How Malware Employs Anti-Debugging, Anti-Disassembly and Anti-Virtualization Technologies
Last week at Black Hat USA 2012, we published the first results of an ongoing security research project called Dissect || PE in our session titled "A Scientific (but Non-Academic) Study of How Malware Employs Anti-Debugging, Anti-Disassembly and Anti-Virtualization Technologies".
Dissect || PE is founded on a database of 30 million current malware samples and offers both static (i.e. scanning of the malware’s code) and dynamic (i.e. running of the malware under observation) analysis engines.
Static Analysis
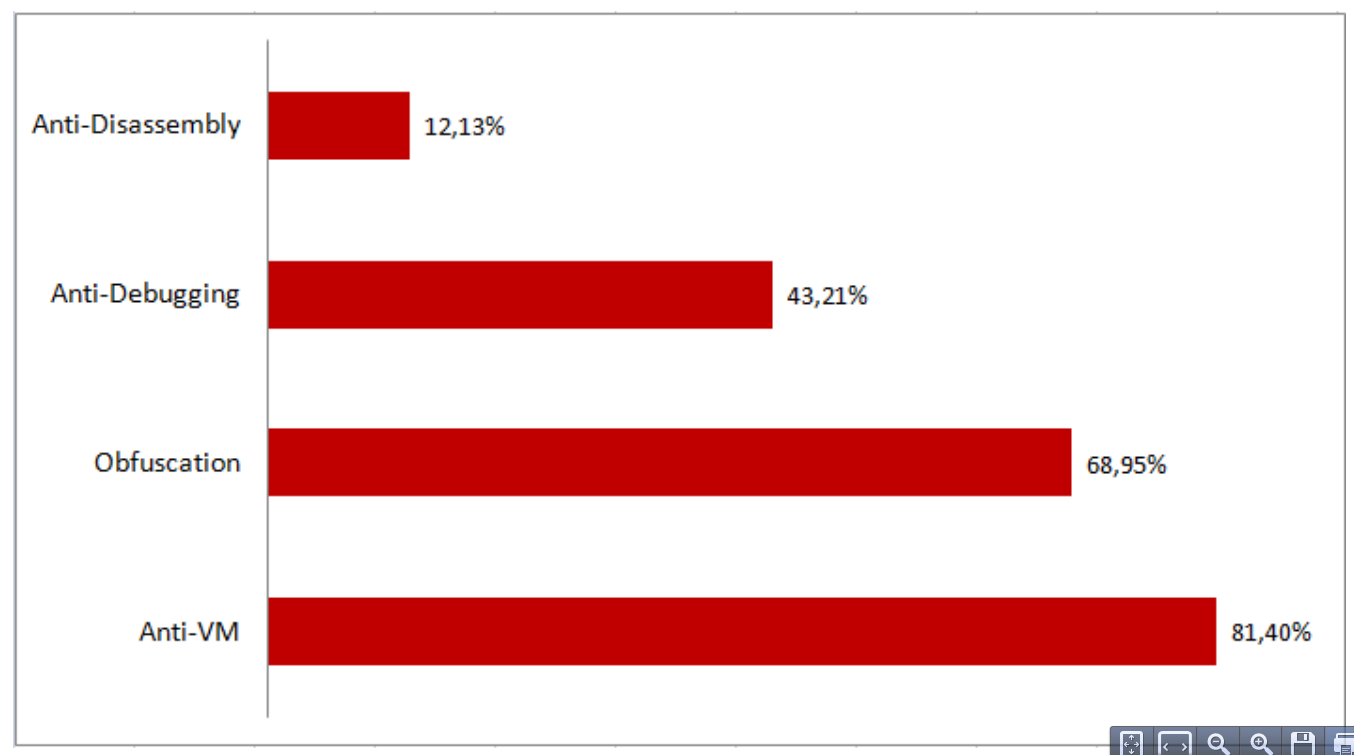
The presentation focused on the static analysis side and introduced the results of 51 static tests run against a representative cross-section of 4 million malware samples. The tests were focused on detection evasion attempts by the malware and divided into 4 groups:
- Detection of virtual machines, i.e. do not run under VM or change behavior to non-malicious
- Techniques to avoid disassembly, i.e. prevent a security researcher from reverse-engineering a malware sample by looking at it assembly language source code
- Methods of preventing debugging
- General obfuscation methods, i.e. disrupting the analysis process by calling functions in unorthodox ways
Results
The results clearly showed that close to 90% (88.96) of the analyzed malware employs at least one of the listed evasion technologies, and that anti-virtualization attempts lead the pack by a wide margin:
For more data on this fascinating world of evasion techniques, please take a look at both the full presentation and detailed technical paper. Sample code for the evasion techniques is available at: http://www.github.com/rrbranco/blackhat2012.
Feedback
The feedback at the conference itself was excellent, but we welcome your opinions on what data you would like us to focus on.
If you are a security researcher, we designed the Dissect || PE analysis engines with you in mind. They are extensible though simple plugin mechanisms, which gives you an opportunity to run your detection algorithms against this large sample database and publish the results in the research portal.
Please get in touch with us through comments in this blog post or email at: rbranco *noSPAM* qualys.com.