The State of Cyber Risk 2025: Business Context Needed
Table of Contents
- A Snapshot from the Frontlines: New Research by Qualys and Dark Reading
- Formal Risk Programs are Expanding, But Business Context is Still Missing
- More Investment Less Risk: Why the Cyber ROI isnt Adding Up
- The Missing Metric: Business Relevance in Asset Intelligence
- Risk Prioritization Needs to be a Business Conversation, Not a Technical One
- Reporting Risk in Business Terms, Not Security Jargon
- Recharting Risk Operations with Business Impact as the North Star
- Final Word: Maturity is About Business-centric Alignment
The cyber risk conversation is changing. Momentum is growing for formal cyber risk programs. However, despite rising investments, evolving frameworks, and more vocal boardroom interest, new data reveals that most organizations remain immature in their risk management programs, and cyber risk is rising.
As digital transformation accelerates and AI-powered threats emerge, the question is no longer whether we need to address cyber risk, but whether organizations can quantify, prioritize, and reduce it in ways that provide real value and reflect business context. A new Dark Reading research report commissioned by Qualys offers a timely pulse check on this challenge and a path forward for those ready to evolve.
Want to see what cyber risk really looks like in 2025? Take a deep dive into the Qualys-Dark Reading Research Report on State of Cyber Risk 2025—Download the full report now!
A Snapshot from the Frontlines: New Research by Qualys and Dark Reading
To get a clearer view of the state of cyber risk management in 2025, Qualys partnered with Dark Reading to conduct in-depth research with over 100 IT and cybersecurity leaders across industries. The findings offer a rare inside look at how security teams are managing business risk and where they are struggling.
What emerged from this collaboration is a stark insight: Many organizations are still approaching cyber risk as a technical problem, not a business one.
Traditional, reactive methods – or “cyber risk whack-a-mole” – are no longer sufficient. Security programs that fail to align with operational, financial, and regulatory stakes are simply ineffective. High-performing teams are instead adopting approaches that incorporate business context into every layer of risk management.
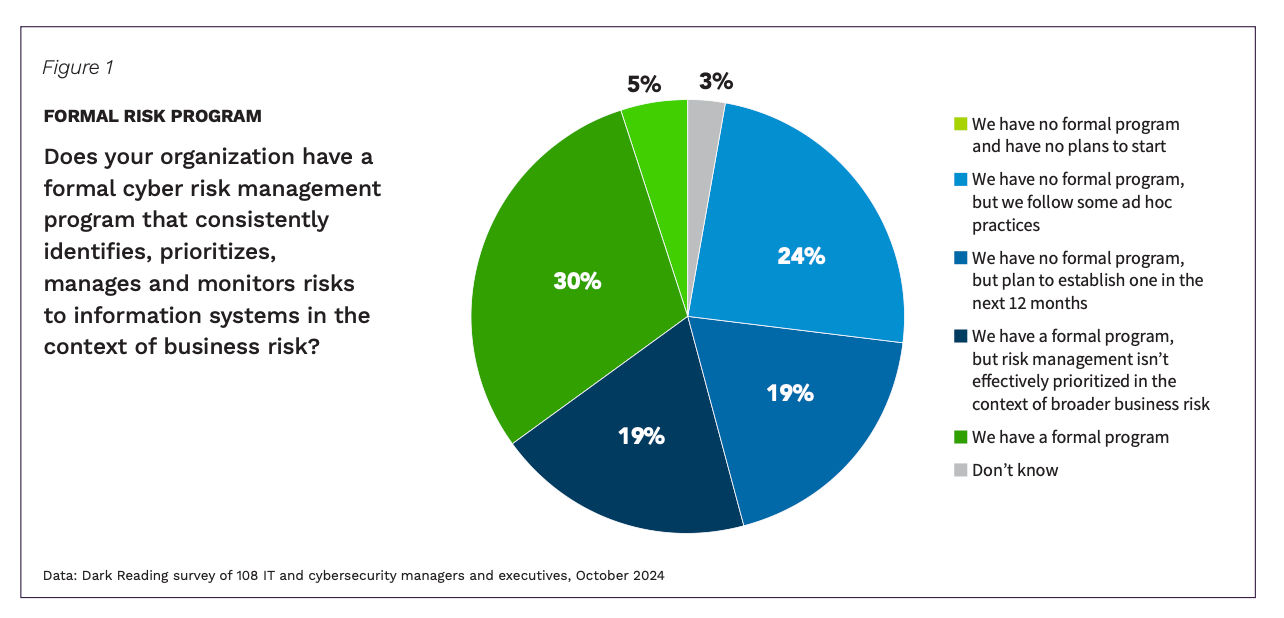
Formal Risk Programs are Expanding, But Business Context is Still Missing
Nearly half (49%) report having a formal cyber risk program in place which looks like a promising statistic on the surface. But dig deeper, and the data shows otherwise:
- Business Alignment Gaps: While 49% of organizations have established formal cyber risk programs, only 30% report that their risk management programs are prioritized based on business objectives.
