Alpine Docker Image Vulnerability (CVE-2019-5021): How to Detect and Fix
A vulnerability affecting the official Alpine Docker images version >=3.3 contains a null password for the root user. Due to the nature of this issue, systems deployed using affected versions of the Alpine Linux container that utilize Linux PAM, or some other mechanism that uses the system shadow file as an authentication database, may accept a NULL password for the root user.
Remediation
If you are using an older, unsupported releases, then you can fix it by adding this line to your Docker file:
# CVE-2019-5021 disable root login RUN sed -i -e 's/^root::/root:!:/' /etc/shadow
You can also remove linux-pam if it is installed.
Detecting CVE-2019-5021 (QID 371776)
This particular vulnerability has been tracked as CVE-2019-5021. You can also find the official Alpine announcement at Alpine-CVE-2019-5021.
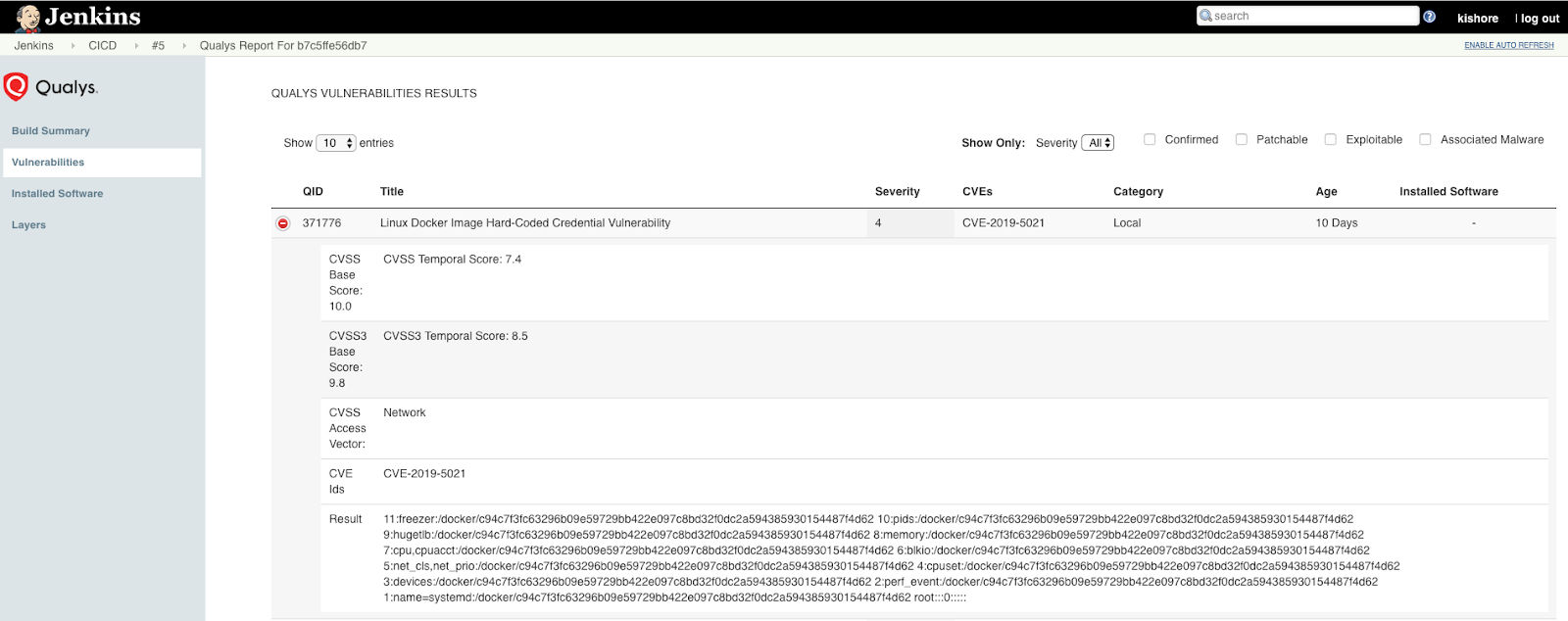
Qualys has released a special QID 371776 for Qualys Container Security to detect this vulnerability, and Qualys customers can use Qualys Container Security to detect this vulnerability at various stages of the Docker image lifecycle.
