Ripple20: Multiple Vulnerabilities Identified in Treck TCP/IP Stack

Multiple vulnerabilities that use a low-level TCP/IP software library developed by Treck, Inc. were identified recently in implementations of the Treck IP stack for embedded systems. These vulnerabilities were discovered by the JSOF research lab and have been named Ripple20.
Ripple20 Vulnerabilities
Ripple20 is a set of 19 vulnerabilities that affects hundreds of devices (or more) and include multiple remote code execution vulnerabilities.
Four of the Ripple20 vulnerabilities are critical (CVE-2020-11896, CVE-2020-11897, CVE-2020-11898, CVE-2020-11901 ), with CVSS scores over 9 and enable Remote Code Execution. One of the critical vulnerabilities is within the DNS protocol and potentially could be exploitable by a remote attacker, or even on devices that are not connected to the internet. The rest of the vulnerabilities have CVSS scores between 3.1 and 8.2, and can cause Denial of Service, Remote Code Execution or Disclosure of Sensitive Information.
Detecting Treck IP Stack Vulnerabilities with Qualys VM
Qualys has issued the information gathered (IG) QID 48106 to help customers track devices where Treck IP stacks are present. This QID can be detected via a remote unauthenticated scan using TCP/IP_Fingerprint as well as an ICMP probe.
QID 48106: Treck IP Stack Detected
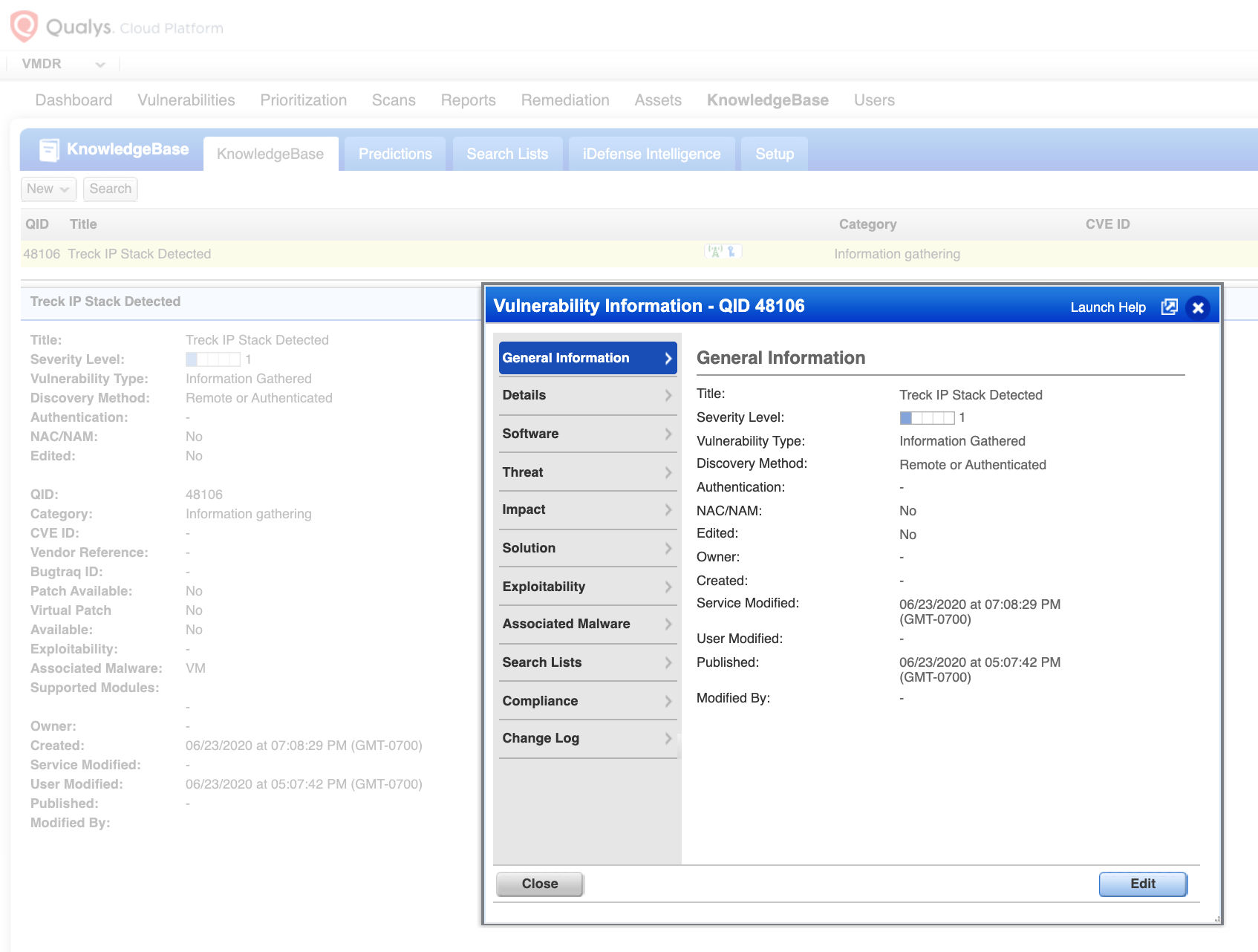
Along with the IG QID 48106, Qualys also released vulnerability QID 38789 that covers multiple CVEs – CVE-2020-11901, CVE-2020-11899, CVE-2020-11900, CVE-2020-11896, CVE-2020-11898, CVE-2020-11904, CVE-2020-11905, CVE-2020-11906, CVE-2020-11907, CVE-2020-11909, CVE-2020-11910, CVE-2020-11911, CVE-2020-11912, CVE-2020-11914 for HP Printers. This QID is included in signature version VULNSIGS-2.4.924-2 and above.
