Microsoft Windows CryptoAPI Spoofing Vulnerability (CVE-2020-0601) – How to Detect and Remediate

Update January 31, 2020: Client testing is now available at clienttest.ssllabs.com.
Update January 15, 2020: Detection dashboard now available.
Today, Microsoft released patch for CVE-2020-0601, aka Curveball, a vulnerability in windows “crypt32.dll” component that could allow attackers to perform spoofing attacks. This was discovered and reported by National Security Agency (NSA) Researchers. The vulnerability affects Windows 10 and Windows Server 2016/2019 systems.
This is a serious vulnerability and patches should be applied immediately. An attacker could exploit this vulnerability by using a spoofed code-signing certificate, meaning an attacker could let you download and install malware that pretended to be something legit, such as software updates, due to the spoofed digital signature. Examples where validation of trust may be impacted include:
- HTTPS connections
- Signed files and emails
- Signed executable code launched as user-mode processes
Exploits/PoC:
There are no reports of active exploitation or PoC available in public domain at this point of time. However, per NSA advisory “Remote exploitation tools will likely be made quickly and widely available.”
Detecting CVE-2020-0601 with Qualys VM
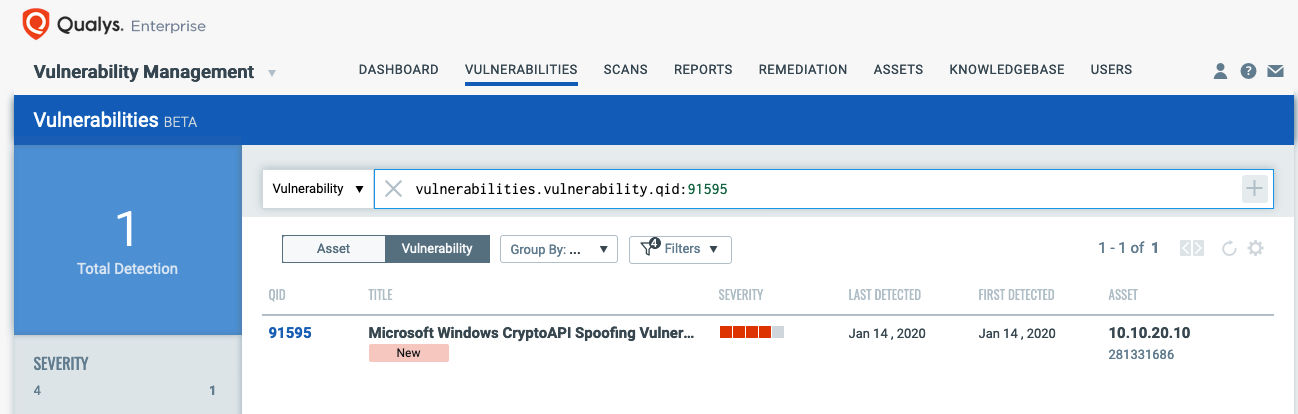
The best method for identifying vulnerable hosts is through the Qualys Cloud Agent or via Qualys authenticated scanning. Qualys has issued a special QID (91595) for Qualys Vulnerability Management that covers only CVE-2020-0601 across all impacted Operating Systems. This QID will be included in signature version VULNSIGS-2.4.791-3, and requires authenticated scanning or the Qualys Cloud Agent. Cloud Agents will automatically receive this new QID as part of manifest version 2.4.791.3-2.
You can search for this within AssetView or the VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.cveIds:CVE-2020-0601 and
vulnerabilities.vulnerability.qid:91595
or use the pre-built CryptoAPI Spoofing vulnerability dashboard.
Remediating with Qualys Patch Management:
Customers using Qualys Patch Management with Cloud Agent can search for cve:`CVE-2020-0601` in the Patch Catalog, and click “Missing” in the side panel to locate and deploy patches to all affected Operating Systems.
For emergency patching, you can create an On-demand Job and target it at the “Cloud Agent” tag to cover all hosts. For continuous patching, a Daily Job can be created with a 24-hour “Patch Window” to ensure all hosts will continue to receive the required patches. This patch does require a reboot.
Targeting specific operating systems is not necessary, and all patches can be placed into a single job. The Qualys Cloud Agent already knows which patch is needed for each host.
You can search for this within Qualys Patch Management by using the following QQL query:
cve:`CVE-2020-0601` and patchStatus: `Missing`
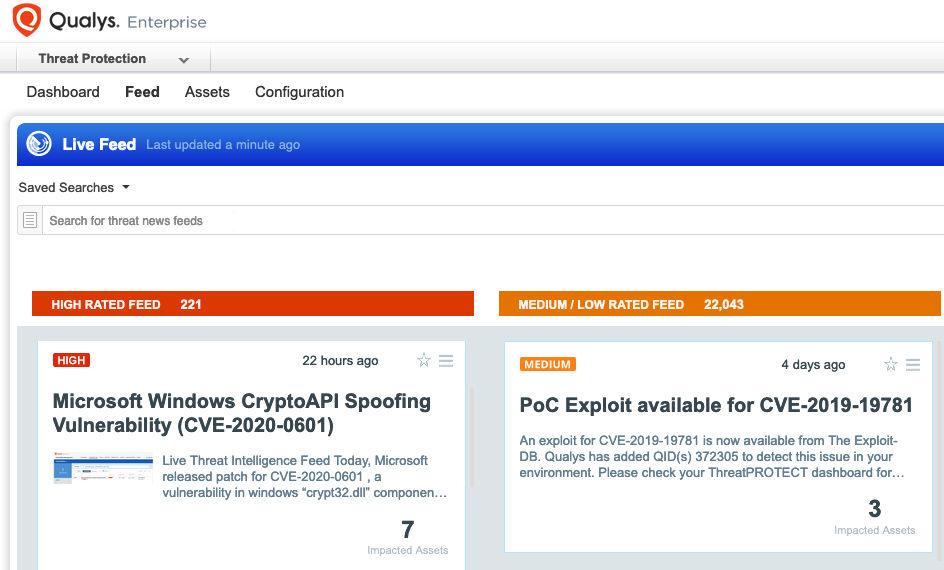
Qualys Threat Protection
In addition, Qualys customers can locate vulnerable host through Qualys Threat Protection. This helps in effectively identifying and tracking this vulnerability.
Mitigation
- Apply Windows OS Patches available for Windows 10, Windows Server 2016 and 2019 as soon as possible.
- Prioritize patching endpoints like – Web Servers, Domain Controllers, DNS Servers, proxies that perform TLS validation.
- Restrict external access to only trusted networks.
- Ensure that certificate validation is enabled for TLS proxies.
- See also DHS Emergency Directive 20-02: Mitigate Windows Vulnerabilities from January 2020 Patch Tuesday
Get Started Now
To start detecting and remediating this vulnerability now, get a Qualys Suite trial.
You have the query text listed as vulnerabilities.vulnerability:qid:91595 and your screen shot shows vulnerabilities.vulnerability.qid: 91595
Also vulnerabilities.vulnerability.cveId:CVE-2020-0601 should be vulnerabilities.vulnerability.cveIds: CVE-2020-0601
First PoC published for CVE-2020-0601
https://github.com/ollypwn/cve-2020-0601