OpenBSD OpenSMTPD Remote Code Execution Vulnerability (CVE-2020-7247)

Qualys Research Labs discovered a vulnerability in OpenBSD’s OpenSMTPD mail server that allows an attacker to execute arbitrary shell commands with elevated privileges. OpenBSD developers have confirmed the vulnerability and also quickly provided a patch.
Proof-of-concept exploits are published in the security advisory.
Vulnerability Details
This vulnerability exists in OpenBSD’s mail server OpenSMTPD’s “smtp_mailaddr()” function, and affects OpenBSD version 6.6. This allows an attacker to execute arbitrary shell commands like “sleep 66” as root user.
Exploitation of the vulnerability had some limitations in terms of local part length (max 64 characters is allowed) and characters to be escaped (“$”, “|”). Qualys researchers were able to overcome these limitations using a technique from the Morris Worm (one of the first computer worms distributed via the Internet, and the first to gain significant mainstream media attention) by executing the body of the mail as a shell script in Sendmail.
For more technical details on this vulnerability, please see the security advisory.
Detecting CVE-2020-7247
Qualys has issued QID 50097 for Qualys Vulnerability Management that includes remote and authenticated detections for OpenBSD vulnerability. This QID will be included in signature version VULNSIGS-2.4.808-2.
QID 50097 : OpenBSD OpenSMTPD Remote Command Execution Vulnerability
- Remote – This detection sends a “MAIL FROM:<;>”, SMTP payload to detect if the vulnerability exists on remote host.
