Enhancing Application Security Using OWASP Recommendations and Best Practices

Table of Contents
- What is OWASP and Its Crucial Role in Application Security
- Understanding the OWASP Top 10 and How It Improves Application Security
- How to Utilize OWASP Security Resources to Enhance Application Security
- Integrating OWASP Security Guidelines into the Development Lifecycle with Qualys WAS
- Common Application Security Challenges with OWASP Adoption and How to Solve Them
- Conclusion
In a time where over 60% of data breaches are linked to software vulnerabilities and a single overlooked software vulnerability can expose sensitive data, the imperative of robust application security cannot be overstated. The 2023 IBM Security Cost of a Data Breach Report highlights that personally identifiable information (PII) of customers and employees is not only the most frequently breached type of record but also the costliest, averaging $183 and $181 per record, respectively. As security threats evolve and become more sophisticated, developers and security professionals must arm themselves with comprehensive, up-to-date knowledge and tools to defend their applications effectively. One of the most crucial resources available to those in the field of cybersecurity is the Open Web Application Security Project (OWASP).
OWASP is an international nonprofit organization dedicated to improving the security of software. Its mission is to make software security visible so that individuals and organizations worldwide can make informed decisions about true software security risks. In this blog, we will decode the various aspects of OWASP, highlighting its significance and offering a roadmap for security engineers to integrate OWASP standards into application security strategies effectively.
What is OWASP and Its Crucial Role in Application Security
The Open Web Application Security Project (OWASP) was established in 2001 as an online community where people interested in software security could come together to learn, share knowledge, and collaborate on projects. Today, OWASP has grown into a respected authority in the field, providing free, openly available documentation, tools, and standards that are widely used by developers and security professionals around the globe.
OWASP offers a plethora of resources designed to assist in securing software across its lifecycle. Among the most valuable are –
- OWASP Top 10 – A regularly updated document outlining the most critical security risks to web applications.
- OWASP cheat sheets – Concise collections of best practices aimed at helping developers avoid common security pitfalls.
- OWASP testing guide – A comprehensive manual for testing web applications for security vulnerabilities.
Why OWASP is Vital for Every Application Security Engineer
For security engineers, OWASP serves as an indispensable guide. The resources provided by OWASP are grounded in real-world data, contributed by security practitioners who deal with these threats on a daily basis. This makes OWASP’s recommendations both practical and directly applicable to everyday security tasks and long-term strategy planning.
Understanding the OWASP Top 10 and How It Improves Application Security
The OWASP Top 10 is perhaps the most well-known document produced by OWASP. It serves as a list of the ten most critical web application security risks, updated every few years based on evolving threats and community feedback. This list is not only a tool for raising awareness but also acts as a guide for security professionals to prioritize their efforts in mitigating the most significant risks.
The OWASP Top 10 categorizes and prioritizes the top security risks based on data from various security organizations and community input. It is designed to be accessible to a wide range of stakeholders, from developers and technical leads to upper management, providing everyone with a common language to discuss application security issues.
The most recent update of the OWASP Top 10 includes the following categories –
- Injection flaws such as SQL, NoSQL, and LDAP injection, where untrusted data is sent to an interpreter as part of a command or query.
- Broken authentication where application functions related to authentication and session management are often implemented incorrectly, allowing attackers to compromise passwords, keys, or session tokens.
- Sensitive data exposure where web applications do not properly protect sensitive data, such as credit cards, health information, and personal details, potentially exposing it to attackers.
- XML External Entities (XXE) where poorly configured XML processors evaluate external entity references within XML documents. External entities can be used to disclose internal files and file shares.
- Broken access control where restrictions on what authenticated users are allowed to do are often not properly enforced. Attackers can exploit these flaws to access unauthorized functionality and/or data.
- Security misconfigurations where security settings are not defined, implemented, and maintained as defaults and are often insecure. Additionally, software might be outdated.
- Cross-Site Scripting (XSS) flaws occur whenever an application includes untrusted data in a new web page without proper validation or escaping, allowing attackers to execute scripts in the browser of an unsuspecting user.
