Google Android May 2021 Security Patch Vulnerabilities: Discover and Take Remote Response Action Using VMDR for Mobile Devices

The recently released Android Security Bulletin for May 2021 addresses 40 vulnerabilities, out of which 4 are rated as critical vulnerabilities. The vulnerabilities affect open-source components such as the Android Framework, Android Media Framework, Android System, and Android’s Linux Kernel fork. The vulnerabilities also affect MediaTek, AMLogic, and QUALCOMM closed-source components.
Android System Remote Code Execution (RCE) Vulnerability
Google released a patch to fix an RCE critical vulnerability (CVE-2021-0473). This vulnerability has a CVSSv3 base score of 8.8 and should be prioritized for patching. It affects Android versions 8.1, 9, 10, and 11.
AMLogic Remote Code Execution (RCE) Vulnerability
Google released a patch to fix an RCE critical vulnerability (CVE-2021-0467). This vulnerability has a CVSSv3 base score of 8.8 and should be prioritized for patching. It affects the AMLogic bootROM component.
Android System Remote Code Execution (RCE) Vulnerability
Google released a patch to fix an RCE critical vulnerability (CVE-2021-0474). This vulnerability has a CVSSv3 base score of 8.8 and should be prioritized for patching. It affects Android versions 8.1, 9, 10, and 11.
Android System Remote Code Execution (RCE) Vulnerability
Google released a patch to fix an RCE critical vulnerability (CVE-2021-0475). This vulnerability has a CVSSv3 base score of 8.8 and should be prioritized for patching. It affects Android versions 8.1, 9, 10, and 11.
Google fixed eight high-severity Elevation of Privilege (EoP) vulnerabilities in Framework, Media Framework, System, and Kernel components. They also fixed four high-severity Information Disclosure (ID) vulnerabilities in Framework, Media Framework, and System.
‘The most severe of these issues is a critical security vulnerability in the System component that could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,’ Google explains. Also, Apple released iOS 14.5.1, iPadOS 14.5.1, and iOS 12.5.3 to fix critical zero-day vulnerabilities in Webkit. This is the second time Apple has released an immediate release after a major release and additional release for iOS 12.5 version to secure old iOS devices. The increase in OS-level vulnerabilities makes mobile security a must-have product as part of the security ecosystem for a company. Mobile device management (MDM) solutions don’t help you detect these latest vulnerabilities and don’t provide provisioning to secure the devices. Usually, MDM provides OS version restriction on enrollment, but in this case, you can’t apply OS version restriction on iOS 14.5 or iOS 12.5.2 or on the security patch. To minimize the risk, you need to identify the affected assets and then update the assets to the latest applicable version.
Discover Assets Missing the Latest Android Security Patch
Discover Vulnerabilities and Take Remote Response Action Using VMDR for Mobile Devices
The first step in managing these critical vulnerabilities and reducing risk is to identify the assets. Qualys VMDR for Mobile Devices makes it easy to identify the assets missing the latest security patch. To get the comprehensive visibility of the mobile devices, you need to install Qualys Cloud Agent for Android or iOS on all mobile devices. The device onboarding process is easy, and the inventory of mobile devices is free.
Query: vulnerabilities.vulnerability.title:’May 2021’

Once you get the list of assets missing the latest security patch, navigate to the Vulnerability tab and apply the Group By “Vulnerabilities” to get the list of the CVEs which Google fixes in the May security patch. Qualys VMDR helps you understand what kind of risk you are taking by allowing the unpatched device to hold corporate data and connect to your corporate network.

QID 610338 is available in signature version SEM VULNSIGS-1.0.0.34, and there is no dependency on any specific Qualys Cloud Agent version.
With the VMDR for Mobile Devices dashboard, you can track the status of the assets on which the latest security patch is missing. The dashboard will be updated with the latest data collected by Qualys Cloud Agent for Android devices.

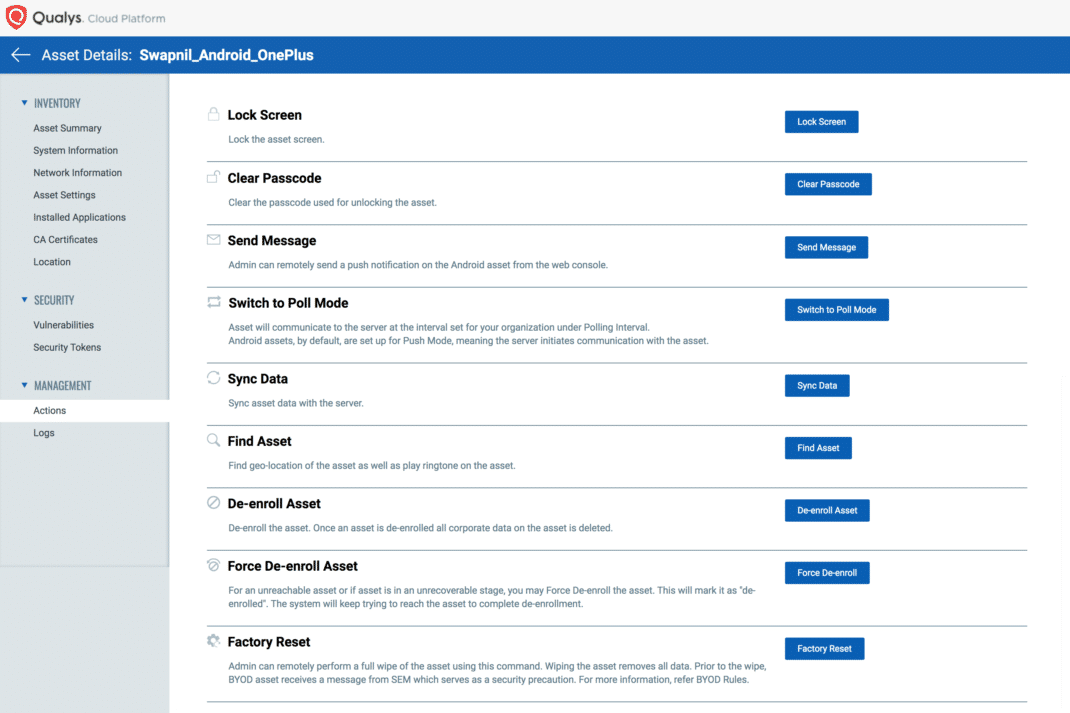
Remote Response Action
You can perform the “Send Message” action to inform the end user to update the security patch to the latest patch. Also, you may provide step-by-step details to update the security patch.
As of this writing, the May security patch is not released by most of the manufacturers. For now, it has been released by Google for Pixel, Samsung, and LG. For such manufacturers, the vulnerabilities are marked as “Confirmed”; for the rest, it is marked as “Potential”. QIDs specific to individual manufacturers are 610337, 610340, 610341, and 610338 is the QID for rest of the manufacturer. All are available in signature version SEM VULNSIGS-1.0.0.34
We recommend updating to the latest security patch for the assets where vulnerabilities are detected as “Confirmed”. For the rest of the manufacturers, you can take appropriate action based on the asset criticality.
Get Started Now
Qualys VMDR for Mobile Devices is available free for 30 days to help customers detect vulnerabilities, monitor critical device settings, and correlate updates with the correct app versions available on Google Play Store. You can try our solution by registering for the free 30-day service.