- Recent Implementations: 43% of existing programs have been in place for less than two years, indicating a nascent stage of maturity.
- Future Plans: An additional 19% are still in the planning phase.
In other words, this is not a maturity curve but a maturity gap. Cyber risk programs may be proliferating, but most remain focused on compliance checklists or technical assessments. What remains absent is a sustained commitment to embedding business context, such as the potential financial loss from a cyber breach or a focus on protecting crown jewel assets, into how these programs identify and prioritize risks. Otherwise, cyber leaders will struggle to make informed decisions that drive real value to the business.
More Investment ≠ Less Risk: Why the Cyber ROI isn’t Adding Up
Cybersecurity spending has continued to grow. Yet one of the most revealing insights from the study is that a vast majority (71%) of organizations believe that their cyber risk levels are rising or holding steady.
- 51% say their overall cyber risk exposure is increasing
- 20% say it remains unchanged
- Only 6% have seen risk levels decrease
This implies that despite organizations’ best efforts, many security investments are failing to move the needle. Often, this stems from a lack of unified visibility and prioritization strategy. Security tools still operate in silos. Asset discovery is fragmented. And most critically, remediation workflows are rarely guided by business context.
Reflecting on this gap, it’s clear that throwing more money at tools or talent won’t move the needle unless the organization has a risk-centric operating model that prioritizes business context, continuously assesses controls, and communicates risk in business terms.
As Qualys CEO Sumedh Thakar emphasized in a recent interview with Bloomberg Intelligence, “Boards and business leaders are no longer asking for dashboards. They want answers to business questions: Are we reducing risk? How much? Where should we focus next? That means connecting security data to the language of business, finance, and operations.”
To answer those questions, security teams need more than tools. They must align technical action with strategic business outcomes.
The Missing Metric: Business Relevance in Asset Intelligence
Visibility in cyber risk management is about a principle that hasn’t changed in 20 years: you can’t protect what you can’t see. Yet even in 2025, asset visibility remains one of the biggest blind spots:
- 83% of organizations perform regular asset inventories
- But only 13% can do so continuously
- 47% still rely on manual processes
- 41% say incomplete asset inventories are among their top barriers to managing cyber risk
In today’s hybrid environments, where virtual machines, containers, and APIs spin up and down constantly, point-in-time inventories simply aren’t enough.
Organizations must understand the business role of the assets they inventory, such as:
- Which applications support revenue-generating services?
- Which systems handle sensitive customer data?
Most teams cannot confidently answer these questions. Effective risk management in modern hybrid environments demands more than visibility. It requires contextual discovery enriched by asset classification, business ownership, and process mapping so that risk signals can be triaged based on their real-world impact.
Set to Triage Risks with Context? Learn how in the Qualys-Dark Reading Research Report on State of Cyber Risk 2025—Download the Full Report Here!
Risk Prioritization Needs to be a Business Conversation, Not a Technical One
Another illusion that persists is the idea that all risks can and should be patched. The longstanding practice of prioritizing vulnerabilities based solely on severity is no longer sufficient. The industry looks to be grasping the fact that risk prioritization needs to go beyond single scoring methods like CVSS alone, with 68% of respondents using integrated risk scoring combining threat intelligence or using cyber risk quantification with forecasted loss estimates to prioritize risk mitigation actions.
