21Nails: Multiple Critical Vulnerabilities in Exim Mail Server
Update May 7, 2021: Exim has released a security update to address multiple vulnerabilities in Exim versions prior to 4.94.2. See the CISA announcement.
Original Post: The Qualys Research Team has discovered multiple critical vulnerabilities in the Exim mail server, some of the which can be chained together to obtain full remote unauthenticated code execution and gain root privileges. Qualys recommends security teams to apply patches for these vulnerabilities as soon as possible.
About Exim
Exim is a popular mail transfer agent (MTA) available for major Unix-like operating systems and comes pre-installed on Linux distributions such as Debian. According to a recent survey, an estimated 60% of internet servers run on Exim. A Shodan search reveals nearly 4 million Exim servers are exposed to the internet.
Mail Transfer Agents are interesting targets for attackers because they are usually accessible over the internet. Once exploited, they could modify sensitive email settings on the mail servers, allow adversaries to create new accounts on the target mail servers. Last year, the vulnerability in the Exim Mail Transfer Agent (MTA) was a target of Russian cyber actors formally known as the sandworm team.
Exim Vulnerabilities

Last fall, the Qualys Research Team engaged in a thorough code audit of Exim and discovered 21 unique vulnerabilities. Ten of these vulnerabilities can be exploited remotely. Some of them leading to provide root privileges on the remote system. And eleven can be exploited locally with most of them can be exploited in either default configuration or in a very common configuration. Some of the vulnerabilities can be chained together to obtain a full remote unauthenticated code execution and gain root privileges on the Exim Server. Most of the vulnerabilities discovered by the Qualys Research Team for e.g. CVE-2020-28017 affects all versions of Exim going back all the way to 2004 (going back to the beginning of its Git history 17 years ago).
Proof of Concept
Vulnerability Summary
| CVE | Description | Type |
|---|---|---|
| CVE-2020-28007 | Link attack in Exim’s log directory | Local |
| CVE-2020-28008 | Assorted attacks in Exim’s spool directory | Local |
| CVE-2020-28014 | Arbitrary file creation and clobbering | Local |
| CVE-2021-27216 | Arbitrary file deletion | Local |
| CVE-2020-28011 | Heap buffer overflow in queue_run() | Local |
| CVE-2020-28010 | Heap out-of-bounds write in main() | Local |
| CVE-2020-28013 | Heap buffer overflow in parse_fix_phrase() | Local |
| CVE-2020-28016 | Heap out-of-bounds write in parse_fix_phrase() | Local |
| CVE-2020-28015 | New-line injection into spool header file (local) | Local |
| CVE-2020-28012 | Missing close-on-exec flag for privileged pipe | Local |
| CVE-2020-28009 | Integer overflow in get_stdinput() | Local |
| CVE-2020-28017 | Integer overflow in receive_add_recipient() | Remote |
| CVE-2020-28020 | Integer overflow in receive_msg() | Remote |
| CVE-2020-28023 | Out-of-bounds read in smtp_setup_msg() | Remote |
| CVE-2020-28021 | New-line injection into spool header file (remote) | Remote |
| CVE-2020-28022 | Heap out-of-bounds read and write in extract_option() | Remote |
| CVE-2020-28026 | Line truncation and injection in spool_read_header() | Remote |
| CVE-2020-28019 | Failure to reset function pointer after BDAT error | Remote |
| CVE-2020-28024 | Heap buffer underflow in smtp_ungetc() | Remote |
| CVE-2020-28018 | Use-after-free in tls-openssl.c | Remote |
| CVE-2020-28025 | Heap out-of-bounds read in pdkim_finish_bodyhash() | Remote |
Successful exploitation of these vulnerabilities would allow a remote attacker to gain full root privileges on the target server and execute commands to install programs, modify data, and create new accounts. Qualys security researchers independently verified these vulnerabilities and developed exploits to obtain full root privileges.