QID 38789 : Multiple HP Printers Network Stack Potential Vulnerabilities (Ripple20)
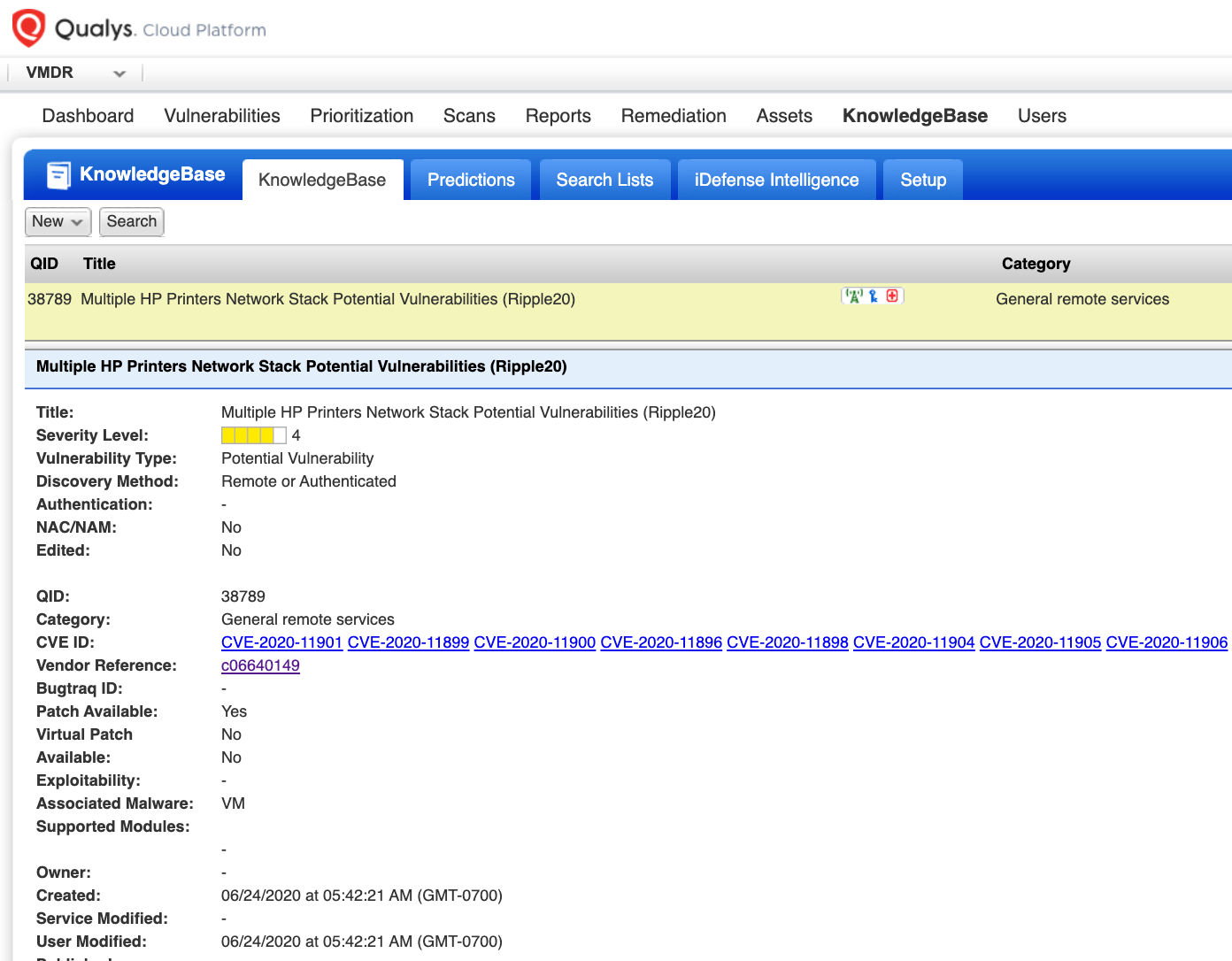
The patches are not available for all the vendors yet, however, HP has released patches for printers and Qualys QID 38789 can be leveraged to identify Treck networking stack vulnerabilities on HP printers.