However, these next data points show that the industry still has some way to go:
- Nearly one in five (19%) of organizations continue to rank vulnerabilities using a single score like CVSS alone
- Just 18% update asset risk profiles monthly
This one-score-fits-all approach continues to over-rely on raw CVE scores and misses the nuance of business operations. A vulnerability on a publicly exposed revenue app carries a vastly different risk than the same flaw on a decommissioned test server. Yet without business-aware prioritization models, they’re often treated equally.
Leading organizations are replacing severity-first models with integrated, contextual scoring that considers exploitability, asset importance, and downstream business effect. This risk-based approach ensures teams are fixing the right problems, not just the loudest ones.
Reporting Risk in Business Terms, Not Security Jargon
Executives no longer want to hear how many vulnerabilities have been patched. They want to understand what the organization stands to lose, and what’s being done to protect it.
Yet the study finds that while 90% of organizations report cyber-risk findings to the board:
- Only 18% use integrated risk scenarios
- Just 14% tie risk reports to financial quantification
- Business stakeholders are only involved less than half the time (43%)
- And only 22% include finance teams in cyber risk discussions
This signals a fundamental shortfall: security teams still struggle to translate operational data into business-aligned insights. Without this bridge, boards are left making decisions with incomplete information or ignoring cybersecurity altogether until it’s too late. To be effective, risk communication must go beyond metrics and dashboards. It must clearly illustrate how security exposures translate to financial, operational, and reputational loss.
Recharting Risk Operations with Business Impact as the North Star
The key takeaway from the research isn’t just that cyber risk is rising. It’s that current methods are not effectively reducing that risk by prioritizing the actions that would make the greatest impact to risk reduction, tailored to the business. Every business is unique; hence, each risk profile and risk management program should also look unique to the organization. Static assessments, siloed telemetry, and CVSS-based prioritization have reached their limit.
To address this, forward-leaning teams are adopting a Risk Operations Center (ROC) model: a technical framework that continuously correlates vulnerability data, asset context, and threat exposure under a single operational view.
A modern ROC model unifies detection, assessment, and mitigation under a common business-risk framework.
This model is differentiated by the following:
- Cyber risk is tracked continuously, not quarterly
- Vulnerabilities are scored based on impact to the business
- Investments are guided by quantified outcomes, not gut instinct
- Security KPIs are tied to business risk reduction
This is where Qualys Enterprise TruRisk Management (ETM) comes in. ETM consolidates real-time telemetry across hybrid infrastructure and applies the TruRisk™ scoring engine, blending severity, exploitability, asset value, and control posture into a single business-aware metric.
On top of this foundation sits the Qualys Risk Operations Center (ROC): a robust interface that provides a centralized view of enterprise risk, not just in technical terms, but in the context of what matters to the business.
It enables teams to:
- Drill into risk by environment, business function, or asset type
- Prioritize action based on potential financial or operational exposure
- Track progress against defined thresholds of acceptable risk
Rather than react to every alert, organizations can focus on what truly reduces business risk – saving time, effort and investment.
As organizations mature their risk strategies, the ROC becomes a critical capability and strategic business function. It is evidence-based, outcome-driven, and tightly aligned with enterprise resilience goals.
Explore how Qualys ETM and ROC can help you modernize cyber risk operations:
- Learn more about Qualys ETM: qualys.com/etm
- Learn more about Qualys ROC: qualys.com/roc
Final Word: Maturity is About Business-centric Alignment
The 2025 State of Cyber Risk report makes one thing clear: the technical foundation for risk management exists. What’s missing is the strategic alignment between security operations and business priorities.
To close this gap, cybersecurity must evolve from an IT function to a business function. One that can quantify loss, model scenarios, prioritize decisions, and demonstrate return on risk reduction.
That evolution starts with business context, not just more data. It moves from detection to direction, and from siloed operations to aligned outcomes. The ROC model provides a proven path forward for organizations ready to manage cyber risk the way the business understands it and expects it to be managed.
Ready to explore the real risk story in 2025 and stay ahead of the emerging threats?
Get the Qualys-Dark Reading Research Report on State of Cyber Risk 2025.