As soon as the Qualys Research Team confirmed the vulnerabilities, Qualys engaged in responsible vulnerability disclosure and coordinated with Exim developers and open-source distributions to announce the vulnerability. See Disclosure Timeline.
Technical Details
The technical details of all 21 vulnerabilities can be found on Qualys Security Advisories or at: https://www.qualys.com/2021/05/04/21nails/21nails.txt
Qualys Coverage
Given the breadth of the attack surface for this vulnerability, Qualys recommends users apply patches for this vulnerability immediately. Qualys customers can search the vulnerability knowledgebase for “21Nails” to identify all the QIDs and assets vulnerable for this vulnerability.
Qualys is releasing the QIDs in the table below as they become available starting with vulnsigs version VULNSIGS-2.5.174-2 and Linux Cloud Agent manifest version lx_manifest-2.5.174.2-1.
| QID | Title | VulnSigs Version |
|---|---|---|
| 50110 | Exim Mail Server Multiple Vulnerabilities (21Nails) | VULNSIGS-2_5_174-2 / lx_manifest-2.5.174.2-1 |
| 178576 | Debian Security Update for exim4 (DSA 4912-1) (21Nails) | VULNSIGS-2_5_177-2 / lx_manifest-2.5.177.2-1 |
| 198350 | Ubuntu Security Notification for Exim4 Vulnerabilities (USN-4934-1) (21Nails) | VULNSIGS-2_5_177-2 / lx_manifest-2.5.177.2-1 |
Discover Vulnerable Exim Servers Using Qualys VMDR
Identify Assets Running Exim
The first step in managing these critical vulnerabilities and reducing risk is identification of assets running Exim software. Qualys VMDR makes it easy to identify such assets.
Query: software:(name:"Exim")
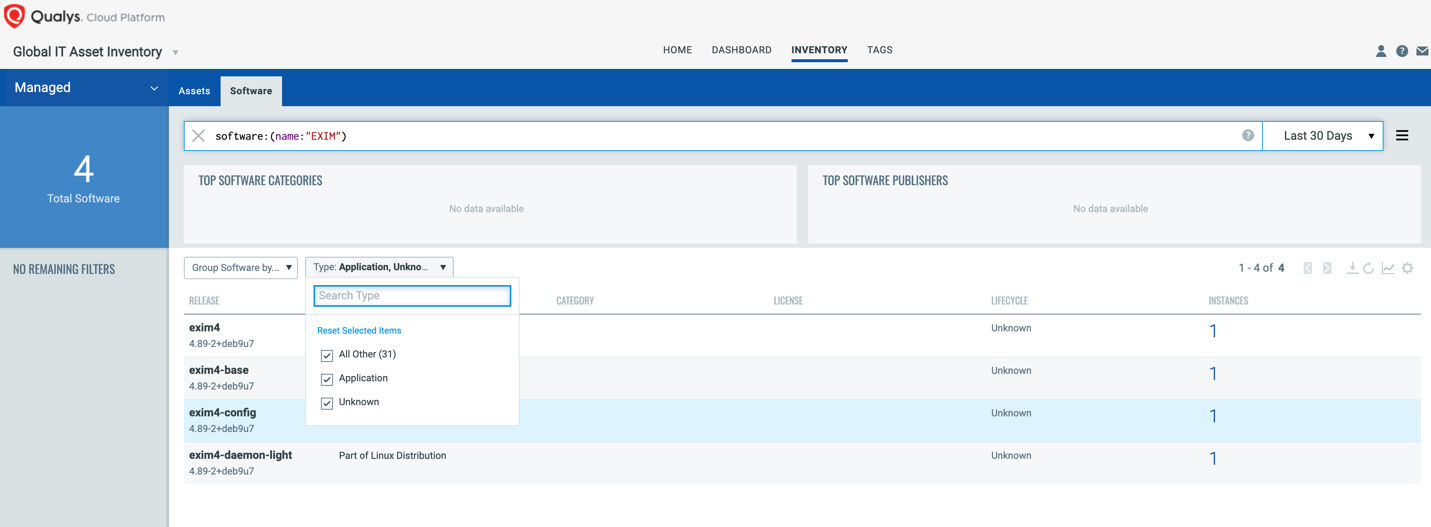