- Insecure deserialization leads to remote code execution. Even if deserialization flaws do not result in remote code execution, they can be used to perform attacks, including replay attacks, injection attacks, and privilege escalation attacks.
- Using components with known vulnerabilities, such as libraries, frameworks, and other software modules, that run with the same privileges as the application. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover.
- Insufficient logging & monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data.
Security engineers can use the OWASP Top 10 to structure their assessment results and develop mitigation strategies by aligning security audits with the OWASP Top 10 to ensure coverage of these critical risks and focus on remediating identified vulnerabilities that correspond to the OWASP Top 10, prioritizing those with the highest potential impact. By familiarizing themselves with the details of each category and taking proactive steps to avoid these risks, security engineers can significantly enhance the security of the applications they protect.
How to Utilize OWASP Security Resources to Enhance Application Security
While the OWASP Top 10 provides a foundational framework for understanding and addressing the most critical web application security risks, OWASP offers a range of other resources that can be instrumental in developing and refining an application security strategy. These include the OWASP Testing Guide, Cheat Sheets, and a variety of tools and projects designed to aid in the practical aspects of security implementation.
OWASP Testing Guide – The OWASP Testing Guide is a comprehensive resource that offers a deep dive into the specifics of testing web applications for security vulnerabilities. It covers a wide array of potential vulnerabilities beyond the Top 10, providing guidance on how to rigorously test and validate each one. The guide offers standardized testing procedures that can be integrated into any security workflow, ensuring thorough coverage and consistency in testing. It recommends tools and techniques for effective security testing, helping teams to be more efficient and effective in their security assessments.
OWASP Cheat Sheets – The OWASP Cheat Sheets are concise, focused guides containing the best practices on a specific security topic. They serve as handy guides for security teams and developers to quickly reference when implementing security measures.Cheat sheets can be used as training materials to educate developers and security professionals on specific security issues and how to mitigate them.By following the guidelines, organizations can ensure compliance with security best practices and standards.
OWASP Tools and Projects – OWASP supports numerous tools and projects that can be leveraged to enhance application security –
- Dependency Check – A tool that identifies project dependencies and checks if there are any known, publicly disclosed, vulnerabilities.
- Security Knowledge Framework – A web-based application that provides detailed information and methodologies on building secure software.
Each of these tools and projects provides practical support in implementing robust security practices, enabling security teams to identify, understand, and mitigate vulnerabilities effectively.
Integrating OWASP Security Guidelines into the Development Lifecycle with Qualys WAS
For security engineers implementing OWASP guidelines in the development lifecycle, Qualys Web Application Scanning (WAS) offers a comprehensive, automated, and integrated approach to web application security.
Step 1 – Integrate security early in the development process (Shift Left)
Integrate Qualys WAS into the development tools used by the team, such as Continuous Integration/Continuous Deployment (CI/CD) pipelines for automated scans every time code is committed, ensuring that any new code is tested immediately for vulnerabilities. Developers must be educated and trained on the OWASP Top 10 vulnerabilities and common security issues for awareness of security in coding practices.
Step 2 – Continuous and Automated Scanning
Configure scans within Qualys WAS to perform automated scanning without manual intervention based on predefined schedules or triggered by specific events, such as code commits or deployments. Utilize Qualys WAS’s capabilities to conduct dynamic scans, static code analysis, and interactive application security testing to cover different aspects of application vulnerabilities.
Step 3 – Prioritize OWASP Top 10 risks and address compliance
Customize scanning rules in Qualys WAS to specifically include tests for the vulnerabilities listed in the OWASP Top 10, ensuring that the applications adhere to recognized security standards. Security engineers can also use Qualys WAS to generate compliance reports that map findings directly to the OWASP Top 10 risks for audits and compliance reviews.
