BlueKeep Attacks Observed Months after Initial Release

The BlueKeep vulnerability, initially released in May 2019, is currently being exploited in the wild. Cybersecurity researchers have spotted initial attacks of Bluekeep RDP vulnerability. Here’s a reminder about BlueKeep and instructions for using Qualys to identify attacks and remediate this vulnerability.
About BlueKeep Attacks
BlueKeep allows an unauthenticated attacker to connect to the target system using Microsoft’s RDP protocol to execute code on the vulnerable system. It is wormable remote code execution vulnerability, as it can propagate itself from one vulnerable computer to another without any victim interaction.
Recently, BlueKeep exploitation activity was seen by security researcher Kevin Beaumont, who has been running a worldwide honeypot network named BluePot to spot exploitation activities. Fortunately, the attack code seen so far is not wormable. Later on, security researcher Marcus Hutchins analyzed these attacks and found that attackers are scanning internet to search unpatched windows systems with RDP (port 3389) exposed to the internet.
The unpatched systems running with RDP ports open are highly at risk and immediate action should be taken to remediate vulnerability.
Protecting from BlueKeep
Microsoft’s Patch Tuesday, May 2019 included patches for CVE-2019-0708 (aka BlueKeep vulnerability).
Qualys released a blog post earlier on how to identify BlueKeep vulnerability in your environment:
Windows RDP Remote Code Execution Vulnerability (BlueKeep) – How to Detect and Patch
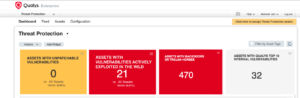
Qualys Threat Protection
In addition, Qualys just updated BlueKeep as “Active Attack RTI” to Qualys customers in Qualys Threat Protection for effectively identifying and tracking the BlueKeep vulnerability.
You can search for all vulnerable systems in Qualys Threat Protection by using the following QQL (Qualys Query Language) query:
vulnerabilities.vulnerability.threatIntel.activeAttacks:true
Mitigation
As explained in the Qualys blog post, admins are advised to apply the patch as soon as possible.
- Block RDP service (port 3389)
- Enable NLA – QID 90788 (Microsoft Windows Network Level Authentication Disabled) can be used to find hosts that have NLA disabled.
Get Started Now
To start detecting and remediating this vulnerability now, get a Qualys Suite trial.