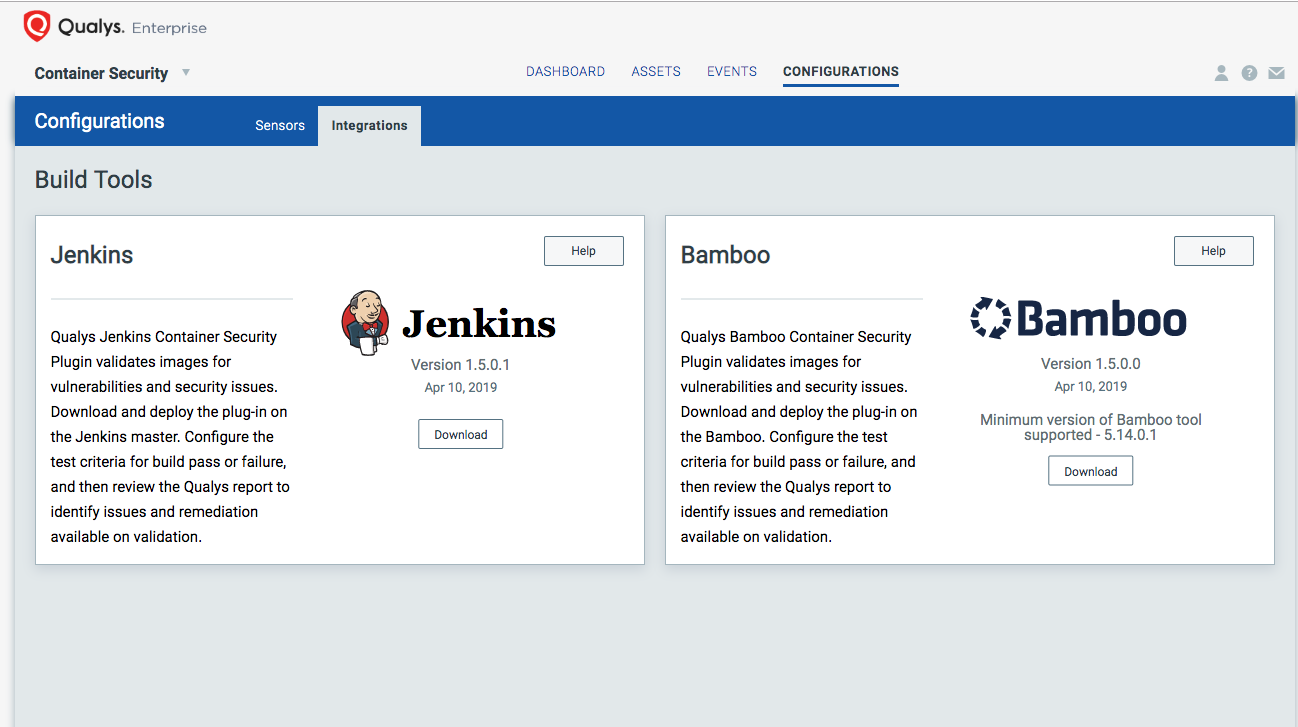
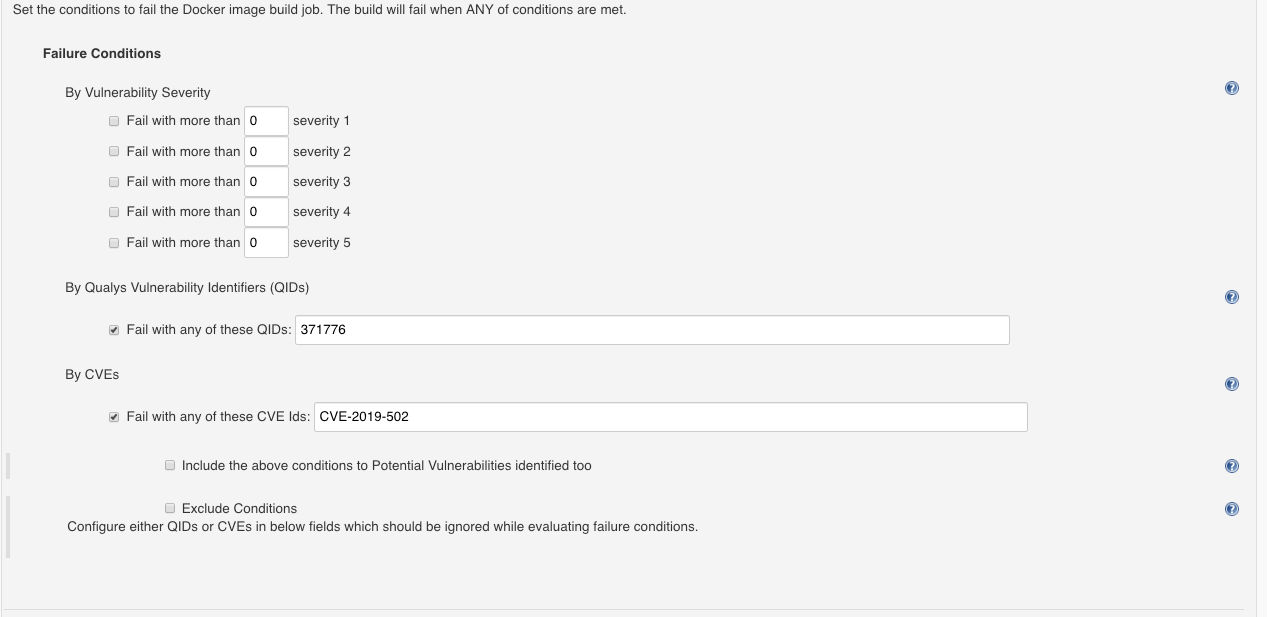
Detecting CVE-2019-5021 QID 371776 in your CI/CD Pipeline
If you are using Jenkins or Bamboo as your build tool, you can use the Qualys plugin to detect this vulnerability during your build process, and you could fail the build and then review the Qualys report to identify issues and remediation available on validation.
