Drupal SQL Critical Vulnerability and How Qualys Can Help
On October 15, 2014, Drupal, a free, open source software used to create and manage websites, announced the existence of a vulnerability in its Drupal 7 database API abstraction layer. The vulnerability allows an attacker to send specially crafted requests resulting in arbitrary SQL execution. Depending on the content of the requests this can lead to privilege escalation, arbitrary PHP execution, or other attacks.
What We Know
![]() The vulnerability impacts all Drupal core 7.x versions prior to 7.32. The vulnerability came out around the same time POODLE was announced and was somewhat overshadowed by POODLE, however this is readily exploitable and similar to Heartbleed.
The vulnerability impacts all Drupal core 7.x versions prior to 7.32. The vulnerability came out around the same time POODLE was announced and was somewhat overshadowed by POODLE, however this is readily exploitable and similar to Heartbleed.
Since October 15, 2014, automated exploits targeting this specific vulnerability have been wreaking havoc on the Internet. The Drupal Security Team is advising that those administering Drupal 7.x-enabled websites should proceed under the assumption that those websites were compromised unless updated or patched before October 15, 2014, 11 PM UTC, or 7 hours after the original announcement of the vulnerability. It’s important to note that simply patching or upgrading a compromised website will not remove backdoors or other Trojans that may have been installed.
Vulnerability Info
SA-CORE-2014-005 – Drupal Core – SQL Injection
Versions Impacted: Drupal core 7.x versions prior to 7.32
Date: October 15, 2014
Related CVE: CVE-2014-3704
How Qualys Can Help
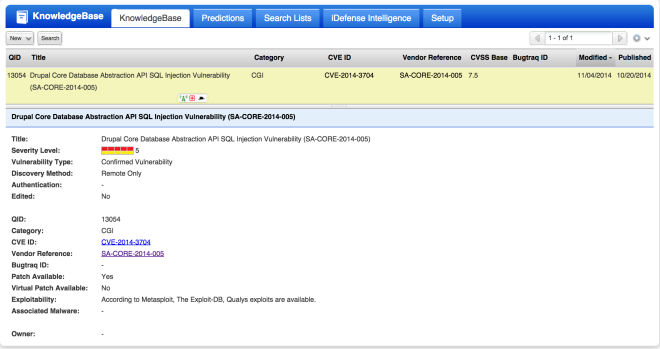
For existing customers, you can run a vulnerability scan using QID 13054 (see details below).
A vulnerable website will appear as follows:
For non-Qualys customers, we have included a check for this vulnerability in Qualys Freescan that can be accessed at https://freescan.qualys.com.
Remediation Steps
If you determine that your website is vulnerable, I suggest following the remediation steps on the Drupal website immediately. As previously mentioned, although upgrading and/or patching your Drupal version is a first step, this will not discover or remove malicious code that may have been added by attackers. In such cases, you will likely need to restore the website (Drupal files, uploaded files and databases) from backups from before October 15, 2014.