GRUB2 Boothole Buffer Overflow Vulnerability (CVE-2020-10713) – Automatically Discover, Prioritize and Remediate Using Qualys VMDR®

On July 29, 2020, Eclypsium researchers disclosed a high-risk vulnerability in GRUB2 (GRand Unified Bootloader version 2) affecting billions of Linux and Windows systems, even when secure boot is enabled. CVE-2020-10713 is assigned to this buffer overflow vulnerability, termed as “Boothole”.
Successful exploitation of the vulnerability requires high privileges or physical access to the device. According to Eclypsium researchers, “attackers exploiting this vulnerability can install persistent and stealthy bootkits or malicious bootloaders that could give them near-total control over the victim device.”
Secure Boot is designed to verify all the firmware of the computer is trusted. However, CVE-2020-10713 results in total pwn of secure boot in systems using GRUB. The bug resides in GRUB’s inadequate error handling.
Additional Vulnerabilities in GRUB2
After the initial vulnerability report by the Eclypsium team, a number of additional vulnerabilities were discovered by the Canonical security team:
- CVE-2020-14308: Heap-based buffer overflow in grub_malloc
- CVE-2020-14309: Integer overflow in grub_squash_read_symlink can lead to heap-based overflow
- CVE-2020-14310: Integer overflow read_section_from_string can lead to heap-based overflow
- CVE-2020-14311: Integer overflow in grub_ext2_read_link can leads to heap-based buffer overflow
- CVE-2020-15705: Failure to validate kernel signature when booted without shim
- CVE-2020-15706: Use-after-free in grub_script_function_create
- CVE-2020-15707: Integer overflow in initrd size handling
Affected Vendors
All operating systems which use GRUB2 with Secure Boot are affected. As per Eclypsium’s report, the following vendors are confirmed to be affected:
- Microsoft
- UEFI Security Response Team (USRT)
- Oracle
- Red Hat (Fedora and RHEL)
- Canonical (Ubuntu)
- SuSE (SLES and openSUSE)
- Debian
- Citrix
- VMware
- Various OEMs
Identification of Assets using Qualys VMDR
The first step in managing vulnerabilities and reducing risk is identification of assets. Qualys VMDR enables easy identification of Windows and Linux systems
operatingSystem.category1:`Windows` or operatingSystem.category1:`Linux`
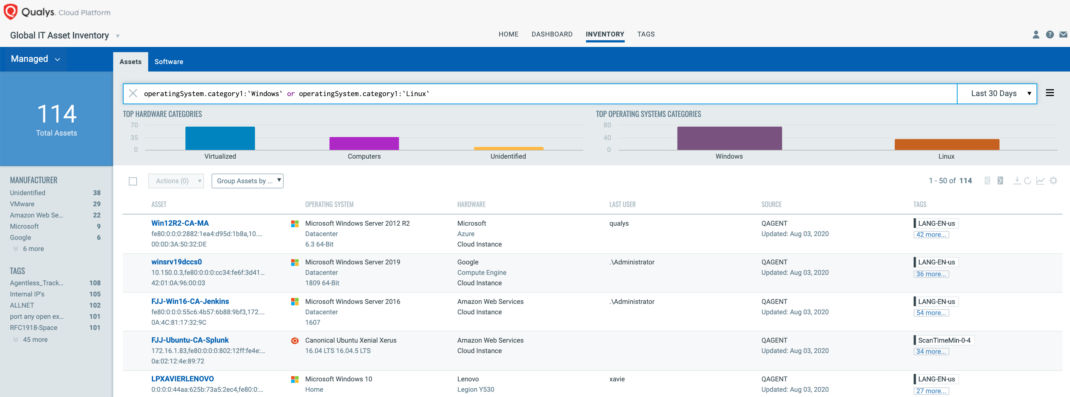
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, let’s say – Boothole. This helps in automatically grouping existing hosts with Boothole as well as any new Windows or Linux host that spins up in your environment. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
Discover Boothole CVE-2020-10713 Vulnerability
Now that hosts with Boothole are identified, you want to detect which of these assets have flagged this vulnerability. VMDR automatically detects new vulnerabilities like Boothole based on the always updated Knowledgebase.