- Authenticated (OpenBSD) – This executes “syspatch -l” command to check for the presence of patch applied on the system.
You can search for this new QID in AssetView or within the VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.qid:50097
vulnerabilities.vulnerability.cveIds:`CVE-2020-7247`
This will return a list of all impacted hosts.
You can also track all OpenBSD vulnerabilities in your environment with the OpenBSD Vulnerabilities Dashboard that leverages data in your Qualys Vulnerability Management subscription, as shown below:
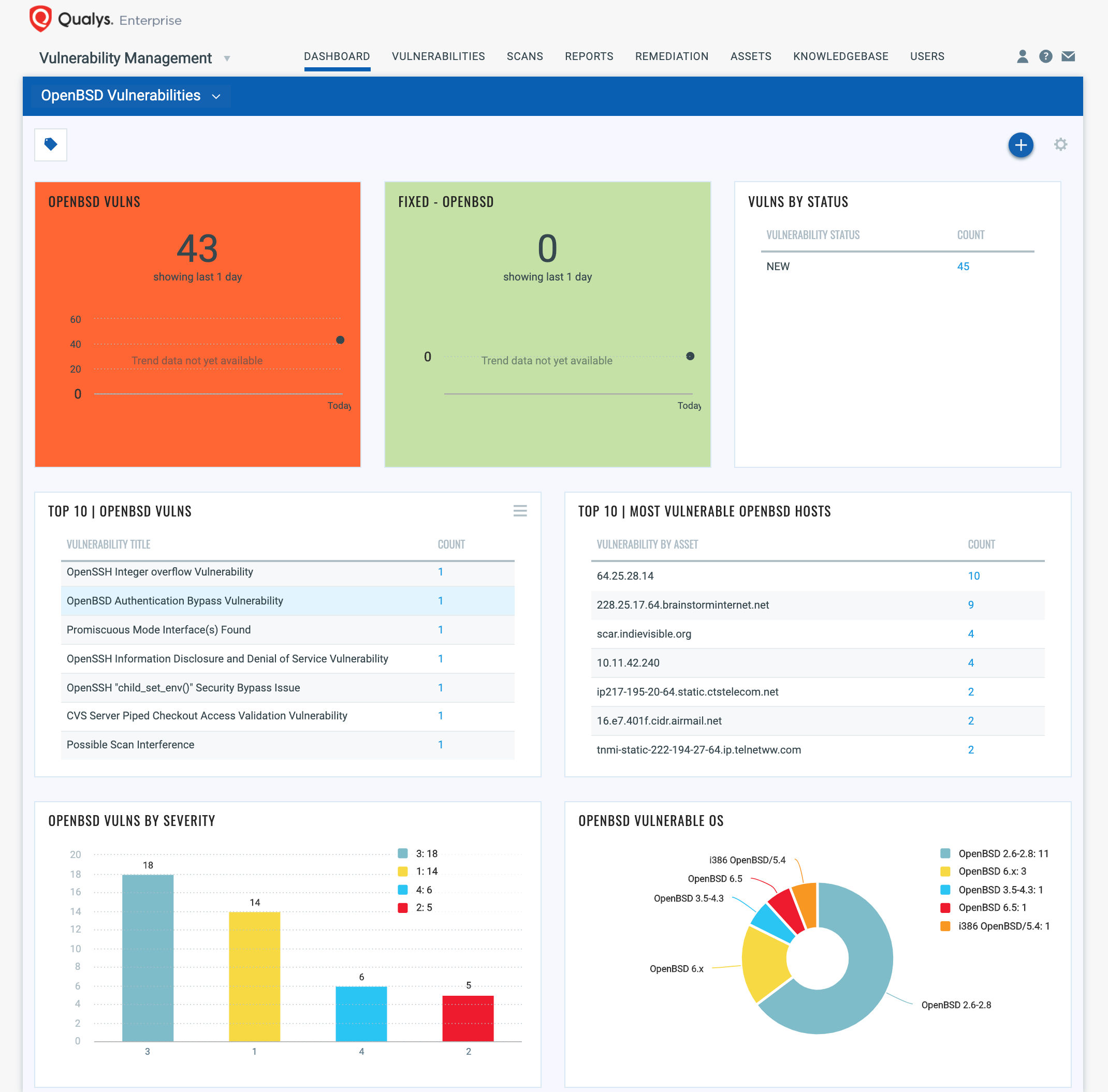
Finding Vulnerable Hosts
The fastest way to locate vulnerable hosts is though the Qualys Threat Protection Live Feed as seen here:
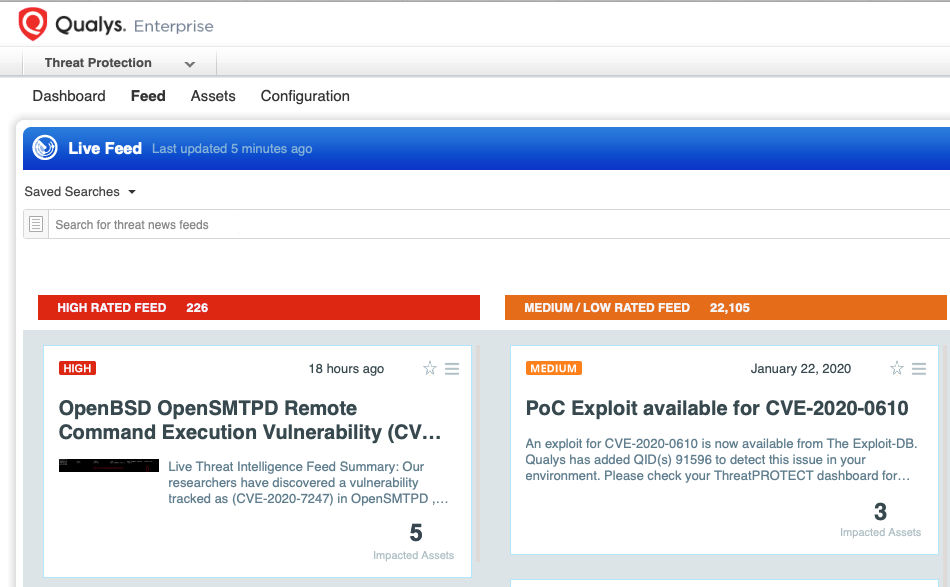
Simply click on the impacted assets number to see a list of hosts with this vulnerability.
Remediation
To remediate this vulnerability, affected OpenBSD users are recommended to install patches for OpenBSD 6.6. See reference 019 in https://www.openbsd.org/errata66.html.
References
- Qualys Reveals Critical OpenBSD Mail Server Security Flaw (Security Boulevard)
- RCE in OpenSMTPD library impacts BSD and Linux distros (ZDNet)
- Critical Remote Code Execution Bug Fixed in OpenBSD SMTP Server (Bleeping Computer)
- CVE-2020-7247 RCE flaw in OpenSMTPD library affects many BSD and Linux distros (Security Affairs)
- Critical RCE flaw in OpenSMTPD, patch available (HelpNet Security)
- Critical Bug Fix: OpenBSD Vulnerability Needs Urgent Patching – RCE With Morris Worm Inspiration (Computer Business Review)
- Kritische Sicherheitslücke in OpenSMTPD erlaubt(e) Codeausführung aus der Ferne (Heise Online)