Microsoft Netlogon Vulnerability (CVE-2020-1472 – Zerologon) – Automatically Discover, Prioritize and Remediate Using Qualys VMDR®

Update October 1, 2020: Microsoft has added step-by-step Zerologon patching instructions because the original instructions “proved confusing to users and may have caused issues with other business operations.”
Update October 1, 2020: Qualys released new QID 91680 to add a remote (unauthenticated) check for the Zerologon vulnerability. The update is included in VULNSIGS-2.4.998-3 and later.
QID 91680 : Microsoft Windows Netlogon Elevation of Privilege Vulnerability (unauthenticated check)
Update Sept 24, 2020: Microsoft is detecting active attacks leveraging the Zerologon vulnerability. Security teams are advised to patch vulnerable systems immediately.
On Sept 11, 2020, A Dutch team, collectively known as Secura, published an exploit on how an unauthenticated remote user can take control over the domain controller and leverage admin privileges. The vulnerability (CVE-2020-1472) received the maximum severity rating score of 10.0 based on CVSS v3 Scoring system.
The prime elements of this vulnerability are the weak encryption standards and the authentication process used in the Netlogon protocol. As new Windows Domain Controllers use standard AES-256 as encryption standards, incorrect use of the AES mode results in spoofing the identity of any computer (DC) account and replace it with all zeroes or empty passwords. As the final output replaces all characters of the password with zeroes, this bug is also well-known as “Zerologon”.
Affected Products
- Windows Servers 2008
- Windows Servers 2012 R2
- Windows Servers 2016
- Windows Servers 2019
A complete list of affected devices is available on Microsoft’s August 2020 security advisory.
Identification of Assets using Qualys VMDR
The first step in managing vulnerabilities and reducing risk is identification of assets. Qualys VMDR makes it easy to identify Windows systems.
(operatingSystem.category1:`Windows` and operatingSystem.category2:`Server`)
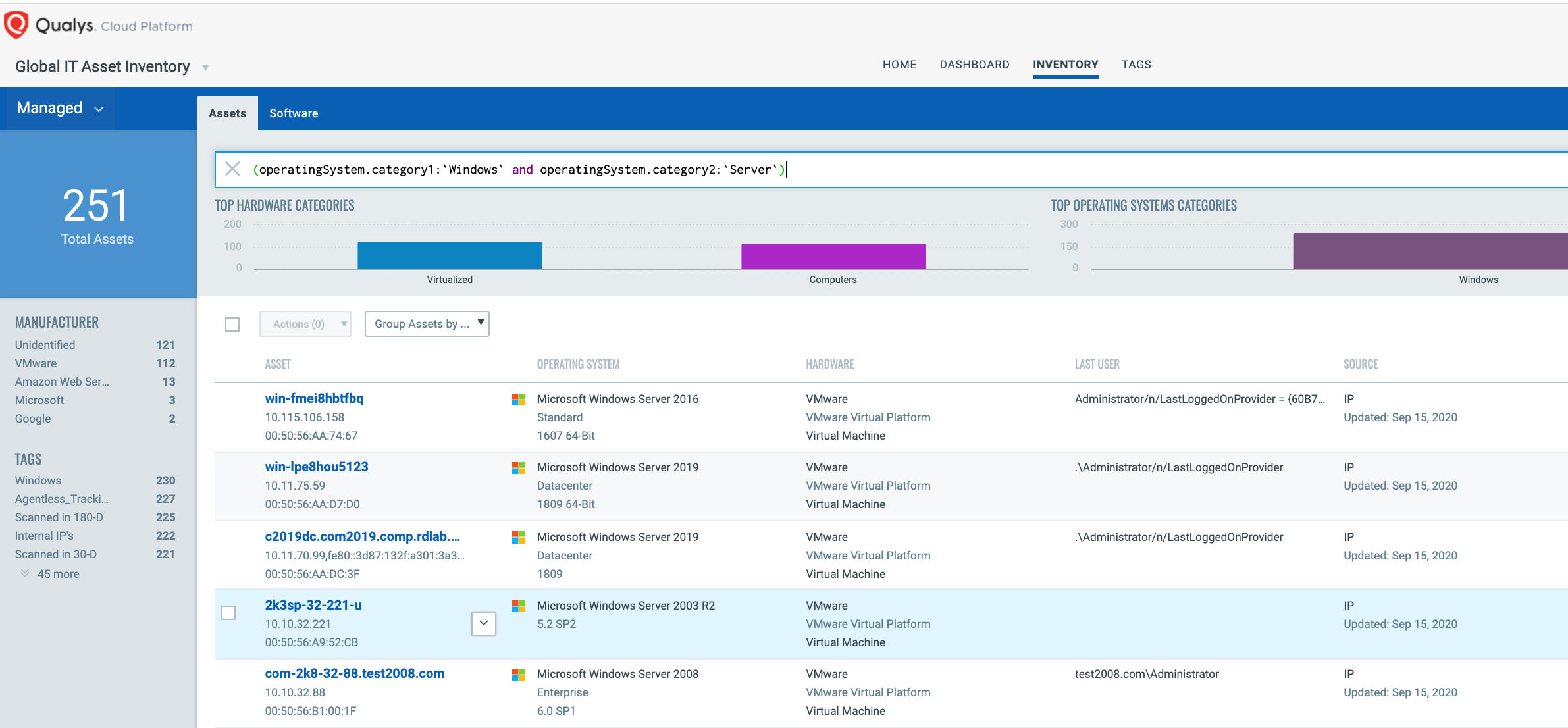
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, let’s say – “Zerologon”. This helps in automatically grouping existing hosts with Zerologon as well as any new Windows server that spins up in your environment. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
Discover Zerologon “CVE-2020-1472” Vulnerability
