Emergency Flash Player 0-day update released by Adobe
Adobe released APSB16-36 today to fix one 0-day vulnerability in Flash. The vulnerability is currently being used in active attacks and therefore Adobe released this emergency fix. If left un-patched, attackers can remotely take complete control of the machine. The vulnerability (CVE-2016-7855) is triggered when the victim views malicious Adobe flash content. Usually innocent users end up with malicious flash content by clicking on bad links from e-mails, blogs, bulletin boards and other sources.
All platforms including Windows, Macintosh, Linux and Chrome OS are affected. It’s a use-after-free issues in which the software attempts to access memory after it has been freed, which can cause a program to crash or in this case can result in the execution of attacker supplied code. The updated versions are below:
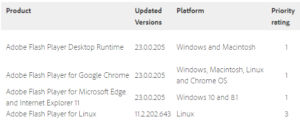
Currently, Adobe flash is the favorite mechanism by which Exploit Kits and bad actors compromise a machine and since this vulnerability is already weaponized and used in the wild, users should patch as soon as possible. This is the fourth zero day fixed by Adobe this year where active attacks are already underway before the availability of the vendor patch.