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, let’s say – “Exim Assets”. This helps in automatically grouping existing hosts with the above vulnerabilities as well as any new Exim-based assets that spin up in your environment. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
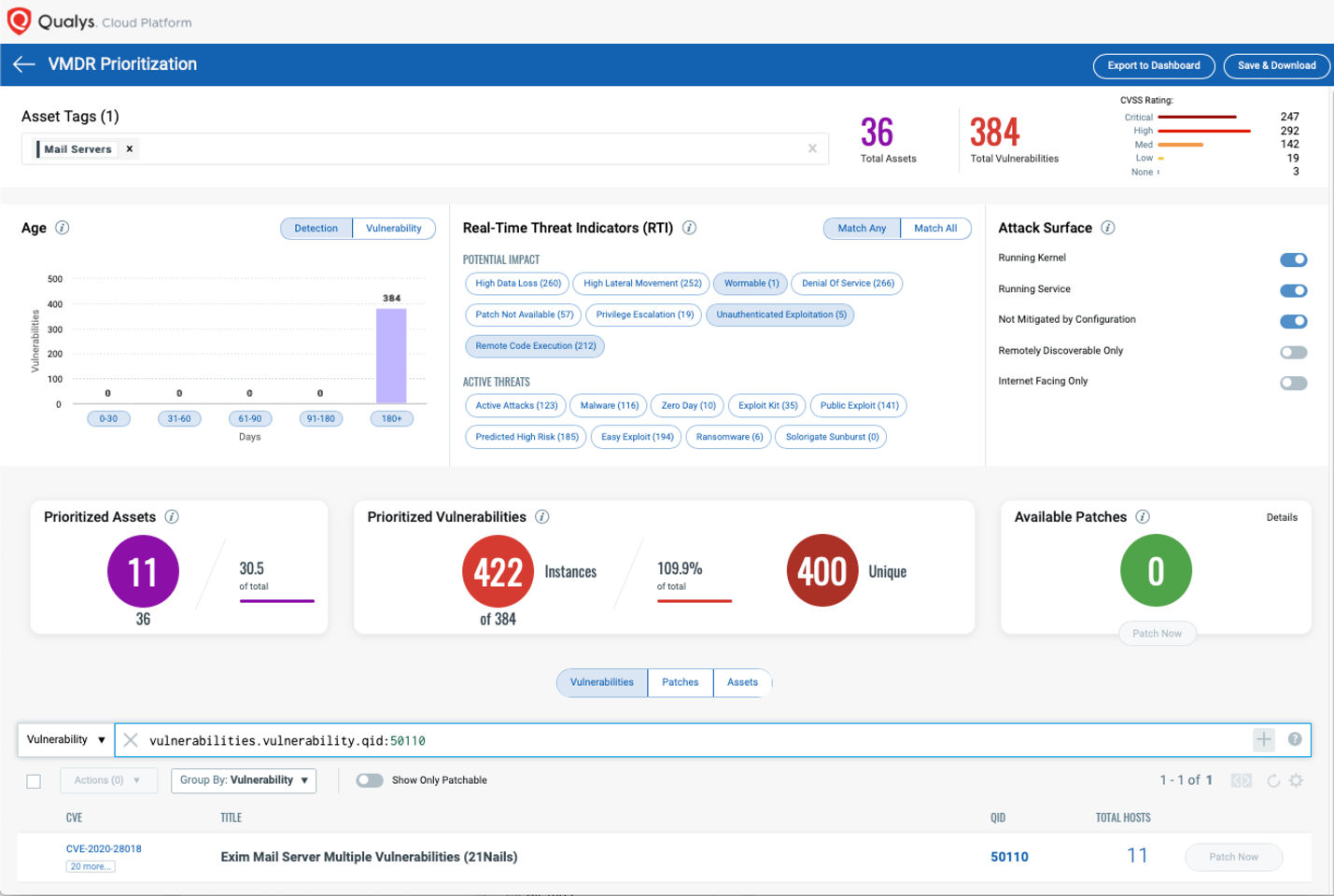
Prioritize Based on RTIs
Using VMDR, the Exim vulnerabilities can be prioritized using the following real-time threat indicators (RTIs):
- Predicted_High_Risk
- Wormable
- Remote_Code_Execution
- Privilege_Escalation
- Unauthenticated_Exploitation
- High_Lateral_Movement
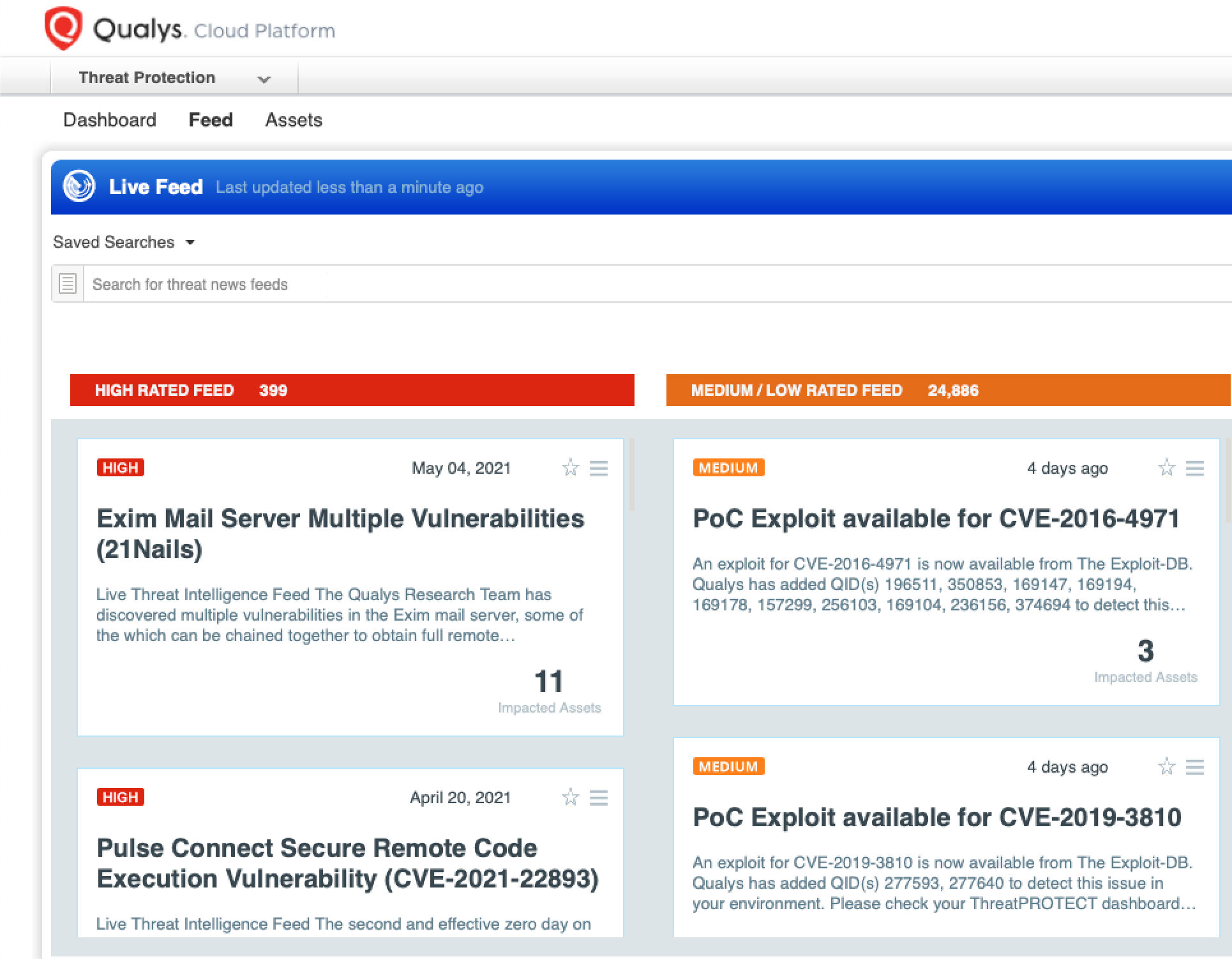
Detect Impacted Assets with Threat Protection
VMDR also enables you to automatically map assets vulnerable to these vulnerabilities using Threat Protection.
