How Security Tool Misuse Is Reshaping Cloud Compromise
Table of Contents
- Cloud Compromise Frequently Starts with Credential Misuse
- Recent Cyber-Attacks Illustrating the Pattern
- What is the Role of TruffleHog in These Campaigns?
- Emerging Threat Scenarios
- Visualizing the Attack Flow
- Expanding the Pattern: Supply Chain Propagation
- Detection Identifiers
- Strengthening Cloud Security Governance
- Conclusion
- Frequently Asked Questions (FAQs)
Key Takeaways
- Legitimate secret-scanning tools such as TruffleHog have been operationalized in real-world cloud attack campaigns.
- Attack progression commonly follows a repeatable sequence: credential discovery, live validation, permission enumeration, and data access.
- Exposed long-lived access keys and IAM misconfigurations remain primary enablers of cloud compromise.
- API-level telemetry, including identity validation calls, provides observable signals during credential misuse.
- Supply-chain propagation can embed credential harvesting directly into development ecosystems.
- Strengthening credential lifecycle management materially reduces the operational value of discovered access.
Cloud Compromise Frequently Starts with Credential Misuse
Cloud compromise is increasingly defined by authentication rather than exploitation. Exposed credentials and mismanaged identities now provide a faster path to access than vulnerability chaining.
At the same time, legitimate security utilities designed to detect secret leaks are widely available. When used defensively, they reduce exposure. When repurposed for offensive purposes, they accelerate the discovery and validation of access. The differentiator is not a tool, but the operational discipline around credential lifecycle management.
Qualys Insights
See how cloud misconfiguration and exposed access combined to drive a real-world data leak.
Recent Cyber-Attacks Illustrating the Pattern
Several 2025 campaigns illustrate how this dynamic plays out in practice. The sequence is consistent. Credentials are discovered. They are validated through native APIs. Privileges are enumerated. Data access follows.
Adversaries often use TruffleHog, a legitimate open-source secret-scanning tool, to locate leaked/exposed credentials in public or compromised repositories.
Below are the recent high-profile attacks:
- An emerging threat actor group known as ‘Crimson Collective’ targeted Amazon Web Services (AWS) cloud environments using exposed long-term access keys and IAM misconfigurations. After validating credentials, the group enumerated resources across S3 and EC2, ultimately claiming the theft of approximately 570 GB of data from Red Hat’s private GitLab repositories.
- In the TruffleNet campaign, stolen AWS credentials were used to automate reconnaissance and abuse Amazon Simple Email Service (SES) for Business Email Compromise (BEC) operations. More than 800 unique hosts across 57 Class C networks were involved, demonstrating how quickly credential misuse can scale once access is confirmed.
- Compromised OAuth tokens enabled data theft from Salesforce instances integrated with Salesloft Drift.
- A supply-chain attack against the Nx build system introduced malicious NPM packages designed to steal and exfiltrate additional secrets (S1ngularity).
- Another NPM-based supply-chain attack replicated across environments, harvesting credentials from infected machines.
Across these incidents, credential discovery preceded exploitation. The campaigns did not depend on sophisticated malware or zero-day vulnerabilities. They leveraged exposed access and the ability to automate validation.
What is the Role of TruffleHog in These Campaigns?
TruffleHog is a widely trusted open-source credential-harvesting tool designed to help development and cloud teams discover accidental leaks. It detects exposed credentials and tokens in code, logs, Slack, wikis, cloud storage, and other sources, enabling security teams to identify and remediate leaks before they are operationalized.
Along with pattern matching and entropy analysis, it attempts to verify whether a discovered secret is still active and potentially usable by an attacker. It currently supports approximately 800 different credentials and secret detectors. What makes the tool particularly effective is not just discovery, but confirmation. It does not simply flag a possible key. It tests whether that key still works within the environment where it is found.
In structured defensive workflows, this combination of detection and live validation shortens the time between exposure and remediation, providing clarity on which credentials require immediate action.