You can see all your impacted hosts for this vulnerability tagged with the ‘Boothole’ asset tag in the vulnerabilities view by using this QQL query:
vulnerabilities.vulnerability.qid:[173771, 173770, 173769, 173768, 197967, 177969, 177966, 256935, 256934, 158696, 158695, 158694]
This will return a list of all impacted hosts.
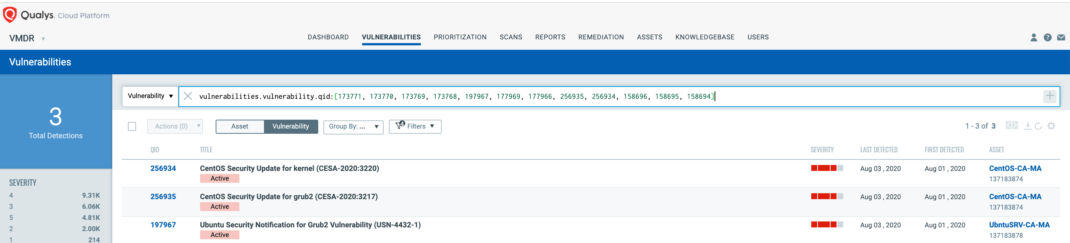
These QIDs are included in signature version VULNSIGS-2.4.951-3 and above and can be detected using authenticated scanning or the Qualys Cloud Agent.
Using VMDR, the Boothole vulnerability can be prioritized for the following real-time threat indicators (RTIs):
- Denial of Service
- High Data Loss
- High Lateral Movement
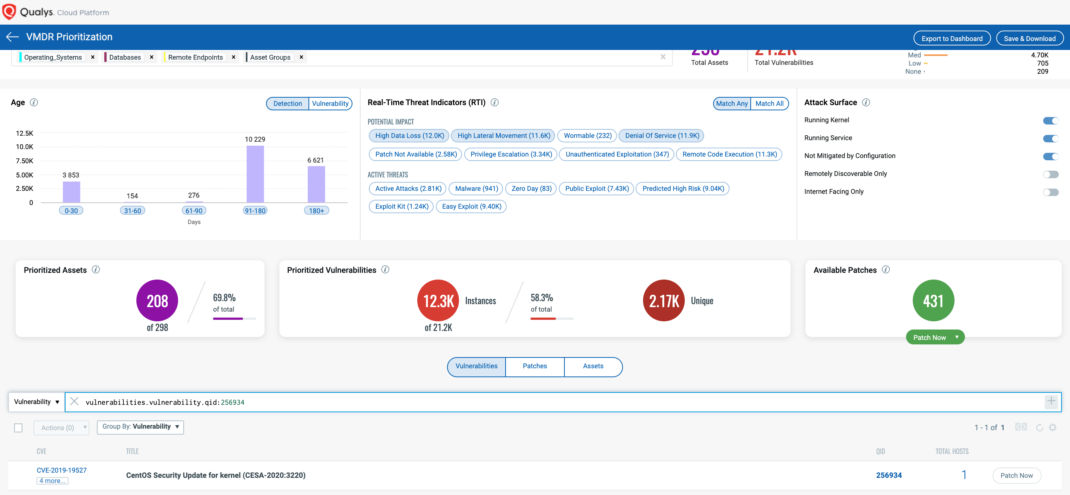
VMDR also enables you to stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
Simply click on the impacted assets for the Boothole threat feed to see the vulnerability and impacted host details.
