Discover A10 Networks Advanced Core OS Vulnerabilities using Qualys VMDR

Last updated on: October 15, 2020
The Qualys vulnerability signatures team has released a new series of signatures (detections) for A10 Networks ACOS (Advanced Core Operating System), allowing security teams to identify A10 hosts and detect their vulnerabilities.
A10 Advanced Core Operating System with true Scalable Symmetrical Multi-Processing (SSMP) provides flexible application delivery platforms optimized for high-performance. A10 ACOS allows software capabilities to be addressed by APIs, allowing these devices to work with any standards-based infrastructure.
The newly released set of signatures (QIDs) covers the most recent A10 ACOS advisories. Qualys plans to release more QIDs covering the rest of the A10 advisories and will add QIDs for upcoming advisories on an ongoing basis.
Security teams should use Qualys Vulnerability Management, Detection and Response (VMDR) to discover, assess, prioritize, and patch critical vulnerabilities in real time, including A10 Network ACOS, as part of your security and compliance programs.
Identify A10 Assets & Vulnerabilities
Qualys VMDR enables easy identification of A10 Advanced Core OS systems:
operatingSystem: "A10"
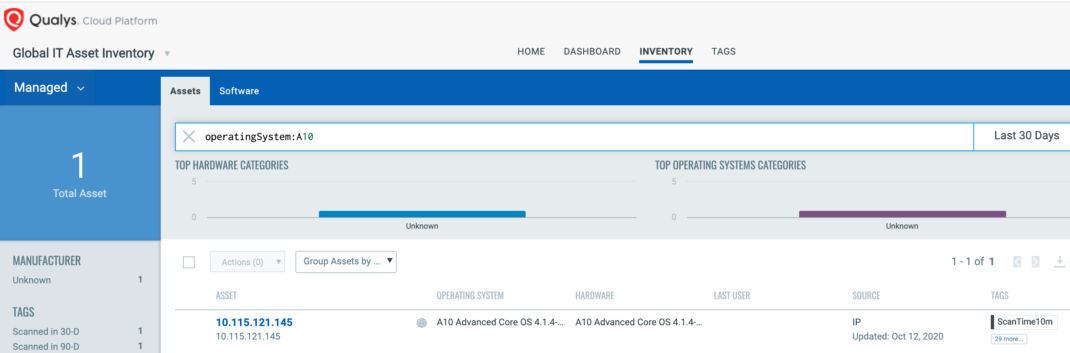
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, let’s say – “A10”. This helps in automatically grouping existing A10 hosts as well as any new host that spins up in your environment. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
In order to identify A10 Advanced Core OS hosts and detect their vulnerabilities, Qualys recommends running an authenticated scan using a Qualys scanner.
A10 QIDs are included in signature version 2.5.4-1 and above.
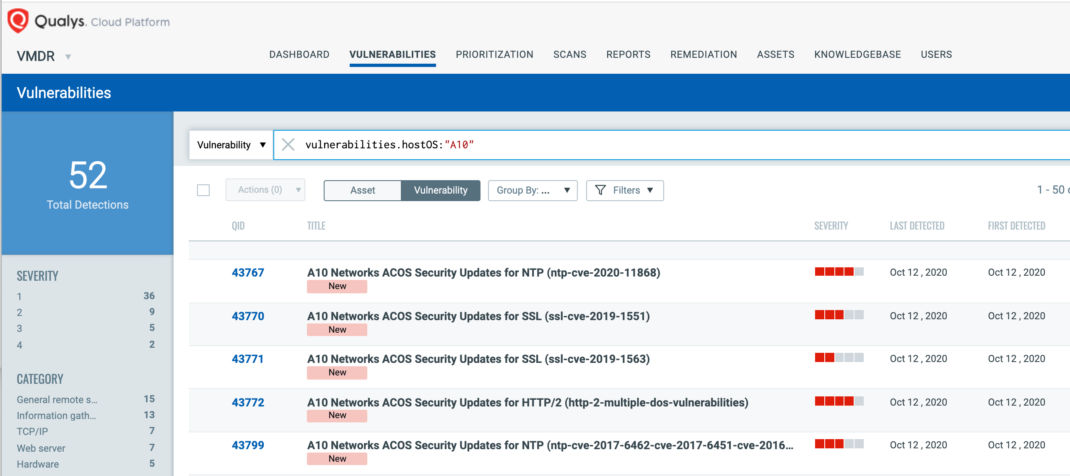
Customers can search for all A10 Advanced Core OS vulnerabilities using the following QQL query :
vulnerabilities.hostOS:”A10″
Configure Unix Authentication Record
Authenticated scanning should be configured via a standard Unix auth record, which is similar to auth records for other Linux OSes, like Redhat, Ubuntu, and others.