Emerging Threat Scenarios
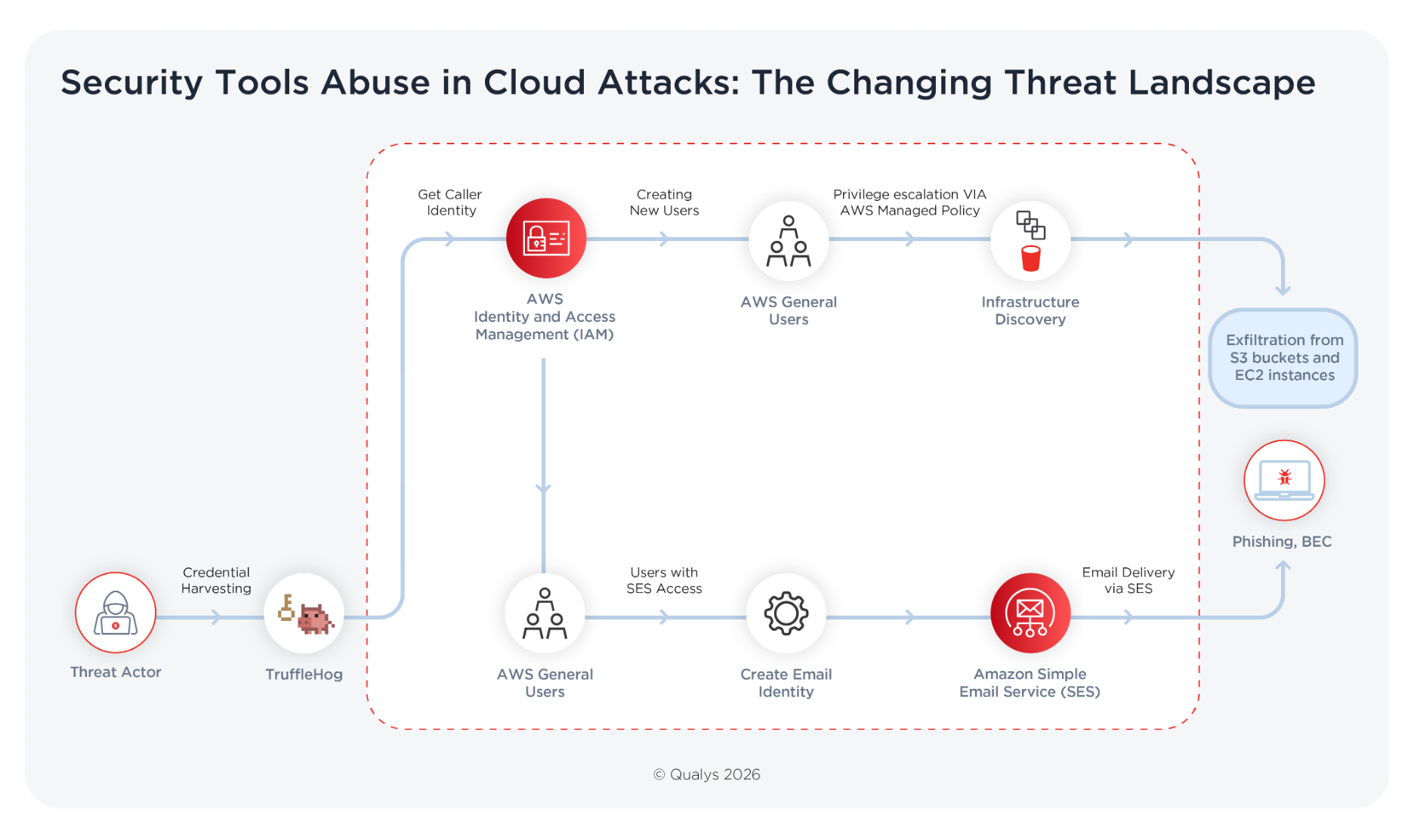
Consider the example of the ‘Crimson Collective’ threat group, which leveraged Trufflehog to harvest AWS credentials. The threat group exploited exposed long-term access keys and IAM misconfigurations to infiltrate cloud environments, escalate privileges, and exfiltrate data from S3 buckets and EC2 instances.
The sequence begins with discovery. Once credentials are identified, the tool attempts live verification. It authenticates using the discovered key and then invokes sts:GetCallerIdentity, which returns details about the IAM entity that called the operation. A successful response confirms that the credential is active.
That confirmation is pivotal. With a validated identity, the attacker can begin enumerating permissions through additional AWS API calls. Roles are inspected. Policies are mapped. Accessible services are identified. The environment reveals itself incrementally.
From there, the activity becomes procedural rather than sophisticated. Privilege escalation where misconfigurations permit it. Reconnaissance across storage and compute resources. Data collection. Exfiltration.
Credential harvesting, verification, exploitation, and exfiltration can unfold within minutes, particularly where long-lived keys and excessive permissions remain in place.