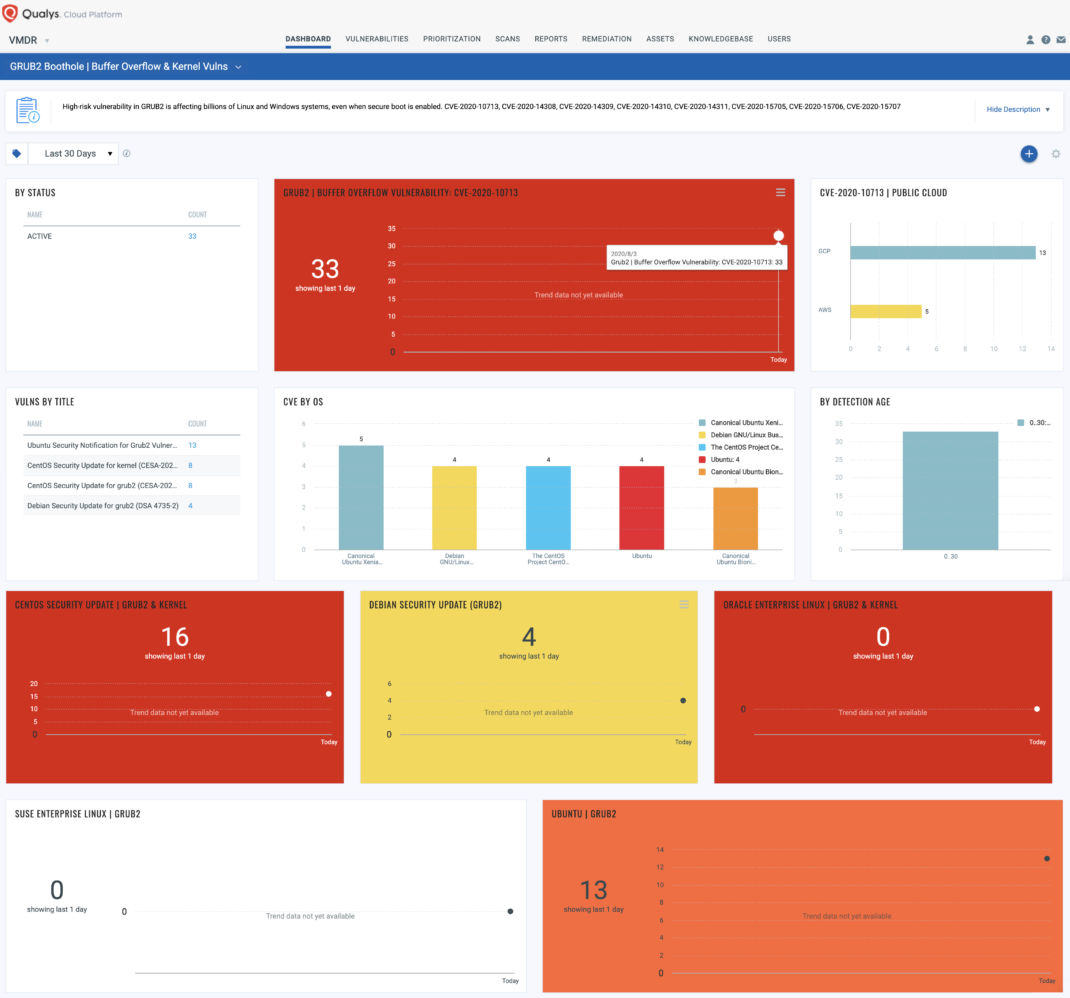
With VM Dashboard, you can track Boothole, impacted hosts, their status and overall management in real-time. With trending enabled for dashboard widgets, you can keep track of Boothole vulnerability trends in your environment using GRUB2 Boothole Vulnerability Dashboard.
Response by Patching and Remediation
VMDR rapidly remediates the Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select “cve:`CVE-2020-10713`” in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go for hosts grouped together by a tag – Boothole.
For proactive, continuous patching, you can create a job without a Patch Window to ensure all hosts will continue to receive the required patches as new patches become available for emerging vulnerabilities.
Users are encouraged to apply patches as soon as possible.
Mitigation
Microsoft has published an advisory to address security feature bypass in GRUB.
Other affected vendors provide updates for GRUB2.
Unstable Linux Patches
Qualys also released a Notification over the weekend for customers : Qualys Support Proactive Notification: Red Hat Update for BootHole Vulnerability Renders Systems Unbootable.
Get Started Now
Start your Qualys VMDR trial for automatically identifying, detecting and patching the high-priority Boothole vulnerability CVE-2020-10713.

Hello, What Dynamic Tag rule was used to group the list of assets identified with “operatingSystem.category1:`Windows` or operatingSystem.category1:`Linux`” ?
Thank you