Adobe Fixes Half a Dozen Flash Vulnerabilities and More
Flash has been the top target for exploit kits and we have observed that defender behavior, i.e. how fast patches are applied along with other factors in the threat landscape could have led to a decline in the number of Flash vulnerabilities being weaponized in exploit kits. In 2016, the time to patch 80% of Flash vulnerabilities reduced by more than half to 62 days as compared to the previous year when it was 144 days. This data is based on more than 3 billion scans performed by Qualys and could be one of the contributing factors why Flash-based attack integration in exploit kits is declining. If organizations patch quickly it gives less time for exploit kits to integrate the exploits and the chances of phishing vulnerable users reduce greatly if more machines are patched quickly.
In today’s release Adobe announced the release of APSB17-15 which fixed six memory corruption vulnerabilities that could lead to code execution. It also fixed a seventh use-after-free issue in Flash which can lead to similar consequences as the other six. These issues allow attackers to remotely take over a user’s machine if the user visited a malicious website that hosted attacker-supplied content. The list of affected versions is below.
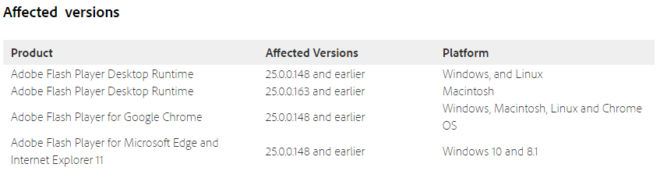
In summary, although Flash exploit integration in exploit kits is showing signs of decline, we highly recommend organizations to apply these patches.