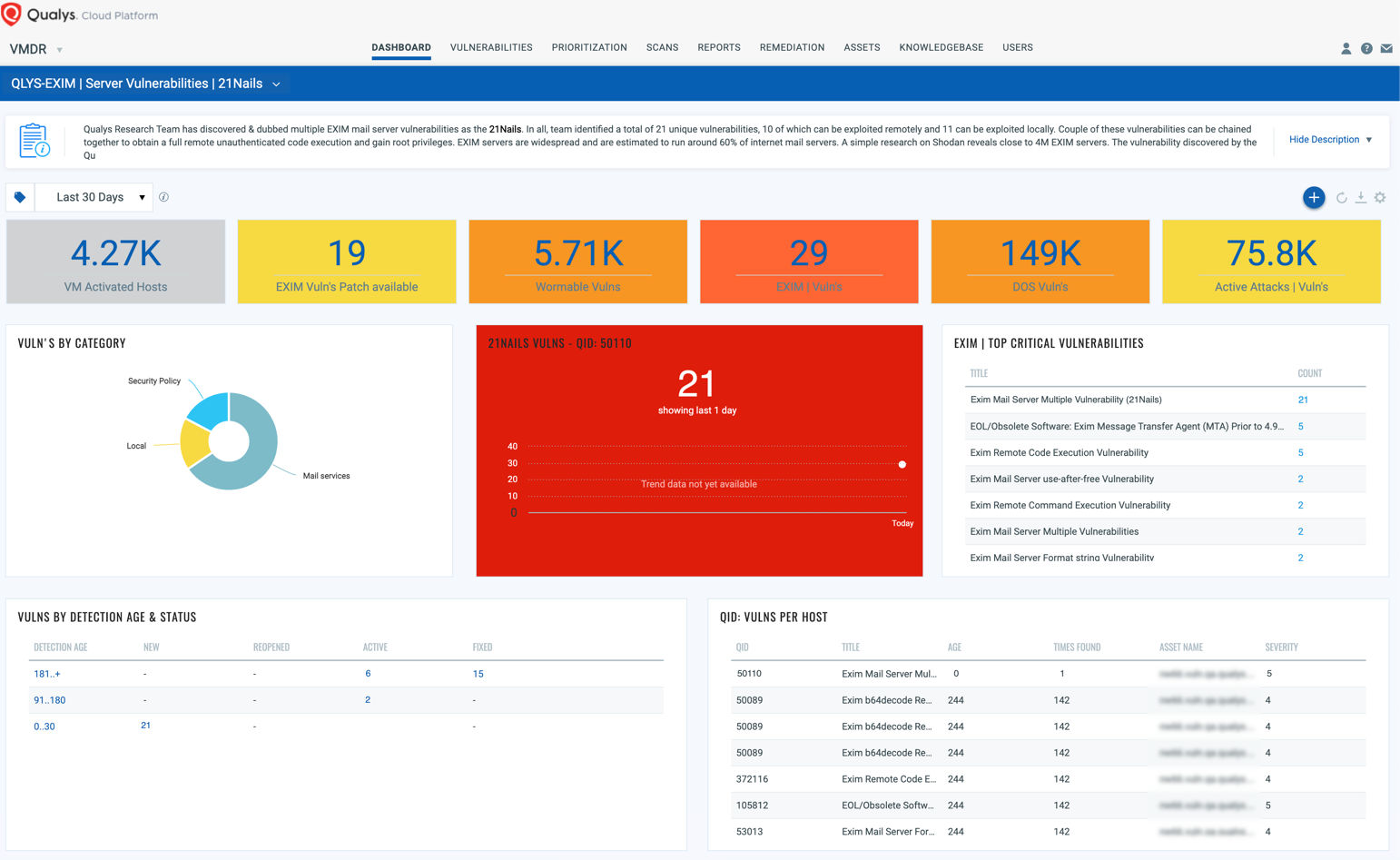
Dashboard
With VMDR Dashboard, you can track this vulnerability, their impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of these vulnerabilities trends in your environment using the “21Nails” Dashboard.