Now that hosts with Zerologon are identified, you want to detect which of these assets have flagged this vulnerability. VMDR automatically detects new vulnerabilities like Zerologon based on the always updated Knowledgebase.
You can see all your impacted hosts for this vulnerability tagged with the ‘Zerologon’ asset tag in the vulnerabilities view by using this QQL query:
vulnerabilities.vulnerability.qid:91668
OR you could modify your search to :
Vulnerability - vulnerabilities.vulnerability.qid:91668
Asset - (operatingSystem.category1:`Windows` and operatingSystem.category2:`Server`)
This will return a list of all impacted hosts.
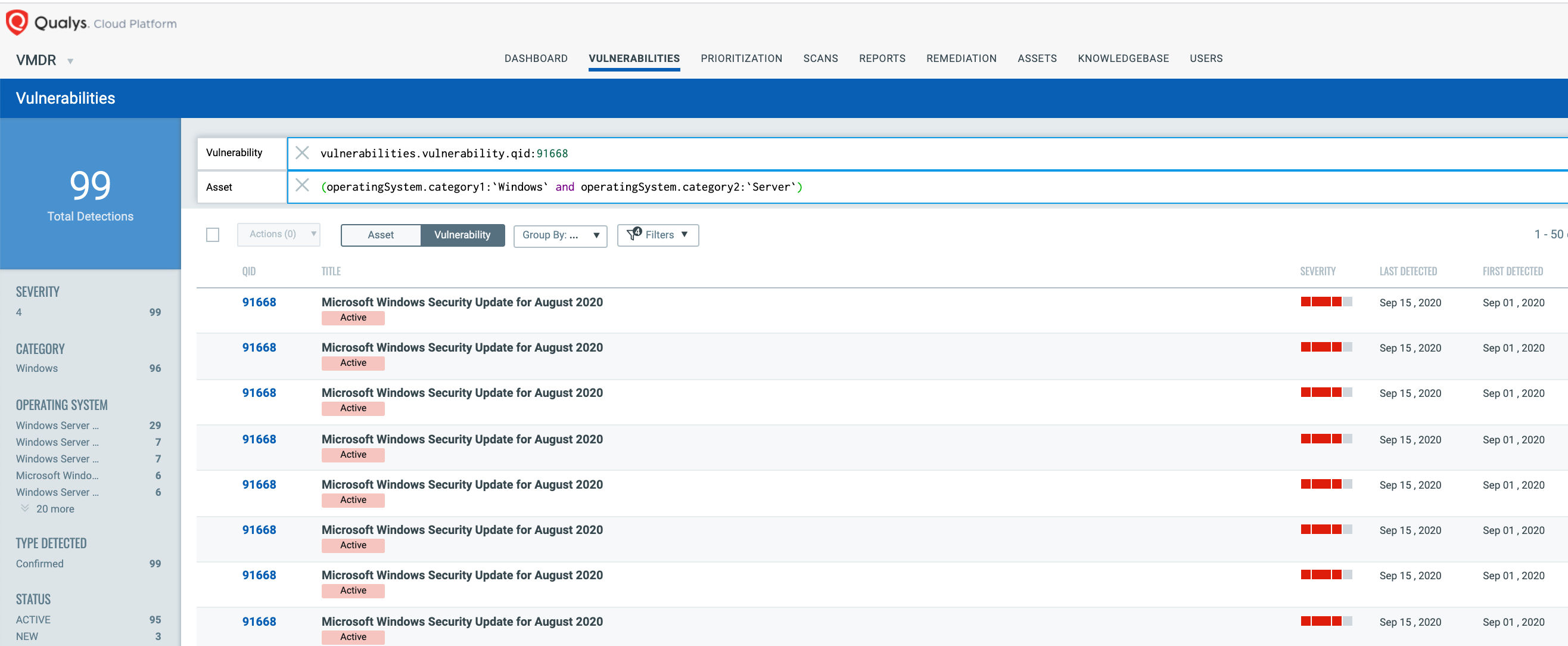
QID 91668 is available in signature version VULNSIGS-2.4.958-3 and above and can be detected using authenticated scanning or the Qualys Cloud Agent manifest version 2.4.958.3-2 and above.
Along with the QID 91668, Qualys released the following IG QID 45461 to help customers track domain controller assets on which netlogon secure channel mode is enabled. This QID can be detected using authenticated scanning using VULNSIGS-2.4.986-3 and above or the Qualys Cloud Agent manifest version 2.4.986.3-2 and above.
QID 45461 : Microsoft Windows Domain Controller Netlogon Secure Channel Enforcement Mode Enabled
