Two Pwnie Awards, One Crucial Lesson: What Our OpenSSH Research Reveals About Cyber Defense in 2025
We’re honored that the Pwnie Awards recognized the Qualys Threat Research Unit (TRU) with two wins at Black Hat/DEF CON this year—Best RCE for regreSSHion (CVE-2024-6387) and Epic Achievement for our multi-year work uncovering issues in OpenSSH, including CVE-2025-26465. Awards are nice; what matters is what the research means for defenders.
The Pwnie Awards, held annually at Black Hat and DEF CON, celebrate groundbreaking (and sometimes infamous) achievements in cybersecurity. Winning two in one year—especially for high-impact vulnerabilities in a staple like OpenSSH—is a massive validation for our TRU team. It underscores years of meticulous research, collaboration with open-source maintainers, and a commitment to making the internet safer. But as exciting as the trophies are, the real win is empowering defenders with actionable lessons.
Why these two matter
- CVE-2024-6387 (regreSSHion): A pre-auth RCE in the OpenSSH server’s default configuration on glibc-based Linux—effectively the first of its kind in ~20 years. It was a true regression of a 2006 bug, re-introduced in 2020. That kind of “back-from-the-dead” flaw is exactly why software supply chain and regression testing discipline are now first-order security concerns.
- CVE-2025-26465: A machine-in-the-middle issue in the OpenSSH client when VerifyHostKeyDNS is enabled. MITM against SSH isn’t theoretical—if the wrong key is accepted early, the rest of the “secure” session is built on sand. (Notably, some platforms enabled this option by default in the past.)
- Multi-Year Epic: Our Epic Achievement award recognizes TRU’s persistent digging into OpenSSH over years, uncovering not just these but related flaws (like CVE-2025-26466). In an era of AI-accelerated exploits and supply chain compromises, this work highlights the need for ongoing vigilance in foundational protocols.
These vulnerabilities affect millions of devices worldwide, from servers to IoT. Our discoveries prompted rapid patches from OpenSSH maintainers, showcasing the power of responsible disclosure. As the Head of the TRU team Bharat Jogi puts it:
“These high-impact vulnerabilities in a core technology like OpenSSH affect millions of devices worldwide highlighting the importance of meticulous research and responsible disclosure. Our collaboration with open-source maintainers and the security community was key to rapid patches and strengthening security baselines. We’re grateful to the Pwnie Award organizers and judges for recognizing this work, which reflects not only our team’s efforts, but a shared commitment to a safer internet.”

Key Takeaways for Security Leaders: What Patching Really Looks Like
We analyzed over 8.8 million anonymized vulnerability lifecycle events across enterprise environments. The curve is encouraging up front—and stubborn in the tail.
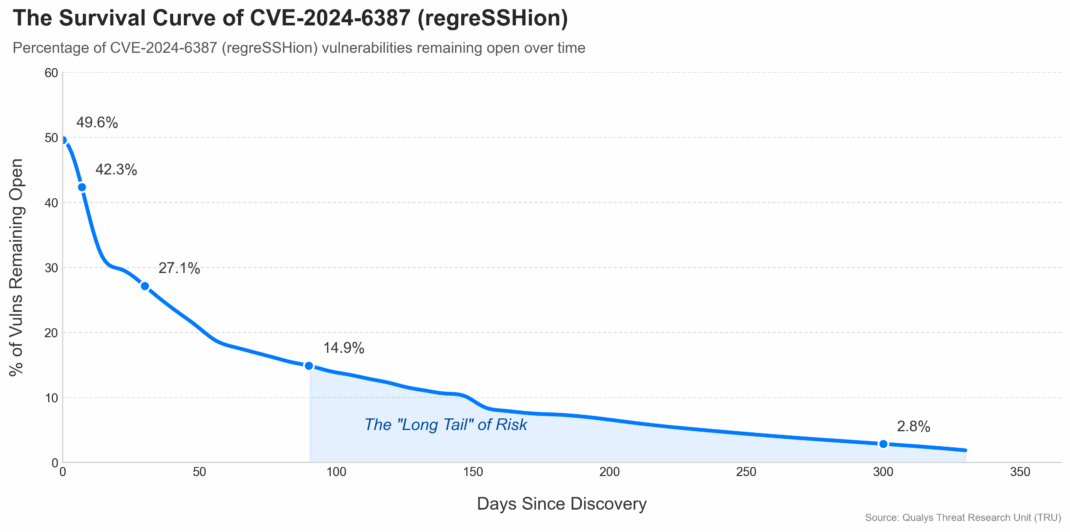
Key Highlights
| Time Frame | % Closed | Key Insight |
| Same Day | 50.40% | Median TTR ≈ 0 days; rapid response is feasible. |
| By 7 Days | 57.70% | Early wins build momentum. |
| By 30 Days | 72.90% | Most fixes happen here, but tails start forming. |
| By 90 Days | 85.10% | Standard benchmarks met, yet risks linger. |
| Past 330 Days | ~1.9% remaining | Breaches often hide in this tail. |
The key takeaways for security leaders are that in such critical cases, the first 24 hours are where half of fixes land; breaches hide in what survives. Make the long tail short by treating anything that is internet-facing + exploitable as something that doesn’t survive the day. In practice, that tail is where real incidents often begin. In 2025, with exploits weaponized in hours, automating detection and patching isn’t optional—it’s survival.
How Qualys Customers Achieve Same-Day Closes with TruRisk
Prioritize by real-world exploitability and exposure, auto-stage patches for the highest-risk sets, and measure MTTR on a live survival curve. If it matters most, it moves first—and it closes today. Same-day wins are a policy choice, not a miracle. With TruRisk, our customers rank assets by risk-to-business, not CVE noise. Result: fewer stragglers at 30/90 days, and a tail too short to hide attackers.
This approach isn’t just theoretical—it’s rooted in the same rigorous research and analysis that powered our OpenSSH discoveries. By applying these insights directly to vulnerability management, TruRisk helps security teams stay ahead of evolving risks in 2025 and beyond. Our TRU experts live this every day, turning vulnerabilities into victories. Qualys CEO Sumedh Thakar adds:
“Qualys has a rich legacy of groundbreaking vulnerability research that sets us apart, delivering genuine expertise in a crowded market. I’m proud to see our TRU team recognized for their vital role in discovering critical vulnerabilities in widely used applications, such as OpenSSH. This work strengthens the security community through responsible disclosure and gives customers a critical edge. It provides premium research that helps security teams understand exploit impacts faster and defend more effectively.”
We’re proud of the recognition, but prouder of the collaboration—with maintainers, vendors, and the research community—that turns hard bugs into better baselines for everyone.
To stay informed of the latest TRU posts, subscribe to our blog.