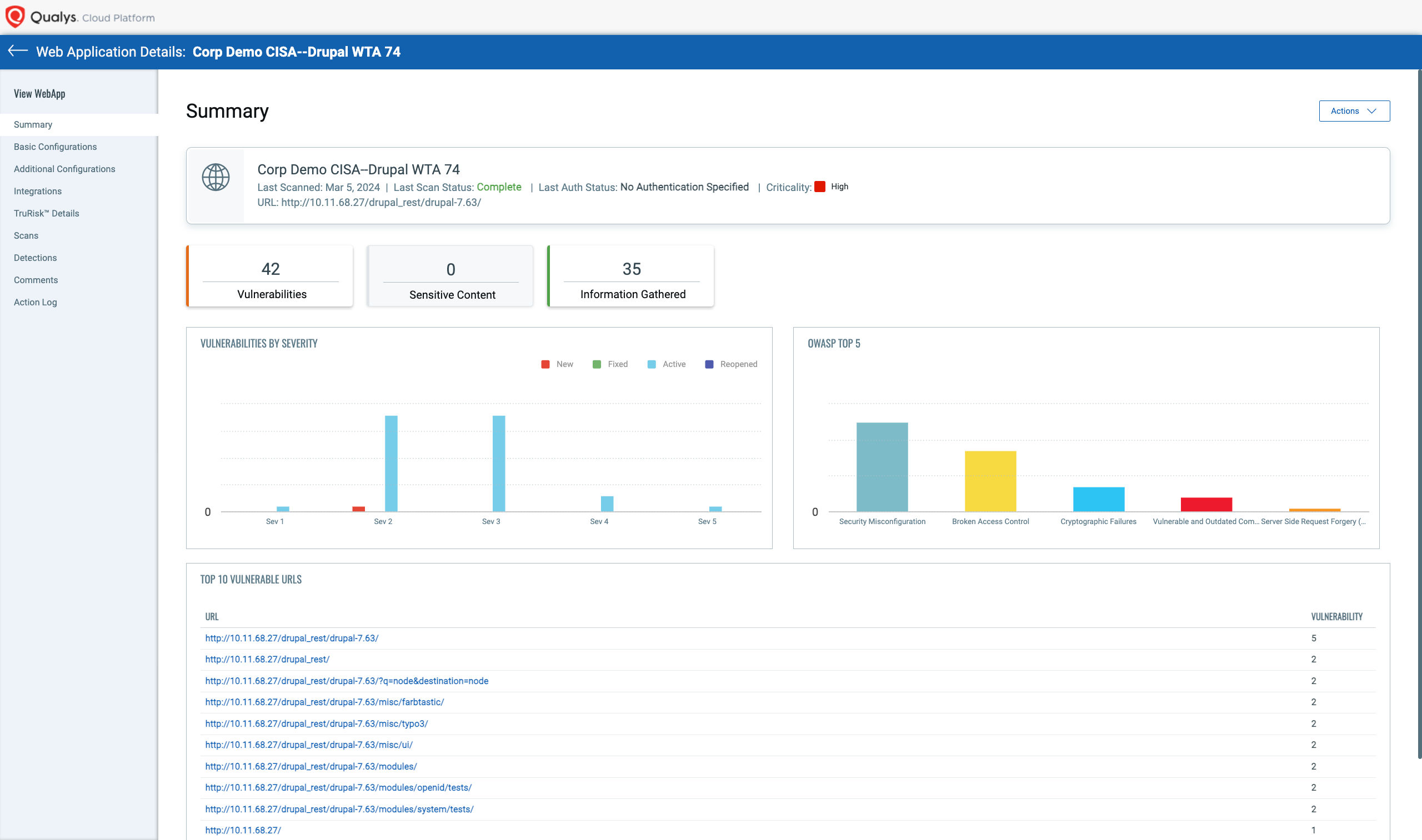
Step 4 – Remediation and feedback loop
Based on the scan results, use Qualys WAS to prioritize vulnerabilities that need immediate attention. Prioritization can be based on the severity, exploitability, and impact of the vulnerabilities. Detailed findings and remediation guidance directly within their working environments, like JIRA, can help developers cut down on repetitive manual work.
Step 5 – Monitor and improve
Keep monitoring the applications for new vulnerabilities as part of the ongoing security efforts and regularly review the effectiveness of the implemented security measures. Qualys WAS can be set to continuously scan and monitor the applications to catch any new threats that emerge due to changes in the application or external environment. Use the data and trends from Qualys WAS to assess and adapt the security posture, ensuring improvements are made continuously based on the evolving threat landscape. Update scanning configurations, rules, and developer training to address new vulnerabilities and security challenges.
