Multiple Vulnerabilities Detected in Schneider FactoryCast HMI Gateway
During my vulnerability analysis work I came across interesting firmware for Schneider Electric ETG3000 FactoryCast HMI Gateway. When playing around with the firmware, I discovered two severe vulnerabilities that could be exploited remotely without authentication. On January 21 ICS-CERT issued an advisory on these vulnerabilities that Qualys reported.
Affected Products
 The following Schneider Electric ETG3000 FactoryCast HMI Gateways are affected:
The following Schneider Electric ETG3000 FactoryCast HMI Gateways are affected:
- TSXETG3000 all versions
- TSXETG3010 all versions
- TSXETG3021 all versions
- TSXETG3022 all versions
Additional Details
Date: January 21, 2015
Related CVEs: CVE-2014-9197 and CVE-2014-9198
Weakness Type: CWE-306 – Missing Authentication for Critical Function
CVE-2014-9197
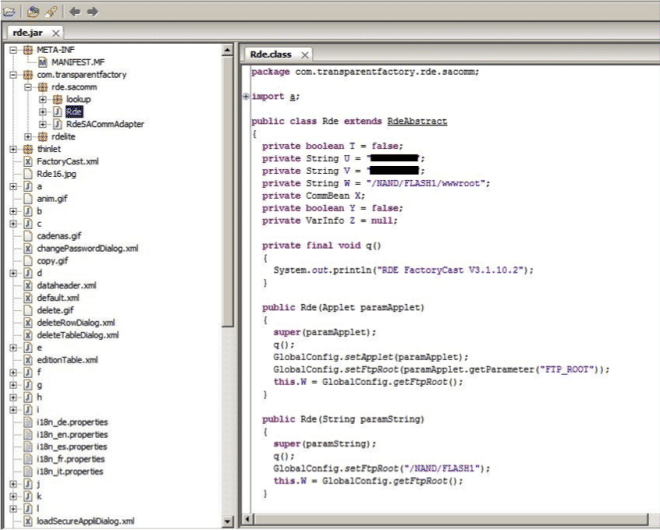
CVE-2014-9197 describes how vulnerable devices store an important configuration file at non-secure location which is accessible to any user. The configuration file rde.jar can be accessed by any unauthenticated user using the web interface of the device or simply by going to http://DeviceIP/classes/rde.jar.
This rde.jar file contains details related to device configuration including FTP service details and other sensitive information. Schneider patched this issue by moving this file to a secure location.CVSS v2 base score of 10.0 has been assigned to this issue.
CVE-2014-9198
As I was stripping apart rde.jar, I found hardcoded credentials for the FTP service on device. To patch this issue, the vendor has provided only a way to disable the affected FTP service but has not removed these hardcoded accounts. CVSS v2 base score of 10.0 has been assigned to this issue.
Impact
All mentioned issues in the advisory are marked as critical because they can cause large-scale damage by allowing a remote unauthenticated attacker to access/modify configurations on the device or shut it down. Hence, I would really advise you to patch your systems as soon as possible and disable the FTP service.
Also, you should note that devices which are configured with default credentials for web interface are still affected by this vulnerability as an authenticated attacker can access this configuration file. It is always recommended to change the default credentials.
Impact to individual organizations depends on many factors that are unique to each organization. NCCIC/ICS-CERT recommends that organizations evaluate the impact of these vulnerabilities based on their operational environment, architecture, and product implementation.
Mitigation
To minimize exposure, network filtering controls should be used to limit the IP ranges that can access the FTP service. See full mitigation details in the ICS-Cert advisory.