Since the vulnerability affects a TCP/IP networking stack that is used by various vendors in their products, we have released the IG QID 48106 that can be leveraged by customers to identify a device running Treck networking stack and apply workarounds to mitigate the risk while the respective vendors release updates for their products. We are actively monitoring vendor updates for patch information and plan to release more QID checks, as and when more vendors publish their updates.
Qualys Threat Protection
Qualys customers can stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
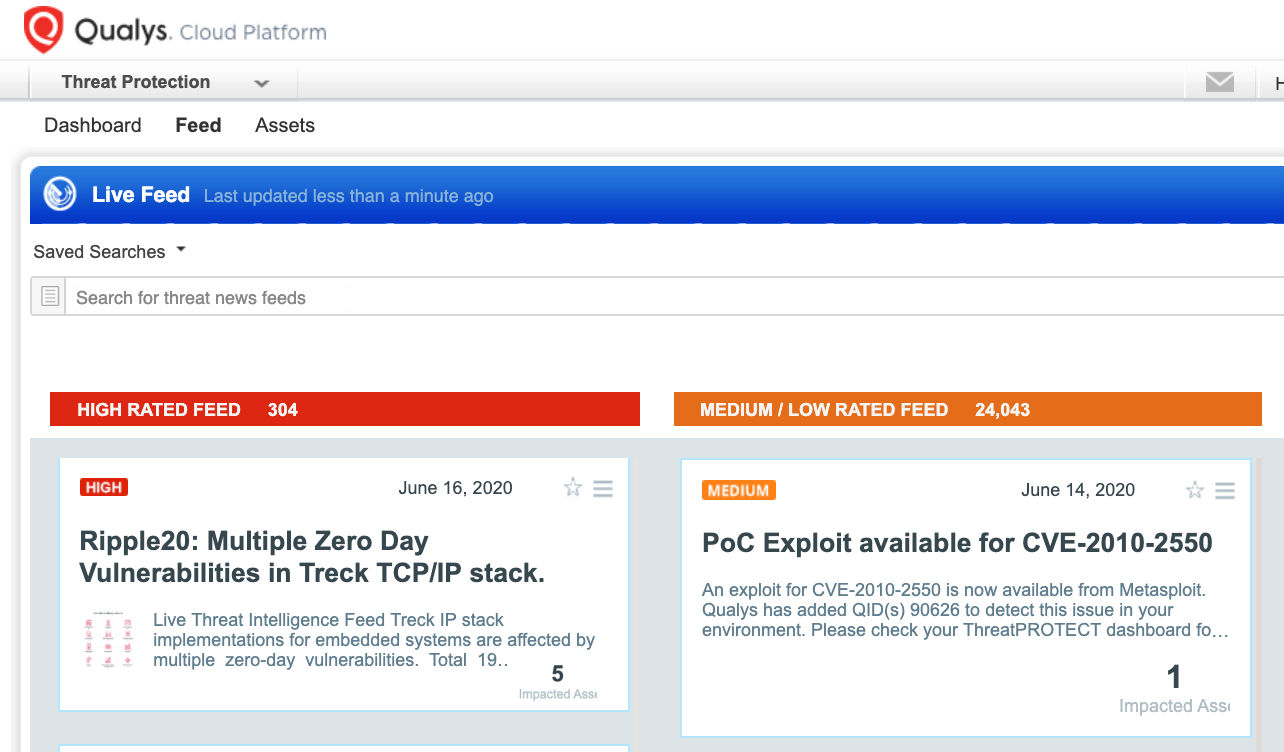
Simply click on the impacted assets number to see a list of hosts with this vulnerability.
Workaround
Treck released patches to address the Ripple20 vulnerabilities, but in some cases where it’s not possible to apply these patches, customers can apply these workarounds:
- Minimize network exposure for embedded and critical devices, keeping exposure to the minimum necessary, and ensure that devices are not accessible from the Internet unless essential.
- Segregate OT networks and devices behind firewalls and isolate them from the business network.
- Enable only secure remote access methods.
- Block network attacks via deep packet inspection, similar to how modern switches, routers, and firewalls drop malformed packets with no additional configuration.
Further mitigation for operators and networks or for device vendors are available on Github and Ripple20.
We would like to thank JSOF research team for their cooperation and for providing necessary information about the vulnerabilities to the Qualys Research team.
Customers are encouraged to use IG QID 48106 to identify the presence of Treck networking stack on their devices. For HP Printers, use QID 38789 to identify the presence of Ripple20.