How to Check for Unprotected MongoDB Databases
Table of Contents
Recently three students from University of Saarland in Germany discovered that the MongoDB databases running on several thousand commercial web servers allow remote attackers to easily access and manipulate the database from the Internet. According to their research, it is not uncommon for MongoDB databases to be configured to accept any connection from the Internet.
In this blog I will discuss how unauthorized access works and how to check if your MongoDB is exposed. Qualys Vulnerability Management has released QID 19965 to check for the same.
Qualys Detection
The Qualys detection works by sending a query to the default MongoDB port and analyzing the response to see if an instance of MongoDB is running on that port, and then sending a second query and analyzing the response to see if the MongoDB instance is open to unauthenticated access from the Internet.
Step 1: Identify MongoDB
The MongoDB service is running on TCP port 27017 by default, but database administrators can of course change it to another port.
The MongoDB Wire Protocol packet format is:
struct MsgHeader { int32 messageLength; // total message size, including this int32 requestID; // identifier for this message int32 responseTo; // requestID from the original request // (used in responses from db) int32 opCode; // request type - see table below }
To identify the service, a message with a Query “OpCode” with “whatsmyurl” in the request is sent.
In the reply from the MongoDB service, you should see the “requestID” at offset 9 which will be followed by \x01\x00\x00\x00. This signifies that it is a response to your previous request. You could also match other fields like “you” or “ok” in the document structure to confirm that MongoDB is running, as shown in the screen capture below.
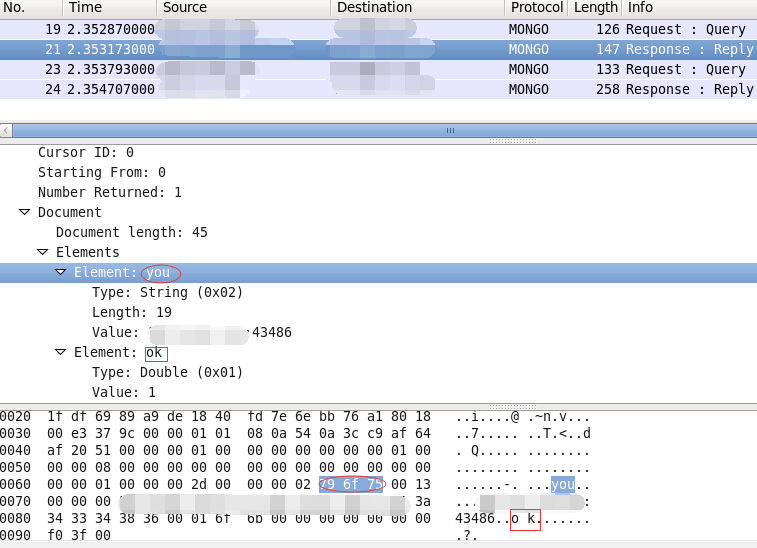
Step 2: Perform the Test
The second step of our detection is to send a “list Databases” query to the remote MongoDB server. Targets that are exposed to unauthorized access should return the packets shown in the screen capture below.
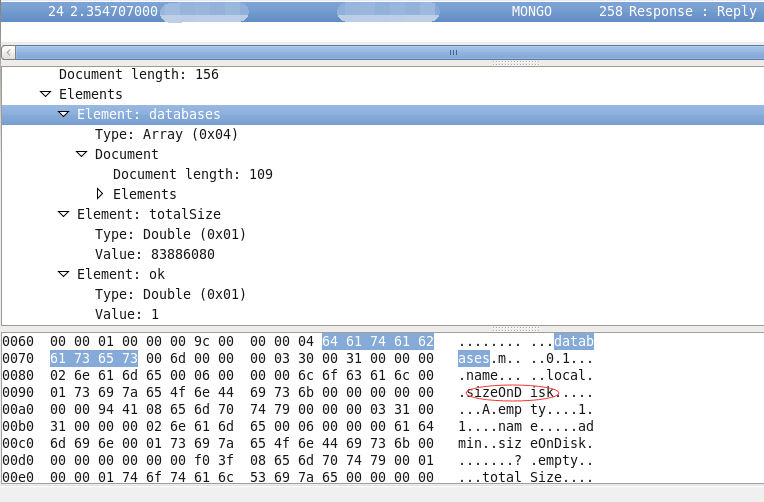
If the remote service returns its databases list and ‘sizeOnDisk’ which means our “list Databases” got executed, we can conclude that it allows remote access without authorization. At this point an attacker could run the MongoDB client to connect to the server and perform any unauthorized action or take control of the database, as shown in the screen capture below.

Conclusion
As you can see it is quite easy to find MongoDB that are exposed in this way on the Internet. With the computing power of today attackers can send thousands of packets in a very short time to get a list of running IPs. It is reported that around 40,000 vulnerable MongoDB databases were discovered in this way on the Internet.