View and download the “21Nails” dashboard here:
Free 30-Day VMDR Service
To help security teams assess and mitigate their risk exposure to the Exim vulnerabilities (21Nails), Qualys is offering an integrated VMDR service free for 30 days to identify vulnerable assets.
Disclosure Timeline
2020-10-20: The Qualys Research Team (QRT) informed Exim (security@exim) about the new vulnerabilities.
2020-10-28: QRT shared the first draft of the advisory. The vendor immediately acknowledged and started to work on patches.
2020-10-29: QRT sent a list of 10 secondary issues to Exim.
2020-10-30: QRT requested 20 CVEs from Mitre. They were assigned on the same day and immediately transmitted to Exim.
2020-11-13: Exim gave QRT read access to their private Git repository to review patches. We started reviewing first set of patches (which tackled 7 CVEs).
2020-11-17 and 2020-11-18: QRT sent a two-part patch review to Exim since several patches were incomplete.
2020-12-02: A second set of patches (which tackled 7 secondary issues) appeared in Exim’s private Git repository. We started reviewing it.
2020-12-09: We sent our second patch review to Exim.
2021-01-28: We mailed Exim and offered to work on the incomplete and missing patches.
2021-02-05: Exim acknowledged our mail. We started to write a minimal but complete set of patches (on top of exim-4.94+fixes).
2021-02-15: While working on a patch for CVE-2020-28014, we discovered CVE-2021-27216. We requested a CVE from Mitre, and immediately sent a heads-up to Exim.
2021-02-24: We completed our minimal set of patches and sent it to Exim.
2021-04-17: Exim proposed 2021-05-04 for the Coordinated Release Date.
2021-04-19: We accepted the proposed Coordinated Release Date.
2021-04-21: Exim publicly announced the impending security release.
2021-04-27: Exim provided packagers and maintainers with access to its security Git repository.
2021-05-04: Coordinated Release Date.
As you can see from the disclosure timeline, it was a long process from when the vulnerabilities were first discovered and reported to the point patches were available for these vulnerabilities. All in all, the Qualys Research Team helped report these vulnerabilities and provide 26 patches. A testament to our commitment to responsible disclosure.
Vendor References
https://www.openwall.com/lists/oss-security/2021/05/04/6
https://www.qualys.com/2021/05/04/21nails/21nails.txt
https://www.exim.org/static/doc/security/CVE-2020-qualys/
Frequently Asked Questions (FAQs)
What versions are vulnerable?
All versions before Exim-4.94.2 are vulnerable.
Why name the vulnerability “21Nails”?
It’s a pun on 21 vulnerabilities in a “Mail” transfer agent. With each nail representing one vulnerability.
Will the Qualys Research Team publish exploit code for this vulnerability?
No.
How do we mitigate this vulnerability ?