By following these steps, a security engineer can effectively implement OWASP guidelines using Qualys WAS, embedding security into the fabric of the development process, making it a fundamental aspect of software development in the organization.
Common Application Security Challenges with OWASP Adoption and How to Solve Them
Implementing the Open Web Application Security Project (OWASP) guidelines throughout the development lifecycle can pose several challenges for security engineers, ranging from coverage of security tests to integration of security practices without disrupting development processes. Qualys Web Application Scanning (WAS) can address these challenges in several ways –
1. Early and continuous vulnerability identification
Security engineers often struggle to detect vulnerabilities early in the development cycle, which can lead to costlier fixes if the vulnerabilities are discovered later in production. Qualys WAS supports the “Shift Left” best practices, enabling engineers to integrate continuous, automated security scanning early in the development stages. By identifying vulnerabilities from the very beginning, Qualys WAS helps ensure that security is a cornerstone of the development process, not an afterthought.
2. Compliance with OWASP Top 10
Staying compliant with the OWASP Top 10 vulnerabilities requires constant updates and knowledge about new security risks, which can be overwhelming for security teams to manage manually. Qualys WAS continuously updates its scanning capabilities to detect the latest known vulnerabilities, including those listed in the OWASP Top 10. With automated update and scanning capability, Qualys WAS ensures that applications are always checked against the current security standards without manual intervention, reducing the burden on security teams.
3. Integration with development tools
Integrating security tools into existing development and deployment pipelines can be technically challenging and may disrupt existing workflows. Qualys WAS offers seamless integration capabilities with popular CI/CD & DevOps tools for facilitating security checks without disrupting the development processes. For instance, developers can receive immediate feedback on vulnerabilities via the CI/CD pipeline, promoting faster and more efficient remediation.
4. Scalability across the application portfolio
Security engineers are tasked with managing and securing a growing number of web applications, which can vary in complexity and technology stack. With its scalable cloud-based platform, Qualys WAS can handle the security assessment needs of any number of web applications, from a few to thousands, without degrading performance or increasing operational complexity, especially for large enterprises that are always expanding their digital presence.
5. Detailed reporting and prioritization
Prioritizing the remediation of identified vulnerabilities based on their risk level can be challenging, especially when resources are limited. Qualys WAS identifies vulnerabilities and provides detailed reports that include risk ratings and remediation recommendations. Security engineers can prioritize fixes based on each vulnerability’s severity and potential impact, ensuring that the most critical issues are addressed first.
Conclusion
Security is not a one-time effort but a continuous process of learning, adapting, and improving. As cyber threats evolve, so too must our approaches to securing our digital environments. The Open Web Application Security Project (OWASP) provides a vital repository of knowledge, tools, and best practices for securing web applications. Embracing OWASP’s guidelines provides a solid foundation for developing resilient and robust security postures that can withstand the challenges of the modern digital landscape.
By engaging with OWASP resources, participating in community discussions, and applying learned principles in practical scenarios, security engineers and developers can significantly advance their application security strategies. While challenges exist in adopting these practices, the benefits of enhanced security, compliance, and protection against cyber threats outweigh the difficulties, especially with automated, continuous application security solutions like Qualys WAS.
For those interested in further exploring their understanding of OWASP’s topics or related resources, consider visiting the following links –
- OWASP Main Website
- OWASP Top 10
- OWASP Cheat Sheets
- OWASP Web Security Testing Guide
- OWASP Dependency-Check
- OWASP Application Security Verification Standard
- Zed Attack Proxy (ZAP), formerly known as OWASP ZAP
- Security Knowledge Framework (SKF)
Experience the power of advanced application security and see how Qualys WAS can enhance your OWASP security practices, sign up for a no-cost trial today.
Not a bad article at all, but as almost anybody else talking about OWASP the focus is on the OWASP Top 10 vulnerabilities, where more attention should be given to the OWASP Top 10 Proactive controls. Which is not mentioned at all in this article.