend the following actions: utilizing the Qualys platform to detect ransomware-related vulnerabilities and “known exploited vulnerabilities” to respond more efficiently.
Action 1: Prioritize ransomware vulnerabilities
Check CISA’s #StopRansomware guide and implement their guidance to measure, map, and prioritize vulnerabilities with a focus on vulnerabilities that are known to be used in ransomware attacks.
First on the list, leverage Qualys VMDR’s prioritization reporting to flag and prioritize vulnerabilities related to ransomware attacks. VMDR leverages dozens of real-time threat feeds to pinpoint the vulnerabilities that are used in ransomware campaigns, and are detected in your environment. VMDR TruRisk should then be used to prioritize those vulnerabilities based on those vulnerabilities’ true risk to your environment.
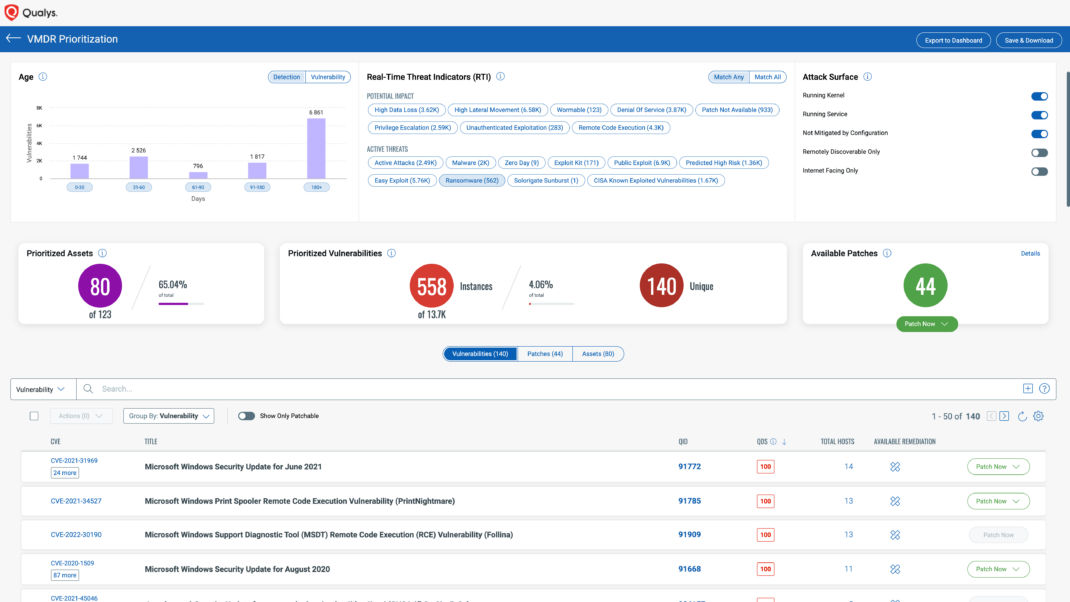
Action 2: Focus on patching vulnerable external-facing assets
Use Qualys Patch Management to map the ransomware-related vulnerabilities in your environment that have been identified and prioritized in VMDR to the patches and configuration changes required for remediation of the ransomware risk. Qualys highly recommends security teams focus first on external-facing assets as they are more easily exploited by attackers.
Once vulnerabilities are mapped to the actual remediation actions (i.e., which patches and configuration changes are required for each vulnerable asset), use Patch Management to test and deploy the relevant OS and third-party application patches, and the required configuration changes to your vulnerable Windows, Mac, and Linux assets. If SCCM is your main patching tool, you may use SCCM to deploy the relevant OS patches to the vulnerable assets and use Patch Management to complement SCCM for ensuring all OS and third-party application patches are deployed.
Action 3: Automate browser and document reader patches
Patch assets that “operate software for processing internet data, such as web browsers, browser plugins, and document readers,” as specifically recommended in the CISA #StopRansomware guide.
Individually patching browsers like Chrome, Firefox, Edge, and Safari, plus document readers like Adobe Reader once is a time-consuming but manageable task for IT. However, as software providers release new patches frequently, most IT teams find it hard to cope with the frequent pace. As a result, many browsers and document readers stay unpatched for longer than expected.
By creating a “Zero Touch Job” with Patch Management, Qualys customers can ensure that all browsers, Adobe Reader, and other internet-facing applications are always up to date. Once set, this job will run on a regular basis and will ensure that as soon as a new patch is released for those apps, the Qualys agent will automatically install it – ensuring those internet-facing applications are secure.
Bonus pro tip: Take advantage of Qualys Patch Management’s automation
You may use Patch Management automation to define a rule that will automatically flag assets with open ransomware-related vulnerabilities, find the latest patch to fix the vulnerability, and test and deploy the patch automatically. This type of automation, which is particularly efficient for workstations, can ensure that assets that have open vulnerabilities that are actively used in ransomware campaigns are automatically patched upon release of the patch.
Experience the Qualys difference yourself

To see the difference implementing the above actions can take, Qualys has created a ransomware prevention dashboard that customers can import into their subscriptions. It only requires a VM license; VMDR customers can start seeing additional value today!
Get a copy of your free ransomware prevention dashboard!
Resources
- CISA: #StopRansomware Guide
- SEC: Final Rule: Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure
Contributors
- Utpal Desai, Senior Director, Product Management, Cloud Agent Platform, Qualys