Detecting CVE-2019-5021 QID 371776 on your Docker Host
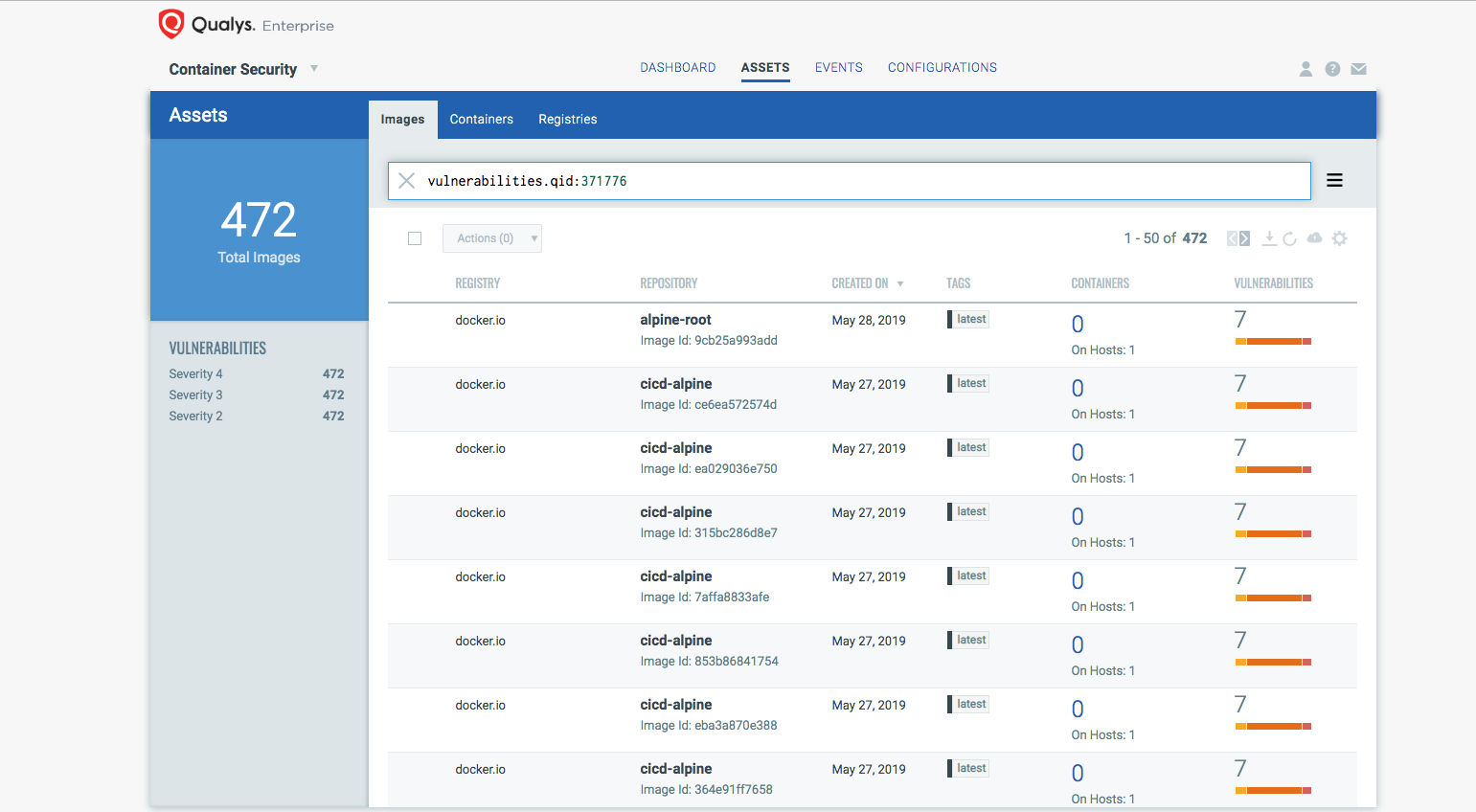
You can search for the QID or CVE to get a list of all the images and container affected by this :
- vulnerabilities.qid:371776
- vulnerabilities.cveids:CVE-2019-5021