What distinguishes these campaigns is not advanced malware engineering. It is the disciplined use of automation against exposed access.
Visualizing the Attack Flow
The progression described above is not theoretical. It is observable in telemetry.
The diagram illustrates how credential validation becomes the pivot point. Once authentication succeeds, lateral discovery is bounded primarily by permission scope rather than technical barriers.
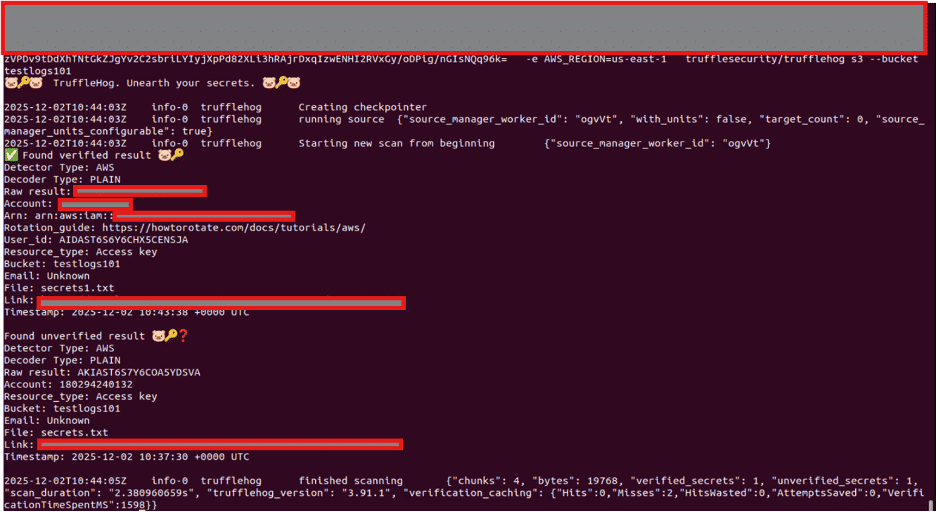
Below is the sample result of the TruffleHog tool that scans an S3 bucket to find exposed credentials:
The output does not simply indicate potential exposure. When live verification succeeds, it confirms that the credential remains active and usable.
An exposed but revoked key represents hygiene debt. An exposed and active key represents immediate access.
The API interactions that follow validation are reflected in CloudTrail logs.
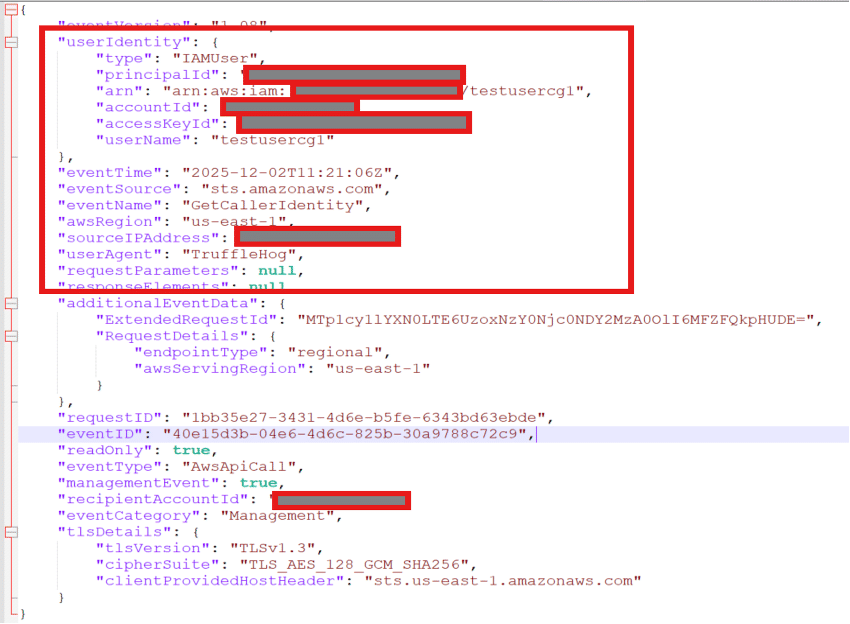
In observed cases, the user agent string includes “TruffleHog,” which may serve as an investigative signal. More importantly, the sequence of API calls often reveals identity confirmation followed by permission enumeration.
Detection depends on recognizing behavioral patterns rather than just tool signatures.