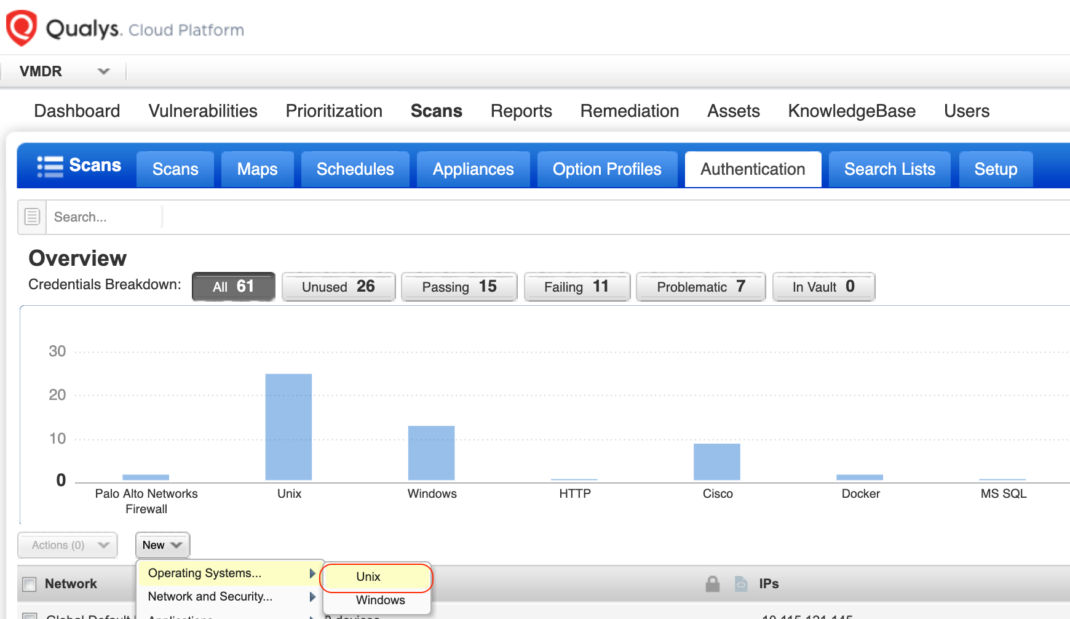
As seen below, simply go to :
Scans -> Authentication -> New -> Operating System -> Unix
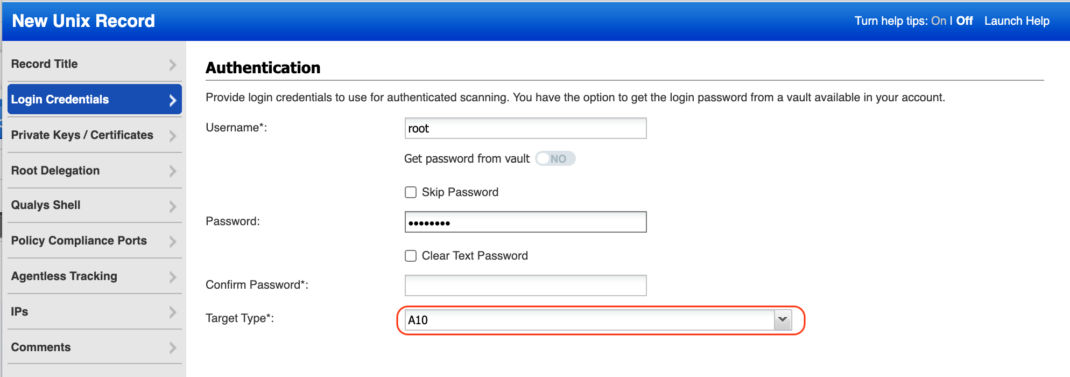
Enter the Unix login credentials (user name, password) that the Qualys service should use to log in to A10 hosts at scan time. Target Type is “A10” for A10 ACOS Network Devices. Online help is always available to assist you.
Scan A10 Network Hosts
Scanning for A10 ACOS vulnerabilities does not require root privileges; however, the account must be able to perform the following command:
1) execute “show version” to identify OS, version information
2) Requires “Read” privileges, and “cli” access
Scan reports identify A10 ACOS as:
Qualys VMDR automatically detects new A10 Advanced Core OS vulnerabilities as their associated detections (QIDs) are added to the KnowledgeBase. As with all detections, A10 QIDs contain recommended steps to address the vulnerability.