Update October 1, 2020: Qualys released new QID 91680 to add a remote (unauthenticated) check for the Zerologon vulnerability. The update is included in VULNSIGS-2.4.998-3 and later.
QID 91680 : Microsoft Windows Netlogon Elevation of Privilege Vulnerability (unauthenticated check)
Please Note: We have tested the QID across Qualys lab environment on a variety of Windows versions, and we have not observed any issues. In case you experience issues with the remote detection, please reach out to Qualys Support for immediate attention.
Using VMDR, the Zerologon vulnerability can be prioritized for the following real-time threat indicators (RTIs):
- Remote Code Execution
- Privilege Escalation
- Exploit Public
- Active Attack
- Denial of Service
- High Data Loss
- High Lateral Movement
- Predicted High Risk

VMDR also enables you to stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
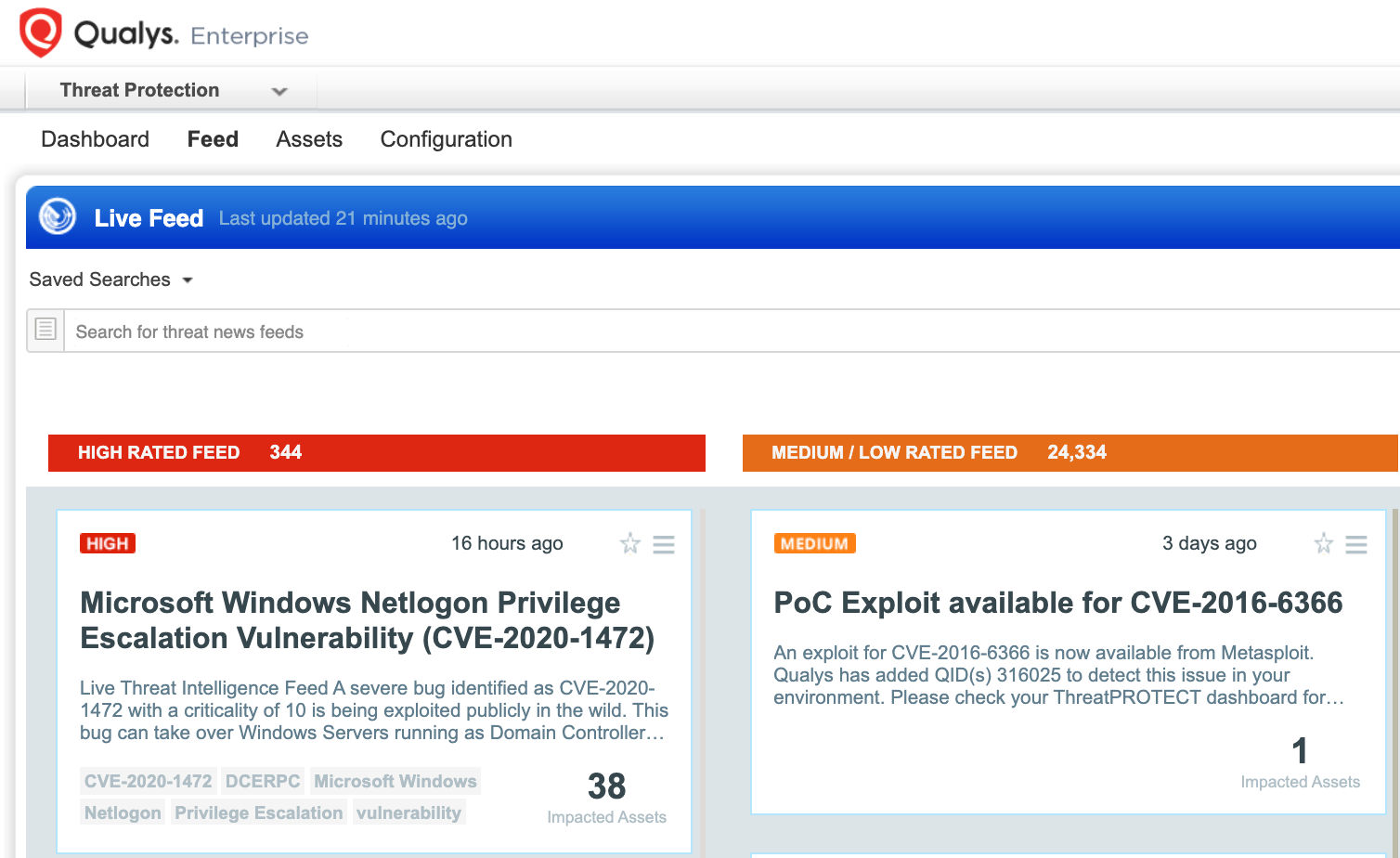
Simply click on the impacted assets for the Zerologon threat feed to see the vulnerability and impacted host details.
With VMDR Dashboard, you can track Zerologon, impacted hosts, their status and overall management in real-time. With trending enabled for dashboard widgets, you can keep track of Zerologon vulnerability trends in your environment using Zerologon Dashboard Link.