Expanding the Pattern: Supply Chain Propagation
A recent supply chain attack attributed to Shai-Hulud extended this pattern. A self-replicating worm infected more than 500 NPM packages, injecting malicious JavaScript designed to download and run TruffleHog to discover keys/tokens and cloud credentials.
More than 25,000 affected repositories across approximately 500 GitHub users were affected, exposing approximately 14,000 secrets.
The API worms are rising, and currently, instead of relying entirely on malware execution, they use APIs and credential trust relationships to spread between accounts, services, and data lakes for the initial propagation. Propagation depended on valid access, not the exploit novelty. This reflects a broader shift toward API-driven expansion across interconnected cloud ecosystems.
Incidents like these reinforce a consistent theme. Credential discovery precedes exploitation, and authentication precedes impact.
Detection Identifiers
Observable signals do exist, particularly during credential validation and privilege enumeration.
Log entries where GetCallerIdentity (or other AWS API calls) have a user-agent string like “TruffleHog” — this is a known indicator of potential credential discovery.
Alerts can be set for monitoring processes where the process name is (“trufflehog.exe”, “trufflehog”)
This aligns with below MITRE ATT&CK TTPs:
- Tactic:
- Name: Credential Access
- Id: TA0006
- Reference URL: https://attack.mitre.org/tactics/TA0006/
- Technique:
- Name: OS Credential Dumping
- Id: T1003
- Reference URL: https://attack.mitre.org/techniques/T1003/
- Technique:
- Name: Credentials from Password Stores
- Id: T1555
- Reference URL: https://attack.mitre.org/techniques/T1555/
Tool signatures may change. The underlying behavior sequence remains consistent. Authentication, permission mapping, and service interrogation often occur in rapid succession.
Effective detection depends on identity telemetry and correlated API monitoring rather than static indicators alone.
Strengthening Cloud Security Governance
Improving resilience in this context requires tighter control over how credentials are issued, used, and observed.
Organizations can prioritize:
- Eliminating hard-coded and long-lived static credentials across repositories and pipelines
- Replacing static keys with short-lived, role-based access wherever possible
- Centralizing secret storage and enforcing automated rotation policies
- Continuously scanning repositories, artifacts, container images, logs, and configuration files for exposed secrets
- Constraining IAM roles to clearly defined functional boundaries
- Monitoring for unexpected API activity, especially involving dormant or newly activated credentials
- Centralizing and protecting audit logs to preserve investigative integrity
- Embedding secure credential handling practices into development workflows
These controls reduce credential surface area, limit privilege concentration, and shorten the window between exposure and remediation.
Conclusion
What begins as a misplaced key in a repository can progress quietly through validation, enumeration, and data access. The mechanics are routine. The outcome depends on how tightly access has been defined and maintained.
Cloud infrastructure responds to authenticated requests exactly as configured. When credentials are time-bound, narrowly scoped, and continuously observed, discovery has limited reach. When they accumulate across systems without clear ownership, the path from exposure to access shortens.
The campaigns discussed here reflect that reality. In environments where authentication determines capability, the discipline applied to identity and credential management ultimately shapes resilience.
Know which credentials are active, which roles are over-scoped, and which API calls do not belong.
Try Qualys TotalCloud™ and see it in your own environment.
Frequently Asked Questions (FAQs)
What is TruffleHog, and how is it used in cloud attacks?
TruffleHog is an open-source secret-scanning tool designed to detect exposed credentials in code and cloud assets. In recent campaigns, threat actors used it to locate and validate active cloud access keys.
How do attackers exploit exposed AWS credentials?
Attackers authenticate using discovered keys, invoke API calls such as identity confirmation, enumerate IAM permissions, and access resources within the scope of those permissions.
Are credential-based cloud attacks more common than zero-day exploits?
Many recent cloud incidents rely on exposed or mismanaged credentials rather than software vulnerabilities, because valid access provides direct operational capability.
How can organizations detect credential misuse in AWS?
By monitoring API activity, tracking identity validation calls, observing rapid permission enumeration, and correlating unusual behavior from newly activated or dormant credentials.
What is secret sprawl, and why does it increase cloud risk?
Secret sprawl refers to the uncontrolled distribution of credentials across repositories, pipelines, logs, and third-party integrations, increasing the likelihood of exposure and misuse.
How can organizations reduce the risk of exposed cloud credentials?
By eliminating long-lived static keys, enforcing least privilege, rotating credentials automatically, and continuously monitoring identity activity across services.