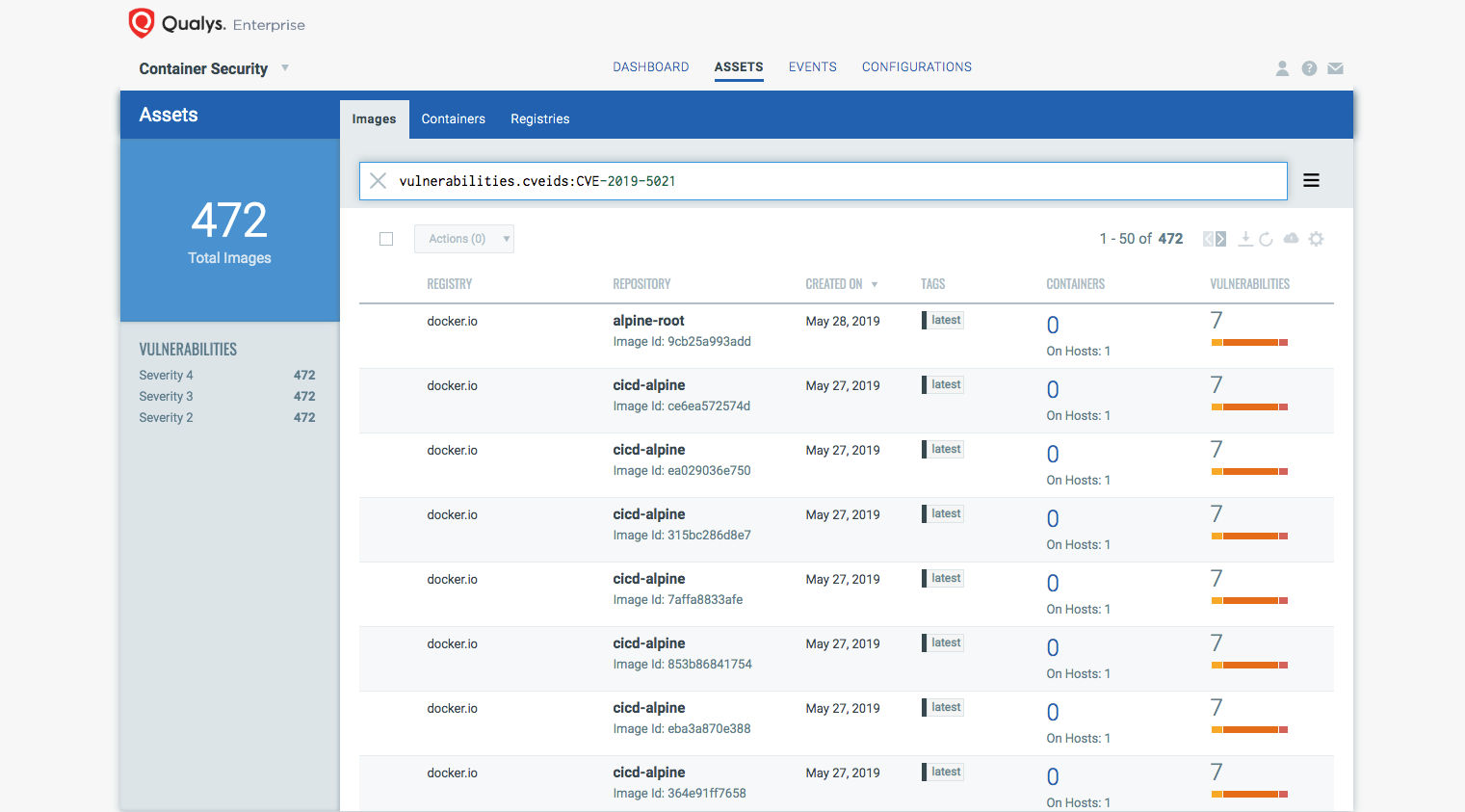
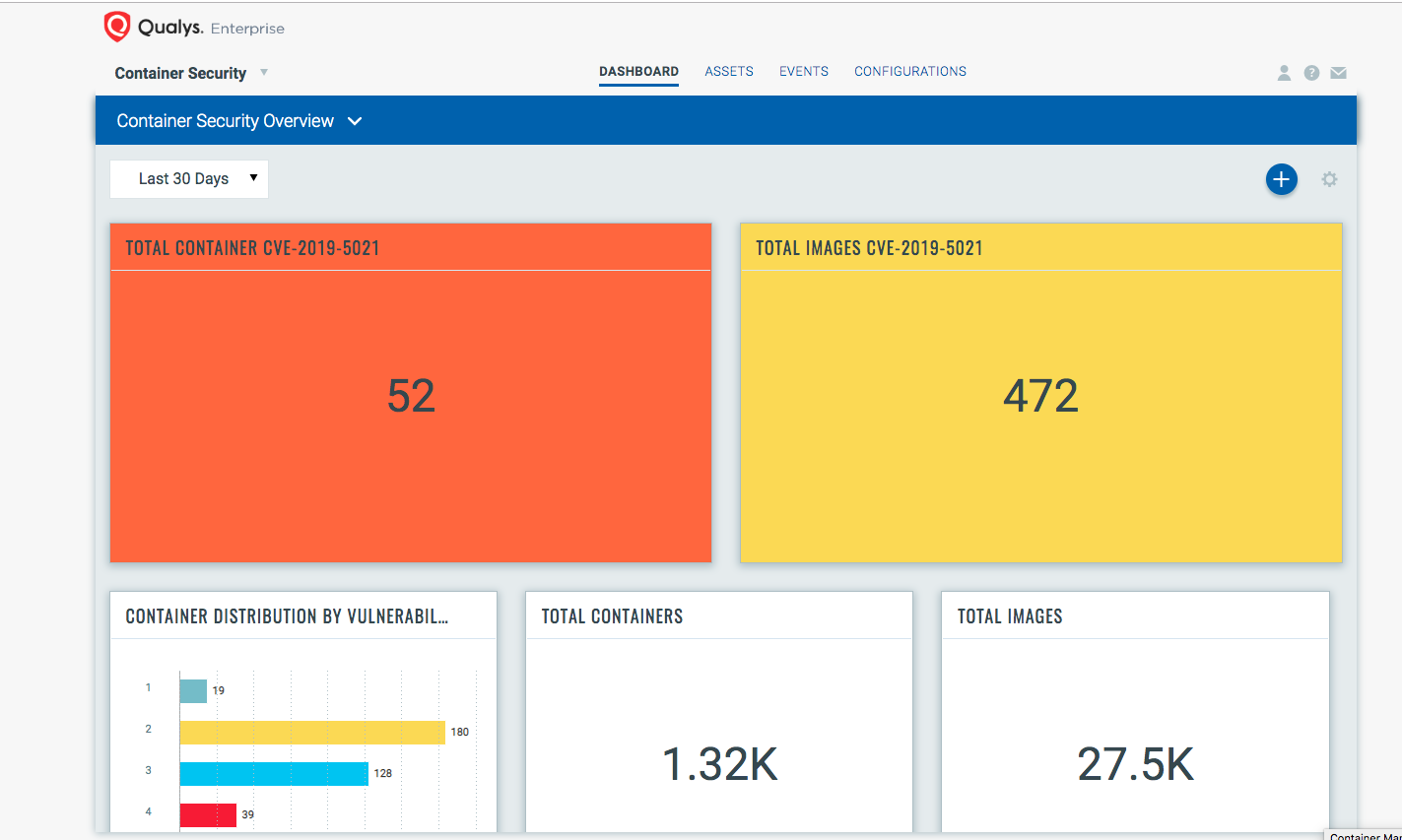
Qualys customers can use a Container Security dashboard to track this vulnerability across your images and containers.
Resources
- Refer to the Qualys Container Security User Guide for registry scanning and runtime protection.
- Discuss with your peers at Qualys Community.
Don’t have Qualys Container Security? Contact your Technical Account Manager to get a free trial, or sign up online.