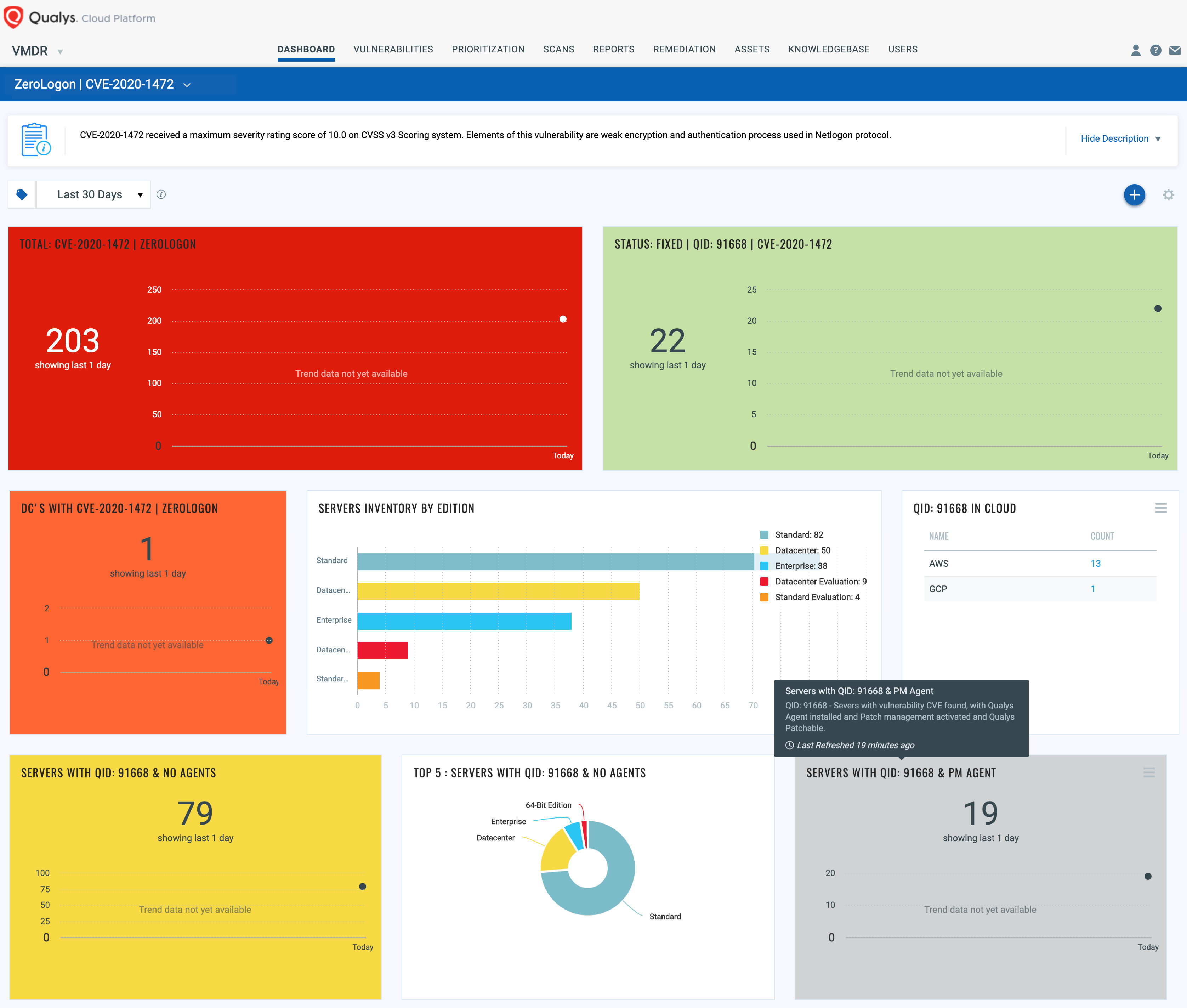
Response by Patching and Remediation
VMDR rapidly remediates the Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select “qid: 91668” in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go for hosts grouped together by a tag – Zerologon.
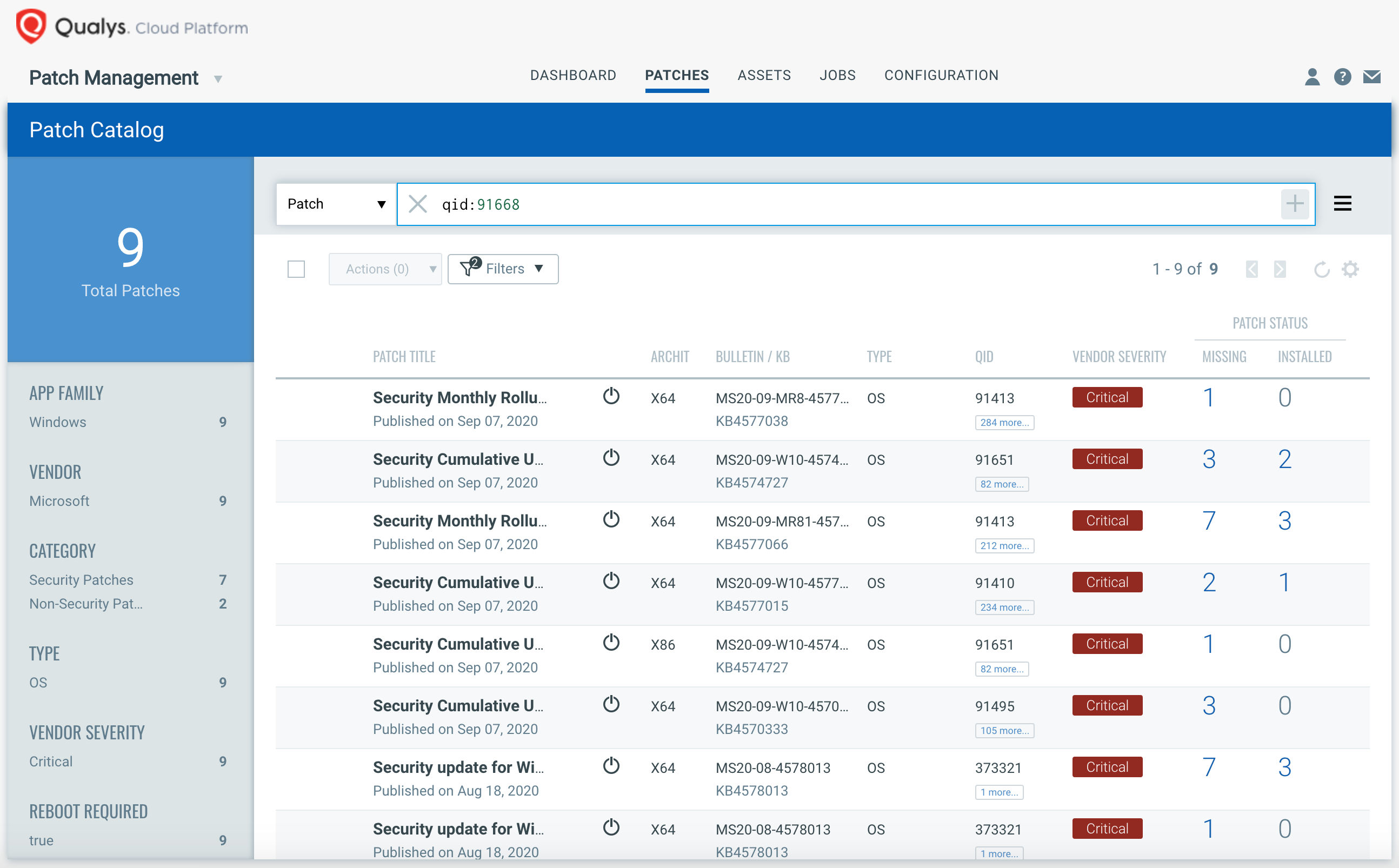
For proactive, continuous patching, you can create a job without a Patch Window to ensure all hosts will continue to receive the required patches as new patches become available for emerging vulnerabilities.
Users are encouraged to apply patches as soon as possible.
Solution
Users are advised to review their Microsoft Windows installations with Microsoft’s August 2020 security advisory mentioned above. For Windows devices, a patch to be published in Feb 2021 would place Domain controllers in enforcement mode; to explicitly allow the account by adding an exception for any non-compliant device.
Get Started Now
Start your Qualys VMDR trial for automatically identifying, detecting and patching the high-priority Zerologon vulnerability CVE-2020-1472.
References
https://www.secura.com/pathtoimg.php?id=2055
https://github.com/SecuraBV/CVE-2020-1472
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1472
Hey There,
Is it only on Windows Domain controllers or application to all Windows servers.
“a patch to be published in Feb 2021 would disable the “enforcement mode” by default.” – please correct the sentence, it will enable, not disable the enforcement mode.
This has been corrected.
Hi Animesh , thanks for sharing good information. we only found summary on Qualys. but as per Qualys KB , Linux OS are also affected due to CVE-2020-1472 vulnerability. Can you pl make provide more information on that and update dashboard accordingly.
Hi,
Do you have similar article for Samba Netlogon vulnerability? Does qualys released QID to detect the vulnerability?
This QID is completely useless in detecting Zerologon – it detects all windows servers laptops and desktops in your environment that are missing the Aug 2020 Microsoft path – Zerologon only affects Domain Controller so the Qualys VM saying you have Zerologon on a desktop, laptop or on any server that is not a domain Controller makes this QID completely useless in detecting Zerologon. Even with the additional selectors to look only for servers, since not all servers are affected but only DC’s it’s still useless.